Risk Assessment
The Risk Assessment module can help mitigate your company’s cyber risk and also align third-parties with your security controls, regulations, and risk tolerance.
The Risk Assessment module provides risk reports from a vendor that specializes in assessing companies by non-intrusively evaluating the third parties’ attack surface. Hundreds of tests are performed, such as collecting information on exposed assets and evaluating security practices.
The assessment is usually completed within 12-72 hours. at which point, an email is sent to notify about the completion.
The following diagram illustrates the Risk Assessment page:
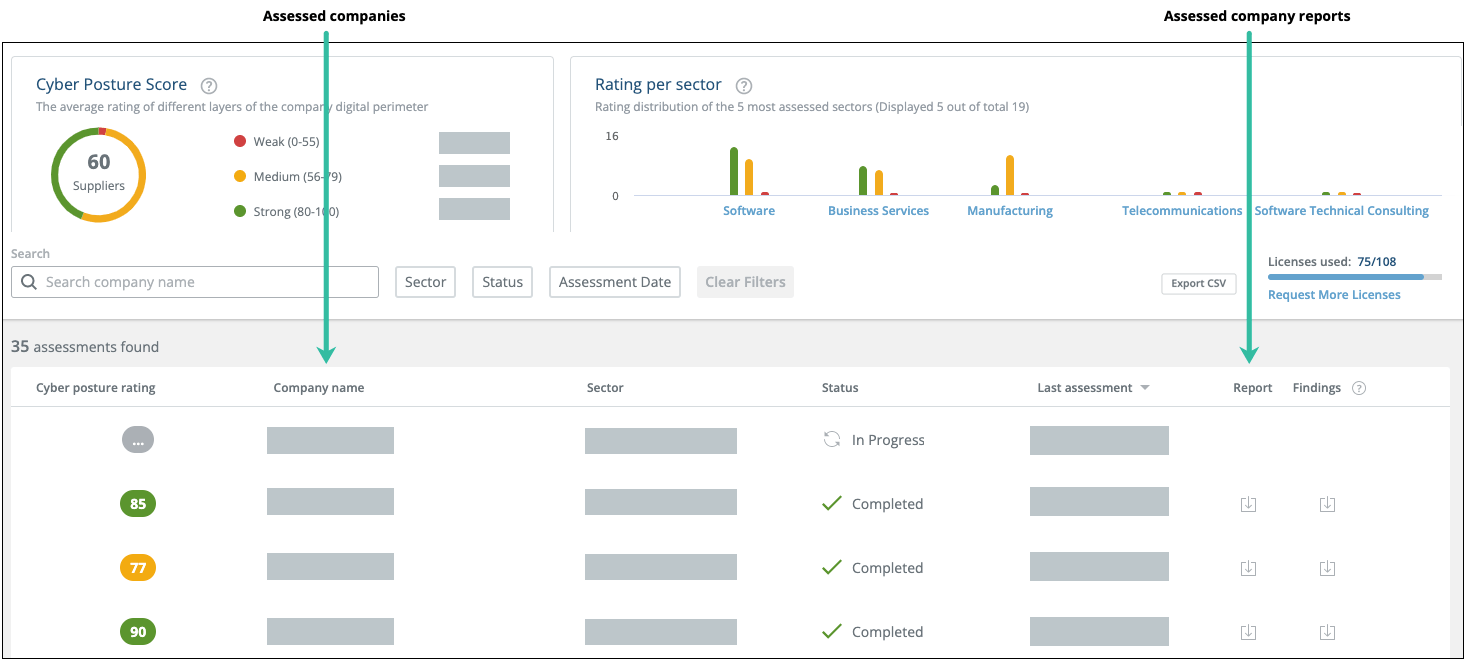
Each assessed company is given a Cyber Posture Rating that represents the risk level attributed to its external digital perimeter. In addition, the assessment includes a Report and Findings. For more information, see View assessed companies.
Assess a company
Before you begin, ensure that:
- You have a subscription to the Digital Risk Protection (Threat Command) Threat Third Party module with rights to create an assessment.
- You have at least one assessment license that can be used. To purchase additional licenses, click Get more under the license counter.
To assess a company:
- From the Digital Risk Protection (Threat Command) main menu, select Threat Third Party.
The Risk Assessment page is displayed. - Click +.
- In the New Assessment Report Request dialog box, type the company name or domain to assess.
The specified name or domain is searched for. - If the company is found (its name is displayed), do the following:
- Select the company.
In this example. “ACME” is used to represent an imaginary company.
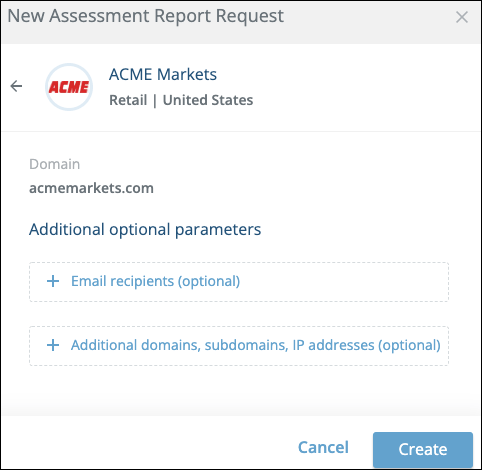
- (Optional) You can add additional email recipients to receive the report when it is complete.
- (Optional) You can add additional domains subdomains, and IP addresses of the same company.
In all cases, TTP discovers assets relevant to the assessed company. These assets are used during the assessment process. - Click Create.
- Skip the next step.
- Select the company.
- If the company is not found, do the following:
- Click Create new company.
- Enter details for the new company.
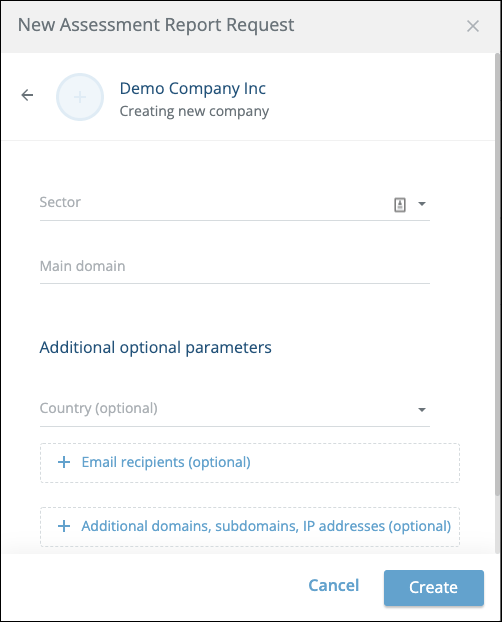
- (Optional) You can add additional email recipients to receive the report when it is complete.
- (Optional) You can add additional domains of the same company.
- Click Create.
Assessments for companies not found can begin only after a Rapid7 representative approves the company. This process can take up to two business days.
Before begining the external assessment tests, we identify every publicly accessible asset linked to the evaluated company. Asset discovery is done automatically by our vendor, requiring only a single asset to get started. Usually, the primary domain of a company is used as a starting point for discovering all of the company’s attack surface, including domains, subdomains, and IP addresses.
To prevent false positives, each asset goes is vetted to determine if it should be attached to the company. That said, it is expected to have a certain rate of false positives.
To assess a company that was already assessed:
- Hover your pointer over the company assessment line in the main table, then click +.
View assessed companies
You can view assessed companies from the Risk Assessment page:

Each line represents a company for which an assessment has been requested. The status changes from In Progress to Completed when the reports are ready. The following sections describe the company assessments.
Cyber posture rating
This rating represents a security assessment of the company’s public-facing digital footprint to evaluate the risk level associated with your third parties. The analysis non-intrusively evaluates the third-party attack surface through the analysis of externally available data. To ensure a comprehensive view of your third parties’ digital perimeter, hundreds of tests are performed, such as collecting information on exposed assets or a lack of security best practices.
Tests are performed to assess these layers:
- Network & IT - Web, e-mail, and DNS servers, TLS protocols, asset reputation, cloud solutions, and other exposed services.
- Application - Web applications, CMS, domain attacks, etc.
- Human - Employee attack surface, social posture, presence of a dedicated security team, etc.
The company Cyber Posture Rating represents a calculated average of ratings for each layer of the assessed digital perimeter. The 0-100 rating represents a security assessment of the company’s public-facing digital footprint to evaluate the risk level associated with your third parties.
Assessment report
From the Report column, you can download a PDF report with the following sections:
- The company overview.
- The Cyber Posture rating.
- The tested categories.
- A comparison of the company’s rating with the industry.
- Dark web mentions trend.
- The results of the tested assets agains the categories.
Assessment findings
From the Findings column, you can download a CSV file that includes a detailed explanation of found issues stated in the report, including the found assess and the issue associated with that asset.
If you created assessment reports with the legacy Risk Assessment, the reports are displayed here, too. The “findings” from the legacy reports are included as part of the PDF report, not separately as they are in this format.
Export details of assessed companies
You can export the details in the assessment table so you can share it easier with executives and other interested parties.
To export the assessed company details:
- From the Risk Assessment page, click Export CSV.
The filters applied to the Risk Assessment page are applied to the export operation. - In the Column selection and order section, select which columns to export and in which order.
- Click Download CSV.
The report is entitled Rapid7 Risk Assessments.csv