Layered Context - User Guide
The information on this page has moved
For the most up to date Layered Context guidance, go to Layered Context.
Layered Context provides access to the visualizations, search functionality, filters, as well as a table/list display of clouds, applications, and resources. Any resource listed here is associated with one or more Insights.
Go to Security > Layered Context to get started.
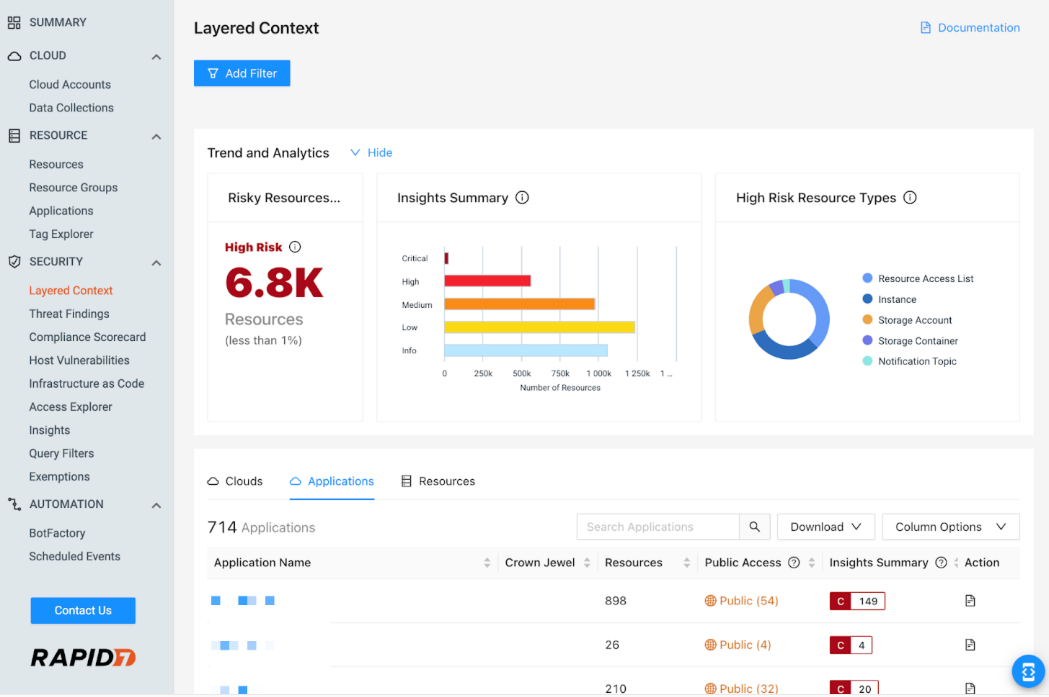
Layered Context Page
The Layered Context Page includes:
- Trend and analytics visualizations that provide a snapshot of risk
- Search functionality and filtering that allow you to narrow the list of resources to only the most critical or vulnerable
- A table/list display with a list of clouds, applications, and resources that are currently associated with one or more InsightCloudSec Insight, Vulnerability, or Threat Finding
Visualizations (Trend and Analytics)
The Trend and Analytics section of Layered Context provides high-level visuals to summarize risk associated with your resources.
| Graph | Description |
|---|---|
| Resource Risk Severity | A summary of the number of resources in your environments with a risk score severity that fall into each category:
|
| Critical Risk Resource Types | Displays a visual breakdown of the resource types with critical risk, including a count and overall percentage. For example: if you have 100 resources with critical risk and 20 of those resources share the same type, their portion of the graph would read <type> 20% (20) Critical Risk Resources |
Scoping the Data
Layered Context includes tabs/sections to narrow your focus to specific categories. We include Clouds, Applications, and Resources as a way to explore and analyze your risk. For organizations with large and complex cloud environments, these scopes provide the ability to evaluate a single cloud account, Application Context, or resource. When combined with filtering, these scoping capabilities enable you to quickly navigate to specific areas that you want to evaluate for risk.
| Tab | Description |
|---|---|
| Clouds | Selecting the “Clouds” tab allows you to view Layered Context for your cloud resources through the scope of your cloud account(s). Selecting an individual cloud (by clicking on the name) generates a view of the resources for the cloud selected. This view can be refined further through filtering to help you target specific security concerns within that cloud account. |
| Applications | Selecting the “Applications” tab allows you to view Layered Context for your cloud resources through the scope of your Applications. This feature requires some additional configuration that you can learn more about through the Application Context page. Selecting an individual application generates a view of the resources within that application. This view can be refined further through filtering to help you target specific security concerns within the application. |
| Resources | Selecting the “Resources” tab displays Layered Context details for all of your connected cloud resources. Selecting an individual resource (by clicking on the name), provides a resource detail pane with where you can explore the properties of the resource, Insight Findings, view Related Resources and download JSON for that individual resource (along with many other contextual details). |
Filtering & Searching
Layered Context has searching and filtering functionality to narrow the scope of the resource list. These features can be used together to effectively and quickly navigate. The “Add Filter” button also allows you to select a filter that will be applied to the Trend and Analytics visualizations.
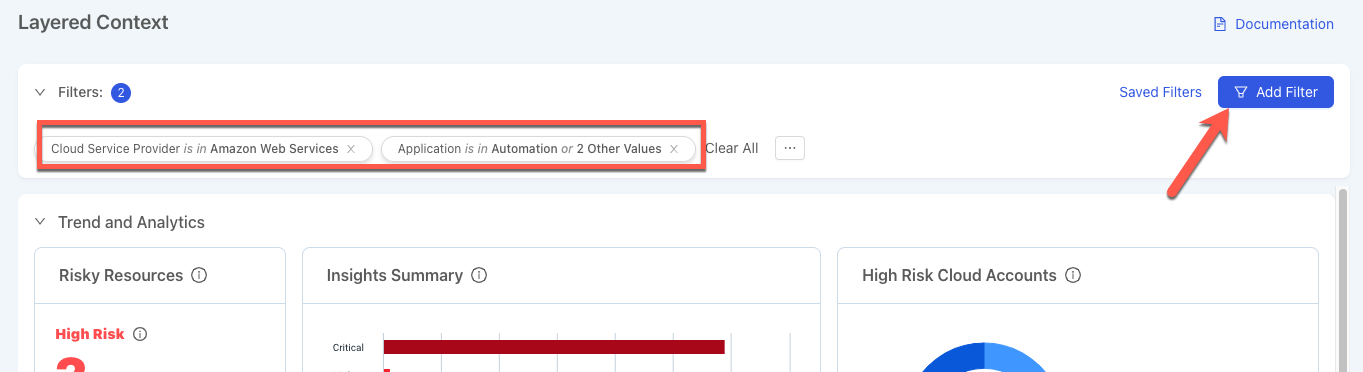
Add Filter
Filtering (“Add Filter”) allows for narrowing the scope of the resources list using properties like: cloud accounts, clusters, and resource groups. Click the Add Filters button to open the panel and Select a property to get started. After choosing your desired filters, select Apply to update the page to display the results of your specified filters.
Filtering Behavior:
- Each selected Filter updates dynamically with options appropriate for the property selected.
- Click + Add Filter to add an additional filter and further narrow the scope.
- Layered Context supports filtering by a Resource Tag.
- Searching for a tag is case insensitive.
- New tags are harvested every 12 hours by the
ResourceTypeTrigramsProcessbackground job (see System Settings fore more information).
Save Filters
After Adding a Filter, you can save it so that can easily be reused the next time you access the feature. Note: Saved filters are feature-specific (since options vary between features), i.e., a Feature “A” saved filter will only be available in Feature “A” and will not be available in Feature “B”.
- In InsightCloudSec, go to Security > Layered Context.
- On the Layered Context page, click Add Filter.
- Enter your filter criteria. Tags are case sensitive. New tags are updated every 12 hours.
- Click Apply.
- (Optional) Save the filter for repeat use. a. Click the ellipsis and select Save Filter. b. Select whether the filter if the default filter to display. c. Select whether to make the filter public. d. Click OK.
- Review the results.
Search
Type into the search bar and the list of resources will automatically filter to match the criteria. Currently, search is limited to the resource name and type metadata attributes.
Download
To save a copy of the information found in the resource list, click “Download” next to the search bar and select either “CSV” or “JSON”. The file will be prepared in the background until it is ready to be downloaded by your web browser.
If the file preparation takes longer than 10 minutes, it will timeout, so it’s best to narrow the scope prior to downloading.
Data Display
Below the Trend and Analytics data visualizations is the main table/list display of all of the data (grouped by Clouds, Applications, and Resources) analyzed within Layered Context.
The capabilities for this section of the page (above the data display) include: Search, Download (JSON/CSV), and Column Options. Column options vary for each of the additional scope options (Clouds, Applications, and Resources) and are provided in detail below.
Detailed descriptions of Cloud fields
Cloud
The following details display by default for Clouds.
| Field | Description |
|---|---|
| Cloud Name | The name of the cloud account |
| Cloud | The type of cloud account |
| Resources | The resource count for the cloud account |
| Public Access |
|
| Insights Summary | Displays highest criticality available (for example if the resource is only associated with an Insight (or Insights) with a misconfiguration identified with a Medium severity, that is what will display in the Insights Summary).
|
| Vulnerabilities Summary | Displays the badge(s) and count (Critical, High, Medium, Low), for the highest severity vulnerabilities identified for the selected cloud.
|
| Threat Findings Summary | Displays the badge for highest severity Threat Finding for the selected cloud
|
| Action | Offers a context menu with a link to view the Resources associated with the given cloud. |
Detailed descriptions of Applications fields
Applications
The following details display by default for Applications.
| Field | Description |
|---|---|
| Application Name | The name of the application |
| Business Critical | Identifies an application as business critical |
| Resources | The resource count for the application |
| Public Access |
|
| Insights Summary | Displays highest criticality available (for example if the application is only associated with an Insight (or Insights) with a misconfiguration identified with a Medium severity, that is what will display in the Insights Summary).
|
| Vulnerabilities Summary | Displays the badge(s) and count (Critical, High, Medium, Low), for the highest severity vulnerabilities identified for the selected application.
|
| Threat Findings Summary | Displays the badge for highest severity Threat Finding for the selected application
|
| Action (View Resources) | Creates a scoped view of resources where you can do the following:
|
Detailed descriptions of Resources fields
Resources
The following details display by default for Resources.
| Field | Description |
|---|---|
| Resource Name | The name of the resource |
| Resource Type | The type of resource |
| Account Name | The name and type of the cloud account the resource is associated with |
| Public Access |
|
| Insights Summary | Displays highest criticality available (for example if the resource is only associated with an Insight (or Insights) with a misconfiguration identified with a Medium severity, that is what will display in the Insights Summary).
|
| Vulnerabilities Summary | Displays the badge(s) and count (Critical, High, Medium, Low), for the highest severity vulnerabilities identified for the selected resource.
|
| Threat Findings Summary | Displays the badge for highest severity Threat Finding for the selected resource
|
| Action | Offers a context menu with links to:
|
Context (Resource)
Selecting an individual resource by name, either from the Resources tab/section, or the scoped Resources tab/section generated by viewing data through Clouds or Applications, opens a detailed view of the context for the selected resource.
Resource Detail Availability
For each individual resource available in Layered Context the additional details (properties, actions, tag, etc) will vary.
- Areas that are not applicable, and/or those that do not contain data will be grayed out.
- Depending on the resource different context is available.
The following details display by default for Context (Resources).
| Details | Description |
|---|---|
| Properties | This tab provides a list of metadata attributes or properties for the selected resource, such as Cloud Account details, Resource ID, and a direct link. |
| Action(s) | A list of actions available for the selected resource. These will vary based on permissions and resource type. |
| Tags | Tags associated with the selected resource. |
| Insight Findings | Provides a detailed list of the Insights this resource is associated with.
|
| Public Access | For resources marked as publicly accessible, this tab contains a count of checks and details for each check, including the date it was identified and the results (Public/Not Public).
|
| Vulnerabilities | This tab will provide a detailed list of the Vulnerabilities associated with this resource when available. Note: This capability is still in development. See Container Vulnerability Assessment for more information on vulnerabilities. |
| Threat Findings | Provides a detailed list of the Threat Findings associated with this resource. Each line includes: Severity, Name, Provider ID, Occurrences (of each finding), First Seen (for each occurrence) and Last Seen (for last or most recent occurrence). Clicking on the arrow next to the individual line expands to show details for the selected Threat Finding. |
| Source Documents | See the full section below for more information. |
| Related Resources | Displays a list of associated resources with links to those resources/details. |
| Activity | Displays a list of activities associated with the resource. |
| Additional Columns | Additional columns beyond “Activity” may include Flow Log Findings, Groups, Policies, Custom Policies, etc. And will vary depending on the type of resource selected. |
Source Data
For select AWS resource types, there is an additional detail pane, Source Data, that surfaces raw data about the resource harvested directly from the Cloud Service Provider (CSP). This additional context about your resources can help to further investigate configuration issues or provide deeper analysis. Click into the document viewing area, then use ⌘F (MacOS) or CTRL+F (Windows) to search through the data. For full support details, see Resources
Documents will only be stored if changes are detected for a resource or if new resources have been created, so some supported resources may not have any source documents.
Layered Context API
There are two endpoints to enable interacting with Layered Context programmatically.
- Detail Resource : This endpoint details a resource, including parent account information and dependencies. Read more about in the InsightCloudSec API reference.
- Export Source Data : This endpoint will export a given resource’s source data.