Honey Files
A honey file is a fake file located on a network file share. Honey files are designed to detect attackers who are accessing and potentially removing data from your network. Attackers will often find a file share on a network, zip the contents of the share into a folder, and dump the data for offline analysis. Because a honey file serves no true purpose, you should never access, modify, or move a honey file. Any such attempts will trigger the Honey Filed Accessed detection rule.
Avoid unnecessary noise and false positive detections
Windows Explorer views that display a preview of the files’ contents can generate false positive detections when users browse directories that contain honey files. Previews of files are indistinguishable from intentional file openings. You may want to consider placing your honey files in alternate directories that users would not be expected to browse in Windows Explorer. You could also use a file extension that does not produce a file preview in Windows Explorer to avoid these false positive detections.
Before You Begin
Before you configure a honey file, complete the following procedure:
- Install the Rapid7 Agent (Insight Agent) on the Windows server hosting a network file share.
- Enable the “Audit Detailed File Share” logging, if it is not already enabled. This can be configured in Group Policy or in the system’s Local Security Policy.
- Create a new file in the desired location on the network file share. The file can be of any type, name, or content.
- Make note of the full path to the file.
Configure Honey Files on your System
To configure a honey file on your system:
- The files that will be configured as honey files must be located on a system running a Rapid7 Rapid7 Agent (Insight Agent). In this example, there are two files that will be used as “honey files.”
- The detection rule for Honey File Access is only triggered when these files are accessed from a network share. In this example, the HR folder has also been shared.
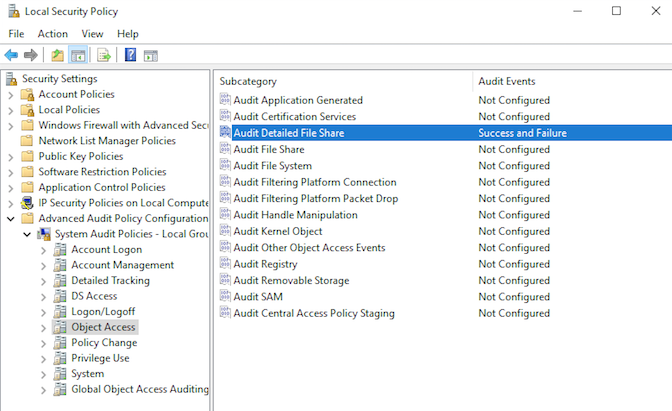
- You must now enable auditing on your Local Security policy.
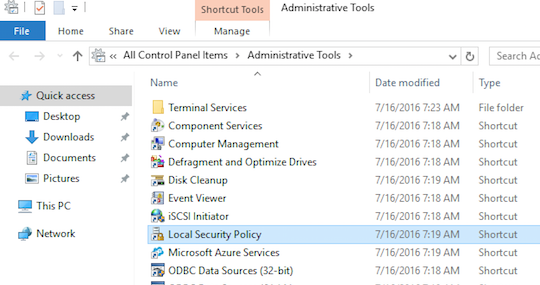
- In either group policy or the Local Security Policy tool, enable auditing.
- Select Advanced Audit Policy Configuration.
- Select Object Access.
- Open the properties for “Audit Detailed File Share.”
- Enable auditing for “Success and Failure.”
- Save this change.
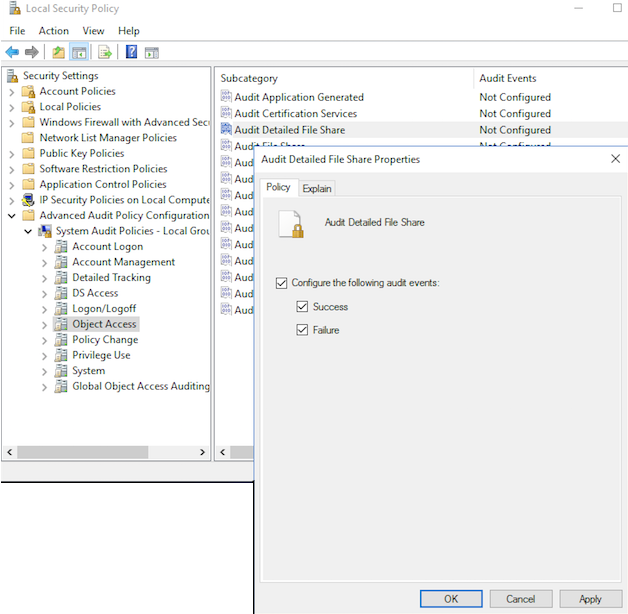
- When you are done with the changes, “Audit Detailed File Share” should have both “Success” and “Failure” auditing enabled.
Configure a Honey File in SIEM (InsightIDR)
To configure a honey file in SIEM (InsightIDR):
- From your SIEM (InsightIDR) homepage, select Settings on the left menu.
- Find and select Deception Technology in the list and click the Honey Files tab. Click the Add a new honey file button in the top right corner.
- A panel will appear. Enter the full local path to the file, as the Rapid7 Agent (Insight Agent) would see it. For example, enter:
C:\path\to\directory\filename.egrather than\\hostname\path\to\directory\filename.eg. - Select the asset that you previously configured.
- Click Add.
- You can add more than one honey file.
Test Your Honey Files
Access the Honey File from across the network
Local access will not cause a Honey File Access detection to trigger.
Additionally, accessing the file by using a hidden share will not trigger a Honey File Access detection.
Any type of access to the honey files from the non-local network will trigger a detection.
- Navigate to the system that contains the honey file from across the network.
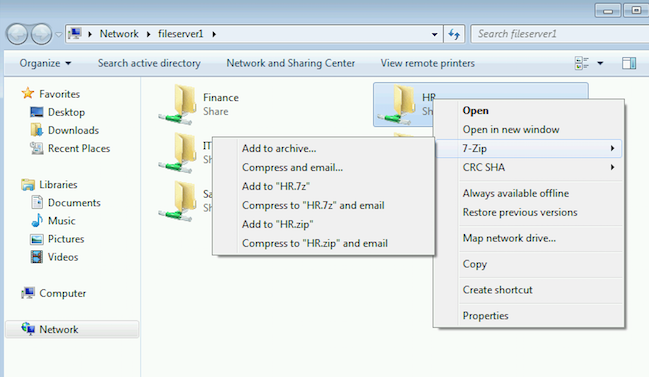
- Browse to the location of the honey file, and zip up the folder, which will trigger a detection.
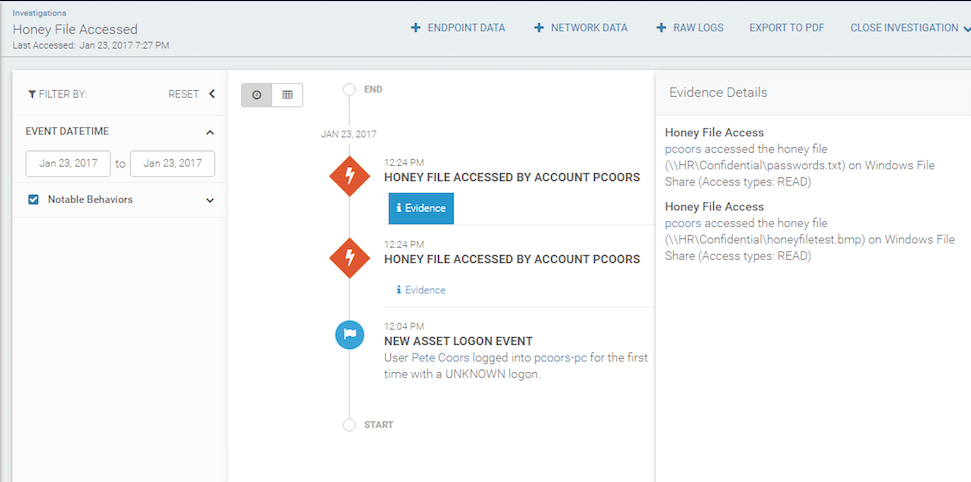
The example below shows an intruder zipping a file from an HR folder.
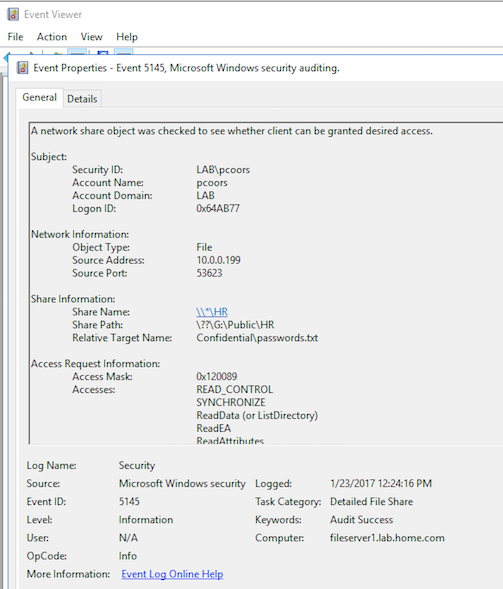
- The honey file access will trigger an event in your Security Log where the honey file(s) reside(s) as 5145 EVID.
- You should receive an investigation with an alert generated by a Honey File Access detection rule. In the investigation, the evidence for the alert includes the source user and asset.
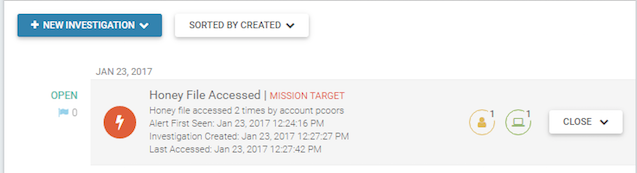
- Open the investigation to view the alert evidence.