Integrate a Microsoft Azure Sentinel Cloud Device
Configure a Microsoft Azure Sentinel cloud SIEM to pull IOCs from Digital Risk Protection (Threat Command). The Azure Sentinel connector supports TAXII v2.0.
You must first add the device to Digital Risk Protection (Threat Command) and then configure the device to pull IOCs from Digital Risk Protection (Threat Command).
After the Azure Sentinel device is integrated, you can View dashboards.
When IOCs are pulled to the device, all IOCs are pulled, every time. IOCs are pulled, together with the following Digital Risk Protection (Threat Command) enrichment data:
- Source name (reporting feed)
- System and user tags
- First seen and last seen
- Severity
- Related threat actors, campaigns, or malware
- Related alert
IOC groups for this device can consist of domains, URLs, IP addresses, file hashes, and email addresses.
Add an Azure Sentinel cloud device
Add a cloud device to Digital Risk Protection (Threat Command).
Prerequisites
- You have the credentials to access the device.
- You have administrative credentials to access Digital Risk Protection (Threat Command) with a subscription to the Automation and TIP modules.
To add a cloud device to Digital Risk Protection (Threat Command):
- Log in to Digital Risk Protection (Threat Command) at https://dashboard.ti.insight.rapid7.com
- From the main menu, select Automation -> Integrations.
- From the Integrations page, click Cloud.
- Click Add new device.
- In the Add New Cloud Device dialog, type a user-defined name for the device. The name can contain a maximum of 50 letters, spaces, numbers, and underscores.
- Select the Device type.
The default device IOCs limit is displayed. - (Optional) You can change the IOCs limit.
- Click Add.
- To verify that the new device is added, refresh the Automation > Integrations page.
The new device is added to the cloud integrations device list. Next to the device name, there is a red dot, indicating that communication has not yet been established. The dot will change to green when the device is synchronized. If the device cannot synchronize for more than 48 hours, an email warning is sent to the account administrator.
Configure a Microsoft Azure Sentinel cloud device to pull IOCs
After a device has been added, you must enable the pulling of IOCs from Digital Risk Protection (Threat Command).
Prerequisites:
-
You have the Rapid7 Digital Risk Protection (Threat Command) account ID and appliance API key. For more information, see API key, account ID, and appliance key.
-
You have the device login credentials.
-
The device has been added.
-
You have administrative credentials to access Digital Risk Protection (Threat Command) with a subscription to the Automation and TIP modules.
-
An IOC group for this device exists in Digital Risk Protection (Threat Command).
Creating IOC groups is described in Create an IOC group
To configure an Azure Sentinel cloud device:
- From the Microsoft Azure portal, open Azure Sentinel.
- Select a workspace, then search for Data connectors.
- In the Connector list, search for TAXII, then click Open connector page.
- In the Configuration section, type the following:
| Field | Description |
|---|---|
| Friendly name | Type a user-defined name. Imported IOCs will be marked with this name. |
| API root URL | Copy/paste from the Digital Risk Protection (Threat Command) Device Details dialog. - From Digital Risk Protection (Threat Command), select Automation > Integrations. - From the Cloud device list, select the Azure Sentinel device. - On the line of the desired IOC group, click the link symbol. 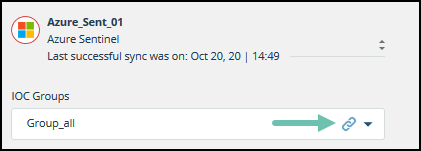 - From the IOC Group URL dialog, use the Copy button to copy the API Root URL. - Paste that URL in this field. |
| Collection ID | Copy/paste from the Digital Risk Protection (Threat Command) Device Details dialog. Follow the same instructions for API Root URL, but copy the Collection ID. The Collection ID is different for each IOC group. |
| Username | Paste the Digital Risk Protection (Threat Command) account ID. For more information, see API key, account ID, and appliance key. |
| Password | Paste the Digital Risk Protection (Threat Command) API appliance key. For more information, see API key, account ID, and appliance key. |
- Click Add.
The connector is added to the Connectors list.
Viewing IOCs in Microsoft Azure Sentinel
You can view IOCs that are pulled in from Digital Risk Protection (Threat Command) in the Azure Sentinel Threat intelligence page. This page shows summary data on imported IOCs as well as details per IOC.
To view IOCs:
- From the Microsoft Azure portal, open Azure Sentinel.
- Select a workspace, then search for Threat intelligence.
The Indicators area displays a summary of all IOCs. To the right is more details on the selected IOC: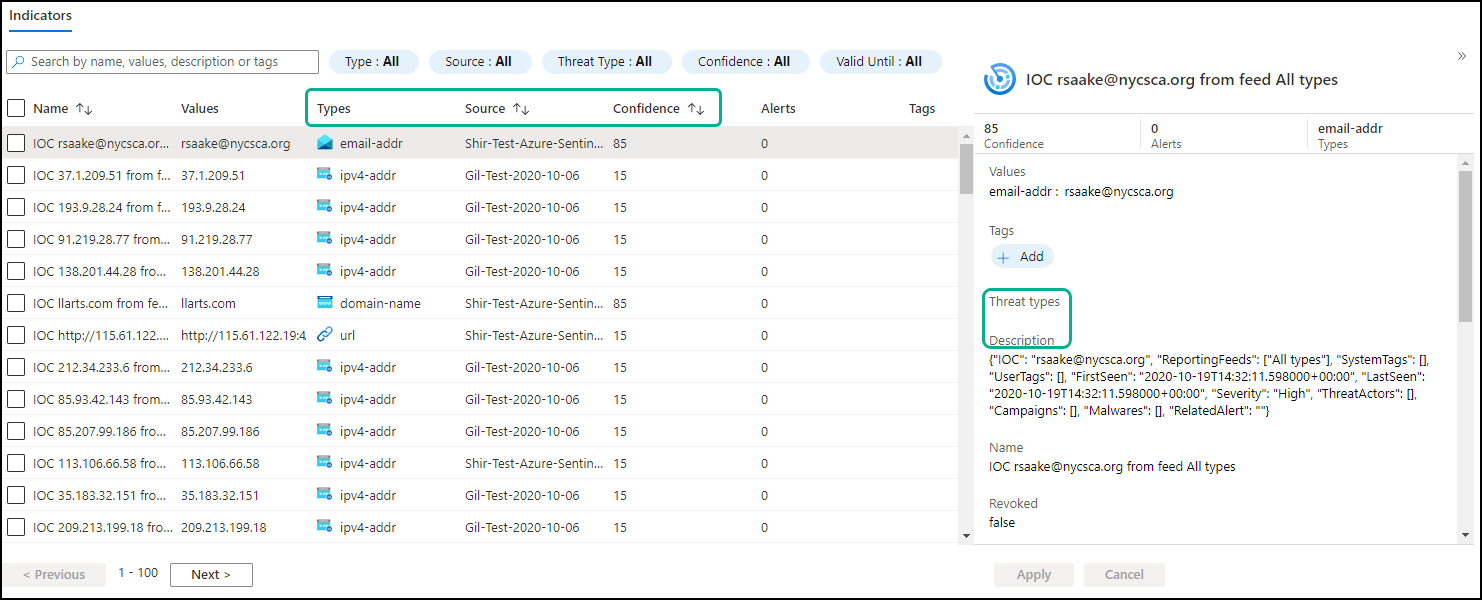
In the summary table, you can see the following data:
- IOC type - IP address, URL, etc.
- Source - The name that was assigned to the Azure connector.
- Confidence - This is mapped from the Digital Risk Protection (Threat Command) severity. Low = 15, Medium = 50, and High = 85
- Alerts and tags are not relevant.
In the detail per IOC, you can see additional data:
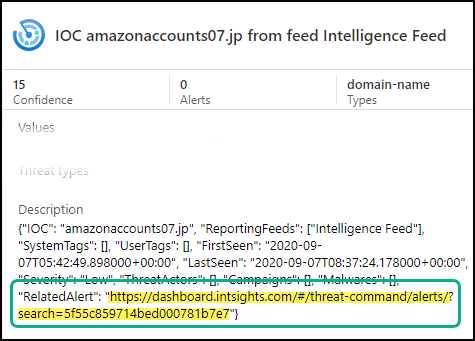
- Description - The IOC enrichment data. If a Digital Risk Protection (Threat Command) alert was created, you can copy the URL to Digital Risk Protection (Threat Command) to see the alert:
Searching for IOCs in Microsoft Azure Sentinel
You can search for IOCs that match criteria in the name, value, description, or tags. For example:
To search for IOCs:
- In the Indicators search bar, type a term to search for.
IOCs that match the term are displayed.
The Description field contains the IOC enrichment data, and you can search for matches in that field, also. This table summarizes some of the more common uses:
| To find this | Enter this in the search bar |
|---|---|
| IOCs of a specific severity | Type the severity (high, medium, or low) |
| IOCs from a specific Digital Risk Protection (Threat Command) feed | Type the name of the feed (e.g., intelligence feed) |
| IOCs from a specific malware or threat actor | Type the name of the malware or threat actor |
View Azure Sentinel Dashboards
You can add the following predefined dashboards to your Azure Sentinel instance:
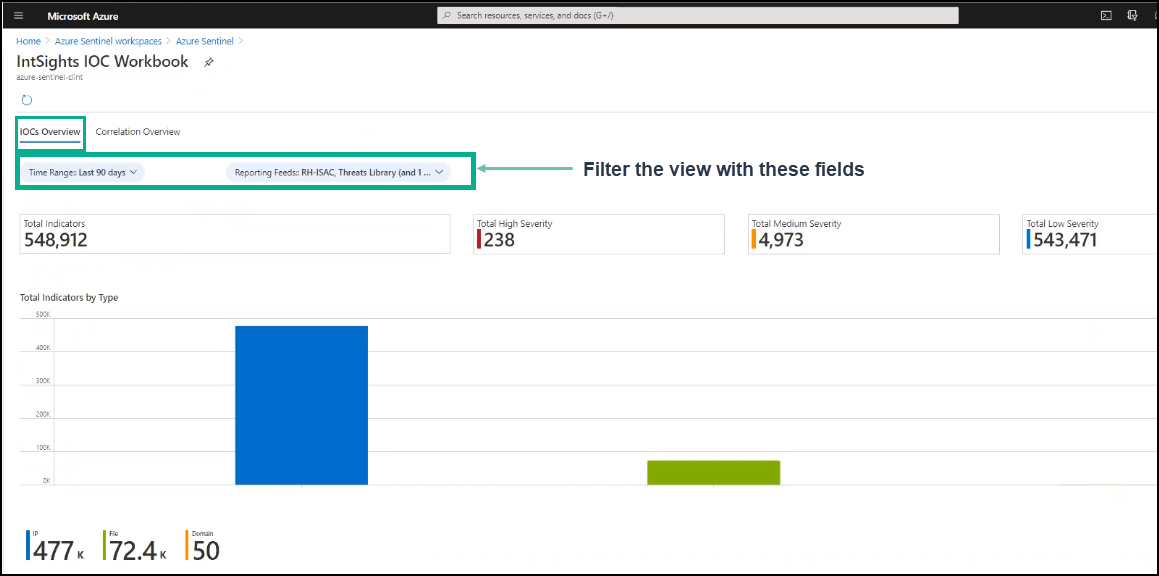
- IOCs Overview - Displays all the IOCs sent from Digital Risk Protection (Threat Command), broken down by severity and IOC type.
- Correlation Overview - Displays all the indicator alerts created in Azure Sentinel by customer-configured rules.
Indicators from those alerts (only) are presented by type and severity and grouped by top tags, top malware, and top threat actors.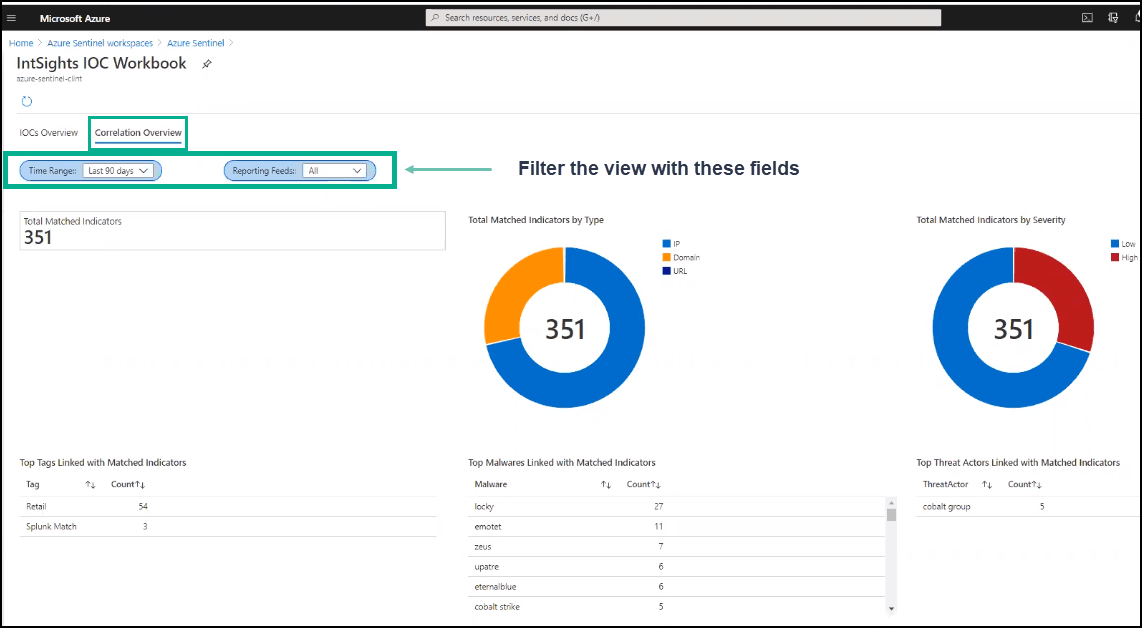
The Correlation Overview page shows the following information:
- Total Matched Indicators - The total number of indicators that match those in the Azure index.
- Matched Indicators by Type - A chart distribution of matched indicators by type.
- Matched Indicators by Severity - A chart distribution of matched indicators by severity.
- Top Tags Linked with Matched Indicators - The Digital Risk Protection (Threat Command) tags (for example, phishing) that are attached to the most matched indicators.
- Top Malwares Linked with Matched Indicators - The name of the malwares (for example, locky) that are associated with the most matched indicators.
- Top Threat Actors Linked with Matched Indicators - The name of the threat actors (for example, Cobalt Group) that are associated with the most matched indicators.
You can filter both dashboards by the time range and the IOC reporting feeds.
To view these dashboards, you must first add predefined IntSights workbooks to your Azure Sentinel instance.
To add dashboards:
- From Azure Sentinel, select Threat management > Workbooks.
- Click the Templates tab (marked as section 1), then search for IntSights.
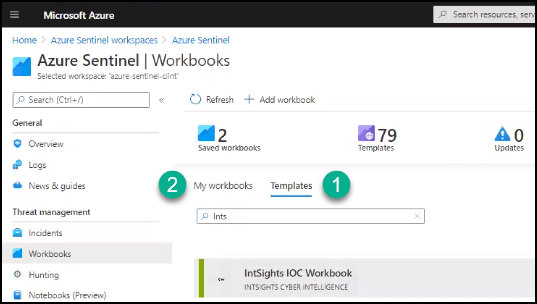
- Select the IOC Workbook, then click View Template.
The IOCs Overview dashboard tab is displayed. Click Correlation Overview to see the other tab. - After viewing the dashboards, click Save.
Once the dashboards are saved the first time, they can be viewed from the My workbooks menu (marked as section 2).