Microsoft Teams Connection Guide
Microsoft Teams is a unified communications platform that combines persistent workplace chat, video meetings, file storage and application integration. The Microsoft Teams plugin allows you to send and trigger workflows on new messages. The plugin will also allow for teams management with the ability to add and remove teams, channels, and users.
Before you begin
- To collect configuration information, log into your Azure Portal .
- Create a new user within Azure for use as a service account for the integration.
- The user must be non-federated and must have MFA disabled.
- Provision the user with a license for Microsoft Teams.
- Typically, Microsoft will require a user to change their password upon first login, so log into the new user account and change the password. Be sure to keep note of it (in a secure manner, such as a password manager), because you will need it later.
- During this configuration, you are required to create a new app registration at
portal.azure.com. Because this can require higher levels of permissions in Azure, you may need to reach out to your IT or infrastructure teams to get assistance with this.
Application ID
Note
These steps may require additional team members outside of security. Creating App Registrations within Azure requires higher levels of permissions, which some organizations reserve for their IT or Infrastructure teams.
In case the Application already exists, please contact an Azure Admin to grant access to the Application.
-
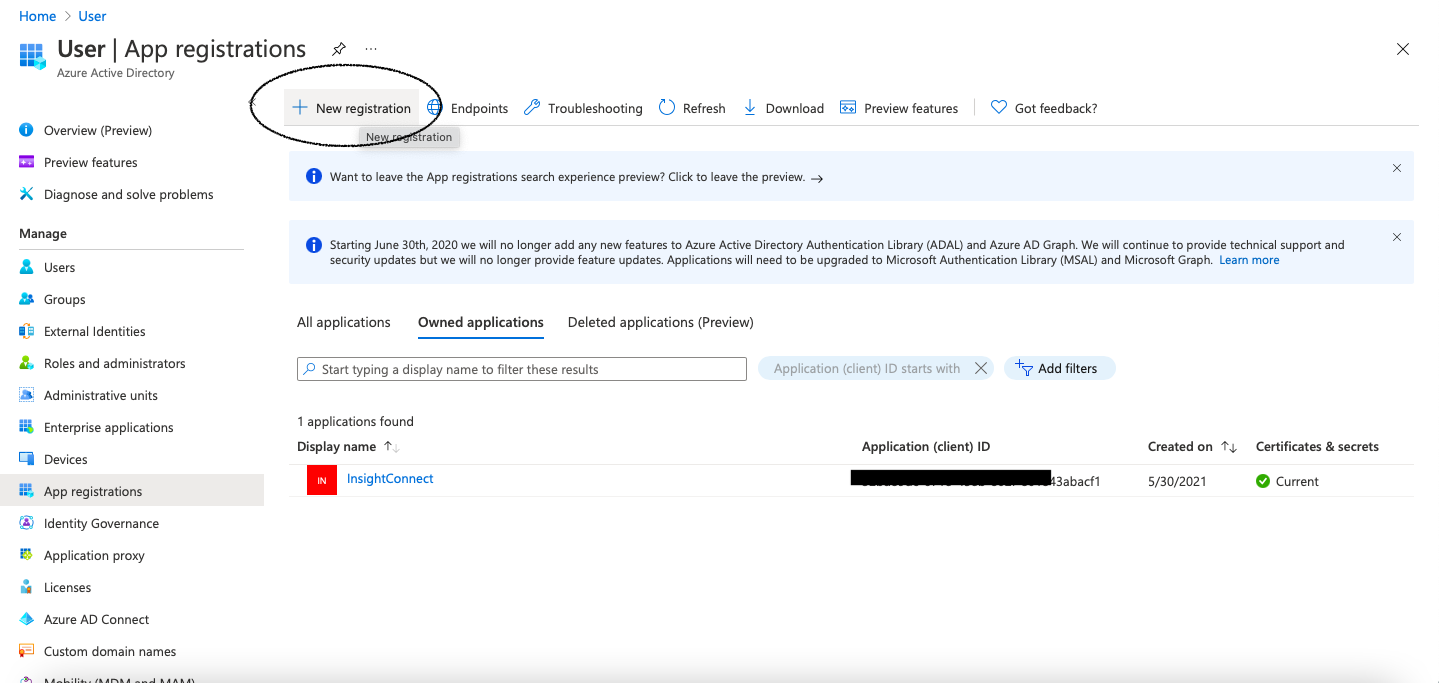
In the side navigation of the Azure portal, click Azure Active Directory, then select App Registrations in the secondary navigation menu.
-
Click New Registration.
-
Complete the form with the following:
- Name: Automation (InsightConnect)
- Redirect URL: The platform type is
Web app/API, and the URL ishttps://login.microsoftonline.com.
- Click Register.
- Copy and save the Application ID.
- Within the newly registered application, select Certificates & Secrets.
Application Secret Key
Azure uses asymmetric keys to authenticate and secure communications with other applications. You will need to create a new key in Azure to use for configuring Automation (InsightConnect) connections.
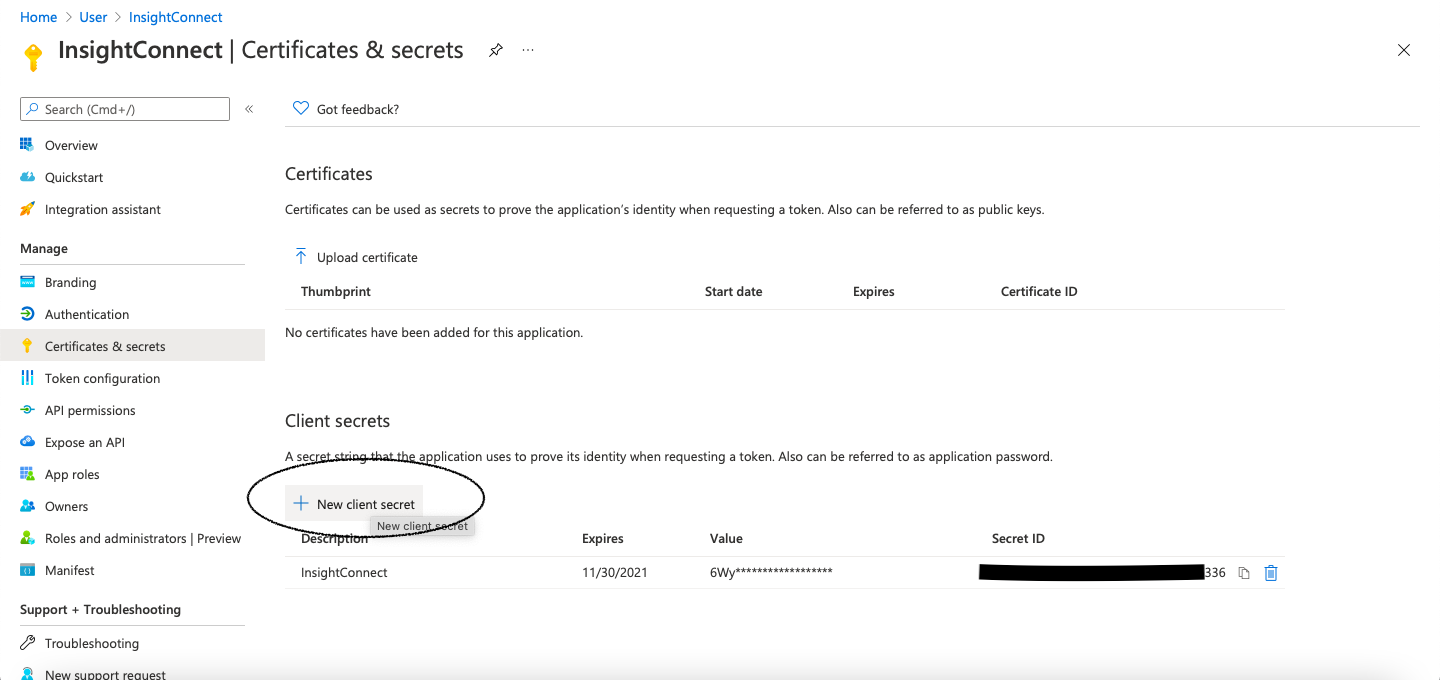
- Click on Certificates & Secrets.
- Select New client secret.
- Give the key a description and set its duration. Take note of the expiration date you provide, as this app registration will no longer function within Automation (InsightConnect) upon expiration.
- Click on Add.
- Azure will generate a value for your new key. In Azure, this secret key will be labeled as
Value. Copy and save this value, as it will be used later to establish a Microsoft Teams connection within Automation (InsightConnect).
Configure Application Permissions
After registering a new Application in Azure, you will need to configure permissions needed for Microsoft Teams.
The Microsoft Teams plugin needs the following permissions to work correctly:
- Delegated Permissions:
Chat.ReadWriteGroup.ReadWrite.All
- Application Permissions:
Directory.ReadWrite.AllGroup.ReadWrite.All
Please note that only the Delegated Permissions are necessary for the “New Message Received” trigger and the various Send Message actions to function in Automation (InsightConnect).
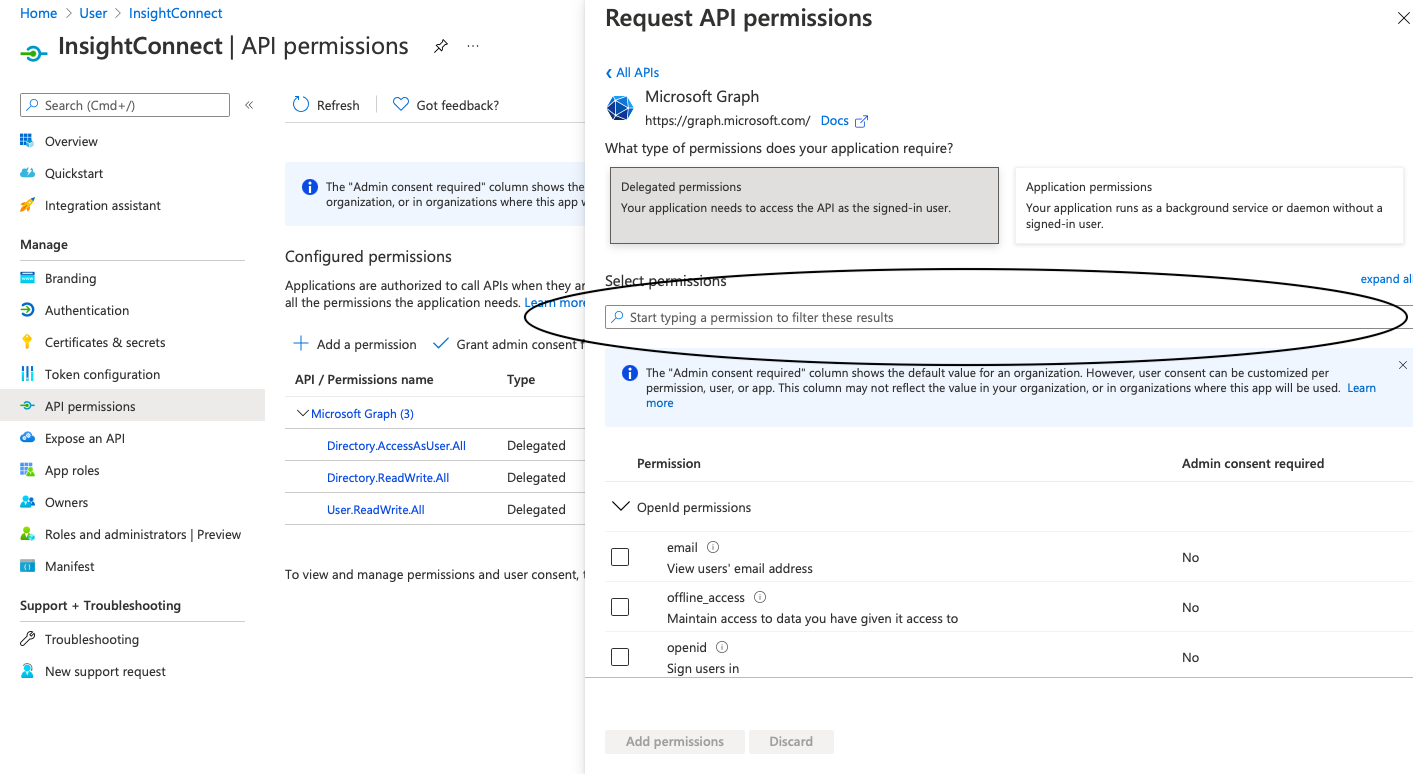
- In the side menu within Azure, navigate to API Permissions.
- Click on Add Permision, then select Microsoft Graph, and choose Delegated Permissions.
- Check the following options:
Chat.ReadWrite, Group.ReadWrite.All - Next, switch from Delegated Permissions to Application Permissions.
- Check the following options:
Directory.ReadWrite.All, Group.ReadWrite.All - Click on Add Permissions.
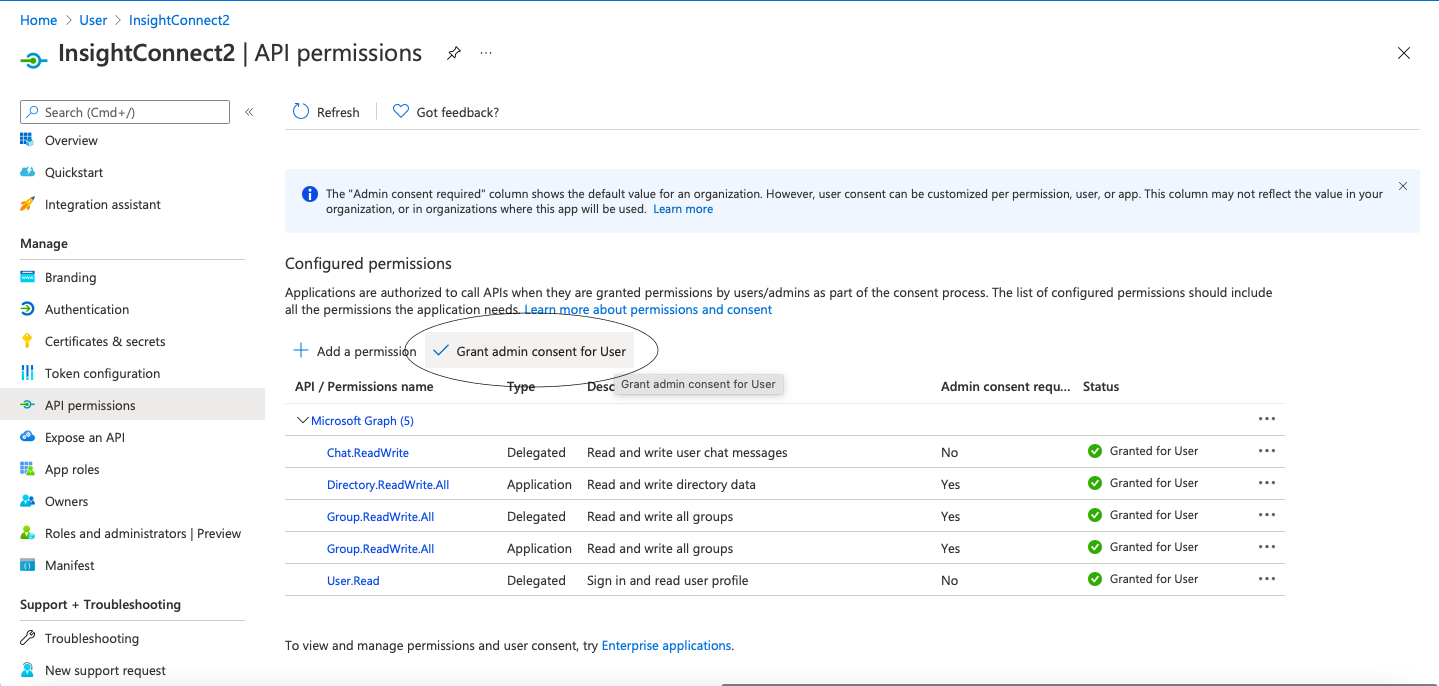
Grant Access For Users
Grant access to users must be enabled. This can be done in the same menu where you have created Application permissions. Select and click Grant admin consent for Users.
User Permissions for Teams Management
Users will need elevated permissions in the following scenarios to perform administrative actions within Microsoft Teams:
- To “Create Team Enabled Group”—the user must be in the Global Administrators Group. Since team enablement requires changing the properties on a group, the user must be a Global Admin.
- To add/remove users from a group, create channels, or remove users from channels—the user must be in the User Administrators Group.
No elevated permissions are required to use the New Message Received trigger from Microsoft Teams or to send messages to users or channels.
Configure the connection in Automation (InsightConnect)
Login to Automation (InsightConnect), expand the Settings drop-down and navigate to Plugins & Tools. Click “Add Plugin” and import the “Microsoft Teams” plugin. If already imported, please ensure you update plugin to the newest version.
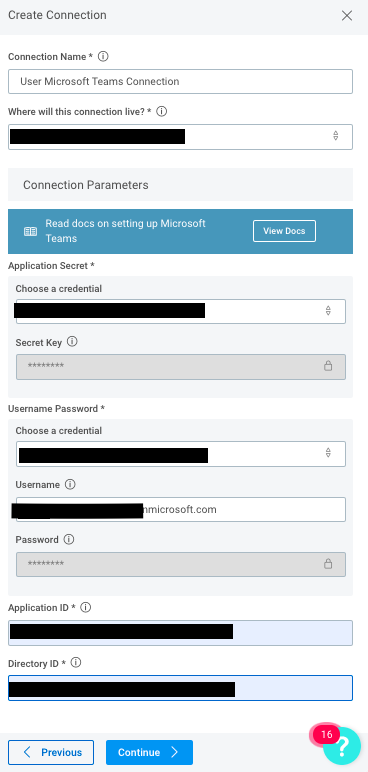
Now go to the Connections tab and create a new Connection. Select the Microsoft Teams plugin from the drop-down menu and complete the following steps:
- Under
Application Secret, enter the Secret Key that was previously created. Note that the Secret Key is labeled asValuein Azure. - Under
Username Password, enter the credentials used for the service account that was previously created. - Enter the Application ID. This is labeled as
Application (client) IDin Azure and can be found on the Overview tab for the application. - Enter the Directory ID. This is labeled as
Directory (tenant) IDin Azure and can be found on the Overview tab for the application.
Automatically Extract Indicators from a Microsoft Teams Message
Instead of constantly switching contexts in different tools, you can configure your chat solutions within Automation (InsightConnect) to listen for message commands that will kick-off workflows.
Automation (InsightConnect) also support message threading in both Slack and Microsoft Teams so you can conveniently organize your chat communications. Additionally, Automation (InsightConnect) maintains a growing library of prebuilt workflow templates that trigger functionality from Slack and Microsoft Teams that can be imported with one click.
The Microsoft Teams plugin automatically extracts commands and common network or security indicators from your messages. You can use these variables to configure additional workflow actions without having to worry about configuring potentially complex regex or pattern match steps.
To configure a workflow to kick-off from a Microsoft Teams message, update the Microsoft Teams trigger (the first step in your workflow) with the channel name to monitor your Microsoft Teams environment. Then, to run your workflow, send a message to the specified Microsoft Teams channel.
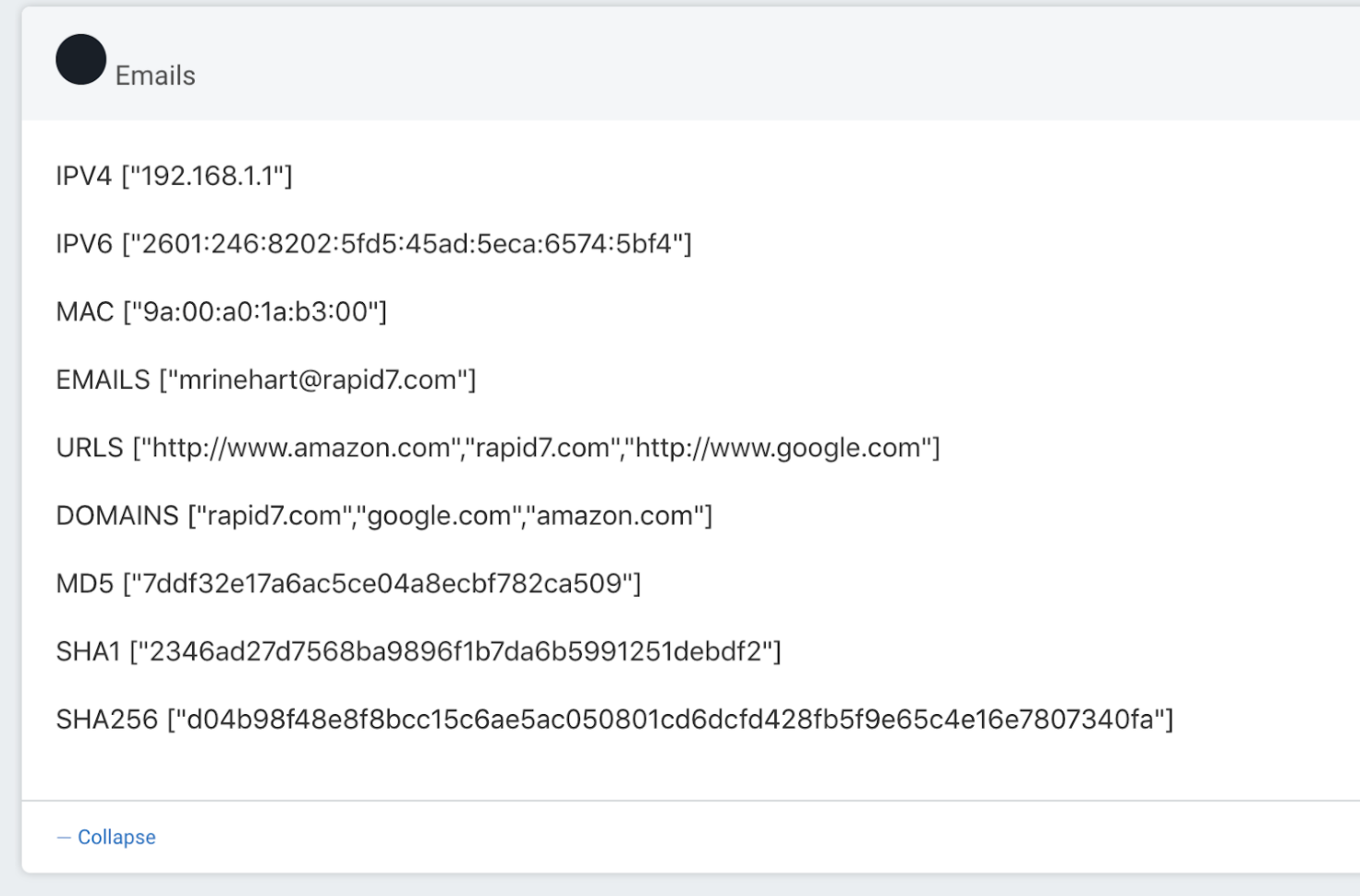
Each of your Microsoft Teams messages follows the same format: [command] [indicator]. An example command might look like this: !block-host 1.1.1.1. Automation (InsightConnect) automatically extracts and captures commands, like block-host in this case, in a variable called $first_word.
When your command is followed by a commonly used network or security indicator, our chatbot detects the format of the indicator, extracts it automatically, and stores it in an output variable.
These are the commonly used network and security indicator types we capture and store:
- IP addresses (IPv4 and IPv6)
- MD5 hashes
- SHA1 hashes
- SHA256 hashes
- MAC addresses
- Email addresses
- Domain names
- URLs
You can use these output variables later in your workflow to easily configure further actions. For example, add a hash to a denylist, enrich a URL or domain with a threat intelligence plugin, delete an email from user inboxes, or block an IP address, all without having to parse these indicators out of your chat messages manually.
Other helpful information
- Add or delete users using Azure Active Directory
- Get access on behalf of a user
- Delegated Permissions
- Graph Permissions Reference
- Administrator roles by admin task in Azure Active Directory
Troubleshoot the Microsoft Teams Plugin
Provisioning a federated user
If you are in the process of provisioning federated or single-sign-on accounts in your environment, this will not work for our plugin. A non-federated user account in the onmicrosoft.com domain is required for this connection.
Error messages to look for:
AADSTS50126 - Error validating credentials due to invalid username or password. That specific error code can indicate that the user account is federated. For more information, read the Microsoft article at https://docs.microsoft.com/en-us/answers/questions/38035/aadsts50126-invalid-grant-error-validating-credent.html .
Including unnecessary permissions that cause interference
Sometimes, adding additional permissions to the app registration in Azure can cause conflicts.
For example, our plugin requires Chat.ReadWrite (delegated) in order to successfully send and receive messages. There are other delegated Chat permissions available within Azure, such as Chat.Read, which you may instinctively assume they should include as well. Microsoft generally leverages a “least first” mentality with permissions, so if an application is given the Chat.Read permission in addition to Chat.ReadWrite, Chat.Read will take precedence, and potentially cause errors.
Other common issues
Authentication to Microsoft Graph failed - If you have not manually logged in to the new user account at portal.office.com to update the password, this error can occur during connection tests. Microsoft will typically treat the user’s initial password as temporary, and require a password change upon first login. Try logging in to reset the password, update the credential in Automation (InsightConnect), then rerun the connection test.
Unnecessary application permissions - If you’ve added any permissions to the registered app outside of the ones listed in our documentation, this can cause conflicts and result in failed plugin functionality. Ensure that the configured permissions align with the ones noted in this documentation.