Pull IOCs from the Rapid7 TAXII server
You can pull enriched IOCs into third-party security devices using the IntSights TAXII server (STIX/TAXII v1.1 and 2.0 are supported). The TAXII server is defined in Threat Command as an external cloud device.
The following enrichment data is included: IOC Type, First seen, Last seen, Reported feeds, Severity, Feed confidence level, User tags, System tags, Threat Actor relation, Malware relation, and Campaign relation.
IOC groups can consist of domains, URLs, IP addresses, file hashes, and email addresses.
Before you begin, ensure that you have administrative credentials to access Threat Command with a subscription to the TIP and Automation modules.
Define the IntSights TAXII server integration
You can define a TAXII server to pull IOCs.
Before you begin, ensure that you have the Threat Command account ID and appliance key.
To define a TAXII server:
-
Log in to Threat Command at https://dashboard.ti.insight.rapid7.com .
-
From the main menu, select **Automation > Integrations.
-
From the Integrations window, click Cloud.
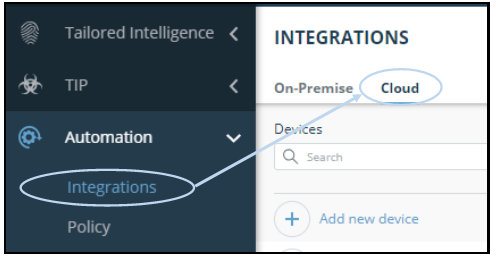
-
Click Add new device.
-
In the Add New Cloud Device dialog box, define the IntSights TAXII server:
- Type a user-defined name for the device.
The name can contain a maximum of 50 letters, spaces, numbers, and underscores. - For the device type, select IntSights TAXII Server.
- Select the STIX version to support v1.1 or v2.0.
- You can change the IOCs limit for the TAXII server (default is 100,000).
- Type a user-defined name for the device.
-
Click Add.
The new device is added to the cloud integrations device list. A red dot next to the device name indicates that communication has not yet been established. The dot changes to green once the device is synchronized. -
Display the device details required to connect to your security device:
- From the Automation > Integrations > Cloud page, select the TAXII integration.
- At the top of the screen, click Device Details.
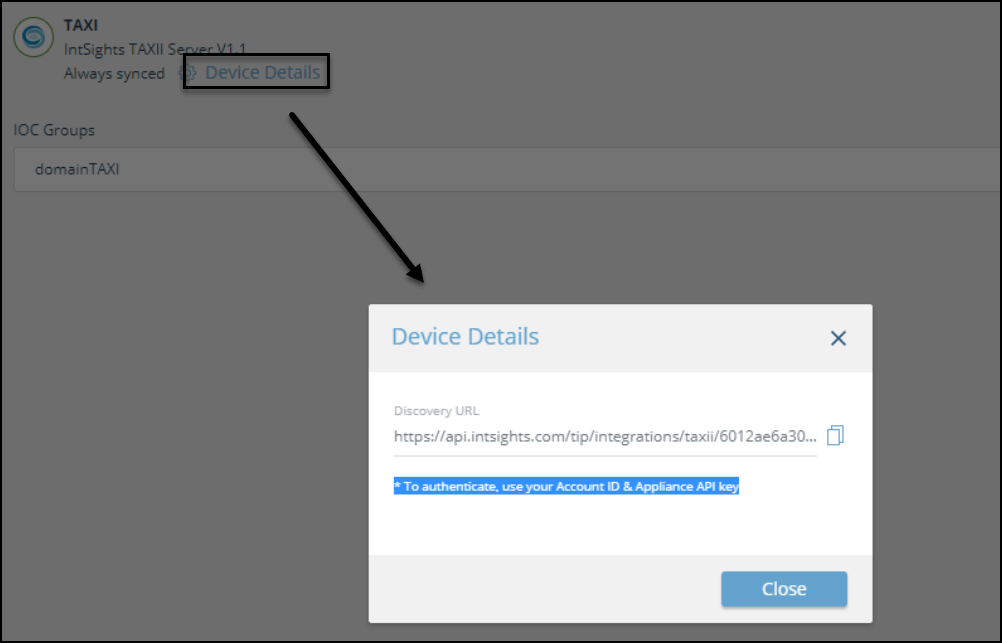
- From the Device Details dialog, you will need the Discovery URL.
In addition, you need the Threat Command account ID and appliance key.
Copy this information into the management console of the security device.