Manage Vulnerabilities with Jira
Jira Server integrations end-of-life
Effective August 19, 2024, Rapid7 will no longer provide support for Jira Server integrations with Vulnerability Management (InsightVM) Remediation Projects. This decision follows the official end-of-life announcement by Atlassian for Jira Server, which occurred on February 15, 2024. Jira Cloud support is available and will continue to be supported. Atlassian Data Center is not supported and there are no imminent plans to support it.
Read Atlassian’s announcement at: https://www.atlassian.com/blog/announcements/farewell-to-server
Many security teams manage remediation efforts by generating CSV or PDF reports spanning hundreds of pages and spend a lot of time breaking down exposures into actionable work items. Application Security (InsightAppSec) integrates with JIRA Cloud so that security teams can automate the creation and assignment of work items based on pre-configured rules.
This integration simplifies this process while allowing you to:
- Create targeted and precise tickets with rules that can be reused across projects.
- Customize ticketing templates to include as much security context as you need.
- Let your remediation teams continue to use their existing tools and processes.
One-way integration
The connection between JIRA and Application Security (InsightAppSec) is a one-way integration. When a ticket is updated in JIRA, the status within your project does not change.
Requirements
You will need an API token for your JIRA cloud account. Learn how to generate Atlassian API tokens here: https://confluence.atlassian.com/cloud/api-tokens-938839638.html .
On-premise integration is not supported
The JIRA Cloud integration uses API tokens which on-premise integrations do not support.
If your Cloud Jira instance requires Application Security (InsightAppSec) to be allowlisted, use the following addresses relevant to your data region. Your data region can be found in Company Settings > Organizational Settings.
| Region | IP Addresses |
|---|---|
| United States-1 | 52.6.250.170 34.226.12.145 34.227.244.27 |
| United States-2 | 3.19.49.3 3.129.37.8 3.129.99.227 |
| United States-3 | 44.234.244.243 54.185.127.16 54.68.74.253 |
| Australia | 52.62.122.149 52.64.219.171 |
| Japan | 18.182.221.223 54.250.74.126 |
| Canada | 52.60.142.1 52.60.43.144 |
| Europe | 52.57.126.184 52.59.161.41 |
Create a JIRA ticketing connection
- Click on the Administration icon in the sidebar.
- Go to Administration > Integrations and click Add a new JIRA server.
- In the New JIRA Server Connection form, enter a name for this new connection as well as the URL, username, and API Token of your JIRA cloud connection and press Save.
- Make sure to verify that the username you’re entering is correct, otherwise your project keys may not show up.
- You will see the Project Configurations for Application Security (InsightAppSec) screen where you can set up various configurations for your JIRA ticketing project. A configuration is a set of rules that Application Security (InsightAppSec) uses to determine the Type, Status, Priority, and contents of automatically generated tickets.
- Click New Configuration and complete the connection details.
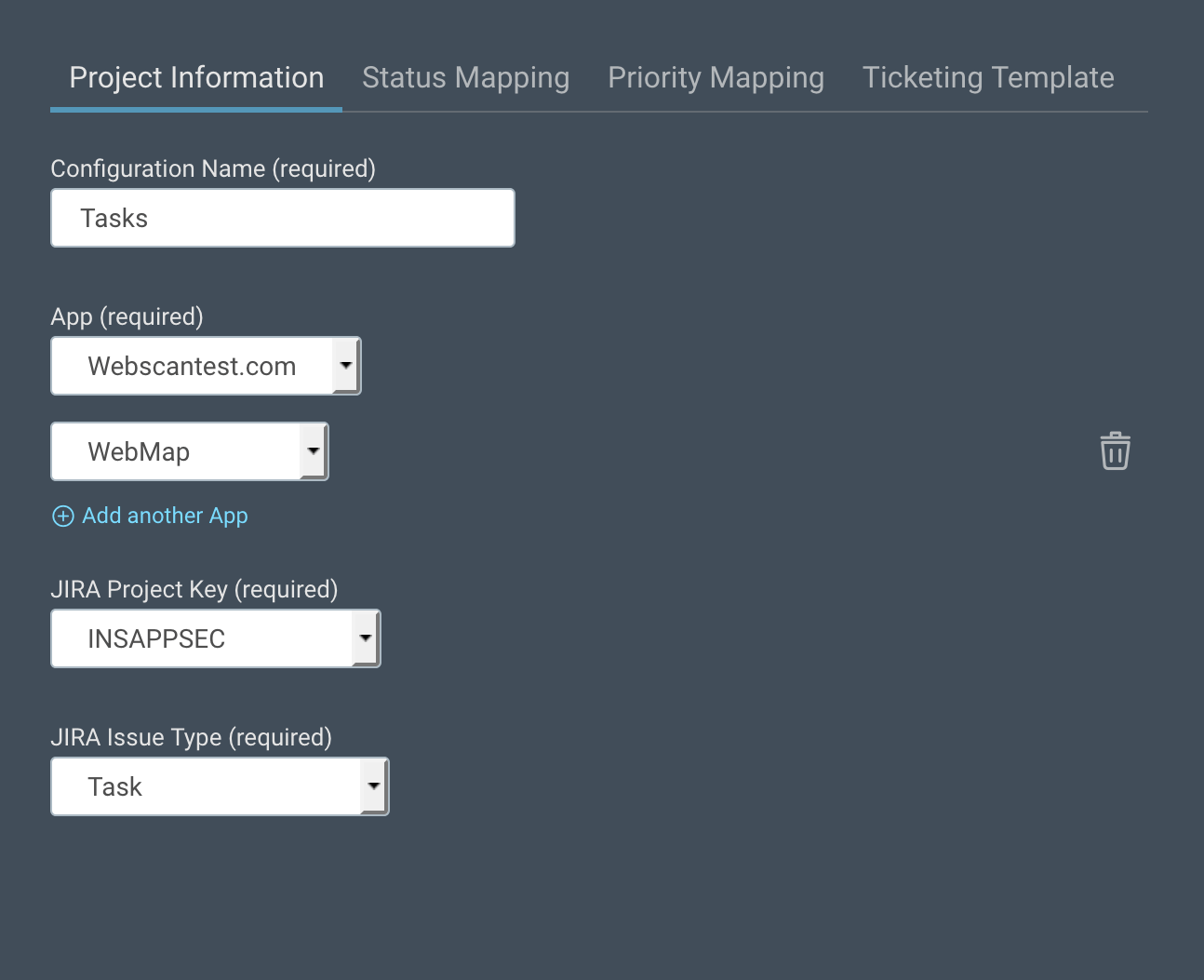
- Enter mappings for Application Security (InsightAppSec) statuses and priority to JIRA statuses. For example, you may wish to show all ‘Remediated’ vulnerabilities in ‘Done’ state in JIRA.
- In the Ticketing Template tab, set up what the Summary and Description in the ticket will say. You can use the special syntax to have terms from vulnerability description to be automatically added to the ticket.
- Click Save.
Note
You can always edit the configuration in the future, but changing the Project Key or Issue type will reset all status and priority mappings.
Create JIRA tickets based on Application Security (InsightAppSec) vulnerabilities
- Visit the Scan Details page of any App for which you have set up a Project Configuration already, or the Vulnerabilities page.
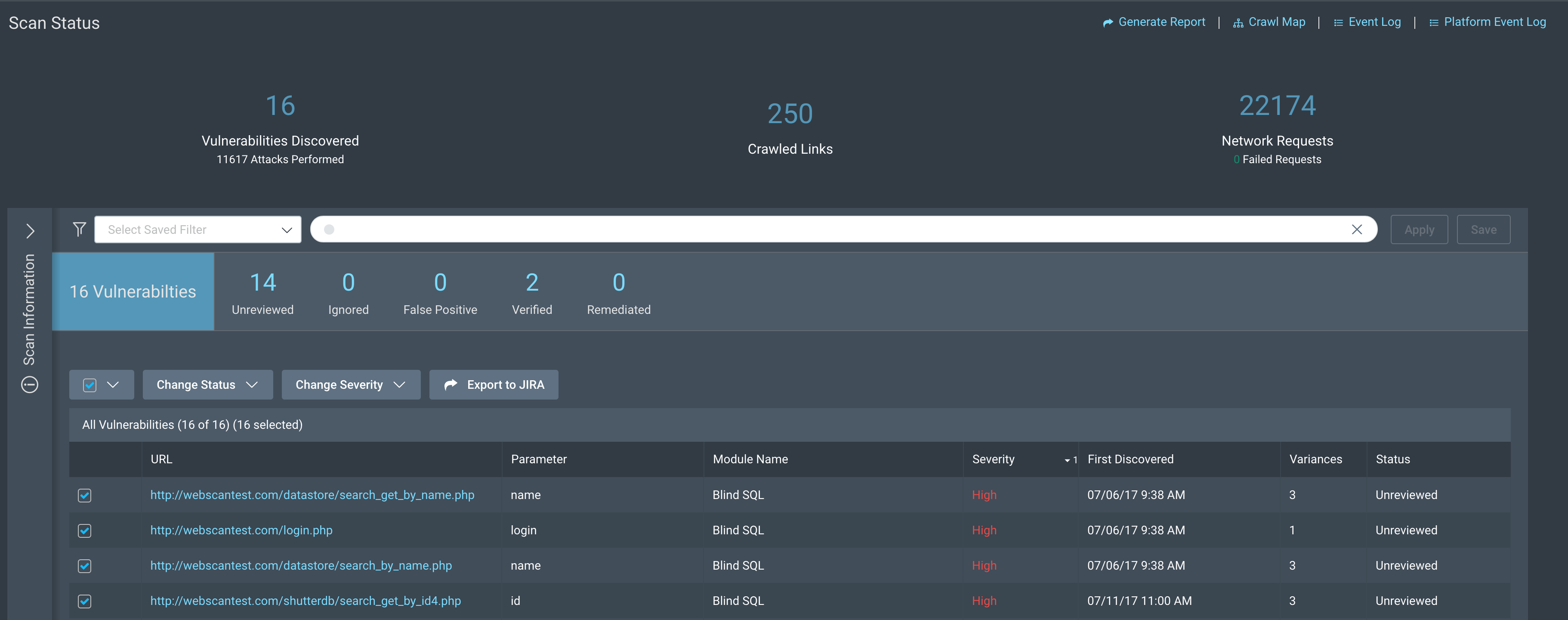
- Select the vulnerabilities that you want to export and click Export to JIRA.
Note that changes to vulnerabilities in Application Security (InsightAppSec) are not automatically reflected in JIRA, and need to be explicitly ported using the ‘Export to JIRA’ functionality.