View Alert Information
General alert information is shown in the Alert header and the Alert description.
The Alert banner shows information regarding the alert’s remediation status. If an alert can be remediated, the banner will show that and will present a Remediate button. If the alert is being remediated, the button will show the remediation status.
In some cases, there may be the following additional information tabs:
- Decision Parameters tab - for phishing, exposed services, and vulnerability alerts
- Credit Cards for Sale tab - for credit cards for sale alerts
- Asset Mention Details tab - for asset mentions in GitHub alerts
- Leaked Secret Details tab - for secret mentions in GitHub or GitLab repository alerts
- Matched Objects tab - for ransomware alerts
To view alert description:
- To see the alert description, select the alert in the Alerts list.
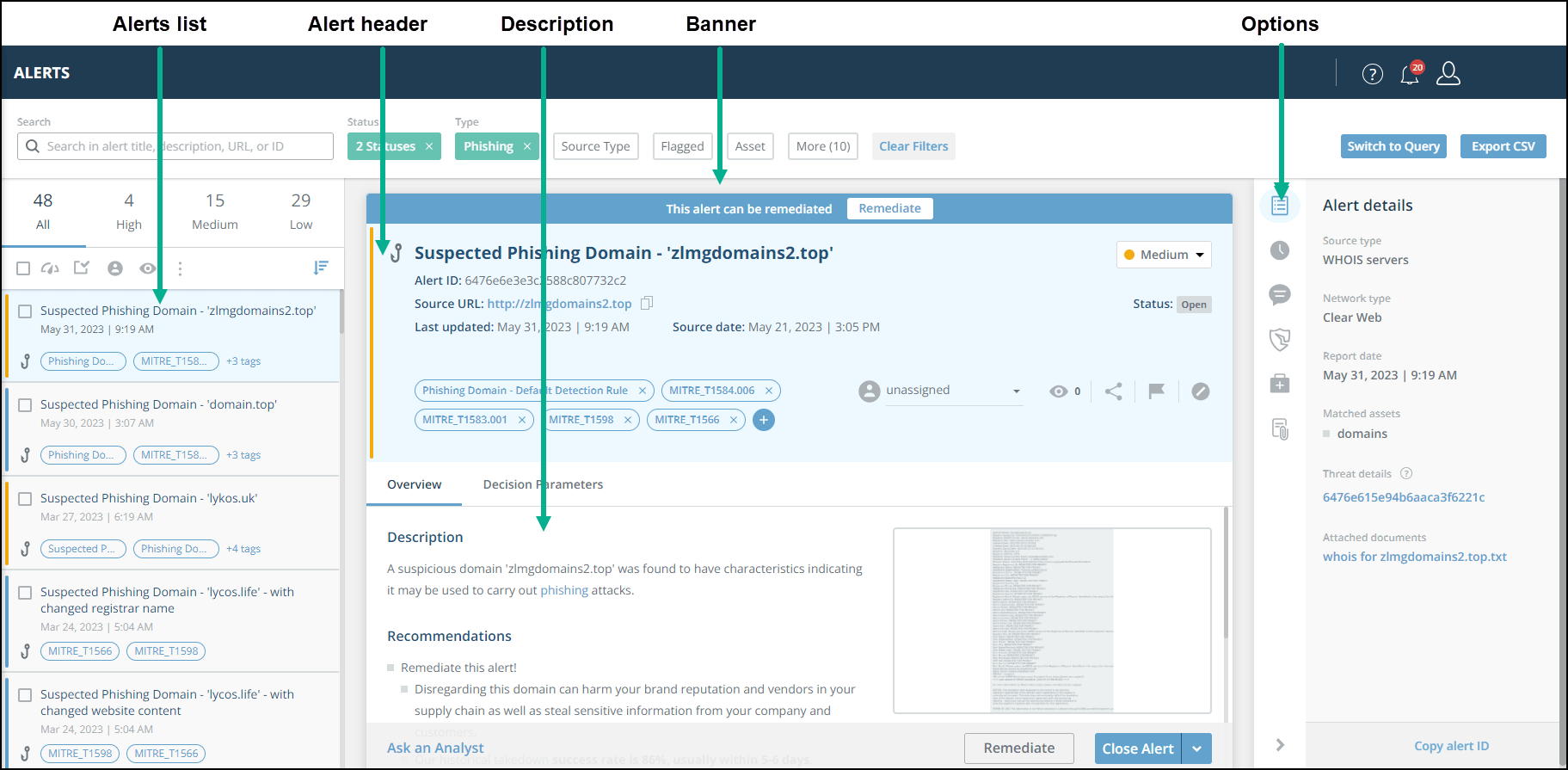
Alert header, Description, Banner, and Options pane
View Alert Decision Parameters
If the Alert Profiler is enabled, an alert is created when a threat (or a vulnerability) meets conditions defined in the Alert Profiler.
When viewing alert details you can use the Decision Parameters tab to understand why a threat was elevated to an alert. With this information, you can create or modify Alert Profiler rules to ensure that future threats are elevated (or not) as you expect.
The Decision Parameters tab is displayed for alerts from Phishing Domains, Exposed Services, Vulnerabilities, and Bot Data for Sale (only).
If an alert was generated from an event, that is shown here, too.
To view decision parameters:
- From the * Digital Risk Protection (Threat Command) > Alerts** page, select an alert.
- Select the Decision Parameters tab.
The following figure shows an alert Decision Parameters tab:
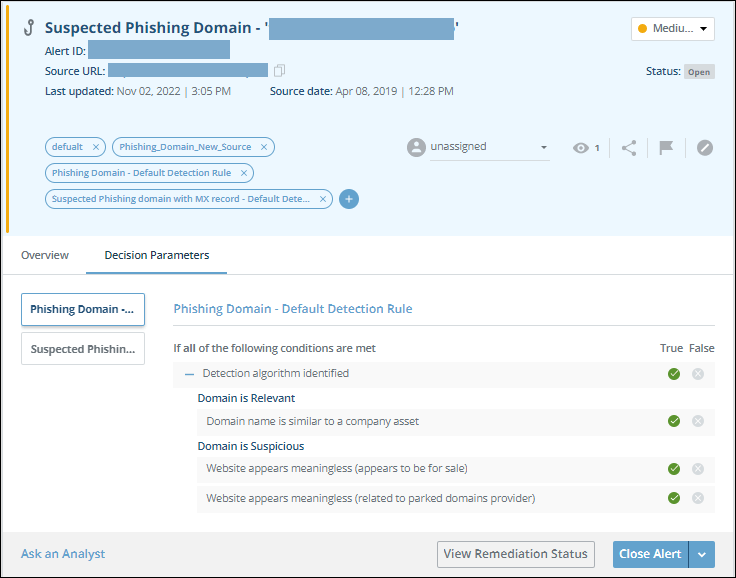
The left side of the tab shows all the rules that the threat matched. In this case, the threat matched the Phishing Domain - Default Detection Rule. (You can see the full name by hovering the pointer over the rule name.) You can select a rule to see its conditions.
For more information, see Alert Decision Parameters.
View Credit Card Details
In the Credit Card for Sale scenario, an alert is triggered when a card for sale contains a strong indicator that can help trace the original card, such as the cardholder address or phone number.
You can use the Alert Profiler to aggregate alerts, for example, all cards found for sale in a 6-hour period will generate one alert (instead of perhaps hundreds or thousands). Each of these aggregate alerts will contain the details for all of the cards found. For more information about configuring this option, see Aggregate Alerts.
Aggregate alerts are indicated in the alert Overview section, and by the presence of the Credit Card Details tab.
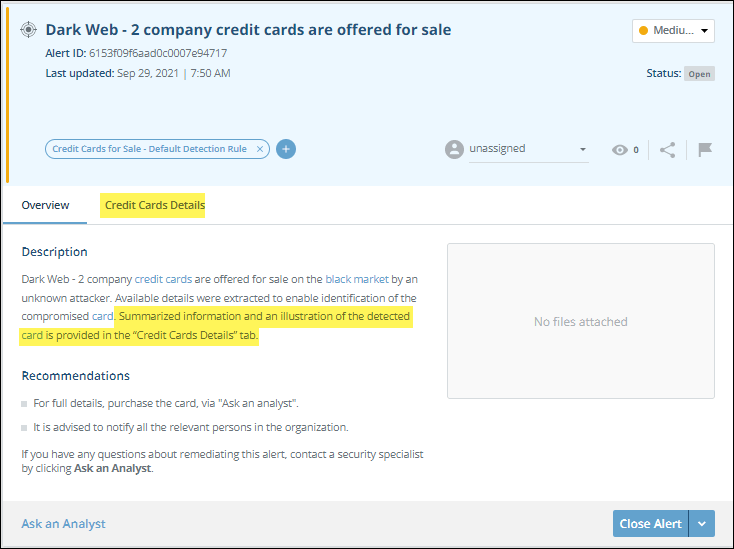
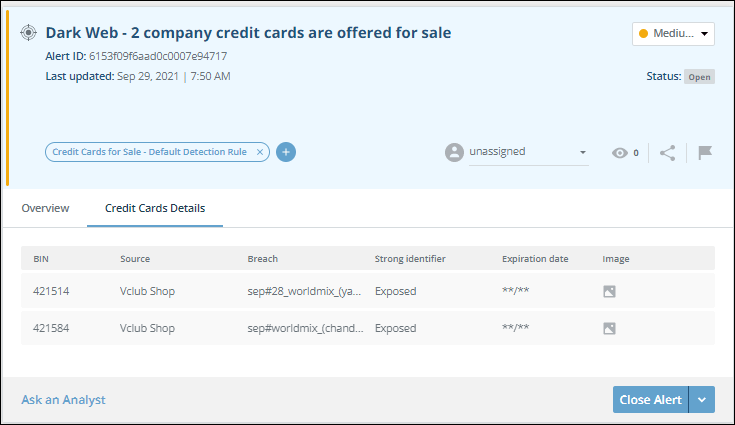
When viewing alert details on an aggregated alert, the details of each card for sale are shown in the Credit Card Details tab.
Together with the source information, an indicator shows whether the sale site is currently reachable.
To view credit card details:
- From the * Digital Risk Protection (Threat Command) > Alerts** page, select an alert.
- Select the Credit Card Details tab.
You can fine-tune the triggering of alerts using the Data Leakage tab of the Alert Profiler.
View Asset Mention Details
When a Code mention asset is found in a GitHub file, an alert is generated. This is determined by the rules in the AlertProfiler.
To provide better visibility and clarity of the mention nature and context, you can review the full details of all the asset’s mentions in the repository. That way, all the relevant information is available directly from the alert.
When multiple asset mentions are found in one GitHub file, the details can be found in the Asset Mention Details tab of the alert:
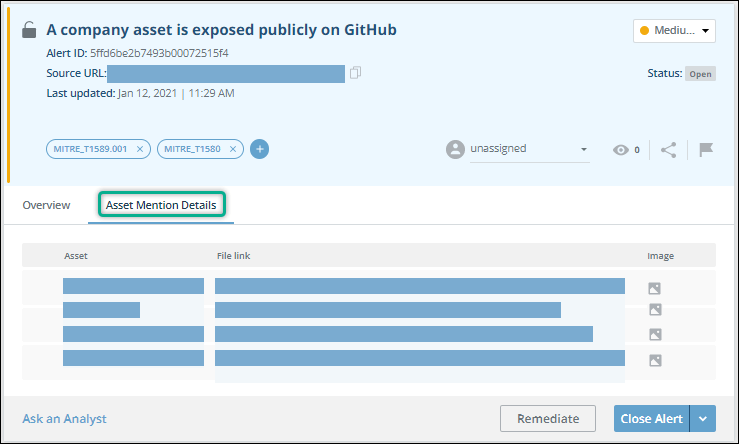
To view asset mention details:
- From the * Digital Risk Protection (Threat Command) > Alerts** page, select an alert.
- Select the Asset Mention Details tab.
- (Optional) To see the mention of the asset, click
 .
.
You can fine-tune the triggering of alerts using the Public Repositories tab of the Alert Profiler.
View Leaked Secret Details
When exposed secrets that contain a company asset are found in a GitHub or GitLab repository, an alert is generated. This is determined by the rules in the AlertProfiler.
To provide better visibility and clarity of the exposed secret nature and context, you can review the full details of the leaked secret and all its mentions in the repository. That way, all the relevant information, such as the leaked secret value, the different commits details, and the secret mentions screenshot, are available directly from the alert.
You can use the Alert Profiler to aggregate alerts, for example, all leaked secrets found in a specified period of time will generate one alert (instead of perhaps hundreds or thousands), with the details for all of the leaked secrets found. For more information about configuring this option, see Aggregate Alerts.
By default, leaked secrets are aggregated by all secrets found in one hour in a specific file. The details of the exposed secrets can be found in the Leaked Secret Details tab of the alert:
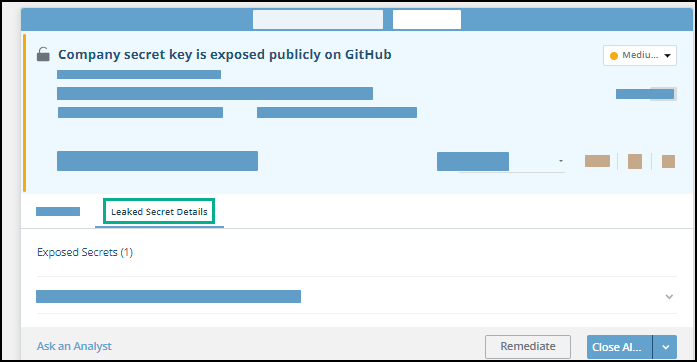
To view leaked secret details:
- From the * Digital Risk Protection (Threat Command) > Alerts** page, select an alert.
- Select the Leaked Secret Details tab.
- (Optional) To see the mention of the secret, click
 .
.
You can fine-tune the triggering of alerts using the Public Repositories tab of the Alert Profiler.
View Matched Objects
For ransomware alerts, you can see the matched objects directly from the alert in the Matched Objects tab. This information is identical to the information displayed in the Threats page.
To view matched objects:
- From the * Digital Risk Protection (Threat Command) > Alerts** page, select an alert.
- Select the Matched Objects tab.
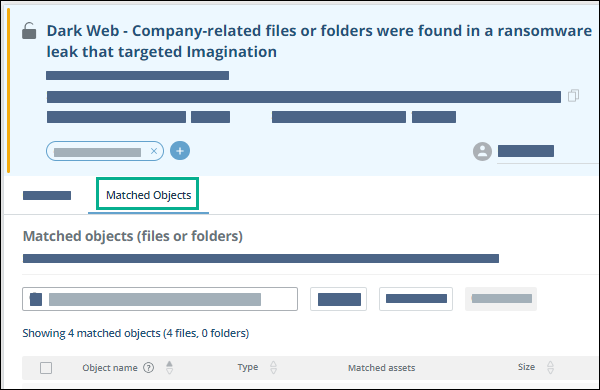
You can fine-tune the triggering of alerts using the Data Leakage tab of the Alert Profiler.