Microsoft Active Directory
Active Directory integration allows Rapid7 to provide indication and mitigation for leaked user account credentials. In case the system locates a user account that was leaked, it validates it with Active Directory if the account is valid and sets the severity level in accordance.
Only one Active Directory validation can be active, either Azure AD in the cloud or Microsoft AD.
When a leaked account is found, the account name is searched across one or more domains, so even if the external domain (the one that was configured as an asset and that triggered the alert) is different than the internal domain, the system will still find the account.
- Example:
The system finds two leaked credentials of company users: bob@company.external.com john@company.external.com
- The system checks if users ‘bob’ and ‘john’ appear in the following domains
- Internal.company.com
- company.com
- The system finds the account of bob@company.com.
- A high severity alert is created stating that ‘bob@compay.com’ is an active account.
On top of active account validation, the system can validate if the matching clear text password is valid or not.
Prerequisites
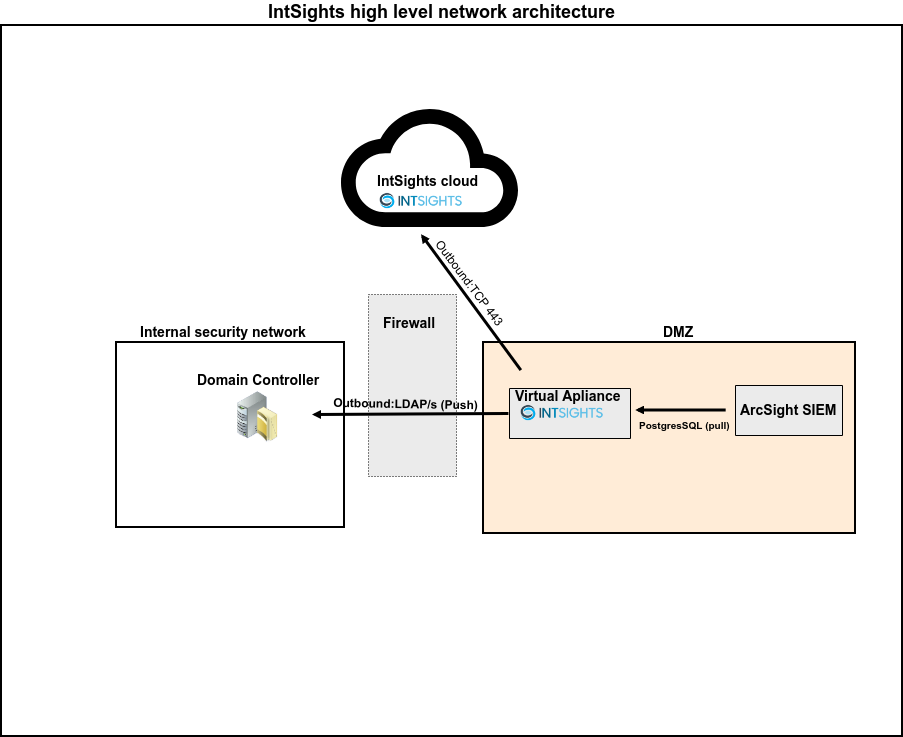
- Network connectivity over LDAP or LDAPS from the virtual appliance to the required domain controller/s.
- Query Domain Controller (DC) over LDAP (389/TCP) or LDAPS (636/TCP).
- List of one or more domains that hold the user directory.
The list of domains will be used as a baseline for searching active users.
- List of corresponding Domain Controller/s IP address per domain.
- A domain user and password
- For account and password validation
Use a dedicated service account, with the minimal permissions necessary. There is no need for administrative privilege or specific group membership.
-
“Write account restrictions” to be allowed for this service account in the AD permissions
-
For remediation
Use a dedicated service account, with permissions to perform the required remediation actions.
- “Write account restrictions” and “Reset password” should be allowed for this service account in the AD permissions
Adding Domains and Domain controllers
-
Navigate to the Active Directory tab.
-
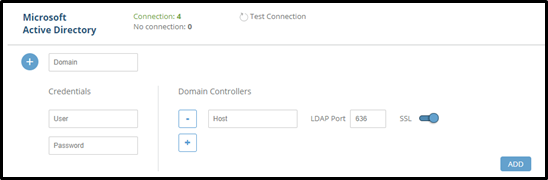
Click Add new domain.
-
Input required information:
- Domain name
- User account and password
- One (or more) domain name or hostname.
- Set the port and mode for LDAP
- Click Add.
-
Repeat the process for adding more domains.
Active Directory settings in the cloud platform
- Navigate to Automation > Integrations
- Select the Microsoft Active Directory
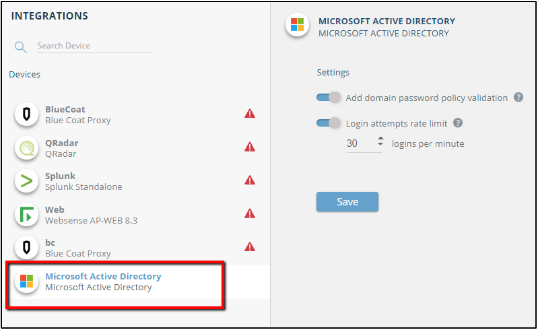
If needed, enable password policy validation and login attempt rate limit
Active Directory in the policy
- Create a new rule of type ‘Data leakage’
- Define leaked credentials related conditions:
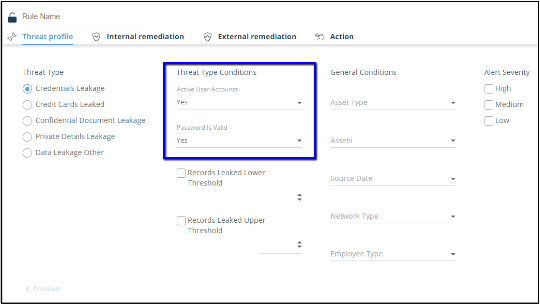
- In the internal remediation tab enable the validation and / or remediation actions
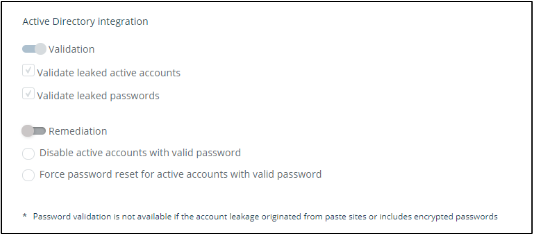
Remediation option can be enabled only if ‘Leaked user account and password validation’ is enabled