Automate Leaked Credentials with Active Directory
When a leaked credentials alert is created, you can validate the credentials against the company Active Directory to determine which users may be exposed. They may belong to expired accounts or the passwords may be expired, which would render them useless.
You can use the Digital Risk Protection (Threat Command) to automate validation of those credentials against the company AD. In addition, you can set a remediation action, either to block that user from logging in or requiring a password reset.
Validation against AD can show not only how many user credentials were found, but also how many of those were active usernames with valid passwords. This information is shown in the alert header.
Only one Active Directory validation can be active, either Azure AD in the cloud or Microsoft AD.
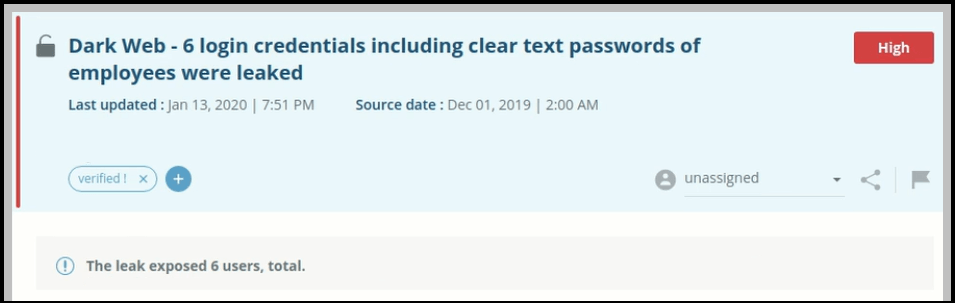
This figure illustrates an alert without AD validation:
This figure illustrates the same alert with AD validation:
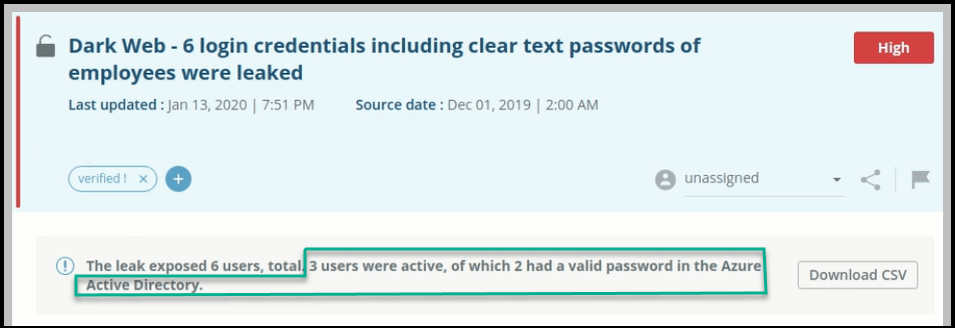
The alert with AD validation shows not only a count of the the total leaks, but also - based on AD validation - how many of the leaked usernames were active and how many of those had valid passwords.
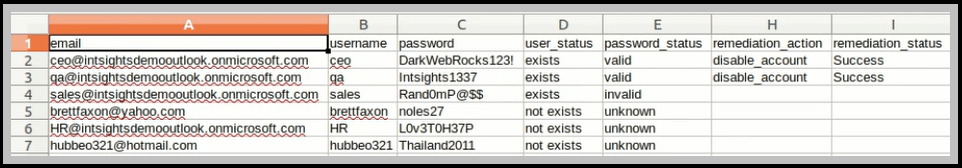
In addition, in the AD-validated alert, you can download a CSV that shows the leaked credentials, whether they validated in the AD, and whether any remediation action took place: