Splunk Standalone (without ES)
In order to successfully integrate with the device make sure to complete:
- Step 1 - Add device to the appliance For device using ‘Pull’ mode don’t forget to copy the IOC group URL
- Step 2 - Creating automation rules
In this integration, the virtual appliance can send:
- Threat Indicators
- Tailored intelligence alerts
| Pushing alerts applies to both standalone version and Enterprise Security version, though it’s only used through the standalone data inputs. |
|---|
This integration supports the Digital Risk Protection (Threat Command) virtual appliance for versions earlier than 6.2.0. We recommend using the IntSights App for Splunk.
Due to the version limitations, if this integration is enabled, you cannot upgrade the virtual appliance to v6.2.0 or later. To upgrade the virtual appliance, disable this integration. We recommend using the IntSights App for Splunk.
Prerequisites
Create a hidden Splunk app and pushes IOCs.
Execute a setup script required for the Splunk standalone installation.
Ensure that port 8089 is available.
Follow the instructions here: https://gist.github.com/hozez/917089bd9afe237b33d5f9d7601345b5
Once you have added Splunk to the appliance integrations, you will see the IOC app in the list of apps.

Tailored intelligence alerts
Background
Pushing alerts to Splunk is done vis the HEC (HTTP Event Collector). Before you add the Splunk to the Virtual appliance or if you are using an existing integration make sure to generate a HEC token as described below
Prerequisites
Create an HEC token
To push Digital Risk Protection (Threat Command) alerts with HEC, ensure that port 8088/TCP is available.
Integrate Splunk to the virtual appliance (or add the HEC Token to an existing integration)
Enable Alerts pushing in the Splunk instance in the cloud platform

What is HEC (HTTP Event Collector)?
The Splunk HTTP Event Collector (HEC) helps you send data to Splunk Enterprise and Splunk Cloud. HEC lets you send data, application logs, and metrics over HTTP (or HTTPS) directly to Splunk Enterprise or Splunk Cloud from your application. HEC operates with tokens, which means you do not need to embed Splunk Enterprise or Splunk Cloud credentials in your app or supporting files.
From Splunk documentation page: http://docs.splunk.com/Documentation/Splunk/latest/Data/AboutHEC
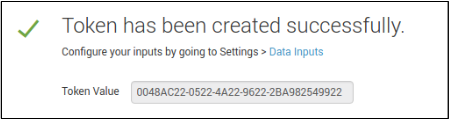
Creating a HEC token
- On splunk page, click the Settings menu, and then choose Add Data.
- Choose monitor category, and on the left menu choose HTTP Event Collector.
- Fill in the desired name of the HEC token (e.g intsights_alerts)
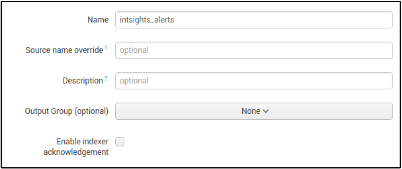
- Click Next.
- On Source Type, choose Select , filter and choose _json.
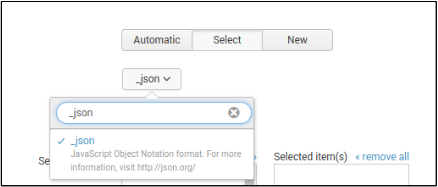
- Press Review, and Submit
- Copy the token value and use it in the Virtual appliance to add a Splunk integration or edit an existing one