Attack Indication Scenario Rule Conditions
This topic describes the conditions that you can use to create rules and the default rules provided for the attack indication scenario.
Attack indication includes the following scenarios:
Each scenario has its own conditions and default rules.
Credit cards for sale
Credit cards for sale - conditions The following table describes the conditions that you can use to create rules. When using a regular expression, don’t surround the expression with quotation marks.
| Features | Operator | Value | Description |
|---|---|---|---|
| Detection algorithm | identified/did not identify | ”A credit card for sale” | Did the detection algorithm identify a company credit card for sale on the dark web? |
| Asset tags | in/not in | Select tags | Are any of the threat’s matched assets tagged with any of the specified tags? |
| Bank name | in/not in | ”Select a bank” | Was the detected card issued by a specific bank? |
| BIN | in/not in | ”Select BINs” | Does the detected card have a specific BIN number? |
| Breach name | in/not in | ”Select breach” | Was the detected card part of a specific data breach? |
| Cardholder address | in/not in | ”Regex list” | Does the cardholder address contain a phrase (can be expressed as a regular expression)? |
| Cardholder address | is/is not | ”Exposed” | Is the cardholder address exposed? |
| Cardholder city | in/not in | ”Regex list” | Does the cardholder city contain a phrase (can be expressed as a regular expression)? |
| Cardholder city | is/is not | ”Exposed” | Is the cardholder city exposed? |
| Cardholder email | in/not in | ”Regex list” | Does the cardholder email address contain a phrase (can be expressed as a regular expression)? |
| Cardholder email | is/is not | ”Exposed” | Is the cardholder email address is exposed? |
| Cardholder full name | in/not in | ”Regex list” | Does the cardholder name contain a certain phrase (can be expressed as a regular expression)? |
| Cardholder full name | is/is not | ”Exposed” | Is the cardholder name exposed? |
| Cardholder phone | in/not in | ”Regex list” | Does the cardholder phone number contain certain numbers (can be expressed as a regular expression)? |
| Cardholder phone | is/is not | ”Exposed” | Is the cardholder phone number exposed? |
| Card PIN number | in/not in | ”Regex list” | Does the card PIN number match a phrase (can be expressed as a regular expression)? |
| Card price | =, !=, >=, <=, >, < | Type an integer | Does the card sale offer price match a certain price? |
| Card service code | in/not in | ”Regex list” | Does the card CVV match a phrase (can be expressed as a regular expression)? |
| Card service level | in/not in | ”Select service level” | Does the card have a specific service level, such as business or student? |
| Card type | in/not in | ”Select card brand” | Is the card from a specific issuer, such as Mastercard or Visa? |
| Source name | in/not in | ”Select source” | Was the card found in a specific store? |
| Strong identifier | is/is not | ”Exposed” | Does the card contain exposed strong identification details? |
| Track | is/is not | ”Select track information” | Does the card contain information from specific magnetic tracks? |
| Transaction type | is/is not | ”Select transfer type” | Is the card of a specific transaction type? |
Credit cards for sale - default rule
The following table lists the rules that are provided to get you started quickly.
| Rule name | Description of match | Default state |
|---|---|---|
| Credit Cards for Sale - Default Detection Rule | A credit card for sale was found with an exposed strong identifier. | Enabled |
Bot data for sale
Bot data for sale - conditions
| Features | Operator | Value | Description |
|---|---|---|---|
| Detection algorithm | Identified/did not identify | Botnet credentials offered for sale | Did the detection algorithm identify relevant bot data for sale on the dark web? |
| Asset tags | in/not in | Select tags | Are any of the threat’s matched assets tagged with any of the specified tags? |
| Bot price | =, !=, >=, <=, >, < | Type an integer between 0 and 1000 | Does the bot price match a specified price? |
| Browser | contains/does not contain | ”regex list” | Does the infected user use a browser that contains a specific pattern (can be expressed as a regex list)? |
| in multiple/not in multiple | All existing options | Does the infected user use a specific browser? | |
| Days since bot installation | =, !=, >=, <=, >, < | Type an integer between 0 and 1000 | How many days ago was this bot installed? |
| Host URL | contains/does not contain | ”regex list” | Does the host URL contain a specific pattern (can be expressed as a regex list)? |
| Internal identifier | in multiple/not in multiple | List of all possibilities | Does the host URL contain compromised credentials for a possible internal host? |
| Matched asset | in multiple/not in multiple | ”Brand names” | Does the host URL contain a brand name asset? |
| in multiple/not in multiple | ”Company names” | Does the host URL contain a company name asset? | |
| in multiple/not in multiple | ”Domains” | Does the host URL contain a domain name asset? | |
| in multiple/not in multiple | ”External IP addresses” | Does the host URL contain an IP address asset? | |
| in multiple/not in multiple | ”Login pages” | Does the host URL contain a login page asset? | |
| Operating system | contains/does not contain | ”regex list” | Does the infected user use an operating system that contains a specific pattern (can be expressed as a regex list)? |
| Operating system | in multiple/not in multiple | All existing options | Does the infected user use a specific operating system? |
| Password after purchase | is/is not | Available | Do the credentials that are offered for sale contain a password that is available after purchase? |
| Relevant credentials (amount) | =, !=, >=, <=, >, < | Type an integer between 0 and 1000. | What is the amount of relevant credentials in this bot? |
| Username after purchase | is/is not | Available | Do the credentials that are offered for sale contain a username that is available after purchase? |
Bot data for sale - default rule
| Rule name | Description of match | Default state |
|---|---|---|
| Bot Data for Sale - Default Detection Rule | A bot data for sale was found with an exposed strong identifier | Enabled |
Black markets
Black markets - conditions The following table describes the conditions that you can use to create rules. When using a regular expression, don’t surround the expression with quotation marks.
| Features | Operator | Value | Description |
|---|---|---|---|
| Detection algorithm | identified/did not identify | Black Markets | Did the detection algorithm identify relevant products for sale on the dark web? |
| Asset tags | in/not in | Select tags | Are any of the threat’s matched assets tagged with any of the specified tags? |
| Days since product published | =, !=, >=, <=, >, < | Type an integer between 0 and 1000. | How many days ago was this product published? |
| Matched asset | in/not in | ”Brand names” | Does the product name or description contain a specified Brand name asset? |
| Matched asset | in/not in | ”Company names” | Does the product name or description contain a specified Company name asset? |
| Matched asset | in/not in | ”Domains” | Does the product name or the product description contain a domain name asset? |
| Price | =, !=, >=, <=, >, < | Type a value. | Does the price for the product match a specified price? |
| Price | is/is not | at auction | Is the product offered for sale at auction? |
| Product description | contains/does not contain | ”Regex list” | Does the product description contain a specific pattern (can be expressed as a regex list)? |
| Product name | contains/does not contain | ”Regex list” | Does the product name contain a specific pattern (can be expressed as a regex list)? |
| Product type | contains/does not contain | ”Regex list” | Does the product type contain a specific pattern (can be expressed as a regex list)? |
| Product type | in/not in | Product types | Does the product type match selected options? |
| Seller | contains/does not contain | ”Regex list” | Does the seller of the product contain a specific pattern (can be expressed as a regex list)? |
| Source name | in/not in | Sources List | Does the source of the published product match a specified value? |
Black markets - default rule
| Rule name | Description of match | Default state |
|---|---|---|
| Black Markets - Default Detection Rule | A company-related product was found to be sold on a dark web black market. | Enabled |
Black markets Alert Profiler examples
These examples show how to use the Alert Profiler for black market threats.
Problem : The customer has a brand that is frequently targeted by threat actors, while other brands are less targeted.
Solution : Add a condition (to the Detection algorithm) that alerts only on products that contain the targeted asset.
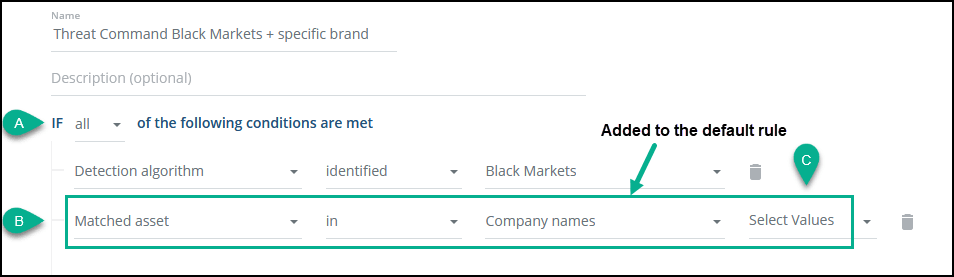
Customize alert triggering with the Alert profiler :
- Edit the default rule, and change the “any ” to “all.”
- Add the Matched asset condition.
- Add the parameters to select the targeted asset.
Problem : The customer wants to be alerted only on specific product types.
Solution : Add a condition (to the Detection algorithm) that alerts only on products that belong to a defined category.

Steps :
- Edit the default rule, and change the “any ” to “all.”
- Add the Product ype condition.
- Add the parameters to define a specific type of product.