Integrate a Check Point R80.x Cloud Device
Configure a Check Point integrated security management cloud device to use the Check Point firewall to act on IOCs pulled from Digital Risk Protection (Threat Command).
The following Check Point versions and IOCs are supported:
| Version | Supported IOCs |
|---|---|
| R80.20, with hotfix_sk132193 installed | IP address, Domain, URL, and MD5 file hash |
| R80.30 | IP address, Domain, URL, and MD5 file hash |
| R80.40 | IP address, Domain, URL, and file hash (MD5, SHA1, and SHA256) |
Limitations
- Check Point device configuration is per gateway. You must configure each gateway separately, either using SSH or the console.
- The device is limited to 20,000 IOCs.
- Check Point does not support email address IOCs.
- Due to a Check Point R80.40 issue, only MD5 file-hashes are sent to the gateway.
Add a Check Point cloud device to Digital Risk Protection (Threat Command)
You can add a Check Point cloud device to Digital Risk Protection (Threat Command).
Prerequisites
- You have administrative access to Digital Risk Protection (Threat Command) with a subscription to the Automation and TIP modules.
- You must be able to provide the Digital Risk Protection (Threat Command) account ID and appliance key, as described inAPI key, account ID, and appliance key.
- You have the credentials to access the device with SSH or the console.
- The Anti-Bot and Anti-Virus blades are installed on each Check Point gateway to be configured.
To add a cloud device to Digital Risk Protection (Threat Command):
- Log in to Digital Risk Protection (Threat Command) at https://dashboard.ti.insight.rapid7.com
- From the main menu, select Automation -> Integrations.
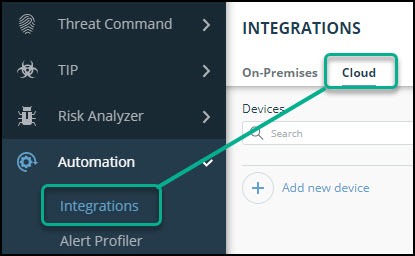
- From the Integrations page, click Cloud.
- Click Add new device **.
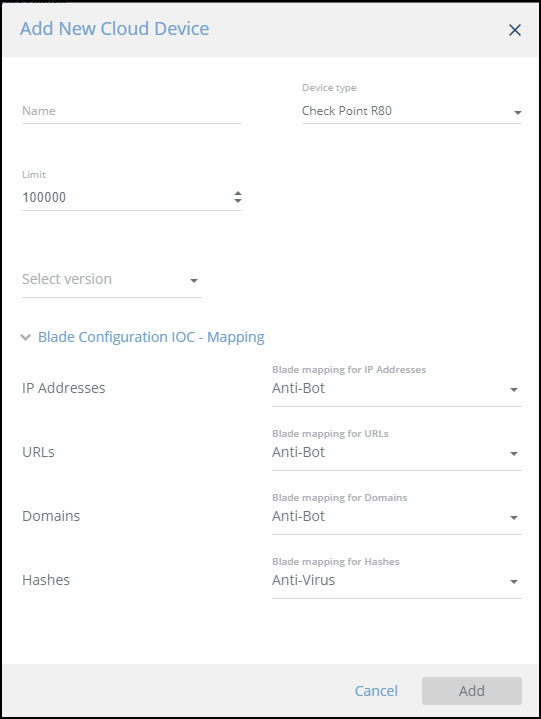
- In the Add New Cloud Device dialog, type a user-defined name for the device. The name can contain letters, spaces, numbers, and underscores.
- Select the Device type.
- (Optional) You can change the IOCs limit.
- Select the version of your Check Point Gateway: R80.40, R80.30, or R80.20.
- (Optional) Map the blade configuration for the gateway:
The default mappings are per Check Point recommendation. For more information, consult with Check Point documentation.- Click Blade Configuration IOC - Mapping.
The configuration section is displayed. - Select a blade mapping for each of the supported IOC types.
- Click Blade Configuration IOC - Mapping.
- Click Add.
- To verify that the new device is added, refresh the Automation > Integrations page.
The new device is added to the cloud integrations device list.
Configure a Check Point device to pull IOCs from Digital Risk Protection (Threat Command)
The default behavior for pulled IOCs is “Prevention.” Instead of only detecting, the configured gateway will block IOCs in the device.
When IOCs are pulled, all IOCs that are present are pulled.
Prerequisites
- Access to Digital Risk Protection (Threat Command) as an administrator.
To configure a Check Point cloud device:
- Get the Digital Risk Protection (Threat Command) Check Point Feed URL:
- From the Digital Risk Protection (Threat Command)Automation > Integrations page, click the Cloud tab,
- Select the Check Point device.
- From the top of the page, click Device Details.
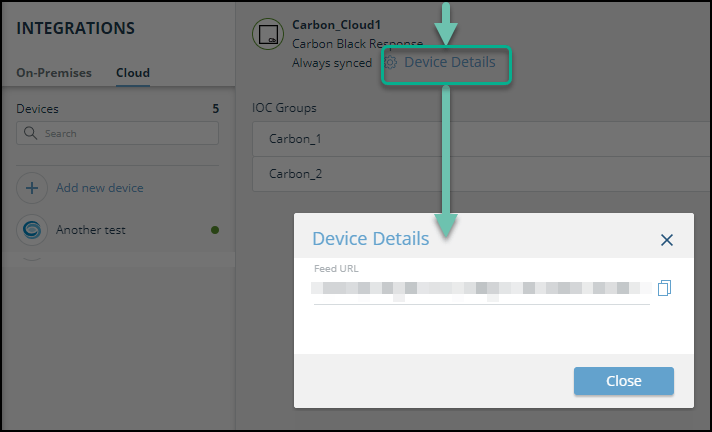
- Copy the Feed URL that is displayed.
- Log in to a Check Point gateway with SSH (or the console).
- Start expert mode.
- (Optional) Set the fetch interval for all configured feed servers. Note: This setting applies to all feed servers.
Type: ioc_feeds set_interval 3600 - (Optional) Confirm that the setting was applied:
Type: ioc_feeds show_interval - Configure the feed server from which IOCs will be pulled:
Type:<font face="Courier">ioc_feeds add --feed_name <feed_name> --transport https --resource "<device_url>" --format [type:#2,value:#1,severity:#3,product:#4,comment:#5,name:#1] --user_name <account ID> --delimiter ","Where :- feed_name is a user-defined name for the Check Point feed.
- device_url is the Feed URL from the Digital Risk Protection (Threat Command) Device Details screen.
- format is according to the following: There are five fields, delimited by ”,”. The format should map what (type, value, severity, etc.) should be taken from each field.
- user_name is the Digital Risk Protection (Threat Command) account ID
- delimiter is “,”
- feed_name is a user-defined name for the Check Point feed.
- To continue, approve the trust feed server by typing “y ” and press Enter.
- (Optional) Confirm that the feed was configured:
Type: ioc_feeds show The feed is configured.
Check Point Troubleshooting
In R80.40, you can determine when the last IOCS were pulled and also force an IOC pull from Digital Risk Protection (Threat Command) (before the scheduled time).
To determine when the last IOCS were pulled:
- Run: cat /opt/CPsuite-R80.40/fw1/log/ioc_feeder.elg
To force an IOC pull:
- Run: ioc_feeder -d -f
The IOCs are displayed.