Threat Library Related Information
Selecting a cyberterm opens an overview where you can view further details.
From this view, you can show the cyberterm in the Investigation or IntelliFind pages, export a cyberterm PDF report, and view the cyberterm description, related IOCs, vulnerabilities, and MITRE techniques.
View cyberterm description
From this tab, you can see the following expanded information:
| Field | Description |
|---|---|
| Full description | The full description of the term and additional information. |
| Investigate | Click the icon to show the cyberterm in the Investigation page. |
| Upload document | Click to attach a document to this cyberterm for your internal use. |
| Additional details | TTPs, aliases, and related threat actors, etc. |
| IntelliFind mentions | Graph of IntelliFind mentions from the past 12 months. This is the same graph that is shown on the front page. Click the graph to see the cyberterm in the IntelliFind page. |
Attach documents to cyberterms
You can attach documents to cyberterms. These documents are available in the company internal Threat Library, and can be an excellent place to store and manage your internal company knowledge, thus turning the Threat Library into your internal knowledgebase.
When a cyberterm has an attachment, there is a paperclip icon that indicates this.
You can search for attachments by filename, filter for terms with attachments, and view and delete attachments.
| Action | Procedure |
|---|---|
| Search for a cyberterm with an attachment | Enter the filename (or partial) in the search bar. |
| Filter to show only cyberterms with attachments | Use the With Attachments filter. |
| View an uploaded attachment | In the cyberterm description, click the attachment icon. |
| Delete an attachment | In the cyberterm description, click the attachment icon, then click delete. |
Export a cyberterm PDF report
You can share all of a cyberterm’s data including the high-level summary, MITRE matrix, and CVE data outside of the Rapid7 platform or use it as an internal resource for attacks targeting their sector and operating countries.
To export a cyberterm PDF:
- From an expanded cyberterm, click Export to PDF.
View related IOCs
Related IOCs are domains, URLs, IP addresses, file hashes, and email addresses that are associated with the cyberterm. These IOCs are shown when a cyberterm is investigated, too.
When you hover over a related IOC value, you can see its properties in the popover that is displayed.This helps gain 360 degree visibility of all relevant context, enabling timely triage and informed decisions.
Related IOCs can be added as followed:
- By Rapid7 intelligence analysts - These are shown in the Related IOCs tab automatically.
- By the user - These are added by the user, either uploaded from a file or added manually, as described in Add related IOCs to a cyberterm.
You can see these on the Related IOCs tab.
The Reporting Feeds column shows from which feeds the IOC were found. A + in the Reporting feeds column indicates that the IOC was reported by more than one feed.
From this page, you can also perform the following:
| Action | Procedure |
|---|---|
| View the related IOCs in the IOCs page | Click View in IOCs page |
| Add all IOCs to the Remediation Blocklist | Click Add All IOC Types to Blocklist |
| Add an entire group of IOCs to the Remediation Blocklist | Click Add … to Blocklist |
| Add selected IOCs to the Remediation Blocklist | See Perform operations on multiple IOCs. |
| View the source URL (relevant for IOCs added by internal analysts, in the Threat Library feed) | Click the Threat Library Source icon |
| Relate (or unrelate) an IOC to a cyberterm | To relate an IOC, click Add Related IOCS. Click again to unrelate. |
| Add (or remove) an IOC to the Remediation Blocklist | Click the Add IOC to the Remediation Blocklist feed icon to relate. Click again to unrelate |
| See an IOC in the Investigation page Related IOCs are also shown in the Investigation page. | Click the Investigate IOC icon. |
| Export IOCs | Click Export CSV |
You can share related IOCs with devices by selecting the Threat Library feed when creating IOC groups.
Relate (or unrelate) IOCs to a cyberterm
In addition to the system-defined related IOCs, you can relate IOCs to cyberterms on your own, using IOCs that exist in the system or custom IOCs that you add. This enhances your ability to research and investigate and further enhances the value of the Threat Library as your one-stop repository of all cyberterm-related information.
Email address IOCs cannot currently be related to cyberterms.
You can relate up to 1,000 IOCs, either through a file upload (according to a system template) or by adding them manually.
You can also unrelate an IOC and a cyberterm. When you unrelate an IOC, the outcome will be different, depending on where it came from:
- IOCs that you added and then you related to a cyberterm - The IOC will no longer relate to the cyberterm, and will be removed entirely from the IOC list.
- IOCs that were added by IOC feeds and then you related to a cyberterm - The IOC will no longer be related to the cyberterm, but it will still exist as an IOC (not related to this cyberterm).
- IOCs that were added by IOC feeds and then both you and a feed related them to a cyberterm - The IOC will still be related to a cyberterm, only from the feed, not from you.
- IOCs that were added by and related by IOC feeds - You cannot unrelate these IOCs as you did not relate them.
The following table summarizes what happens to an IOC after you unrelate it:
| IOC added by | IOC related by | Relation | IOC list |
|---|---|---|---|
| You | You | Removed | Removed |
| Feed | You | Removed | Remains |
| Feed | You and feed | Remains, related only to the feed | Remains |
| Feed | Feed | Remains | Remains |
To add related IOCs to a cyberterm:
- From the Related IOCs tab, click Add Related IOCs.
- Add IOCs, either from a file or manually:
- To add from a file, download and enter values in the template, save that file, then drag the file to the upload area.
- To add manually, enter the IOCs into the manual area.
- Click Add IOCs.
Added IOCs are shown in the Related IOCs window in the appropriate section. If the added IOCs were not valid, you can view the analysis file to see the error.
To unrelate IOCs from a cyberterm: To unrelate more than one IOC at a time, see Perform operations on multiple IOCs.
- From the Related IOCs table, click the
 to the right of the IOC.
to the right of the IOC. - If a confirmation message is displayed, review and confirm.
Perform operations on multiple IOCs
You can perform some operations on multiple IOCs at one time, thus enhancing efficiency. First, select the desired IOCs, then use the multiple IOC toolbar to perform the operations.
These actions can be performed to multiple IOCs at one time: Relate (or unrelate) to a cyberterm and add (or remove) to Remediation blocklist.
To perform operations on multiple IOCs:
- From the Related IOCs table, select multiple IOCs:
| To select these | Select like this |
|---|---|
| All IOCs of a certain type |  |
| Individual IOCs | 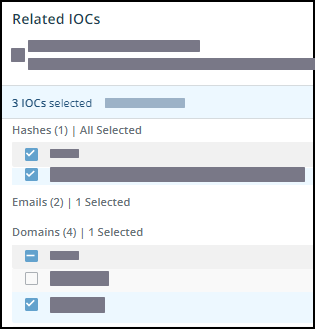 |
When you select IOCs, the multiple command menu is displayed. 2. Click the desired command and perform the activity to all selected IOCs.
View cyberterm vulnerabilities
A cyberterm may have CVEs related to it. You can see these on the Vulnerabilities tab. For each vulnerability, you can see the accompanying Rapid7 score and an icon that indicates if there is an available exploit or if the CVE is trending. You can also export the list of CVEs to a PDF.
View cyberterm MITRE techniques
You can view the MITRE classification of a cyberterm. You can see these on the MITRE ATT&CK tab.
When you click a technique, you will be redirected to the MITRE technique definition.