The Digital Risk Protection (Threat Command) Virtual Appliance
The following diagrams illustrate how the virtual appliance fits in your company environment.
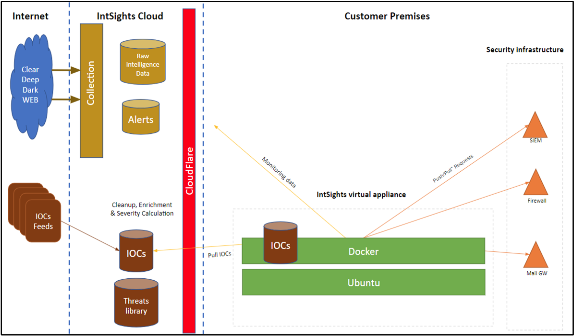
High-level connectivity diagram
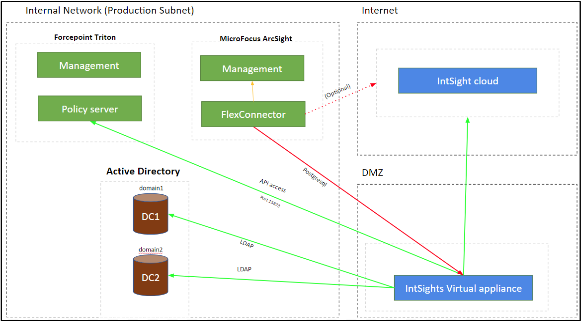
High-level Device connectivity
Virtual appliance hardening is detailed in Virtual Appliance Hardening.
General prerequisites for deploying the appliance
For on-premises security devices, you must set up the Digital Risk Protection (Threat Command) virtual appliance (“appliance”) on either a VMware or Hyper-V host. For cloud devices, skip to Device-side Configuration for Cloud Devices.
Prerequisites
- Subscription to the Digital Risk Protection (Threat Command) TIP and Automation modules
If you don’t have such a subscription, contact Rapid7 sales. - Network connectivity from the appliance to the Digital Risk Protection (Threat Command) cloud (External)
There is no connectivity initiated from the cloud to the internal network.
Connectivity includes unrestricted access to *.intsights.com- To enable access based on the IP addresses, enable the IPv4 addresses listed here: https://www.cloudflare.com/ips/
Digital Risk Protection (Threat Command) uses Cloudflare for IP address allocation.)
- To enable access based on the IP addresses, enable the IPv4 addresses listed here: https://www.cloudflare.com/ips/
- For appliance versions earlier than v3.7.0, unrestricted access is also required to: *.gcr.io, *.googleapis.com, *.docker.io, *.cloudfront.net
- Network connectivity between the appliance to and from the security devices for IOC sharing.
| Service/Port | Direction | Purpose |
|---|---|---|
| DNS (53/UDP) | Outgoing (from the machine) | Allow DNS queries from the machine. |
| HTTPS (443/TCP) | Incoming (to the machine) | From the internal network to the virtual appliance “Management” interface, for administration. |
| HTTPS (443/TCP) | Outgoing (from the machine) | From the virtual appliance to Digital Risk Protection (Threat Command) cloud (Internet). Please make sure that all access is allowed to: *.intsights.com That is, all subdomains under the above domain must be allowlisted too. Note: during the initial setup phase of the DEB file, the machine needs to have unrestricted access to the internet. After a successful installation, the access can be limited to the above. |
| SSH (22/TCP or other) | Incoming (to the machine) | From the internal network to the virtual appliance for administration. |
| 8080/TCP | Incoming (to the machine) | From the various security devices to the virtual appliance for pulling IOCs. |
| Per device connectivity, (as described inIntegration support list) | Outgoing (from the machine) | From the virtual appliance to the various security devices, for pushing IOCs. |