Integrate a LogRhytm SIEM Cloud Device
Configure a LogRhythm SIEM cloud device to pull IOCs from Digital Risk Protection (Threat Command). You must first add the device to Digital Risk Protection (Threat Command) and then configure the device itself to pull IOCs from Digital Risk Protection (Threat Command).
For LogRhythm devices, ensure that port 9000 is open.
Add a LogRhythm SIEM cloud device
Add a cloud device to Digital Risk Protection (Threat Command).
Prerequisites
- You have the credentials to access the device.
- You have administrative credentials to access Digital Risk Protection (Threat Command) with a subscription to the Automation and TIP modules.
To add a cloud device to Digital Risk Protection (Threat Command):
- Log in to Digital Risk Protection (Threat Command) at https://dashboard.ti.insight.rapid7.com
- From the main menu, select Automation -> Integrations.
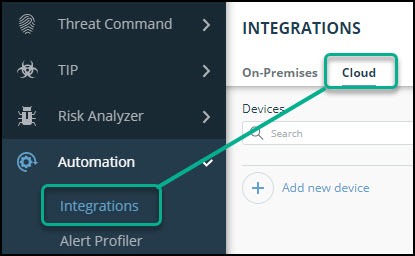
- From the Integrations page, click Cloud.
- Click Add new device.
- In the Add New Cloud Device dialog, type a user-defined name for the device. The name can contain a maximum of 50 letters, spaces, numbers, and underscores.
- Select the Device type.
The default device IOCs limit is displayed. - (Optional) You can change the IOCs limit.
- Click Add.
- To verify that the new device is added, refresh the Automation > Integrations page.
The new device is added to the cloud integrations device list. Next to the device name, there is a red dot, indicating that communication has not yet been established. The dot will change to green when the device is synchronized. If the device cannot synchronize for more than 48 hours, an email warning is sent to the account administrator.
Configure a LogRhythm SIEM device to pull IOCs
After a device has been added, you must enable it to pull IOCs from Digital Risk Protection (Threat Command). The configuration is done by editing the hosts file and then configuring the device in the LogRhythm management console.
Prerequisites
-
You have the Digital Risk Protection (Threat Command) account ID and appliance key, as described in API key, account ID, and appliance key.
-
You have the device login credentials.
-
The device has been added.
-
You have administrative credentials to access Digital Risk Protection (Threat Command) with a subscription to the Automation and TIP modules.
-
An IOC group for this device exists in Digital Risk Protection (Threat Command).
Creating IOC groups is described in Create an IOC group
IOC groups for LogRhythm SIEM devices can consist of the following types of IOCs: domains, URLs, and IP addresses.
To configure the device to pull IOCs:
- Log into the LogRhythm management console.
- Click Add STIX/TAXII Provider.
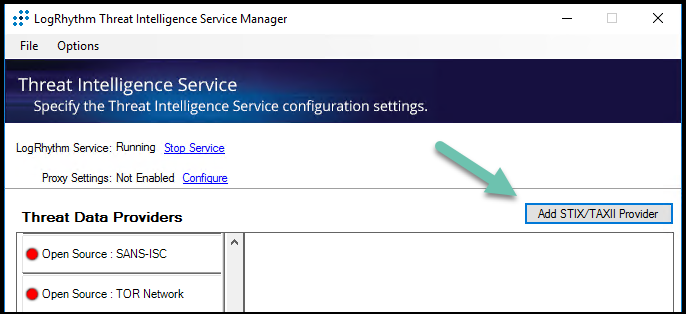 The LogRhythm Custom Provider dialog is displayed:
The LogRhythm Custom Provider dialog is displayed:
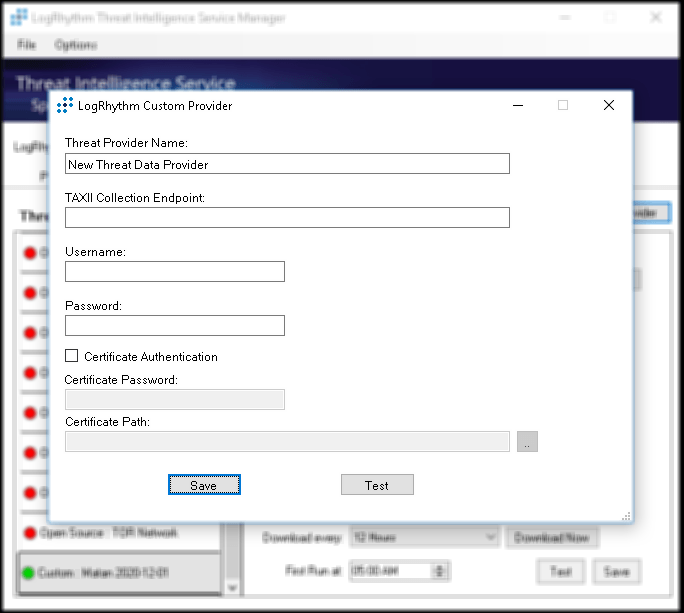
- Fill in the details:
| Field | Description |
|---|---|
| Threat Provider Name | Type a user-defined name. Collected IOCs can be found under this folder name. |
| TAXII Collection Endpoint | Copy/paste from the Digital Risk Protection (Threat Command) Device Details dialog. - From Digital Risk Protection (Threat Command), select Automation > Integrations. - From the Cloud device list, select the LogRhytm SIEM device. - Click Device Details. 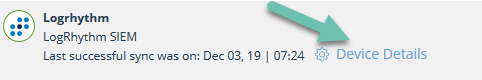 {inline}- From the Device Details dialog, use the Copy button to copy the TAXII Collection Endpoint URL. |
| Username | Enter the Digital Risk Protection (Threat Command) account ID. |
| Password | Enter the Digital Risk Protection (Threat Command) appliance key. |
| Certificate fields | Optional. |
- Test the connection by clicking Test. For more information, see Troubleshooting
- Click Save.
- Click Enabled, then click Save.
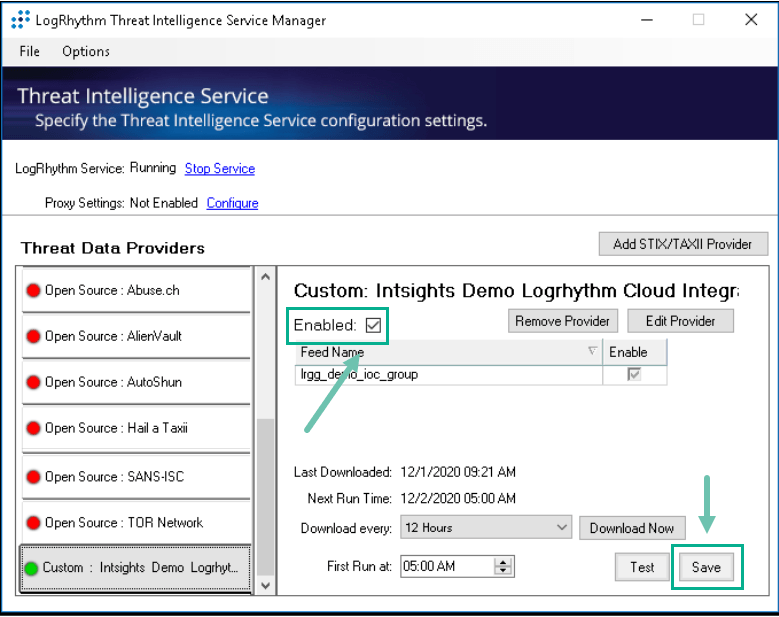
When IOCs are present in the Digital Risk Protection (Threat Command) IOC group, the LogRhythm SIEM device will begin to pull them.
View pulled IOCs in LogRhythm SIEM
You can download a TXT file of the pulled IOCs in the LogRhythm SIEM management console.
To view pulled IOCs:
- In the LogRhythm Threat Intelligence management console, select the group to download.
- Click Download Now.
Downloaded files are located in the <installation directory>\staging\<Threat Provider Name> folder.
For example, C:\Program Files\LogRhythm Threat Intelligence Service\staging\Intsights5
Troubleshooting errors during testing
The following table describes possible errors and their solution:
| Error displayed is similar to the following | Description and solution |
|---|---|
| Feeds not found for the provider | Configuration was successful, but there are no IOC groups in Digital Risk Protection (Threat Command). |
| Exception while testing … : The underlying connection was closed | Configuration was successful. This is a random error that can be ignored. |
| Exception while testing … : Unable to connect to the remote server | The IP address or port in the TAXII Collection Endpoint field is incorrect or this is a communication problem between LogRhythm and the Digital Risk Protection (Threat Command) virtual appliance. |
| Exception while testing … : The remote server returned an error: (401) Unauthorized | The Digital Risk Protection (Threat Command) account ID or appliance key is not correct. |