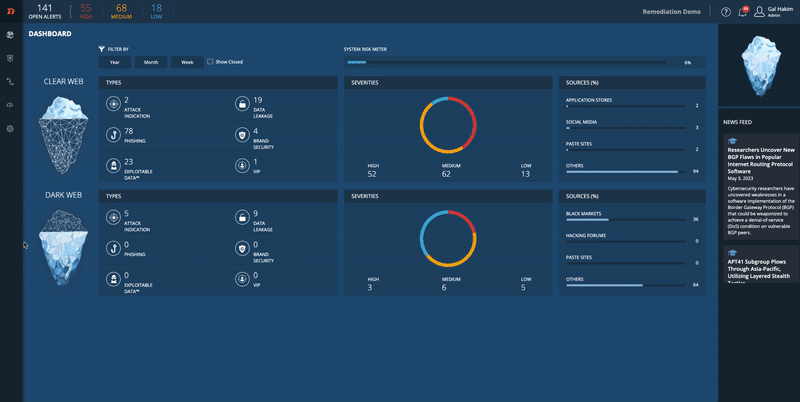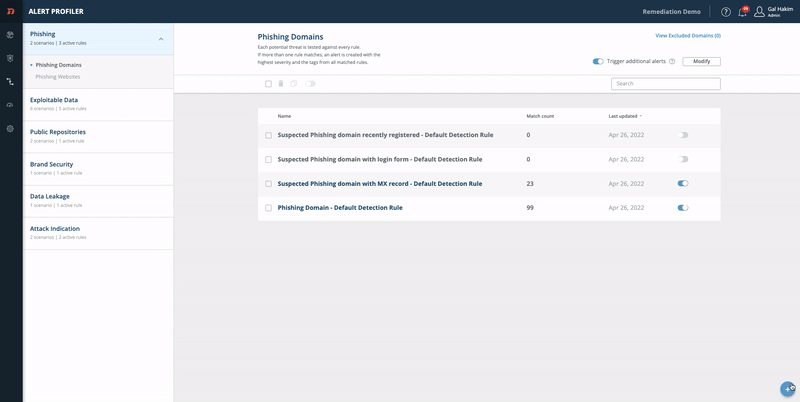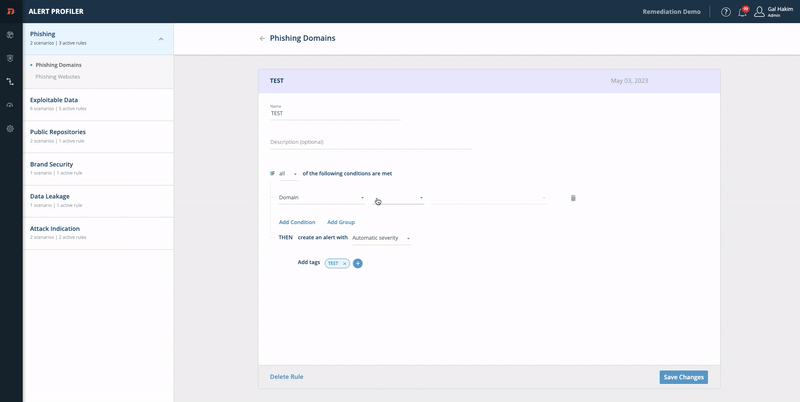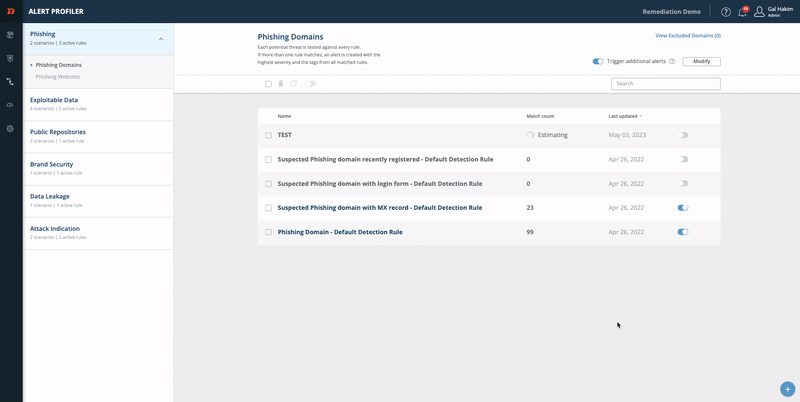
Additional Monitoring and Protection Steps
To initiate the takedown of a suspicious domain, the domain registrar requires the following evidence:
- The spam email with its original headers.
- A scan of the domain in a malware analysis tool or a malware scan hyperlink.
If our system alerts you about a suspicious domain, but you do not have the above indicators of malicious activity, we cannot move forward with a system takedown.
That said, all hope is not lost! This section outlines how to monitor suspicious domains for malicious activity, typical scenarios you may face, steps you can take to protect your organization, and, when evidence does become available, how to be prepared when it’s time to initiate a domain takedown.
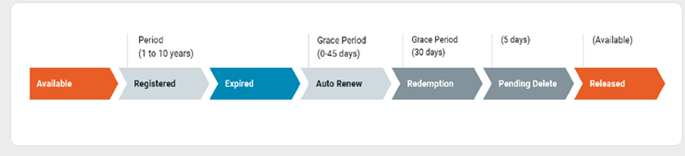
The Domain Lifecycle
Understanding the lifecycle of a domain can point to the best protection activities, which change throughout the lifecycle. In addition, at some point, the domain may turn malicious, which may enable the gathering of the evidence needed to perform a system takedown.
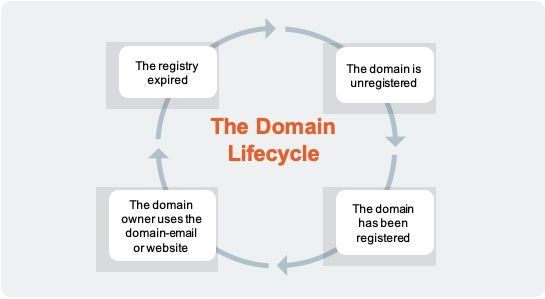
** A domain can be used for malicious activity only after it has been registered.
The following section describes the domain lifecycle.
The domain is unregistered:
-
A new domain is available for purchase.
-
The last registration has expired, and the domain is available for purchase.
-
The following example, from GoDaddy, is from a domain that was purchased (typically for one year), but it is not in use.
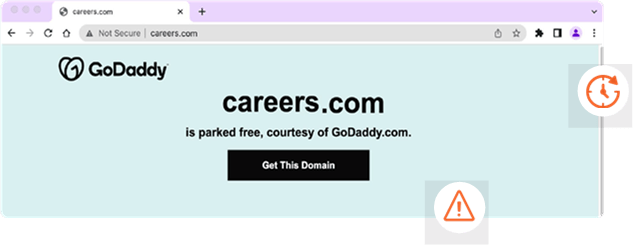
This domain is “parked” for future use and is available for purchase when the registrar or domain owner chooses to sell it.
The domain has been registered:
- A domain name is registered but is not connected to an online service (like a website or email hosting). In other words, it is a purchased domain name that is not currently in use.
The owner starts to use the domain:
- Exclusively for emails: MX records
- A website: using the hosting provider’s services
- Both: emails and website
The domain registration has expired:
- Once the registration of the domain has expired, the domain owner can renew the registration (within 35-40 days of the expiration date).
The domain is available for purchase:
- After approximately 40 additional days (total of ~75 days), the domain is again offered for purchase. When the domain has been sold as part of the agreement between the registrar and the domain owner, the registrar reserves the right to revoke the domain name as a result of illegal activity.
Only a registered domain can be used for malicious activity.
Malicious Domain Timeline
Once a domain has been registered, it may pass through several phases until it is finally malicious. The following diagram shows the preventative measures that can be taken during each of the stages. Each preventative measure is described in full later in this topic.
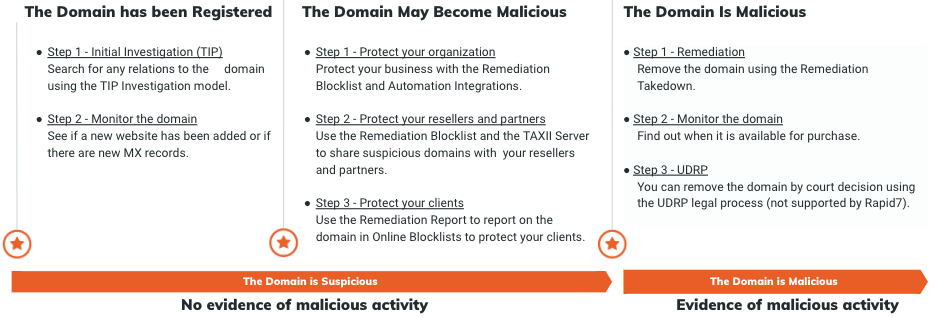
The Domain has been Registered
If the domain is registered and there is no indication of malicious activity, you can:
Step 1 - Conduct a TIP Investigation
Find out if there is any relation between the domain and potentially malicious activity. The TIP Investigation* feature reveals any connections between the domain and other IPs, CVEs, APTs, and more. It is possible that these findings will lead to evidence that the domain is associated with malicious activity (although it is important to note that these findings are not always relevant). See the TIP Investigation Short Guide for more information.
License required.
Step 2 - Monitor the Domain with the Alert Profiler
Monitor the domain to find out when something in the domain character has changed. Use the Alert Profiler to configure it to push a new alert when the domain has new MX records or is hosting a website. See the Alert Profiler (MX records and website) Short Guide for more information.
Step 3 - Purchase the Domain
If the domain is already registered, ask the registrar if you can offer a price and buy the domain, or use online services for negotiation (for example, Domain Name Aftermarket by GoDaddy).
**This service is not provided by Rapid7.
The Domain May Become Malicious
If the domain is registered and there is no indication of malicious activity, but it uses your company’s name and has the potential to become malicious, you can:
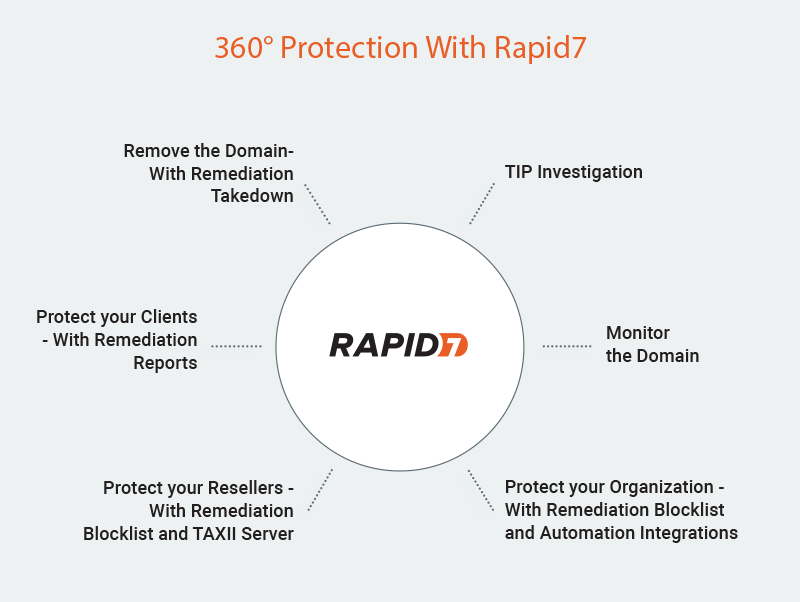
Step 1 - Protect Your Organization Using Blocklist Remediation
To protect your organization from a suspicious domain, you can use our out-of- the-box integrations to security devices. With these integrations, you can define and configure your defense devices (for example SIEM, web proxy, etc.) to block or monitor the domain.
First, you should add the domain to your private Blocklist Remediation*. Once the domain name is in this list, you can configure your devices to work by this feed. See the Blocklist Remediation Short Guide for more information.
After you have created the Blocklist Remediation feed (and added the suspicious domain), configure your defense devices to work with it. See the Automation Integrations Short Guide for more information.
*License required.
Step 2 - Protect Your Resellers using TAXII
To protect your resellers from the suspicious domain, you can use the built-in TAXII Server*. A TAXII (Trusted Automated eXchange of Indicator Information) server is a community-driven technical specification designed to enable automated information sharing for cybersecurity situational awareness, real-time network defense, and sophisticated threat analysis. It defines a set of services and message exchanges that, when implemented, enable sharing of actionable cyber threat information such as malicious and suspicious domains to protect your partners and resellers. As a result, your partners and resellers can block or monitor access to the domain from their own networks.
After you create the Blocklist Remediation feed (and add the suspicious domain), configure the TAXII Server to work with it. See the TAXII Server Short Guide for more information.
*License required.
Step 3 - Protect Your Clients using Online Blocklists
In some cases, an attack is aimed at your rather than directly at your organization. One way to protect your clients from a suspicious domain is to report the domain to online blocklists like PhishTank and Google Safe Browsing . Both will warn users about the domain. For example:
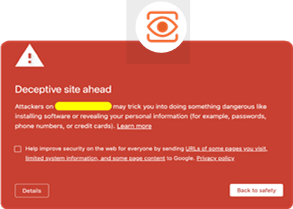
This only works if there is evidence of malicious activity, otherwise it wouldn’t be blocked.
To easily report on the domain, use the Remediation Report*. See the Remediation Report Short Guide for more information.
*License required.
The Domain Is Malicious
If the domain is registered and there is evidence of malicious activity associated with it, you can:
Step 1 - Initiate a Takedown with Rapid7 (Remediation)
Click on the Remediate button to initiate the takedown process*.
Again, the domain registrar requires:
- The original phishing email that was sent by the reported domain, including the full email headers. The original email is necessary because the email headers prove the reported domain was sent via the email.
- A malware analysis report that indicates malicious activity (VirusTotal or URL Scan, for example).
Domain registrars may require the original phishing email in some cases since malware analysis is not sufficient evidence.
*License required.
Step 2 - Monitor the Domain Status
After a successful Remediation Takedown, the domain status usually changes to ClientHold. This status means the domain has been blocked due to illegal activity. There is a Renewal Grace Period (RGP) that varies from 30-75 days based on the domain extension and registrar. See the Alert Profiler (Domain Status) Short Guide for more information.
If you are interested in purchasing the domain, you can monitor its status with Alert Profiler to check expiration and availability to purchase. See the Alert Profiler (MX records and website) Short Guide for more information.
Step 3 - UDRP (Not Provided By Rapid7)
UDRP (Uniform Domain Name Dispute Resolution) is a policy that all registrars must follow. It is a trademark-based domain-name dispute that is resolved by agreement, court action, or arbitration before a registrar will cancel, suspend, or transfer a domain name to adjudicate domain name disputes between trademark holders and bad faith registrants of domain names.
To invoke the policy, a trademark owner should:
- File a complaint in a court of proper jurisdiction against the domain-name holder.
- Submit a complaint (~60 pages) to an approved dispute-resolution service provider.
According to WIPO , It usually takes about two months to solve the issue, and the cost is approximately $5K (not including legal fees). See the WIPO Guide to the UDRP for more information.
Short Guides
This section gives a quick guide to how to perform several preventative measures against suspicious and malicious domains.
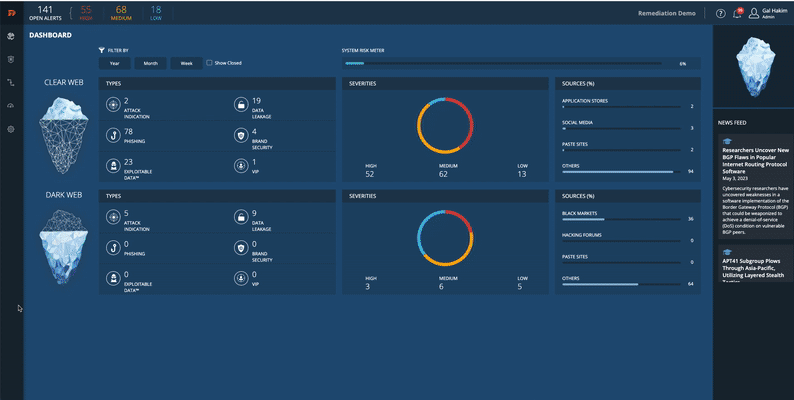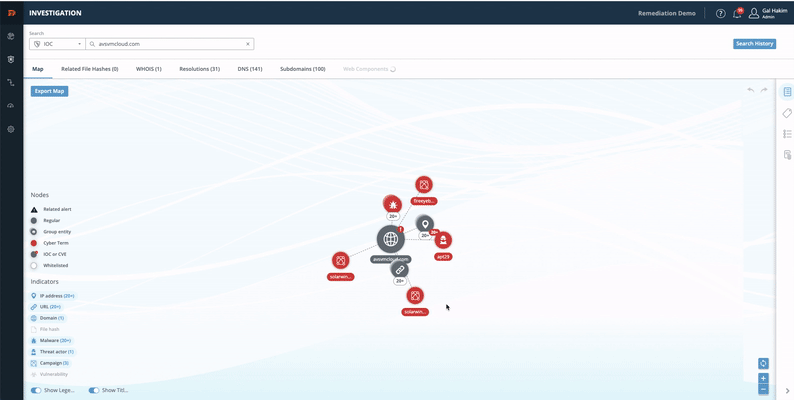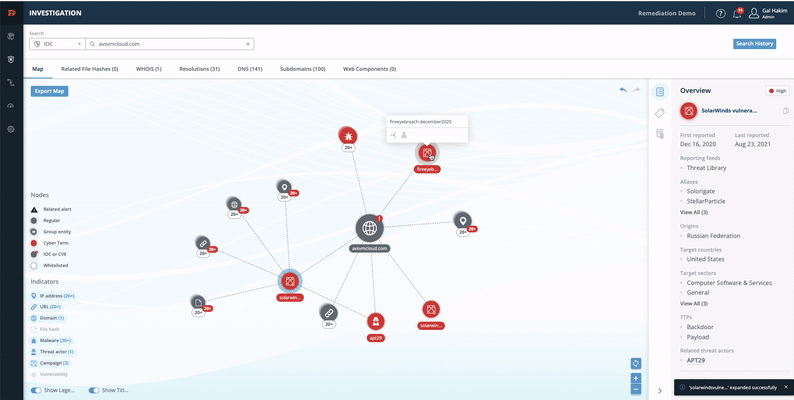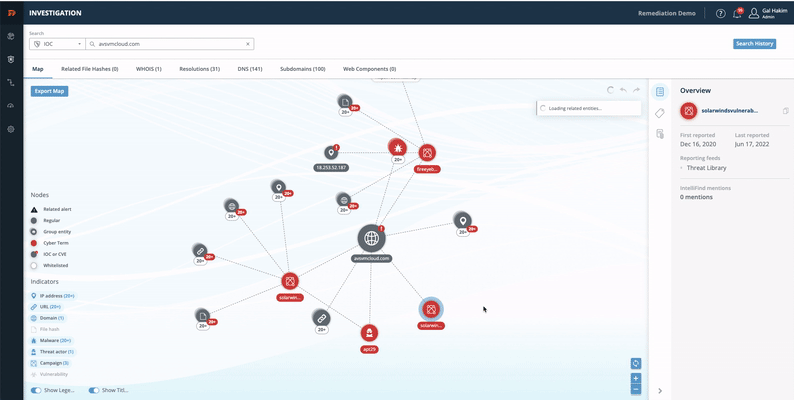
TIP Investigation
- From the Digital Risk Protection (Threat Command) Dashboard main menu, choose TIP > Investigation.
- In the search bar, select IOC, type the domain name, then press Enter.
The Investigation page contains all IP addresses, CVEs, APTs, and more that are related to this domain (malicious components are highlighted in red).
See the complete guide: Investigation.
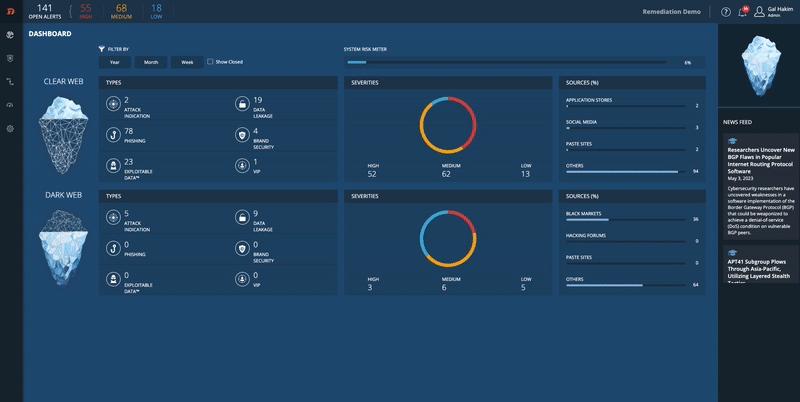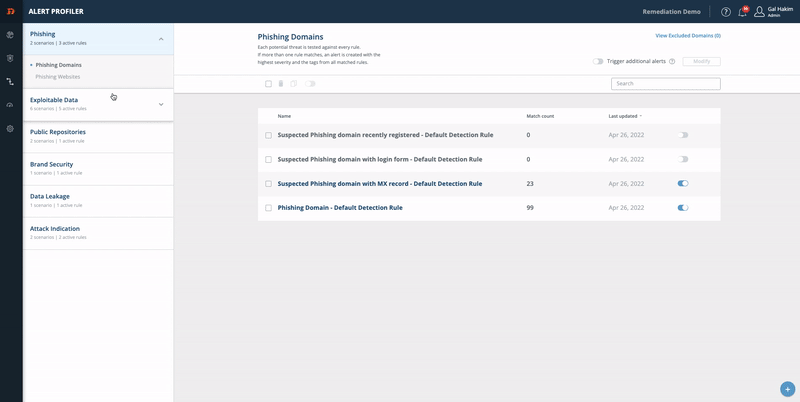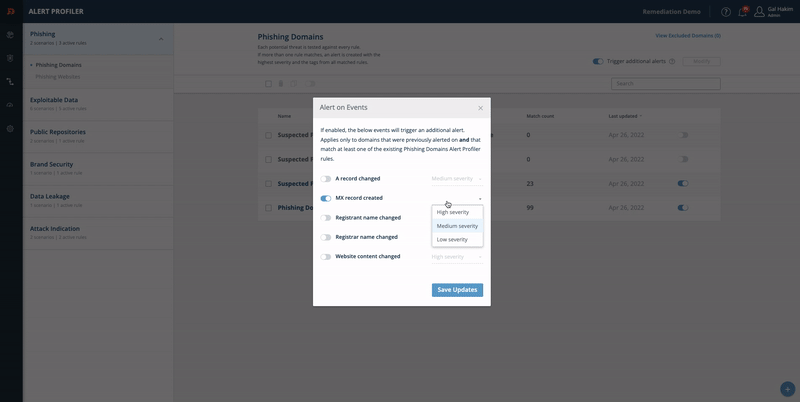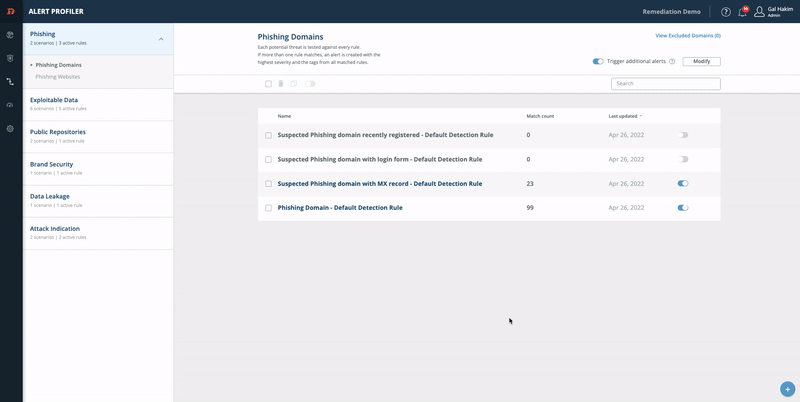
Alert Profiler: MX Records and Website
Enable receiving a new alert when the domain has new MX records or when a website is hosted.
-
From the Digital Risk Protection (Threat Command) Dashboard main menu, choose Automation > Alert Profiler.
-
Select the Phishing section.
-
On the right top of the screen, turn on Trigger additional alerts.
-
Click Modify.
-
Turn on MX record created and select a desired severity.
-
Turn on Website content changed and select a desired severity.
-
Click Save Updates.
Now, when the domain has new MX records or a website is hosted, you will get a new alert.
See the complete guide: Creating Alerts from Events.
Blocklist Remediation
To add the domain to your Blocklist Remediation feed:
- From the Digital Risk Protection (Threat Command) Dashboard main menu, choose Alerts.
- Select a specific alert.
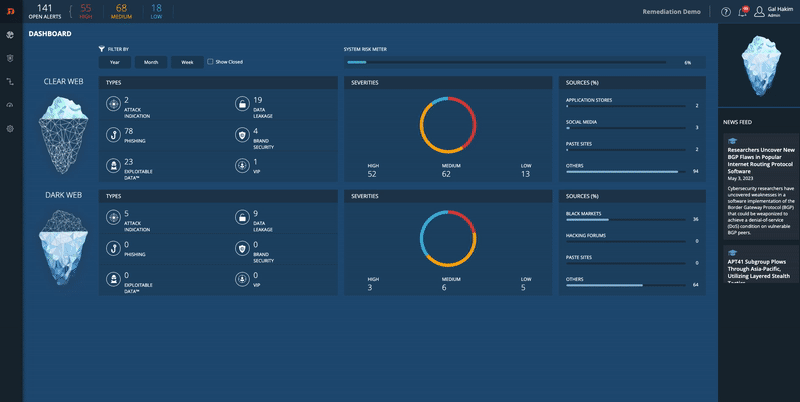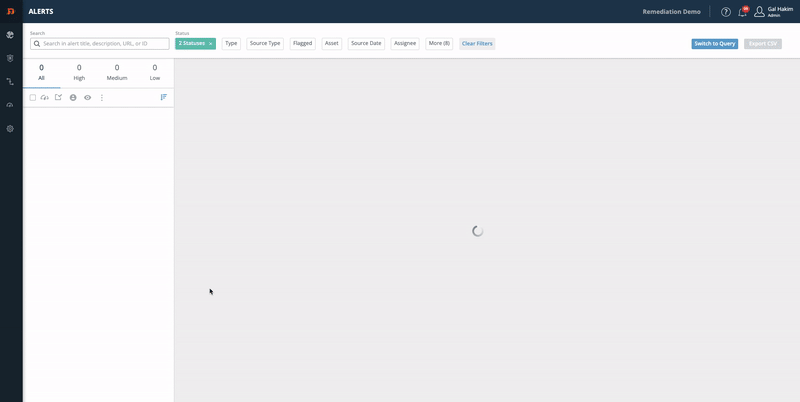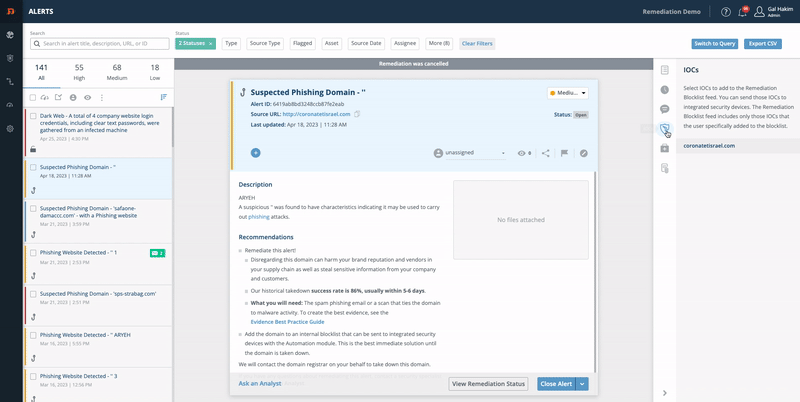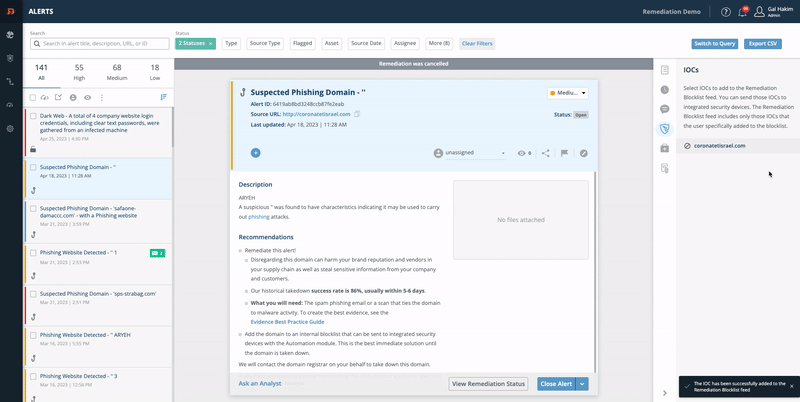
- From the right-side menu, click IOCs:
- Click the IOCs icon on the right:

- Click Add to blocklist feed.
Now the domain is in your personal Remediation Blocklist feed.
See the complete guide - Blocklist Remediation.
Automation Integrations
Integrate a security device: add a device, configure an IOC group, and enter device details.
Step 1 - Add a device.
- From the Digital Risk Protection (Threat Command) Dashboard main menu, chooseAutomation > Integrations.
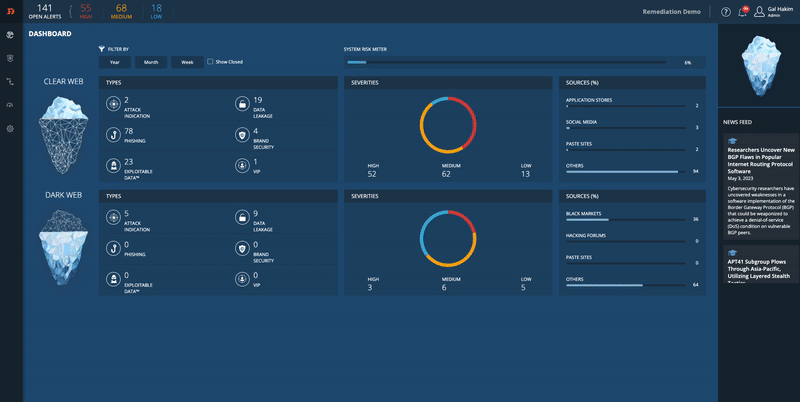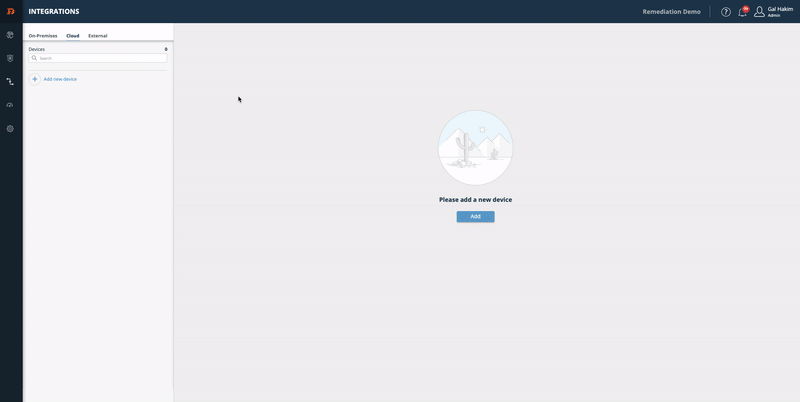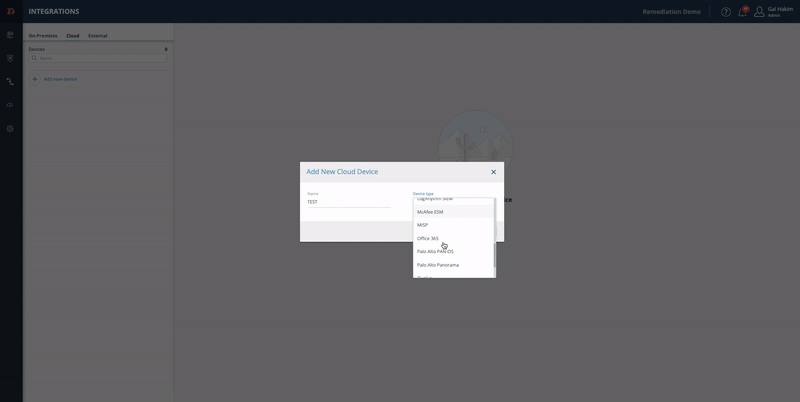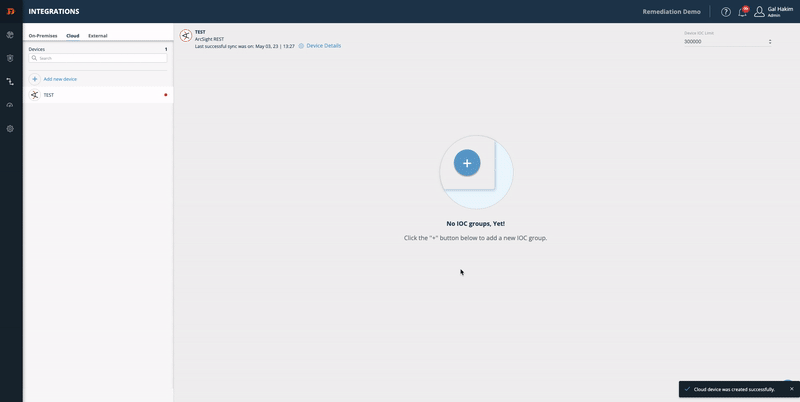
- Choose your device type: On-Premise orCloud.
- Click Add.
- Fill in your device info and click Add.
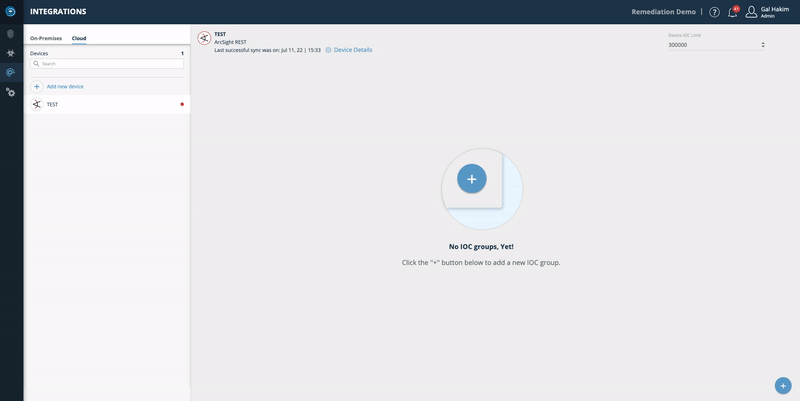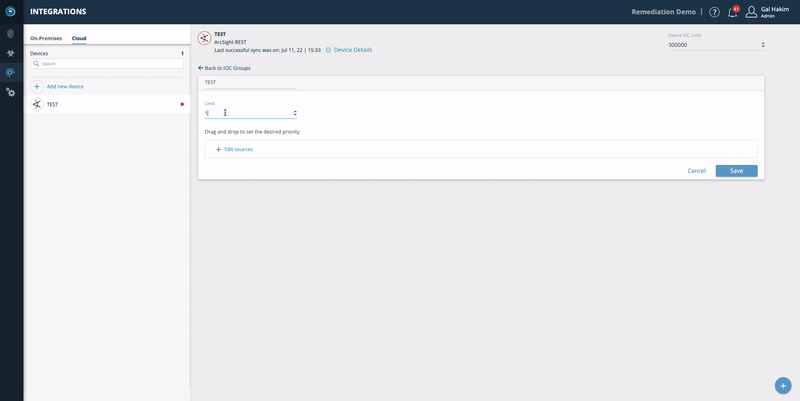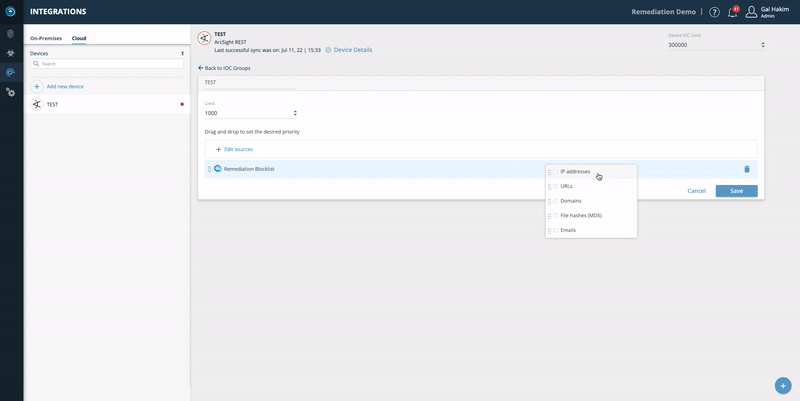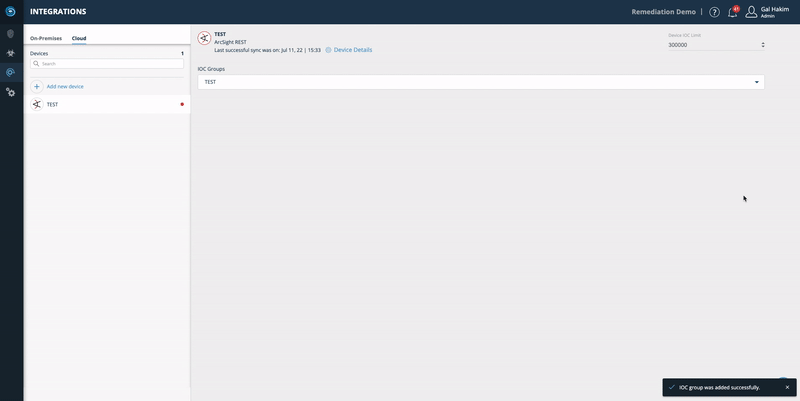
Step 2 - configure an IOC group:
- From the Digital Risk Protection (Threat Command) Integrations page, select the device.
- On the device, click the + button.
- Enter an IOC group name.
- Define the limit.
- To add the source, click Edit Sources.
- Choose the feed (for example, Remediation Blocklist) and click Add.
- Choose the IOC type: IP addresses, URLs, Domains, File hashes, and Emails. You can drag them to choose the desired priority.
- Click Save.
Copy the relevant URL and paste it into your device:
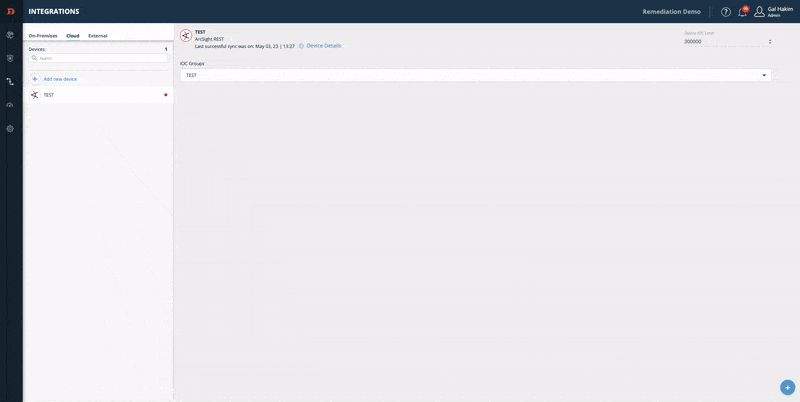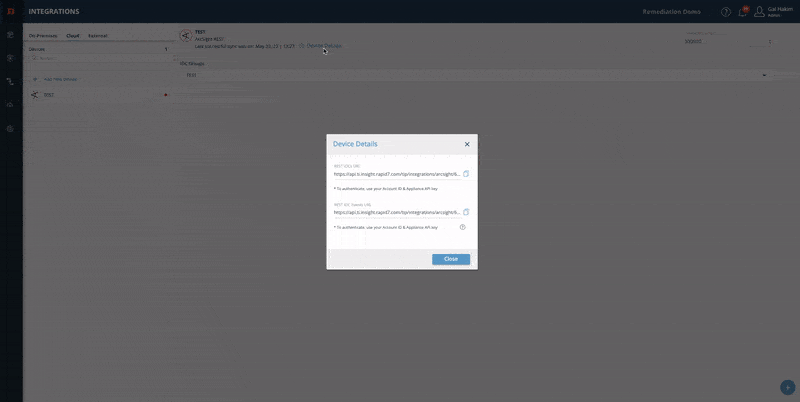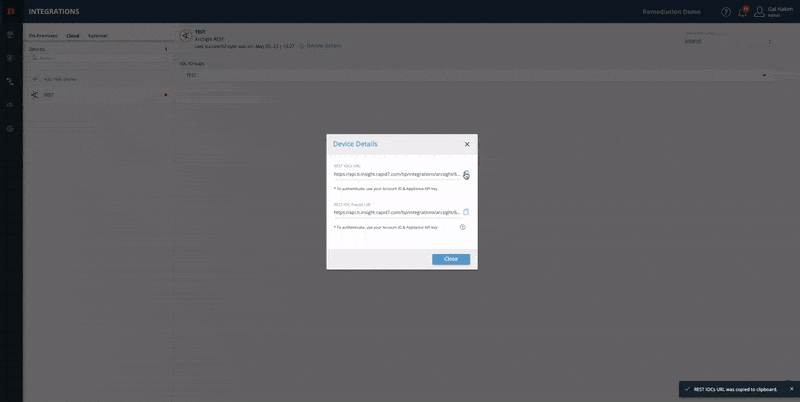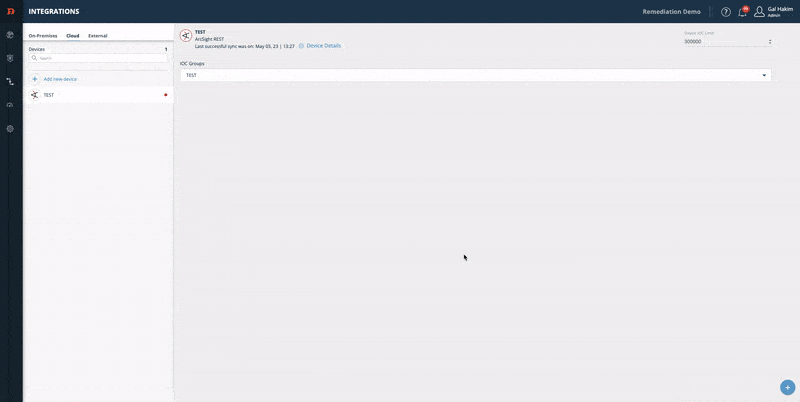
See the complete guide: Integrating Devices
TAXII Server
Integrate a TAXII server: add a TAXII server device, configure an IOC group, and enter device details.
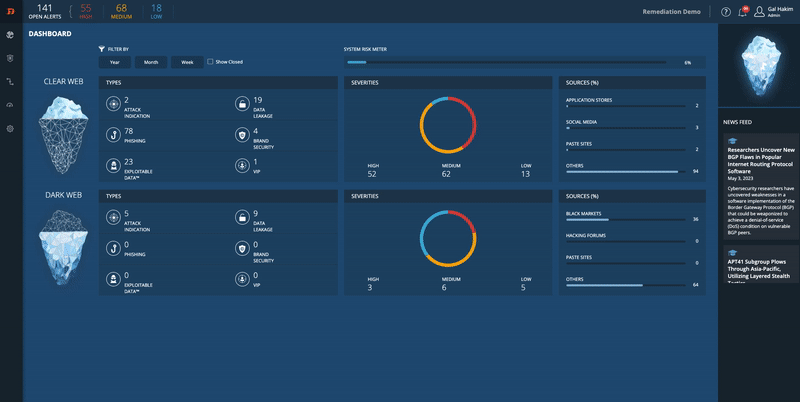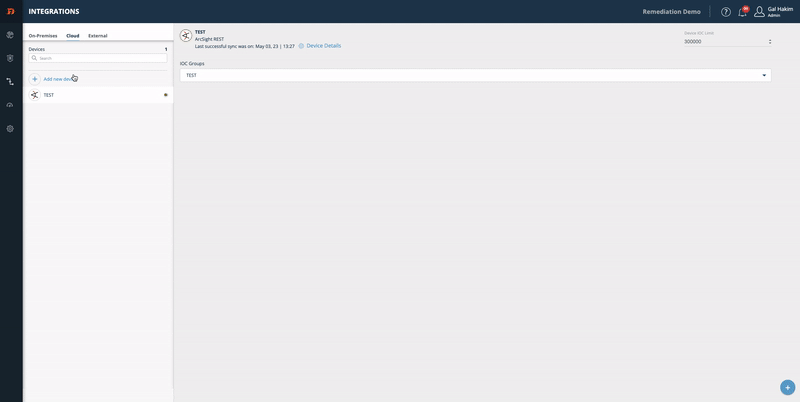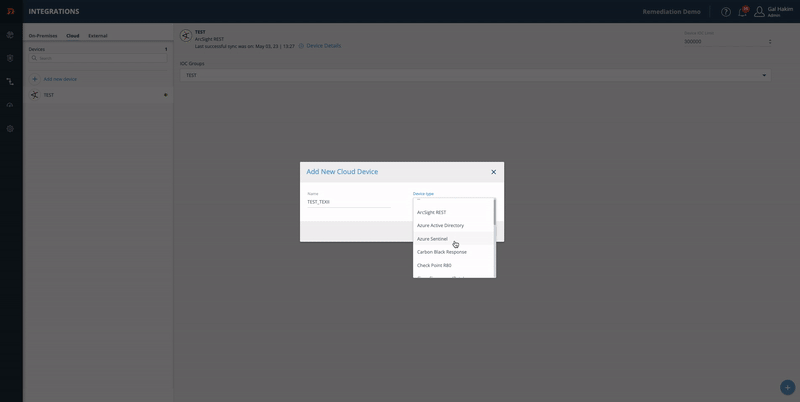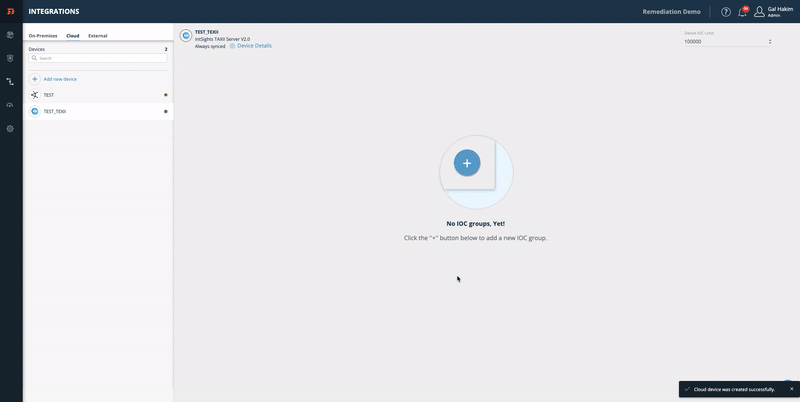
Step 1 - Add a TAXII server device:
- From the Digital Risk Protection (Threat Command) Dashboard main menu, choose Automation > Integrations.
- Choose your device type: Cloud.
- Click Add.
- Fill in your device info. For Device Type, chooseRapid7 TAXII Server.
- Select a version.
- Click Add.
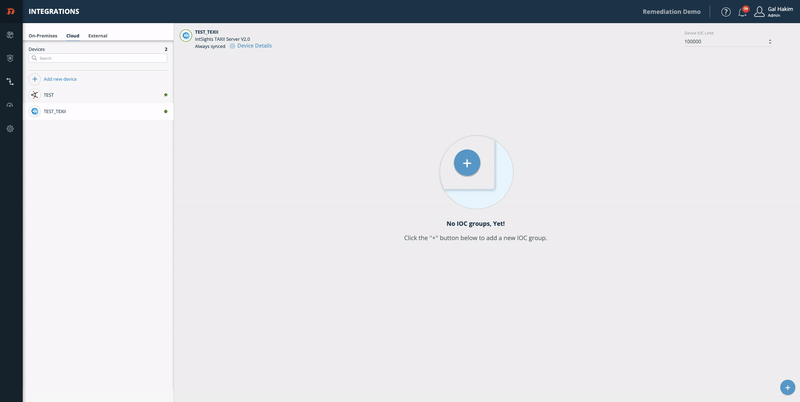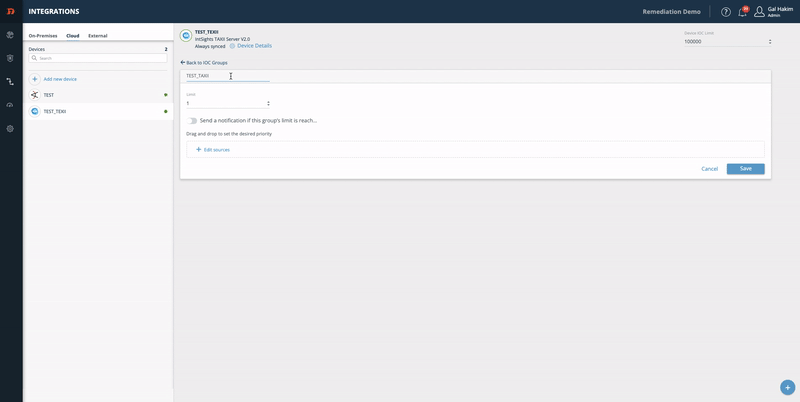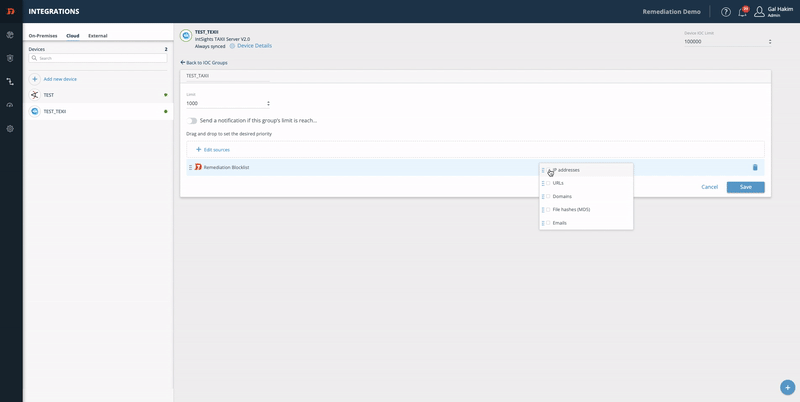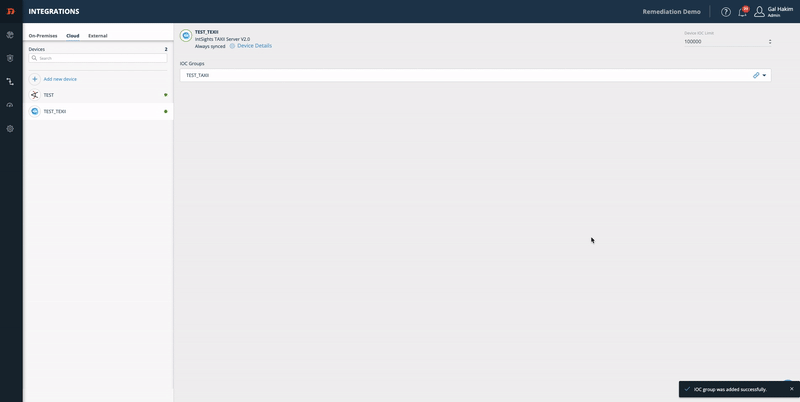
Step 2 - configure an IOC group:
- From the Digital Risk Protection (Threat Command) Integrations page, select the device.
- On the device, click the**+** button.
- Enter an IOC group name.
- Define the limit.
- To add the source, click Edit sources.
- Choose the feed (for example, the Remediation Blocklist) and click Add.
- Choose the IOC type: IP addresses, URLs, Domains, File hashes, and Emails. You can drag them to choose the desired priority.
- Click Save.
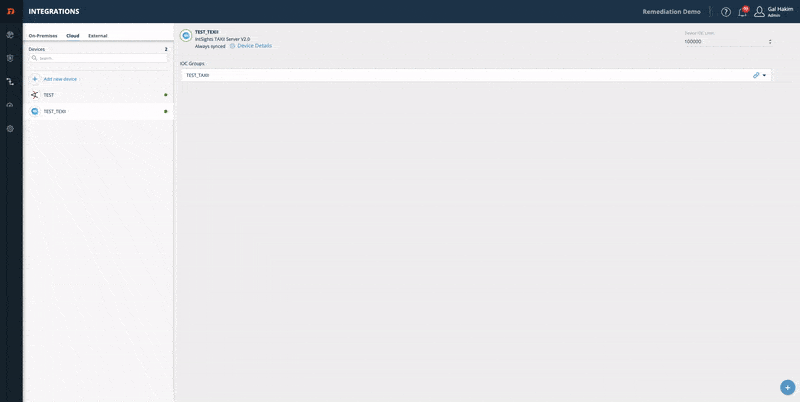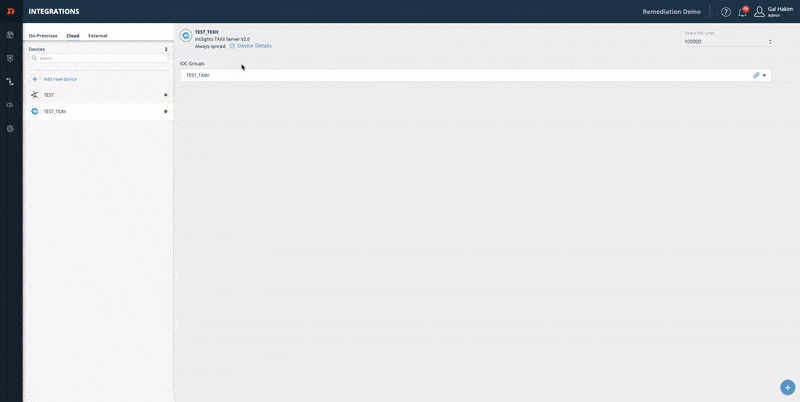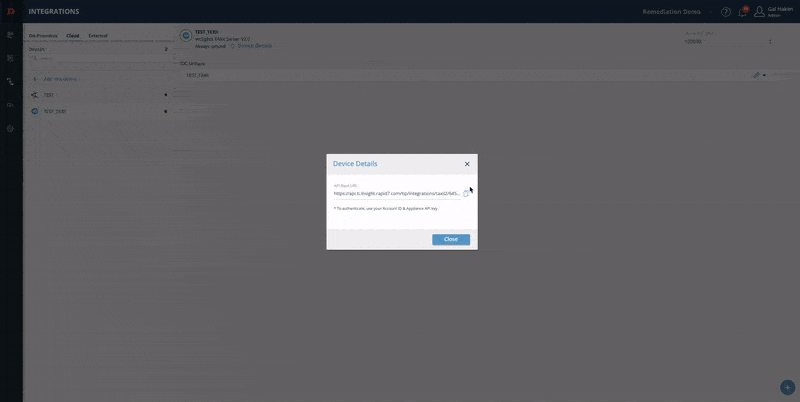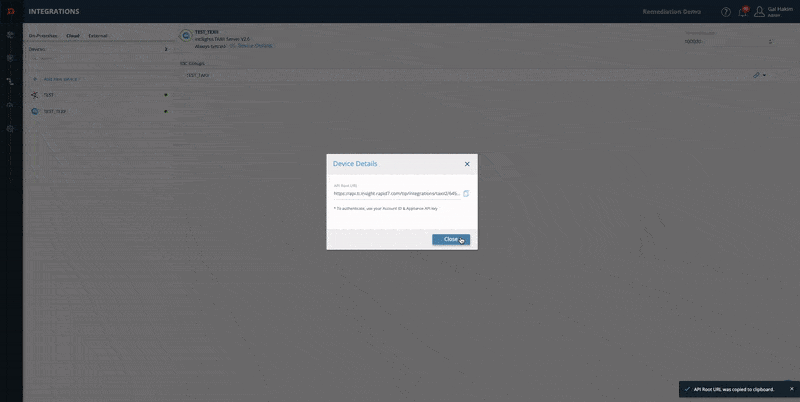
Step 3 - copy and paste the Device Details:
- From the Digital Risk Protection (Threat Command) Integrations page, select the device.
- On the device, click Device Details.
- Copy the relevant URL and paste it into your device.
See the complete guide: TAXII server
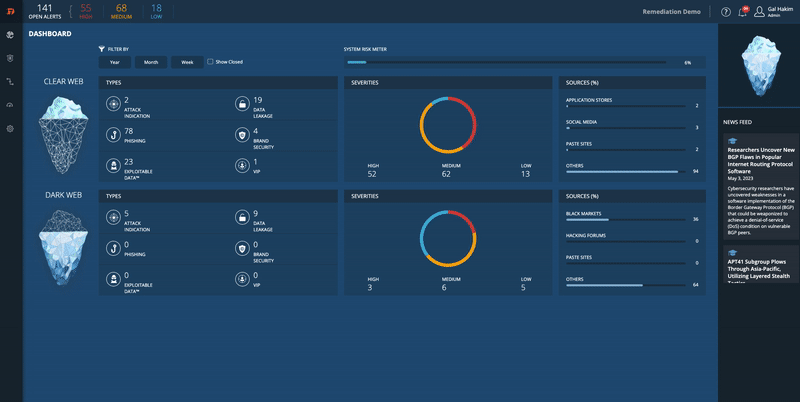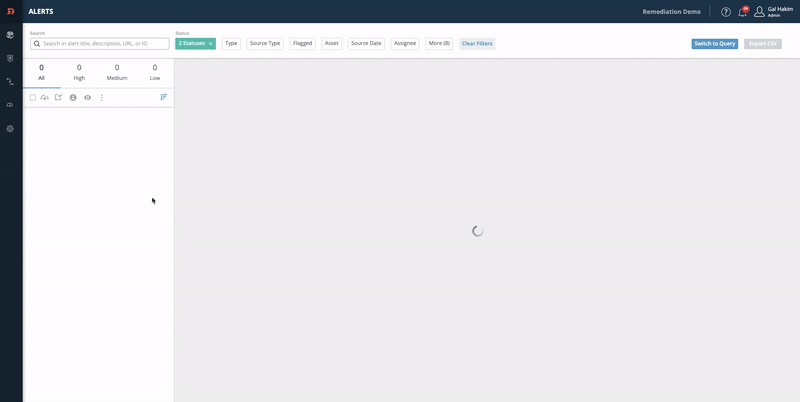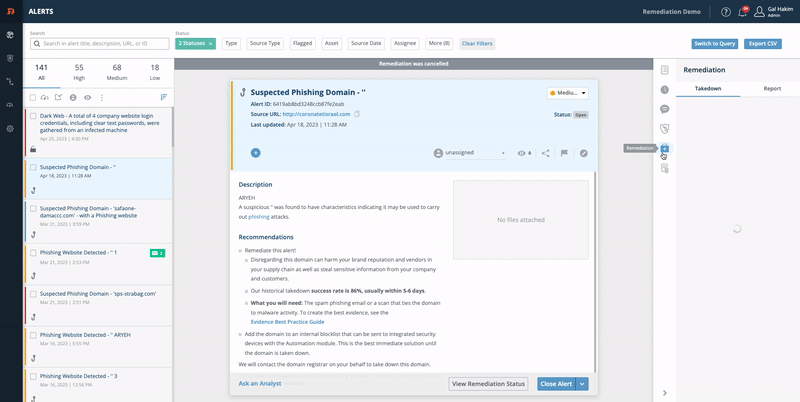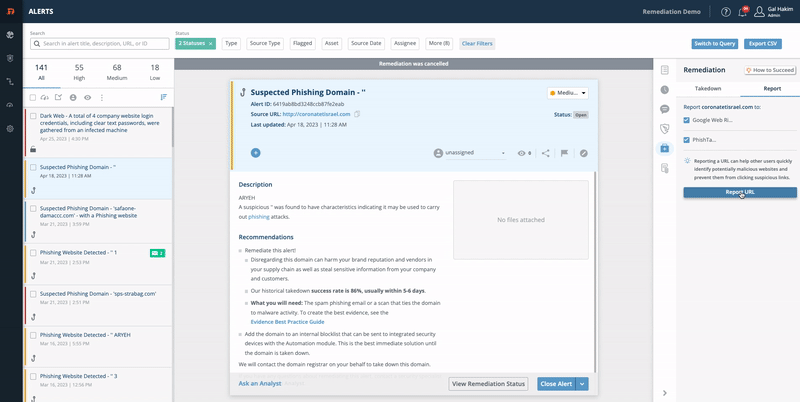
Remediation Report
- From the Digital Risk Protection (Threat Command) Dashboard main menu, choose Alerts.
- Select a specific alert.
- From the right-side menu, click Remediation :
- Click the Report tab and click Report URL :
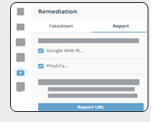
See the complete guide: Report to Google Web Risk or to PhishTank.
Alert Profiler: Domain Status
- From the Digital Risk Protection (Threat Command) Dashboard main menu, choose Automation > Alert Profiler.
- Select the Phishing section.
- At the bottom-right of the page, click the + icon.
- Enter a rule name, for example: Domain has expired
- Enter the following conditions:
- “IF all of the following conditions are met”
- Click Add Condition:
- Select Feature = “Domain”
- Select Operator = “is”
- Select Value = “Expired ”:
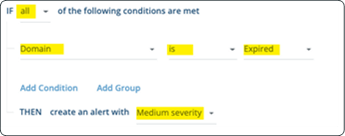
- Choose the desired severity.
- Click Save Changes.
Now, when the domain status has changed to Expired, you will get a new alert. See the complete guide: Phishing Scenario Rule Conditions.