Compromised and Vulnerable Hosts Report
The Compromised and Vulnerable Hosts Report details all target hosts on which Metasploit opened a session, successfully ran a module, or recorded a vulnerability.
Host vs Target Host
Generated reports refers to “target host” as “host”.
Project Summary
The Project Summary section summarizes the project administration data.
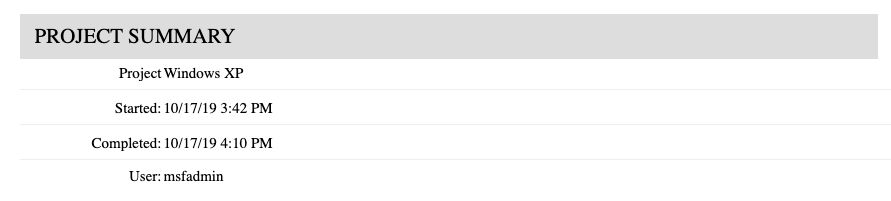
- Name - The name of the project name.
- Started - Date and time the project was created.
- Completed - Date and time the project was last updated.
- **User - **User that generated the report.
Executive Summary
The Executive Summary summarizes the number of hosts, services, modules, and logins. It also lists the most common modules and if a successful session was opened

Compromised Hosts Report Summary
The Compromised Hosts Report Summary goes over the purpose of the report.

Compromised Hosts by Exploit
The Compromised Hosts by Exploit lists any session opened against a target host.
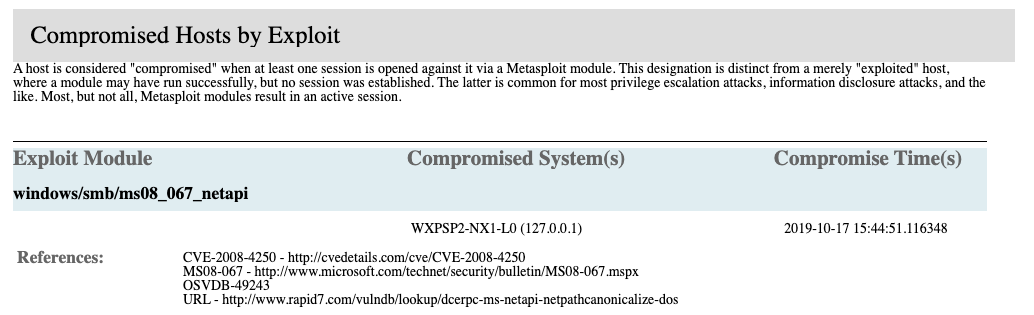
- Exploit Module -Name of the module used in the attack .
- References - Any references for the module, such as CVE and origin.
- Compromised Systems(s) - The system the session opened in, including the hostname and IP address.
- Compromised Time(s) - Date and time the target host was compromised using the format
yyyy-mm-dd hh:mm:ss:fffffffff.
Discovered Vulnerabilities
The Discovered Vulnerabilities section lists any vulnerabilities that are successfully exploited on the target host.
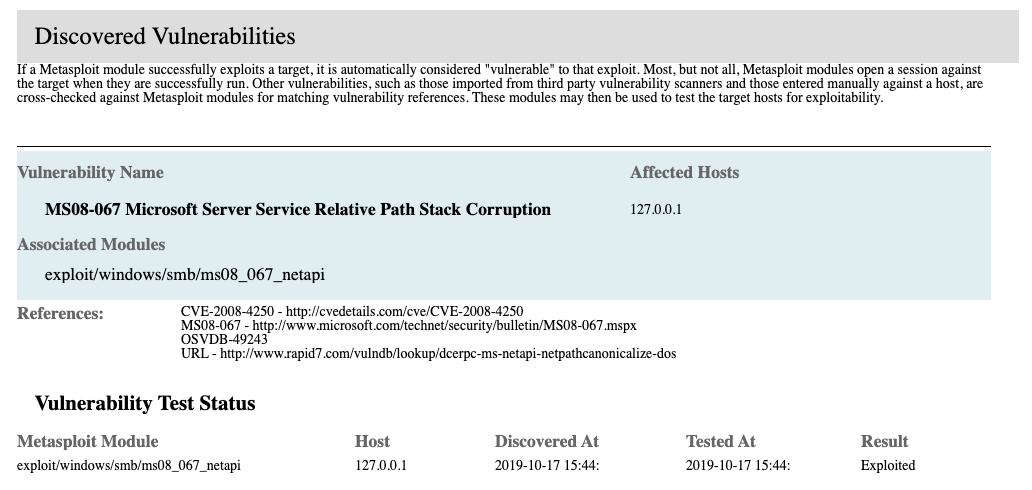
- Vulnerability Name - Name of the vulnerability.
- Affected Hosts - Any target hosts the vulnerability was successfully used against.
- Associated Modules - Modules the vulnerability is part of.
- References - Any references to the module, such as CVE and origin.
- Vulnerability Test Status - Status of the vulnerability test against the host.
- Metasploit Module - Name of the module in Metasploit.
- Host - Host IP address.
- Discovered At - Date and time the exploit was discovered using the format
yyyy-mm-dd hh:mm:ss:. - Tested At - Date and time the exploit was tested using the format
yyyy-mm-dd hh:mm:ss:. - Results - Results of the test. The result can be “Not tested” or “Exploited.”
Login Details
The Login Details list out the available login information for the exploited hosts.
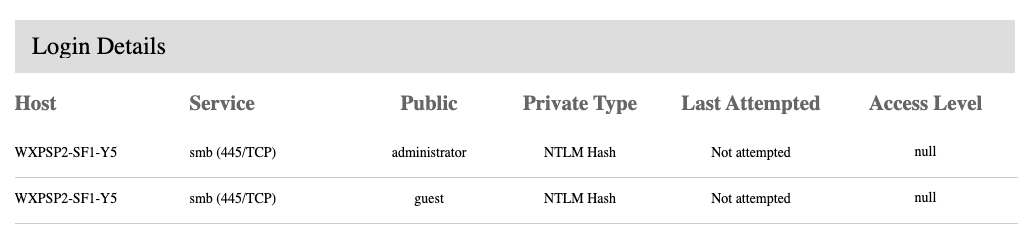
- Host - Name of the host.
- Service - The program exposed by the target on a network port.
- Public - The username.
- Private Type - Additional details about the private credential type.
- Last Attempted - Date and time the public and private type were attempted.
- Access Level - The level of access the public and private type offer.
- user
- guest
- RO (read-only)
- RW (read-write)
- Null (unsure or unknown)
Public and Private Type
“Public” and “Private Type” are typically the username and password. The username is the public part, while the password is the secret or private type.
Compromised and Vulnerable Hosts Options
The following options are available for generating the Compromised and Vulnerable Hosts Report.
- File Formats - HTML, PDF, RTF, Word
- Name - Name of the report
- Address Settings - Specify Included Addresses and Excluded Addresses to configure the scope of the report, or leave blank to include all the hosts associated with this project. Hosts with addresses outside the allowable range(s) will not be included in the reported data. Entries may be specified as single addresses (192.168.1.1), dashed entries (192.168.1.1-192.168.1.100), wildcards (192.168.1.*), or using CIDR notation (192.168.1.0/29).
- Cover Logo - If no logo is upload, the Rapid7 logo is used
- Sections - Sections as labeled in the User Interface may not match the exported report.
- Project Summary = Project Summary
- Executive Summary = Executive Summary
- Compromised Summary = Compromised Hosts Report Summary
- Compromised Hosts = Compromised Hosts by Exploit
- Vulnerabilities and Exploits = Discovered Vulnerabilities
- Login Details = Login Details
- Email Report - List of comma or semicolon separated addresses to send the report to
Additional Resources
- LM, NTLM, Net-NTLMv2, oh my! - https://medium.com/@petergombos/lm-ntlm-net-ntlmv2-oh-my-a9b235c58ed4
- What is an SMB Port + Ports 445 and 139 Explained - https://www.varonis.com/blog/smb-port/