Alert Profiler Rule Creator
Use the Alert Profiler rule creator to fine-tune which threats are elevated to alerts.
The rule creator is a straightforward, graphical way to create “If…Then” statements: If a threat matches the conditions, then create an alert.
You can also simplify statements by applying a “group” to conditions (akin to putting them inside parentheses). Use the Add Group option for this.
The following terms apply when creating rules:
| Term | Definition |
|---|---|
| Any | Create an alert if ANY of the conditions are met. This is like the “OR” operator used between logical conditions and is commonly used to expand the detection and creation of alerts for those cases. |
| All | Create an alert only if ALL the conditions are met. This is like the “AND” operator used between logical conditions and is commonly used to reduce the detection and creation of alerts for those cases. |
| Feature | Properties of the examined domain, for example, domain name or the website behind it. |
| Operator | The logical test condition, for example, “does it contain” or “does it not contain”. You can create a condition that requires a certain property of the examined domain to have a certain value. If that condition is met, the result is true. |
| Value | What is being matched against, for example “MX record” or “Company asset”. After selecting certain values, another field is displayed for required input. |
The following are sample rules. For information on how to create rules, see Adding Alert Profiler rules.
Rule creator example 1
From the Alert Profiler page, you can click on a rule to view its properties. The following figure shows the Suspected Phishing Domain with MX record rule (part of the Suspected Phishing Domain threat scenario).
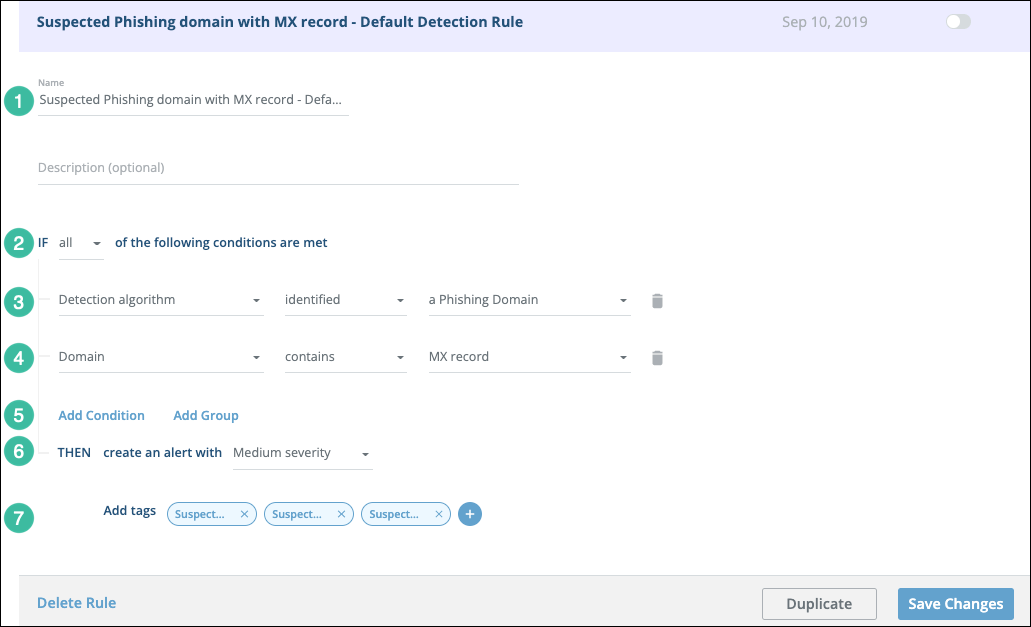
| Section | Description |
|---|---|
| 1 | Name and description. |
| 2 | Selecting all requires a match for all conditions. |
| 3 | Did the Digital Risk Protection (Threat Command) internal detection algorithm determine that this domain is a phishing domain? |
| 4 | Does the domain contain an MX record? This condition was added by clicking Add condition (5). |
| 5 | You can add additional conditions or groups of conditions. |
| 6 | If the threat matches all conditions, then an alert will be created with high severity. |
| 7 | If an alert is created, the specified tag will be added to it. |
This is one of the default rules for suspected phishing domains. If the current rules create alerts that are not relevant for your business needs, you can define additional conditions (in this rule or in another enabled rule). If the current rules are not picking up threats that should be elevated to alerts, you can loosen up the requirements to generate an alert, perhaps by changing all to any or by removing one of the current conditions.
Rule creator example 2
The following figure shows the properties of a custom rule that uses ALL and ANY as well as a condition group.
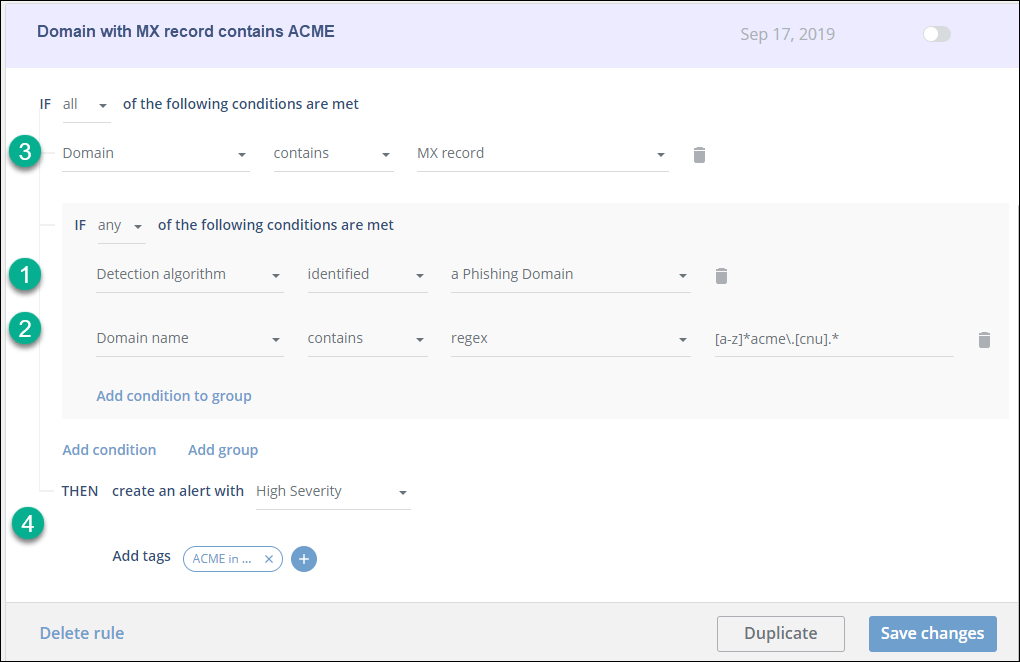
This rule, from the ACME company, was created as a group, by using Add Group instead of Add Condition.
The rule can be read as:
If (1) the Digital Risk Protection (Threat Command) internal detection algorithm determined that this domain is a phishing domain OR if (2) the domain name includes acme) AND (3) the domain contains an MX record, THEN (4) create a high severity alert with a tag, as specified.