Adjusting risk with criticality
The Risk Score Adjustment setting allows you to customize your asset risk score calculations according to the business context of the asset. By adjusting the risk score calculations using modifiers, you can better represent the risk of assets in your environment.
You must enable Risk Score Adjustment for the criticality levels to be taken into account in calculating the risk score; it is not set by default.
Adjusting risk with criticality only applies to your asset risk scores
You may adjust your asset risk scores by applying criticality tags. Vulnerability risk scores cannot be adjusted using modifiers.
Example use case: Criticality for the assets of senior executives
If you have set the Very High criticality level for assets belonging to your organization’s senior executives, you can configure the risk score adjustment so that those assets will have higher risk scores than they would have otherwise. You can specify modifiers for your user-applied criticality levels that will affect the asset risk score calculations for assets with those levels set.
Applying criticality tags
When applying criticality tags, an asset risk score multiples by the risk score factor associated with the tag. Adjust the risk score factor associated with individual criticality tags.
When applying criticality tags, consider the following constraints:
- Each modifier must be greater than 0.
- You can specify up to two decimal places. For example, frequently-used modifiers are values such as .75 or .25.
- The numbers must correspond proportionately to the criticality levels. For example, the modifier for the High criticality level must be less than or equal to the modifier for the Very High criticality level, and greater than or equal to the modifier for the Medium criticality level.
- The numbers can be equal to each other. For example, they can all be set to 1.
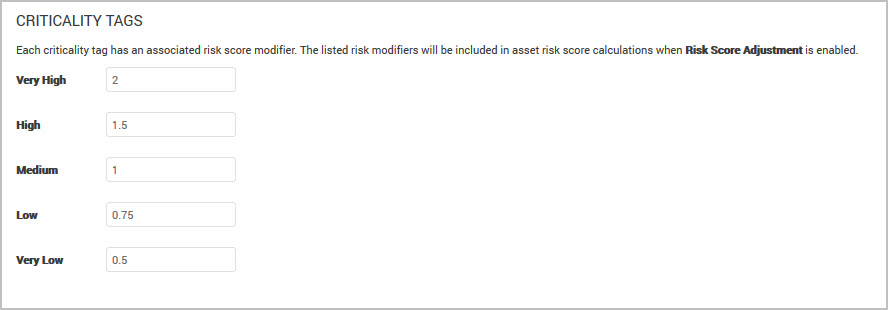
The default criticality values are:
- Very High: 2
- High: 1.5
- Medium: 1
- Low: 0.75
- Very Low: 0.5
Adjust risk scores based on criticality
- On the Administration page, under Vulnerabilities, click Risk Score Settings.
- On the Global Settings page, select the Risk Score Adjustment tab.
- Select the Adjust asset risk scores based on criticality box.
- In the Criticality Tags section, fill out the fields with the value you want for each tag.
Interaction with risk strategy
The Risk Strategy and Risk Score Adjustment are independent factors that both affect the risk score.
To calculate the risk score for an individual asset, the Security Console uses the algorithm corresponding to the selected risk strategy. If Risk Score Adjustment is set and the asset has a criticality tag applied, the application then multiplies the risk score determined by the risk strategy by the modifier specified for that criticality tag.
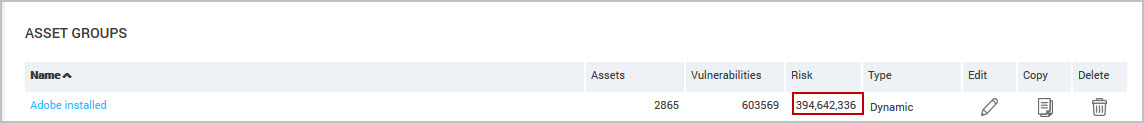
The risk score for a site or asset group is based upon the scores for the assets in that site or group. The calculation used to determine the risk for the entire site or group depends on the risk strategy. Note that even though it is possible to apply criticality through an asset group, the criticality actually gets applied to each asset and the total risk score for the group is calculated based upon the individual asset risk scores.
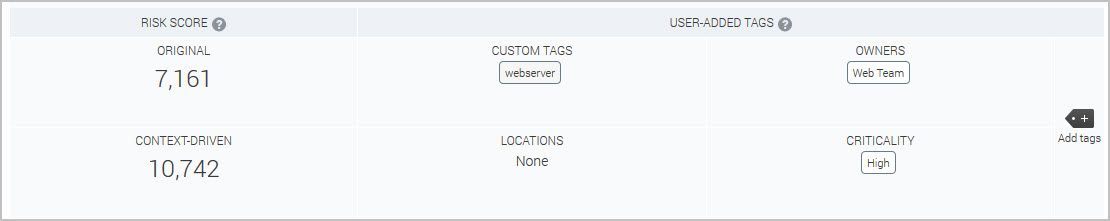
Viewing risk scores
If Risk Score Adjustment is enabled, nearly every risk score you see in your Security Console installation will be the context-driven risk score that takes into account the risk strategy and the risk score adjustment. The one exception is the Original risk score available on the page for a selected asset. The Original risk score takes into account the risk strategy but not the risk score adjustment. Note that the values displayed are rounded to the nearest whole number, but the calculations are performed on more specific values. Therefore, the context-driven risk score shown may not be the exact product of the displayed original risk score and the multiplier.
When you first apply a criticality tag to an asset, the context-driven risk score on the page for that asset should update very quickly. There will be a slight delay in recalculating the risk scores for any sites or asset groups that include that asset.
Risk score hierarchy
The risk score from every vulnerability found on a particular asset is aggregated to obtain an overall asset risk score. This score is normalized to a range between 0 and 1000. To ensure that not too many low-severity vulnerability risk scores overwhelm important high-severity ones, asset risk scores are skewed towards the highest vulnerability risk scores found on an asset. Assets can be organized into Asset Groups. Asset groups are used to categorize similar or related assets for monitoring purposes. An asset group’s risk score is an aggregate of all individual asset risk scores found within the group. A Site risk score is also generated. It is a calculation derived from all assets within a given site. In addition to asset risk scores, you can create a Criticality Tag to prioritize and label the level of urgency required when performing remediation on a specific asset.