How to test a Mobile App
Mobile applications are growing at a rapid pace that the developers and security teams are unable to secure them. There are lots of communications going on about the securing mobile devices and clients. But the most vulnerable aspects of the mobile application back-end services is simply being ignored by the developers and security teams.
These back-end services are generally RESTful APIs using JSON, XML or AMF technology. These services are similar to web applications at High level and are vulnerable to common web application vulnerabilities like SQL injection, XSS, etc.
To find this vulnerabilities requires new techniques. As these services are web services or RESTful apis, It is not possible to crawl the mobile application as web applications. For security testing, it is essential to crawl and capture the traffic manually, save it as consumable format and provide it to AppSpider.
To test a Mobile application, user need to setup the Android emulator in the software model. User need to setup Android SDK which is freely available on the following link: http://developer.android.com/sdk/installing/index.html?pkg=tools
Install Hackazon application in the Emulator
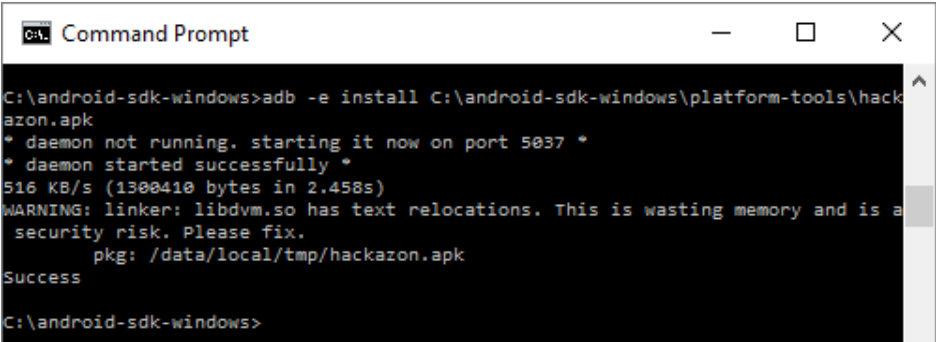
Hackazon application binary is available at the “\hackazon\web\app” of the downloaded package from Github. To install application on Emulator, open a command prompt of the windows system and apply following command. Hackazon application will get installed on the Emulator.
Command to install apk file into the Emulator: adb -e install “System Path of Apk”
For example: adb -e install C:\android-sdk-windows\platform-tools\hackazon.apk
Configuring the Proxy at the Emulator layer
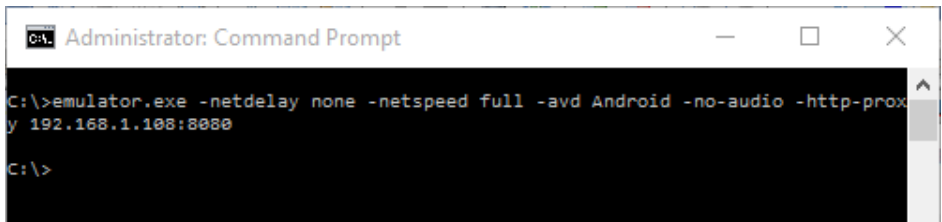
There are two methods to configure the proxy.
- Run and set the proxy using a command line tool
avd {avd-name| example testdroid} -http-proxy {http-proxy address:port| example 192.168.56.101:8080}
For example: emulator -avd Android-http-proxy 192.168.56.101:8080
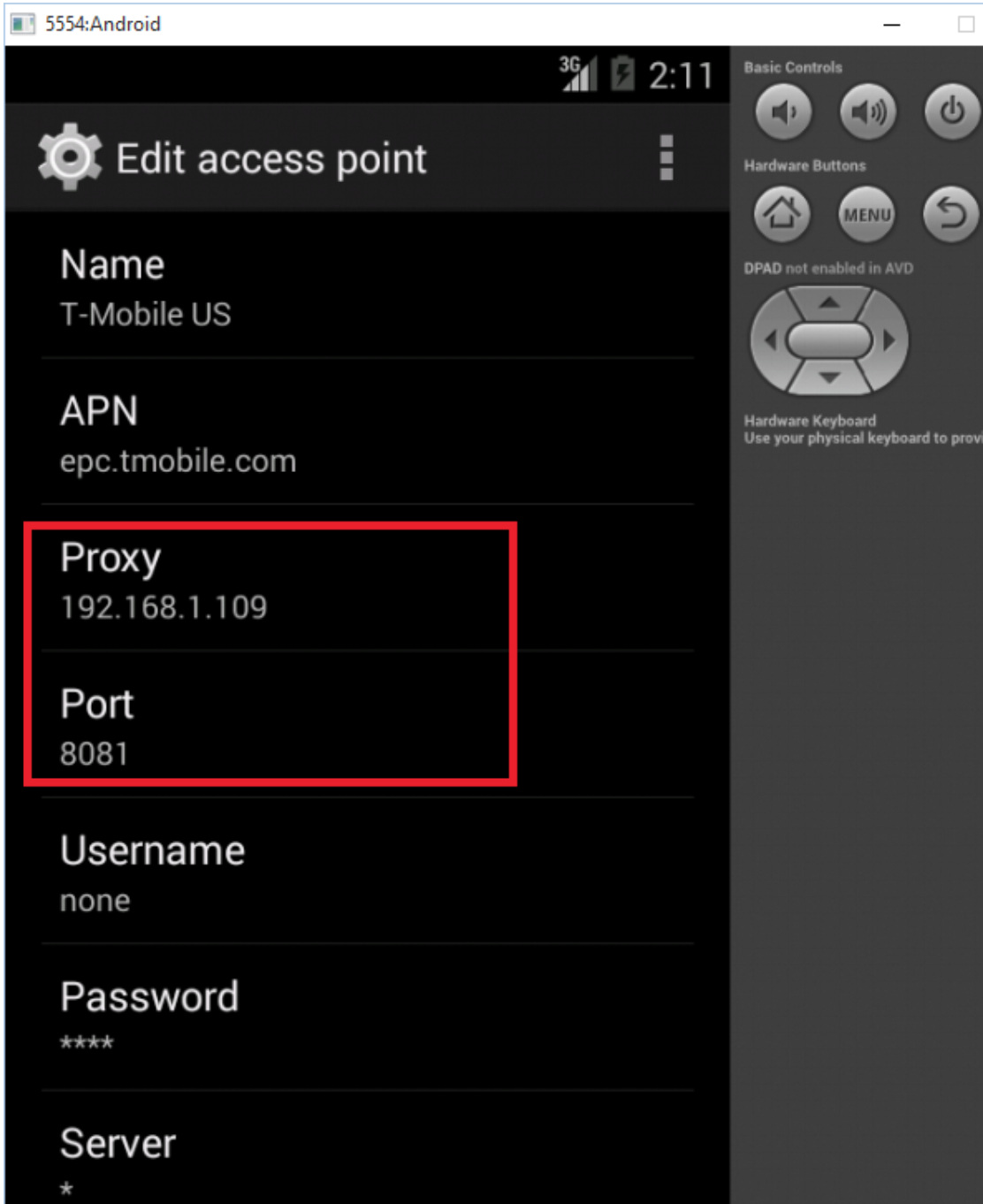
- Configure in the Android Operating System Itself
- On your Android device, navigate into Settings, then tap Wi-Fi
- Tap and hold WiFi connection to Modify network
- Enter proxy settings
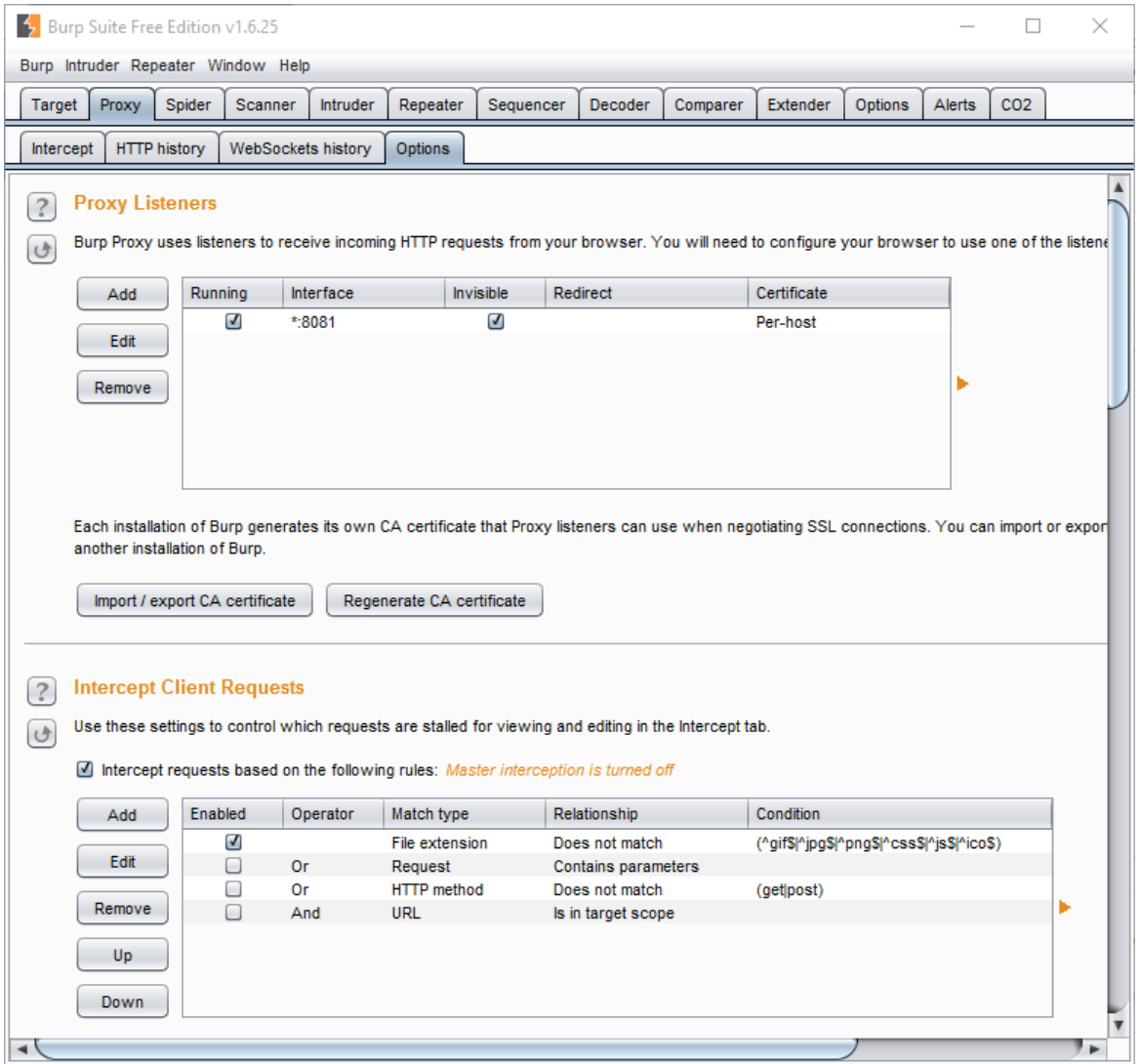
We are using a Burp proxy tool to capture traffic. Navigate to “Proxy” >> “Options” and setup a proxy listener.
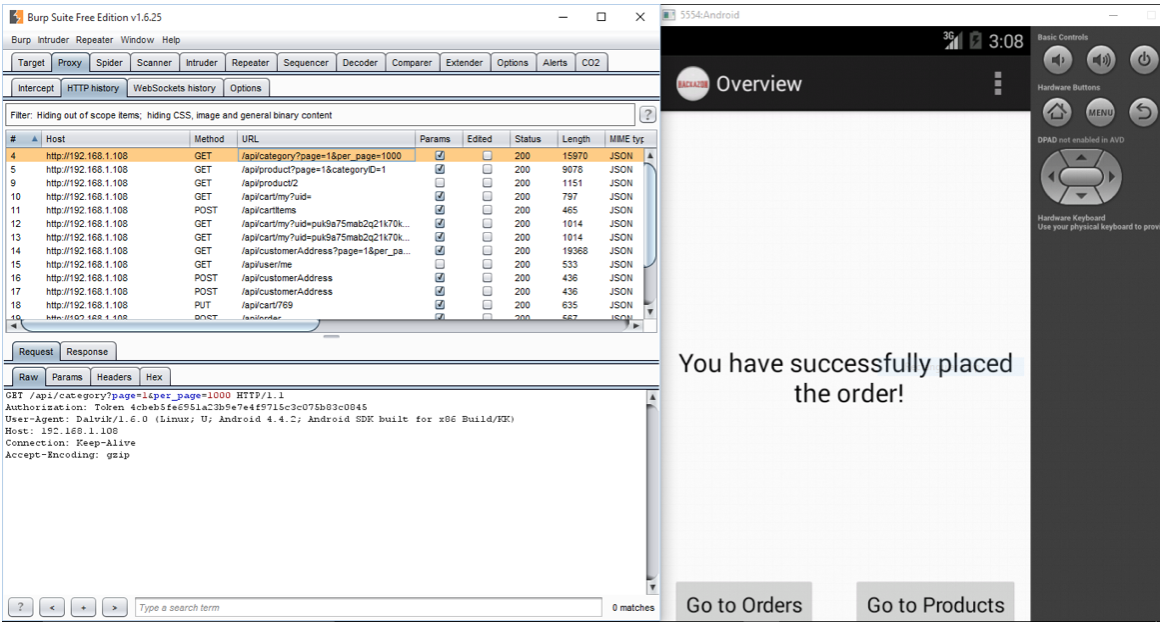
Now, launch the Hackazon application. Login into the application using default login credentials. Manually crawl the application.
- Browse through the items.
- Add items to cart.
- Proceed to checkout.
Save requests to XML format.
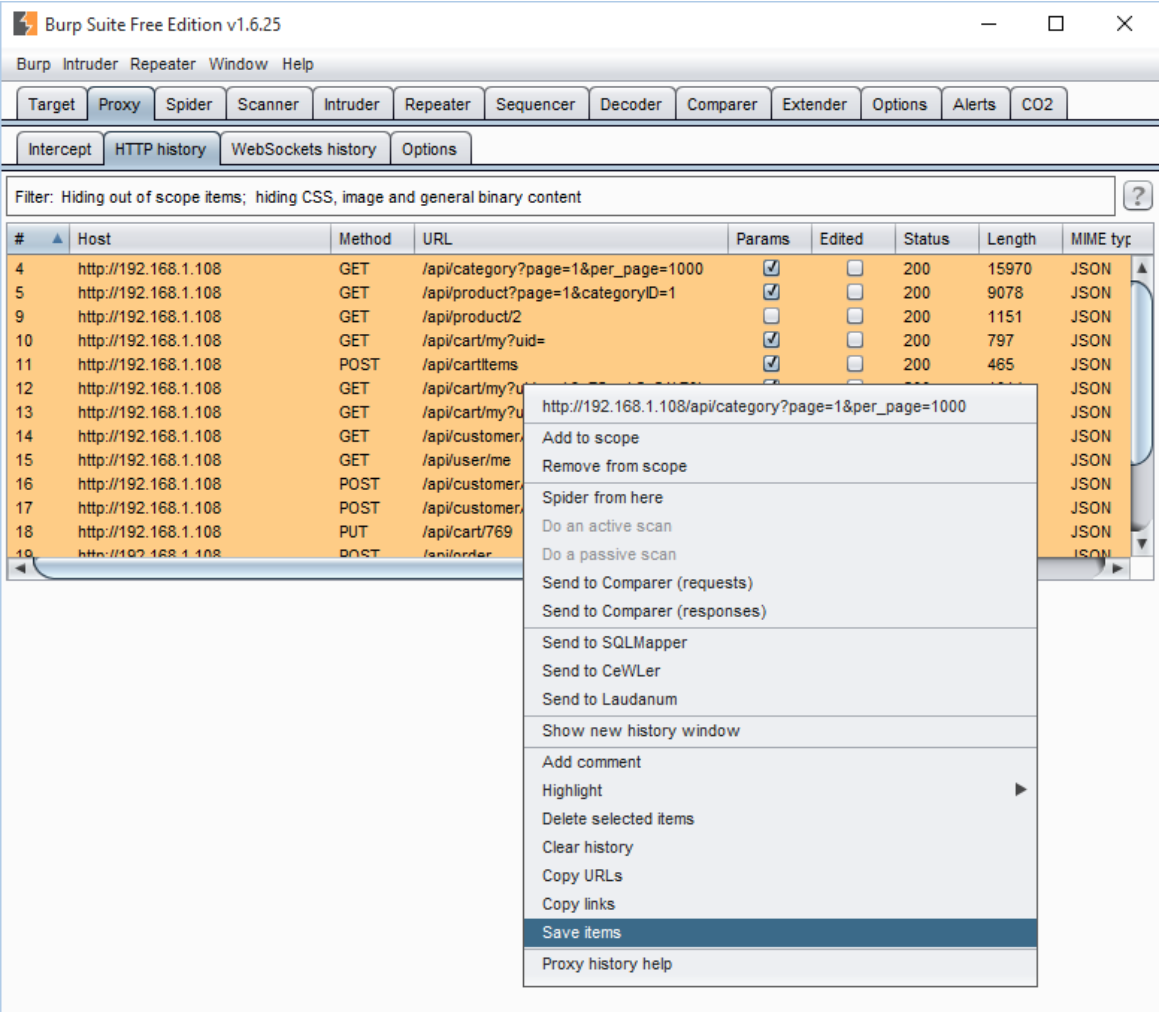
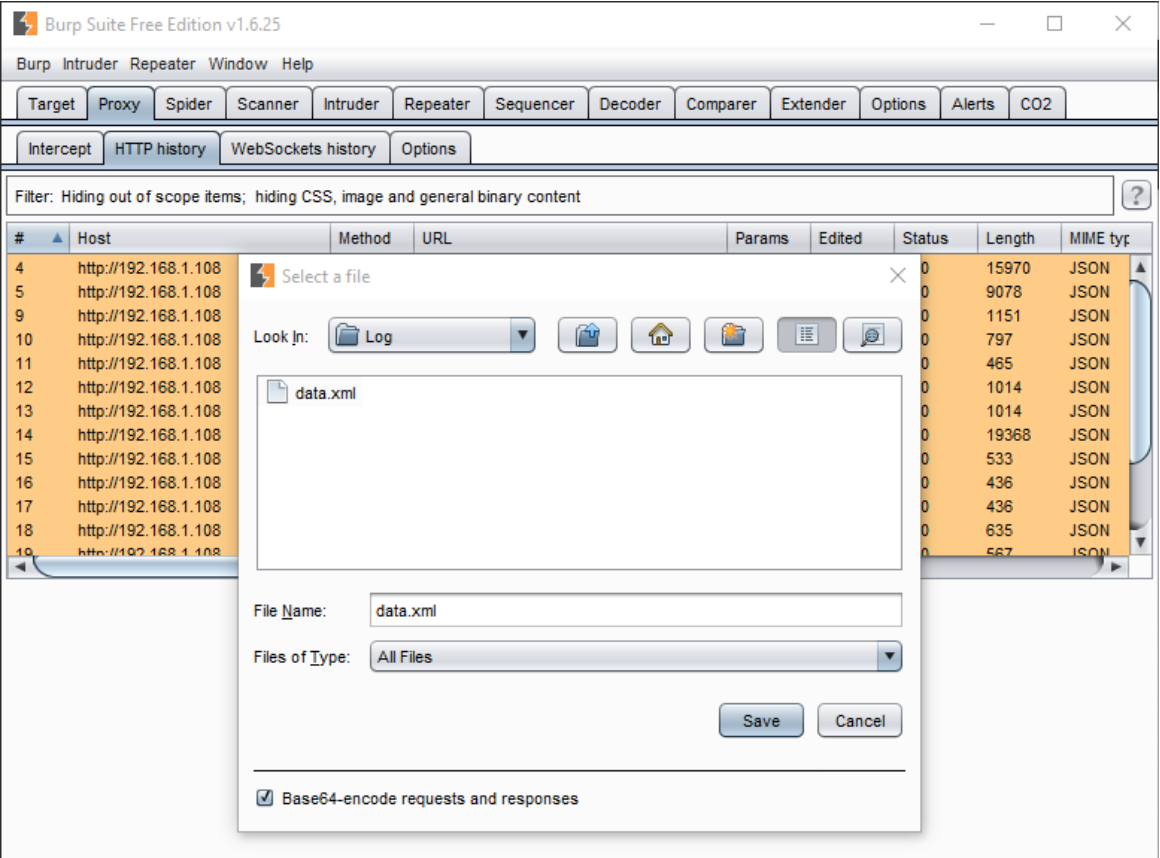
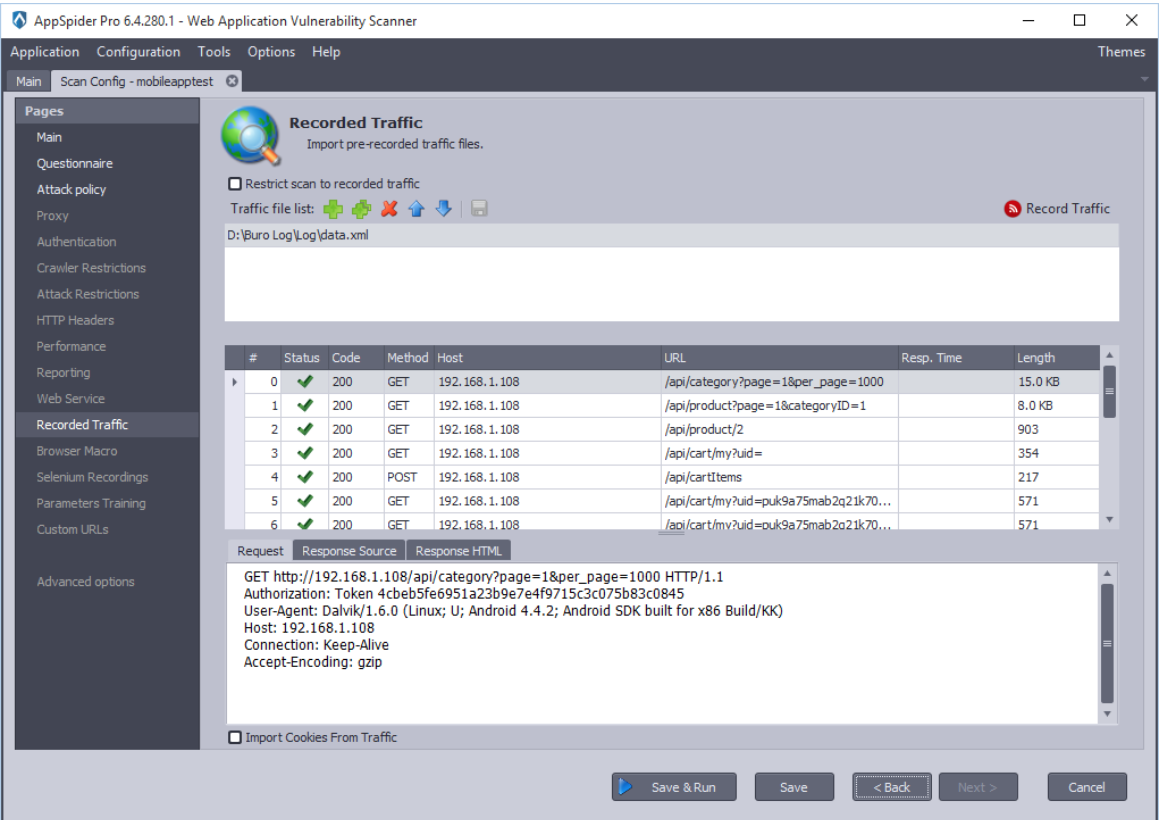
AppSpider has feature called “Import Recorded Traffic,” which allows users to import prerecorded traffic to AppSpider and enable the “Restrict scan to recorded traffic” option. This feature restricts the AppSpider to attack and finds vulnerabilities only on the HTTP traffic imported by user.
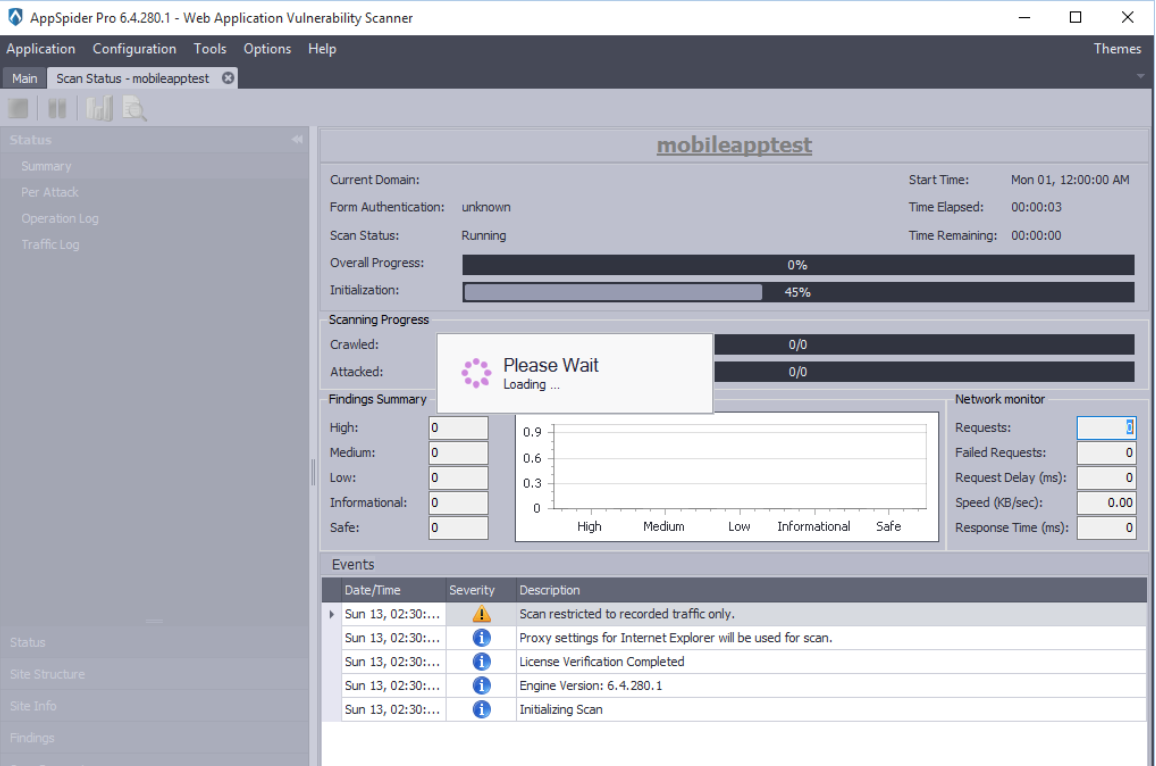
Create a new scan using Appspider and insert scan name and URL of the application.
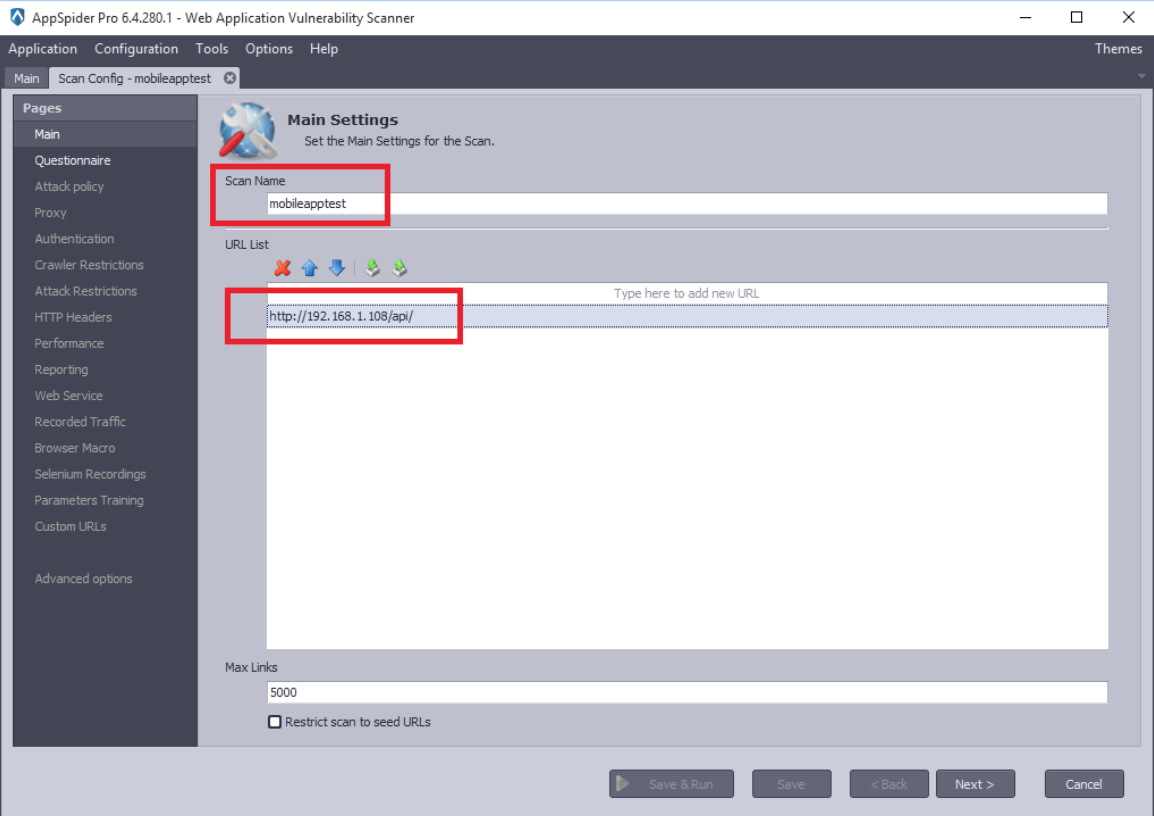
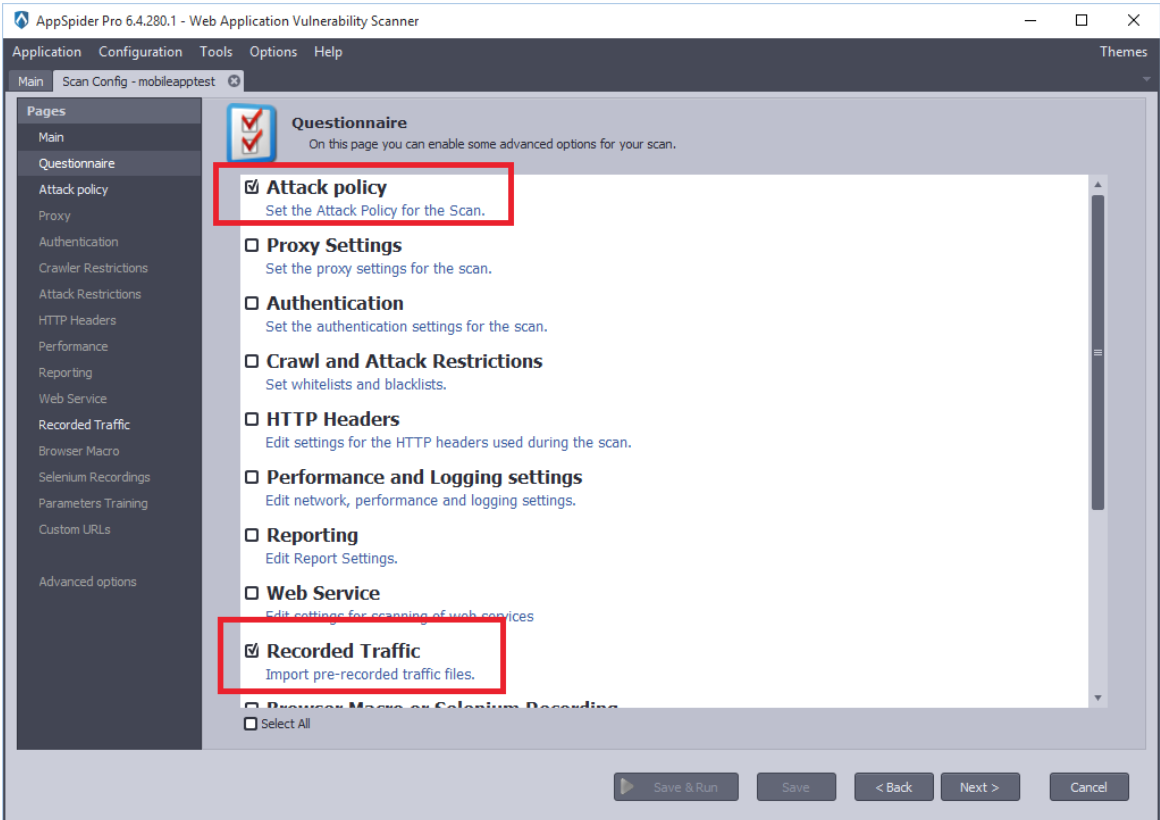
Check the “Attack policy” and “Recorded Traffic” options as we are scanning mobile application to find vulnerabilities.
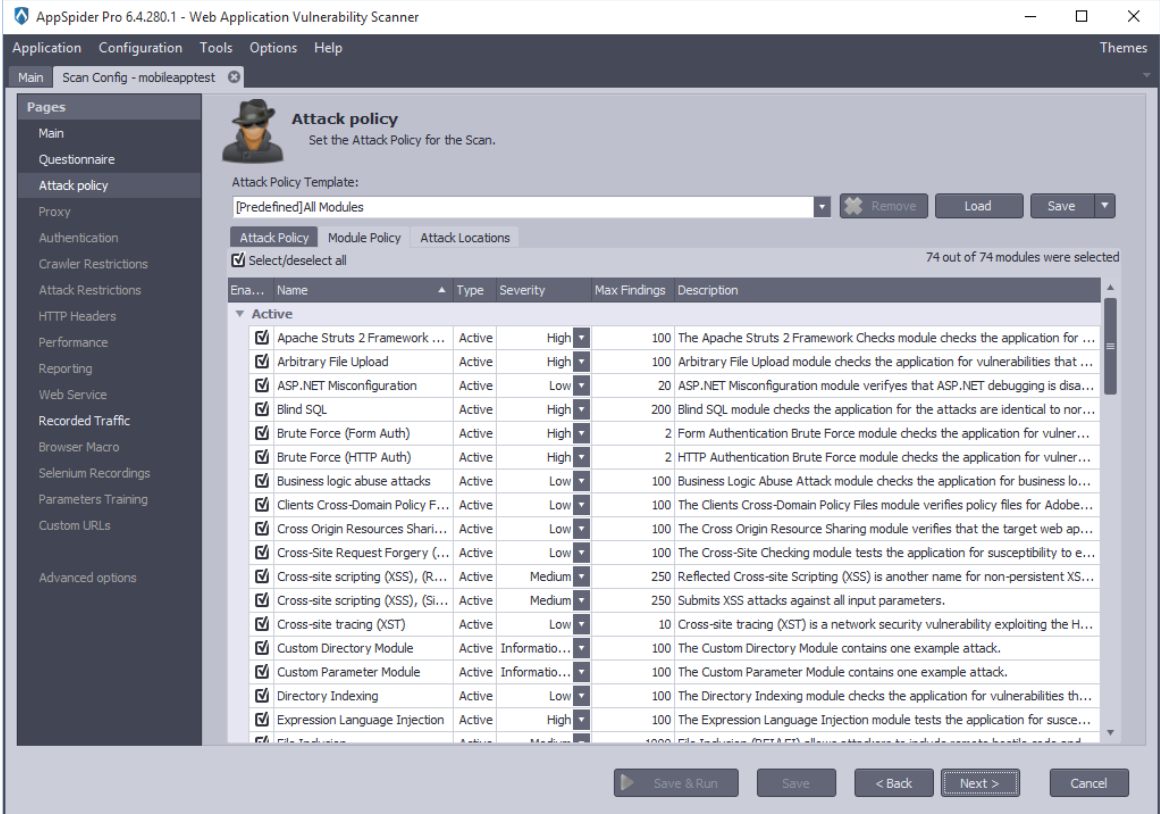
Select a predefined Attack Policy or Create your own attack policy and load it.
Now, click on the “Import Traffic” button and load the recorded traffic.
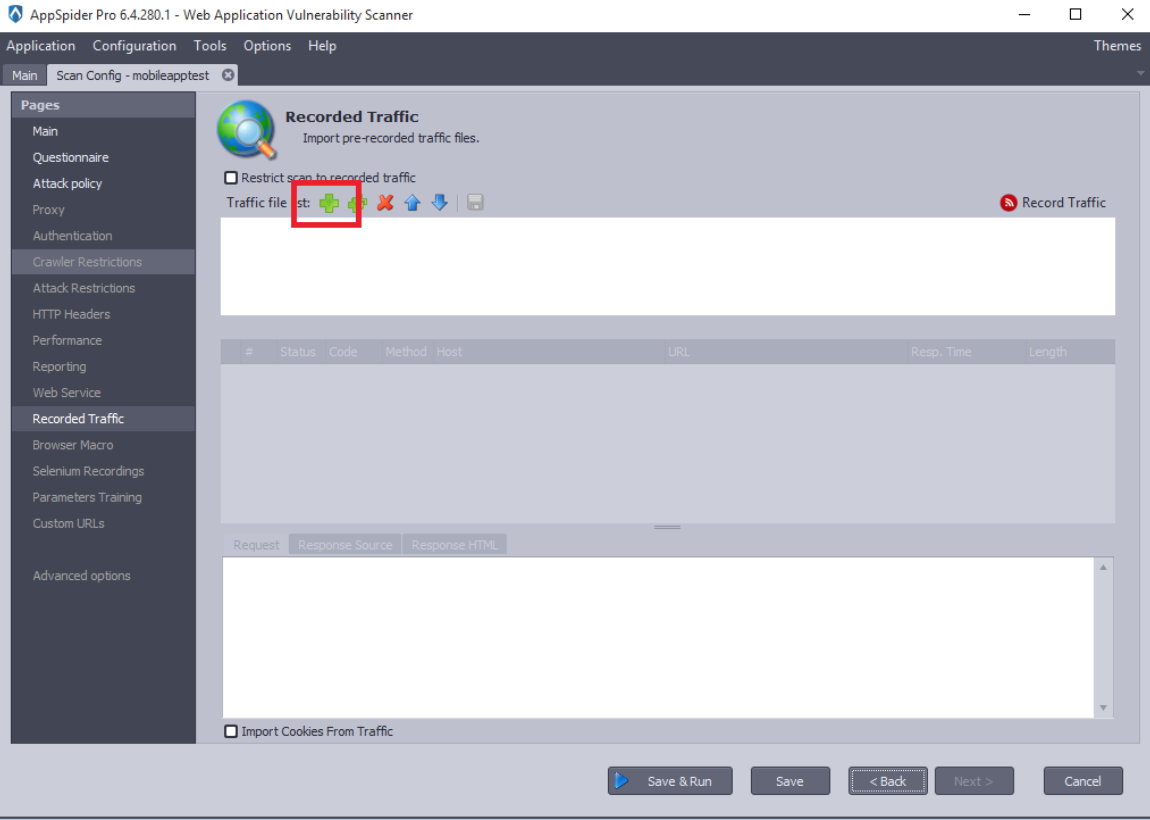
AppSpider imports the prerecorded traffic and loads it.
User can check the “Restrict the scan to recorded traffic”, If they do not want to scan the entire domain. In our case, we would like to perform scanning on limited recorded traffic. Hence, we have checked the Restrict Traffic option.
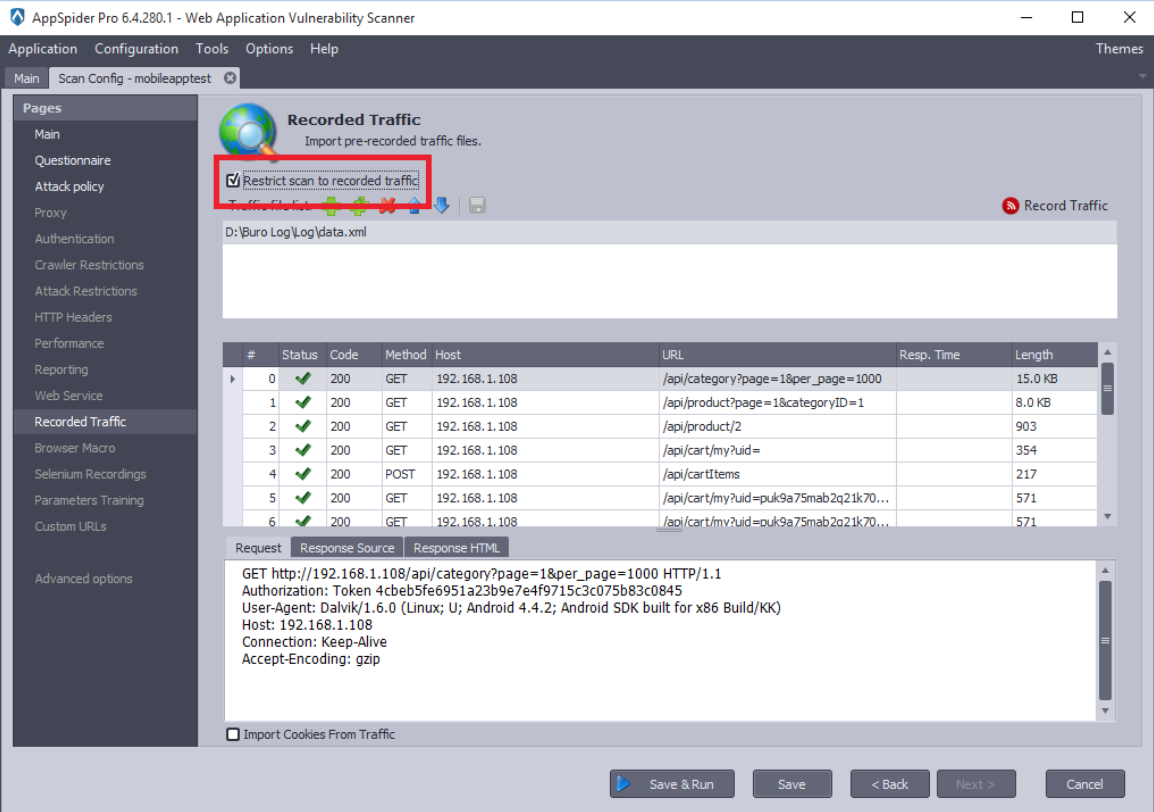
Now, Click on the Sava and Run and AppSpider will start scanning the mobile application.