Host Vulnerability Assessment - User Guide
The information on this page has moved
For the most up to date Host Vulnerability Assessment (HVA) user guidance, go to Reviewing and Managing Vulnerabilities.
After configuration and running an initial assessment(s), go to Security > Host Vulnerabilities to see the following:
- Visualizations that provide a snapshot of risk
- A table/list display with resources that were scanned during your assessment
- Search functionality and filtering to narrow the list of resources to only the most critical or vulnerable
- A tab of Known Vulnerabilities with details like the associated CVE ID, CVSS Score, and associated risk.
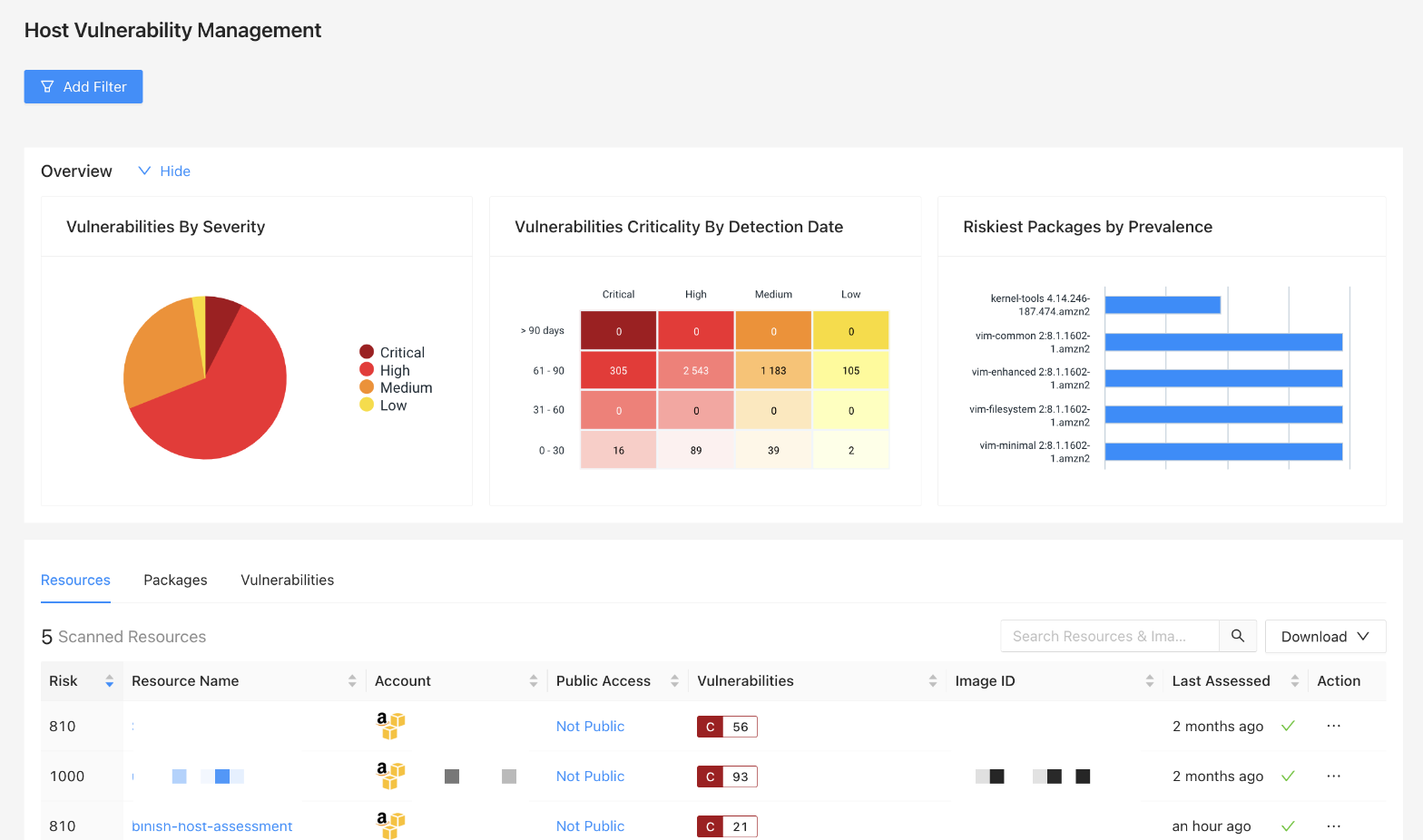
Navigating Host Vulnerability Assessment
General Options
You can add a filter, search, and download on the HVA page.
| Option | Description |
|---|---|
| Add Filter | Filtering allows for narrowing the scope of the resources list using cloud accounts, regions, resource risk score and other useful properties. Click the Add Filters button to open the panel and Select a property to get started. After choosing your desired filters, select Apply to update the page to reflect the results of your specified filters. |
| Search | Type into the search bar and the list of resources will automatically filter to match the criteria. Currently, search is limited to the resource name and type metadata attributes. |
| Download | The Download menu provides two options, the option to download a Resource Vulnerability Report or the option to download the Resource Data, which will be generated in a CSV format. |
Data Visualizations
The top of the page includes three individual data visualizations. These collapse with the “Hide” option to the right of the Overview.
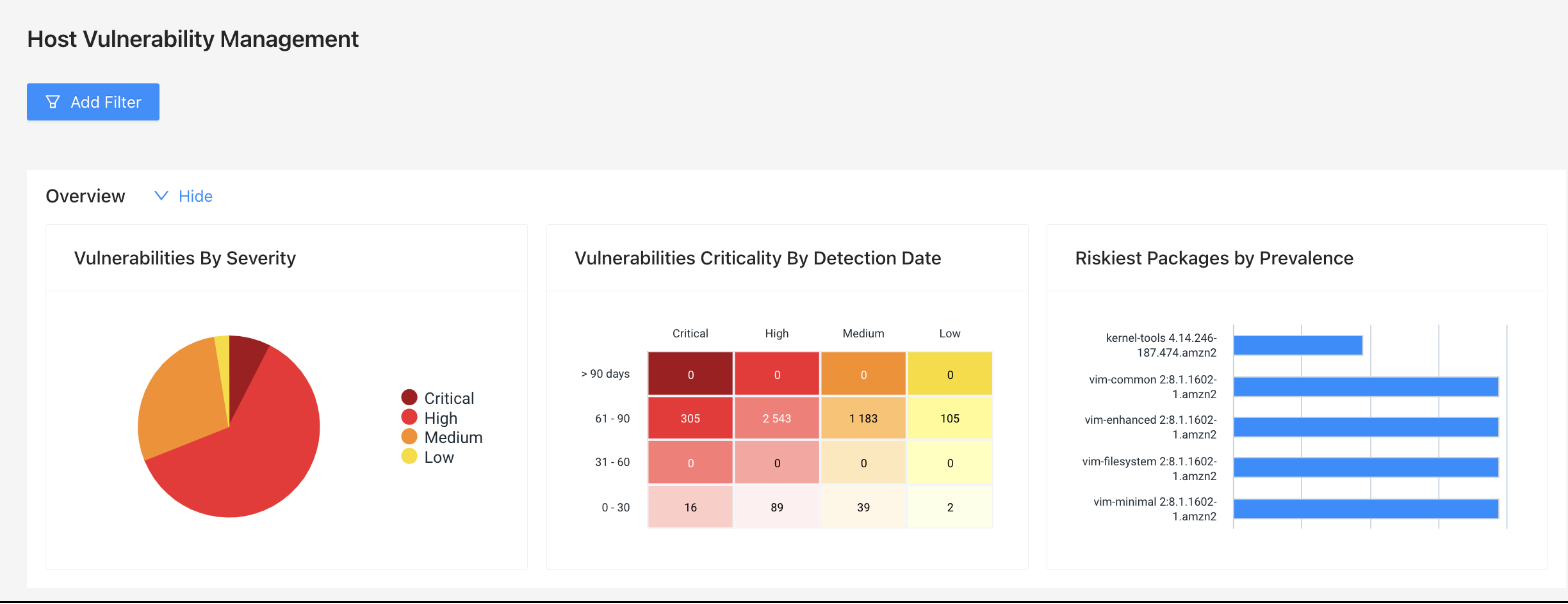
| Visualization | Description |
|---|---|
| Vulnerabilities by Severity | Displays discovered vulnerabilities by severity (Critical, High, Medium, Low). Hovering over a segment displays a count for the selected severity. |
| Vulnerabilities Criticality by Detection Date | Displays a count of vulnerabilities grouped by severity and detection date. |
| Riskiest Packages by Prevalence | Displays the riskiest packages discovered based on how often they appear within the analyzed hosts. |
All Resources Table
Below the data visualizations is the main table/list display of all of the resources analyzed for Host Vulnerability Assessment. Details about the data reflect here is explored in more detail in the Frequently Asked Questions (FAQ).
The default columns that display for All Resources are:
| Column | Description |
|---|---|
| Risk | The risk score assigned to the resource. |
| Resource Name | The name of the resource |
| Account Name | The name of the cloud account the resource is associated with |
| Public Access |
|
| Vulnerabilities | Summary count(s) of vulnerabilities by severity for the selected resource |
| Image ID | ID for the image associated with the resource |
| Last Assessed | The time and date of the last successful scan |
| Action | A drop-down menu of actions available for the resource |
Packages
This tab provides a list of packages used in the host analysis. Selecting an individual package displays details for the package including scanned resources and vulnerabilities.
The default columns that display for Packages are:
| Column | Description |
|---|---|
| Risk | The Risk score assigned to the resource |
| Name | Displays the name of the selected package |
| Impacted Resources | Count of impacted resources for the package |
| Version | Version of the package |
| Vulnerabilities | summary count(s) of vulnerabilities by severity for the selected resource |
| Assessment Date | Date of the last assessment performed |
| Assessment Status | Status of the last assessment performed |
Vulnerabilities
This tab provides a list of Vulnerabilities used in the risk scoring of the resources. Selecting an individual CVE ID provides details of the selected CVE ID.
The default columns for Known Vulnerabilities the display are:
| Column | Description |
|---|---|
| Risk | The Risk score assigned to CVE ID |
| CVE ID | The CVE ID associated with the vulnerability |
| CVSS Score | CVSS Score for the CVE ID listed |
| Impacted Packages | Count of impacted packages for the CVE ID listed |
| Impacted Instances | Count of instances impacted for the CVE ID listed |
| First Detected | Time of the first detection for the CVE ID listed |
| Last Detected | Time of the last detection for the CVE ID listed |
| Action | A drop-down menu of actions available for the CVE ID selected |
Frequently Asked Questions (FAQ)
How Do I Know if Assessments are Completing Successfully?
Assessment progress, errors, and issues are tracked on the Cloud page. An assessment typically completes in about 10 minutes. You can view the status page for an individual cloud account in order to understand what types of issues are occurring including:
- Issues that are preventing assessments from completing successfully
- The number of assessments that have occurred for a cloud account with information about the assessment completions over time
When do Assessments Occur?
Assessments happen as soon as a new instance is discovered in InsightCloudSec either through normal harvesting or Event Driven Harvesting. Once an instance is discovered the snapshot is taken, assessed, and cleaned up as a part of the assessment process.
How Do I Start a Manual Assessment?
Assessments can be manually triggered by taking the ‘Assess for Vulnerabilities Using InsightCloudSec’ action on an Instance. This can be done by navigating to the Host Resource and viewing the Actions that can be taken against the Host or executed through the InsightCloudSec API. A manual assessment can also be performed directly from the Host Vulnerabilities page in the user interface.
Triggering an assessment starts the snapshot immediately and the progress of the Assessment can be viewed on the Host Vulnerabilities progress page. The timing for an assessment to complete depends on the size of the image and can take anywhere from 5 minutes to 20 minutes.
Where Can I View the Host Vulnerabilities Assessment Results?
The assessment results can be seen on the Resources Page in the details blade of the Host and in the Host Vulnerabilities page in InsightCloudSec.
In order to report on Vulnerabilities across multiple Hosts, the Host Vulnerabilities page can be used. The Vulnerability Assessment page in the InsightCloudSec product allows for filtering, searching, and prioritization of Vulnerabilities across multiple Vulnerability sources consumed by InsightCloudSec.
What if InsightVM is Assessing the Same Host Using the Rapid7 Agent?
You don’t need to remove the InsightVM agent. InsightCloudSec Host Vulnerability Assessment will snapshot instances with an existing agent and conduct the collection and assessment with no issues.
Most vulnerabilities will be reported identically between the two; however, InsightCloudSec has a larger scope of detection and may report more vulnerabilities than InsightVM.
This allows time to evaluate the new feature before removing the agent and transitioning Host instance vulnerability management from InsightVM to InsightCloudSec.
What Bot Actions Are Available?
A new category of Bot Actions has been added to support HVA, this new category allows for Bots to execute reactively after new vulnerabilities or packages are discovered on an instance or container image.
Some common use cases for Bot Actions are: Notify Users that un-allowed packages have been deployed or Shut down instances that have Log4J vulnerabilities. The combination of Event Driven Harvesting and Bot Actions allows for security administrators to respond to infrastructure and deployment changes within minutes.
Take a look at our BotFactory & Automation documentation for additional details on these capabilities.
How is “Risk Score” Calculated?
The Vulnerability Risk Score rating in InsightCloudSec uses a variety of factors to determine the rating of a vulnerability. Threat Feeds, Exploit Databases, and the vulnerability CVSS score are combined to produce a Risk Score to help prioritize vulnerabilities.
When viewing the risk score for a vulnerability there are details about the reason for the score produced: vulnerabilities with published exploits and vulnerabilities that threat feeds have marked as actively exploited will have scores that are higher than other vulnerabilities within the product that have similar CVSS scores.
For example, CVE-2022-0318 has a CVSS score of 9.8. This vulnerability is not actively exploited and does not have published exploits. This vulnerability has a risk score of 810 (if there are threats and/or exploits published in the future this risk score will change accordingly). On the other hand CVE-2020-15999 has a CVSS score of 6.5, and is a known exploited vulnerability according to the CISA KEV Catalog. The active exploitation of the vulnerability raises the risk score to 1000.
This calculation enables you to quickly identify vulnerabilities that need to be addressed in order to reduce the risk of your cloud environment.