Import CVEs from Tenable.io Integration
Integrate your Tenable.io Vulnerability Management cloud software account so you can import CVEs to Digital Risk Protection (Threat Command).
In addition to importing CVEs, you can enable the import of host information (host name, IP address, and last scan date). This data, which gives a better understanding of which assets are affected by each CVE, is displayed in the Affected Assets tab for each imported CVE.
Before you begin, ensure that you have the Tenable.io access key and secret key.
The Tenable.io keys must be created by a Tenable.io user with the role of “Administrator.”
Import CVEs from Tenable.io to Digital Risk Protection (Threat Command)
Import CVEs so you can manage them in Digital Risk Protection (Threat Command). CVEs from 30 days back are imported.
To import CVEs:
- From Digital Risk Protection (Threat Command), select Automation > Integrations.
- From the Integrations window, click Cloud.
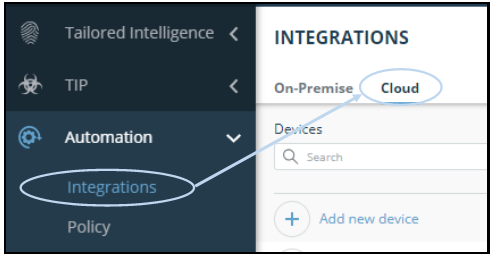
- Click Add new device.
- Type a user-defined name for the device.
The name can contain a maximum of 50 letters, spaces, numbers, and underscores. - For the Device type, select Tenable.io.
- Type the Access Key and Secret Key for the Tenable.io account.
- (Optional) To enable the display of host information, select Enable collection of host information.
- It is recommended to click Test Credentials to ensure that the credentials are valid.
If the credentials are not valid, a message is displayed. - Click Add.
The new device is added to the cloud integrations device list. Next to the device name, there is a red dot, indicating that communication has not yet been established. The dot will change to green when the device is synchronized.
Integration credentials are checked periodically. An email message will be sent to the administrator if credentials have expired.
Edit Tenable.io integration
You can edit the Tenable.io connection credentials.
To edit a connection:
- From the Digital Risk Protection (Threat Command) main menu, select Automation > Integrations.
- From the Integrations window, click Cloud.
- Select the integration to update.
The integration details are displayed. - (Optional) You can enable or disable the collection of host information.
- Make necessary corrections, then click Test Credentials.
If the credentials are not valid, a message is displayed. - Click Save.