Segmentation and Firewall Testing MetaModule
When firewalls have badly configured or lax egress traffic filtering policies, they open the network up to attacks from reverse shells, data exfiltration, and other forms of exploitation. In order to identify the open ports that allow outbound traffic and to verify that your egress filtering policies properly block traffic, you can run the Segmentation and Firewall Testing MetaModule.
The MetaModule runs an Nmap SYN scan against an egress target to reveal the outbound ports that are open from an internal host. It identifies the state of the ports in your firewall based on the traffic received by the server. If the server receives the traffic, then the MetaModule flags the port as open. If the firewall blocks the traffic, the MetaModule flags the port as filtered. The MetaModule tags the remaining ports as unfiltered or closed depending on the their response to connections. After the MetaModule completes its run, it generates a report that provides you with a comprehensive look at port state distribution and unfiltered ports. Egress Scan Target The egress target, egadz.metasploit.com, is a server hosted by Rapid7 and has been set up to have all 65,535 ports open. Each port is configured to respond with a single SYN-ACK packet. In its default configuration, the MetaModule initiates a port scan using Nmap’s default 1000 most common ports; however, if you need to include additional ports, you can define a custom port range. Port States The Segmentation and Firewall Testing MetaModule uses the following states to categorize ports.
- Open - A port is assigned an open state if it allows traffic out of the network and the EGADZ server receives it. An open state indicates that there is an application that is actively accepting TCP connections, UDP datagrams or SCTP associations.
- Filtered - A port is assigned a filtered state if it drops the traffic before it reaches the desired port on the EGADZ server. It will not receive a response from the EGADZ server. Typically, a port has a filtered state if a dedicated firewall device, router rules, or host-based firewall software has successfully blocked the port from sending traffic.
- Closed - A port is assigned a closed state if it allows traffic through the port, but there is not an application or service bound to the port. A closed port can be used to determine if t a host is up on an IP address.
- Unfiltered - A port is assigned an unfiltered traffic if it allows traffic through to the port, but it cannot be determined whether the port is open or closed. Setting Up an Egress Testing Server The Firewall Egress Testing MetaModule uses an external server hosted by Rapid7 to identify open outbound ports from an internal host. In some cases, you may want to set up and your own egress testing server. For example, if you want to test egress between different endpoints or if you do not want to send data to a server on the Internet, you can set up a custom egress testing server.
To help you set up a custom egress testing server, Metasploit Pro provides you with a script that you can run on an Ubuntu 12.04 LTS server. The script can be downloaded from the Projects page.
Egress Testing Server Requirements
To set up an egress testing server, you need to perform the following tasks:
- Set up a Linux machine with your favorite distribution.
- Add two network interfaces, or network adaptors, to the Linux machine. Each network interface should have an IP address.
For more information on setting up a network interface on a virtual machine, please visit the documentation for your virtualization software.
- Assign one IP address as the administrative interface. This interface will be used to control the egress testing server. It should be assigned to the eth0 interface.
- Assign the second IP address as the egress testing server. This interface should be assigned to the eth1 interface.
- Download and run the egress testing server script.
Set Up a Custom Egress Target
To set up a custom egress target, you will need an Ubuntu 12.04 box that is configured with two IP addresses. The two IP addresses are needed for the following interfaces:
- The admin interface - This is usually found on the eth0 interface and will be used for controlling the egress server.
- The egress server - This is usually found on eth1, or a virtual interface such as eth0:1. This is the IP address you will scan from the Firewall and Segmentation Testing MetaModule.
After you set up the box with two addresses, perform the following steps:
- Log in to the Metasploit Pro web interface.
- Click the Segmentation Target Setup Script button located under the Global Tools.
The download process will automatically start.
If your browser is not configured to automatically download files, a dialog window will appear and prompt you to save the file. You will need to save the file to your computer.
- Follow the instructions provided in the
create-egadz.shscript to set up the egress target. - Verify that you are able to set up an egress target using the instructions.
After you have set up the egress target, you can run the Segmentation and Firewall Testing MetaModule. Running the Segmentation and Firewall Testing MetaModule
- From within a project, select Modules > MetaModules.
- Find the Segmentation and Firewall Testing MetaModule and click the Launch button.
The Segmentation and Firewall Testing configuration window appears. 3. From the Scan Config tab, choose one of the following scan target options:
- Use default egress target - The MetaModule runs against the egress server that Metasploit has set up for testing outbound traffic.
- Use a custom egress target - The MetaModule runs against a server that you have set up for testing outbound traffic. You can specify an IP or a fully qualified domain name. To learn how to set up a custom egress target, go to the Global Tools area located on the Projects page and download the Segmentation Target Setup Script. You can follow the instructions provided in the script to create a custom egress server.
- From the Scan Config tab, choose one of the following port range options:
- Use default nmap port set - Scans Nmap’s 1000 most common ports.
- Use a custom port range option - Scans the range of ports that you define.
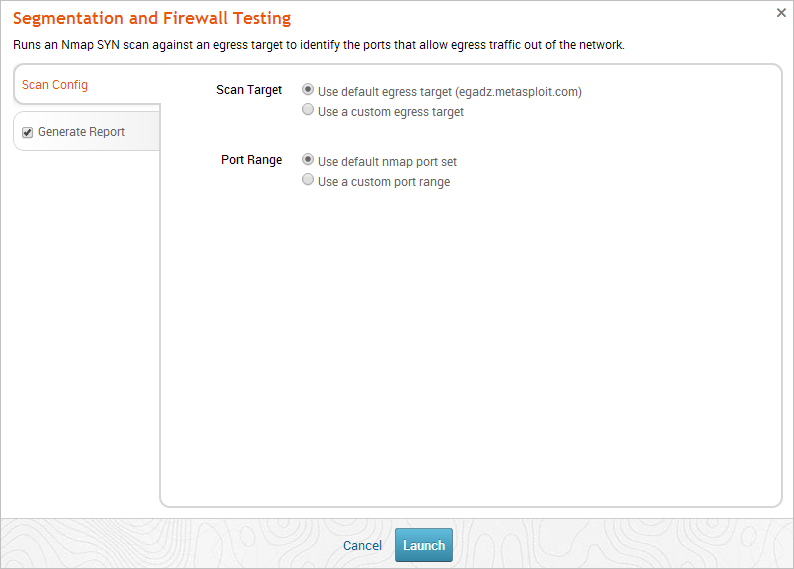
- Click the Generate Report tab. The Report configuration form appears.
- Enter a name for the report in the Report Name field, if you want to use a custom report name. Otherwise, the MetaModule uses the default report name.
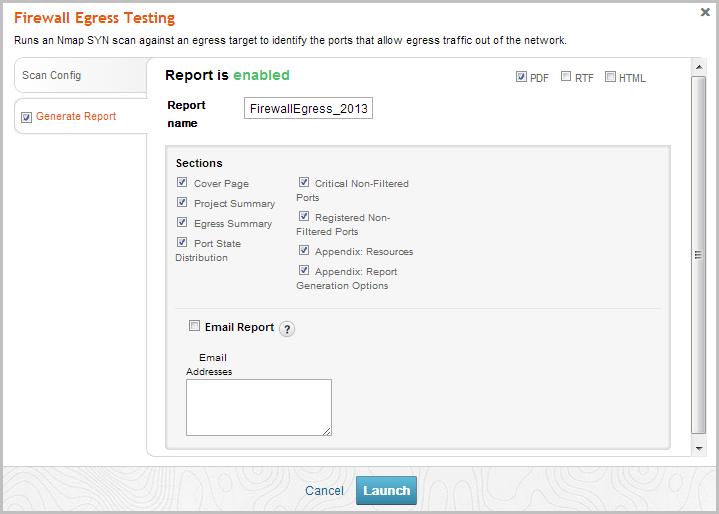
- From the Sections area, deselect any sections you do not want to include in the report. Skip this step if you want to generate all the report sections.
- Select the Email Report option if you want to email the report after it generates. If you enable this option, you need to supply a comma separated list of email addresses.
If you want to email a report, you must set up a local mail server or email relay service for Metasploit Pro to use. To define mail server settings, select Administration > Global Settings > SMTP Settings.
- Click the Launch button.