Data Leakage Scenario Rule Conditions
This topic describes the conditions that you can use to create rules and the default rules provided for the data leakage scenario.
Data leakage includes the following scenarios:
Each scenario has its own conditions and default rules.
Ransomware leaks
Ransomware - conditions
The following table describes the conditions that you can use to create rules. When using a regular expression, don’t surround the expression with quotation marks.
| Features | Operator | Value | Description |
|---|---|---|---|
| Detection algorithm | identified/did not identify | ”A relevant ransomware leak” | Did the Rapid7 internal detection algorithm identify a ransomware leak? |
| Asset tag | in/not in | Select tags | Are any of the threat’s matched assets tagged with any of the specified tags? |
| Attacked company name | contains/does not contain | ”Asset name” | Does the name of the attacked company contain a specific company asset? |
| Attacked company name | contains/does not contain | ”Regex list” | Does the name of the attacked company contain a pattern (can be expressed as a regular expression)? |
| Attacked company regions | in/not in | List of regions | Did the leak occur in selected geographical regions? |
| Attacked company sectors | in/not in | List of sectors | Did the leak occur in selected sectors? |
| Days since first reported | =, !=, >=, <=, >, < | How many days ago was the leak first reported by Rapid7? | |
| Days since publication date | =, !=, >=, <=, >, < | How many days ago was the leak published? | |
| File content | contains/does not contain | ”Asset name” | Does the content of at least one leaked file contain a specific company asset? |
| File or folder name | contains/does not contain | ”Asset name” | Does at least one leaked file or folder name name contain a specific company asset? |
| Leak name | contains/does not contain | ”Asset name” | Does the name of the leak contain a specific company asset? |
| ”Regex list” | Does the name of the leak contain a pattern (can be expressed as a regular expression)? | ||
| Leak publish status | is, is not | Is the leak publication status full, partial, or unknown? | |
| Leak URL | contains/does not contain | ”Regex list” | Does the URL of the leak contain a pattern (can be expressed as a regular expression)? |
| Number of matched files | =, !=, >=, <=, >, < | How many leaked files contain a company asset in the file name or content? | |
| Number of matched folders | =, !=, >=, <=, >, < | How many leaked folders contain a company asset in the folder name? | |
| Number of matched objects | =, !=, >=, <=, >, < | How many leaked objects (files or folders) contain a company asset in the file name, content, or folder name? | |
| Ransomware group name | contains/does not contain | ”Regex list” | Does the ransomware group name contain a pattern (can be expressed as a regular expression)? |
Ransomware - default rule
The following table lists the rules that are provided to get you started quickly.
| Rule name | Description of match | Default state |
|---|---|---|
| Digital Risk Protection (Threat Command) Ransomware Leaks | Did the Rapid7 internal detection algorithm identify a ransomware leak? All threats that hold matched objects (at least one match between the file, folder name, or content and the asset) will be elevated as alerts. | Enabled |
Example uses
These examples show how you can use the Alert Profiler to fine-tune ransomware alert reporting.
Trigger an alert when a leak is published about a specific sector:
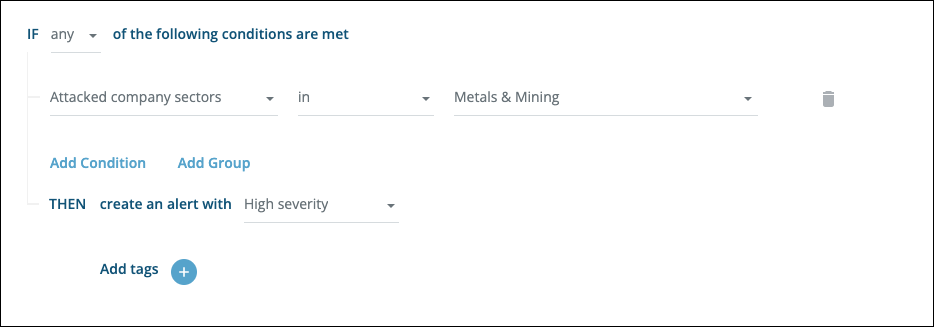
Trigger an alert when a specific ransomware group publishes a leak:
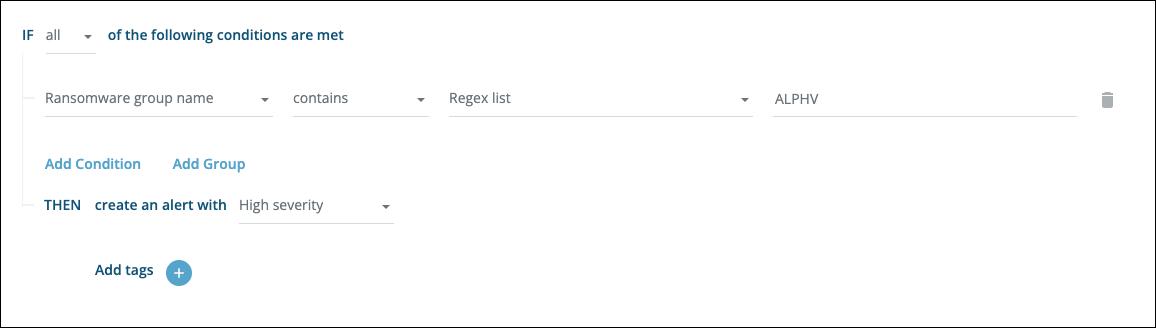
Trigger an alert when your assets are mentioned in any context (even if not deemed to be relevant):
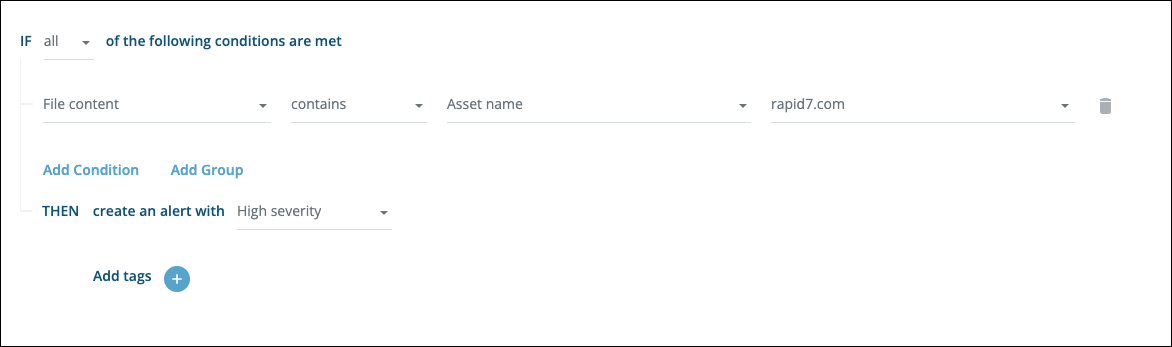
Confidential documents
Confidential documents - conditions
The following table describes the conditions that you can use to create rules. When using a regular expression, don’t surround the expression with quotation marks.
| Features | Operator | Value | Description |
|---|---|---|---|
| Detection algorithm | identified/did not identify | A confidential document | Did the Digital Risk Protection (Threat Command) internal detection algorithm identify an exposed confidential document? |
| Asset name | in/not in | Asset Name | Does the document match a specific company asset? |
| Asset tags | in/not in | Select tags | Are any of the threat’s matched assets tagged with any of the specified tags? |
| Author name | contains/does not contain | “regex list” | Does the document author name contain a pattern (can be expressed as a regular expression)? |
| contains/does not contain | Asset Name | Does the document author name contain a specific company asset? | |
| Document | contains/does not contain | regex list | Does the document contain a specific phrase (can be expressed as a regular expression)? |
| contains/does not contain | Asset Name | Does the document contain a specific company asset? | |
| contains/does not contain | Confidentiality terms list | Does the document contain a specific confidentiality term? | |
| Document URL | contains/does not contain | Asset Name | Does the document URL contain a specific company asset? |
| contains/does not contain | regex list | Does the document URL contain a specific phrase (can be expressed as a regular expression)? | |
| File | is/is not | ”Protected” | Is the file protected (by either a password or encryption)? |
| File name | contains/does not contain | regex list | Does the document name contain a pattern (can be expressed as a regex)? |
| contains/does not contain | Asset Name | Does the document name contain a specific company asset? | |
| contains/does not contain | Confidentiality terms list | Does the document name contain a specific confidentiality term? | |
| File type | in/not in | Closed list | Is the document a specific file type? |
| Last editor | contains/does not contain | regex list | Does the document last editor name contain a pattern (can be expressed as a regular expression)? |
| Location of confidentiality term | in/not in | Closed list | Is the confidentiality term located in a specific location in the document? |
| Weeks since creation date | =, !=, >=, <=, >, < | User types an integer number | How many weeks ago was the document created? |
| Weeks since last modification | =, !=, >=, <=, >, < | User types an integer number | How many weeks ago was the document last modified? |
Confidential documents - default rule
The following table lists the rules that are provided to get you started quickly.
| Rule name | Description of match | Default state |
|---|---|---|
| Confidential documents - Default Detection Rule | An exposed document was found to be related to your company and confidential, based on your assets | Enabled |
| Confidential documents - Extended DLP Detection Rule | An exposed document was found to be related to your company and generally confidential, based on common confidentiality terms. | Disabled |