Findings
In the Findings panel, you can observe the vulnerabilities statistics, charts and vulnerabilities details.
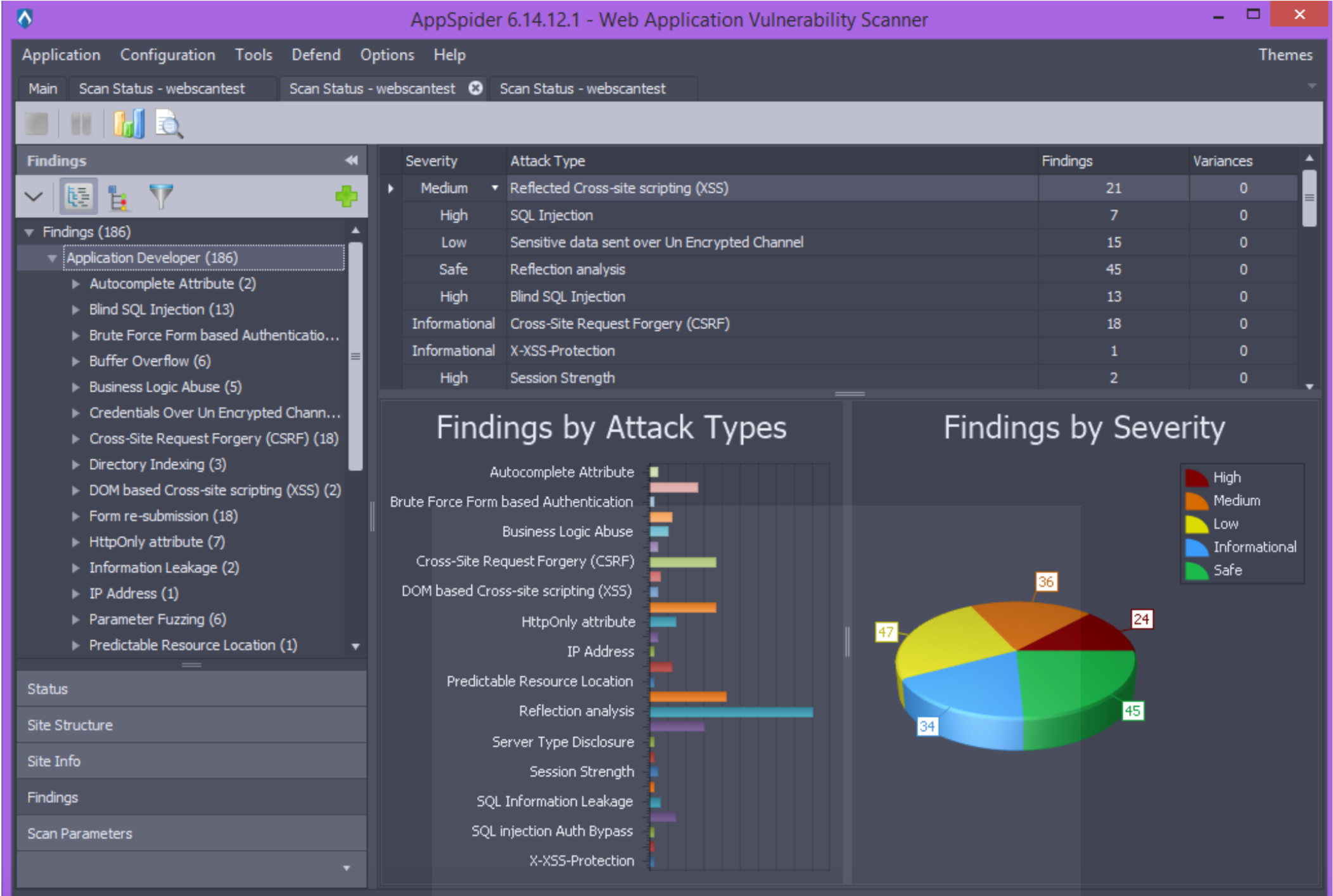
The left panel has the tree view of the vulnerabilities with count in brackets. You can click the “Expand all” button ( )to expand the entire vulnerability tree:
- Findings
- Attack class
- Attack type
- Finding location
- Attack Variance
Vulnerabilities panel
The Vulnerabilities panel contains the statistics for all vulnerabilities:
- Attack class table:
- Attack class: the name of the attack class
- Findings: the number of vulnerabilities found
- Variances: the number of attack variants
- Findings by Attack Classes chart
- Findings by Severity chart
Attack class panel
The Attack class panel contains the statistics for the selected attack class:
- Attack type table:
- Severity: the severity of the attack type
- Attack type: the name of the attack type
- Findings: the number of vulnerabilities found
- Variances: the number of attack variants
- Findings by Attack Class chart
- Findings by Severity chart
Attack type panel
Attack type panel contains the statistics for the selected attack type:
- Vulnerabilities for the Attack type table - the user may select a vulnerability and observe the following options:
- Severity: the editable combo box with the vulnerability severity.
Once you have expanded the tree or a node, you can click on a vulnerability type to view vulnerabilities of that type. You can:
- Change the severity of the vulnerability
- Ignore the vulnerability using the Ignore checkbox
- Globally ignore using the Globally Ignore check box
- Mark the vulnerability as known using the Known check box
- Add notes using the Notes button
- Add new vulnerability using the Add New button.
- Filter issues by All, Active, Ignore.
The table contains following columns:
- Method: the request method
- URL: the finding URL
- Parameter: the vulnerable parameter
- Variances: the number of attack variants
- Ignore: the user marks this check box to ignore the issue
- Globally Ignore: the user marks this check box to globally ignore the issue
- Known: the user marks this check box to set issue status as Known
- Notes: displays notes about the vulnerability when clicked
Details
The following options are available in the Details tabs:
- Description: the description for the selected attack type.
- Recommendation: the recommendation for the attack type.
- References: the reference to the documentation about the attack type
Finding location
The Finding location tabs contain the information about the location of the finding.
You can:
- Ignore the vulnerability by using the Ignore check box
- Globally ignore it using the Globally Ignore checkbox
- Mark the vulnerability as known using the Known check box
- Add notes using the User notes text area
- Add a new vulnerability using the Add New button.
The Finding location table contains the following information:
- AttackType: the vulnerability attack type
- Attack Class: the vulnerability attack class
- Severity: the vulnerability severity
- Method: the request method
- URL: the finding URL
- Parameter: the vulnerable parameter
- User Notes: displays notes about the vulnerability
Variances
The Variances table contains the following information about the attack variant:
- URL: the finding URL
- Parameter: the attack variant parameter
- Ignore: the user marks the check box to ignore the attack variant
- Notes: shows the note for this attack variant.
The Variance panel contains the information about the attack variant.
The following read only fields are available:
- Attack Type
- Attack description
- Original Value
- Attack Value
- Vulnerability
- The Ignore check box ignores the attack variant if marked.
- The Notes text area allows you to enter notes.
The following tabs are available for Original Traffic:
- Request: the web request
- Response Source: the web response
- Response HTML: the response view