Juniper Networks ScreenOS
Juniper Networks ScreenOS, formerly known as Juniper NetScreen Firewall, is real-time firewall hardware among a series of security devices that you can access through your local internet, or through the Juniper web console.
You can configure Juniper ScreenOS’ Integrated Services Gateway (ISG) to send syslog to your SIEM (InsightIDR) Collector in order to collect firewall events.
To collect ScreenOS ISG events from Juniper:
Configure Syslog
To configure syslog forwarding from your ScreenOS device:
- Sign in to your Netscreen Management console.
- In the left menu, expand the Report Settings tree and select the Syslog page.
- If you are using an older version of ScreenOS, navigate by Configuration > Report Settings > Syslog.
- Check the Enable Syslog box to enable syslog.
- Click the + plus button to add a new host.
- In the “Config” window, enter the IP address of your SIEM (InsightIDR) Collector.
- In the “Port” field, enter the unique port on your Collector that will accept these firewall logs.
- In the “Security Facility” dropdown, select the Local0 option. This option logs every single security event to syslog.
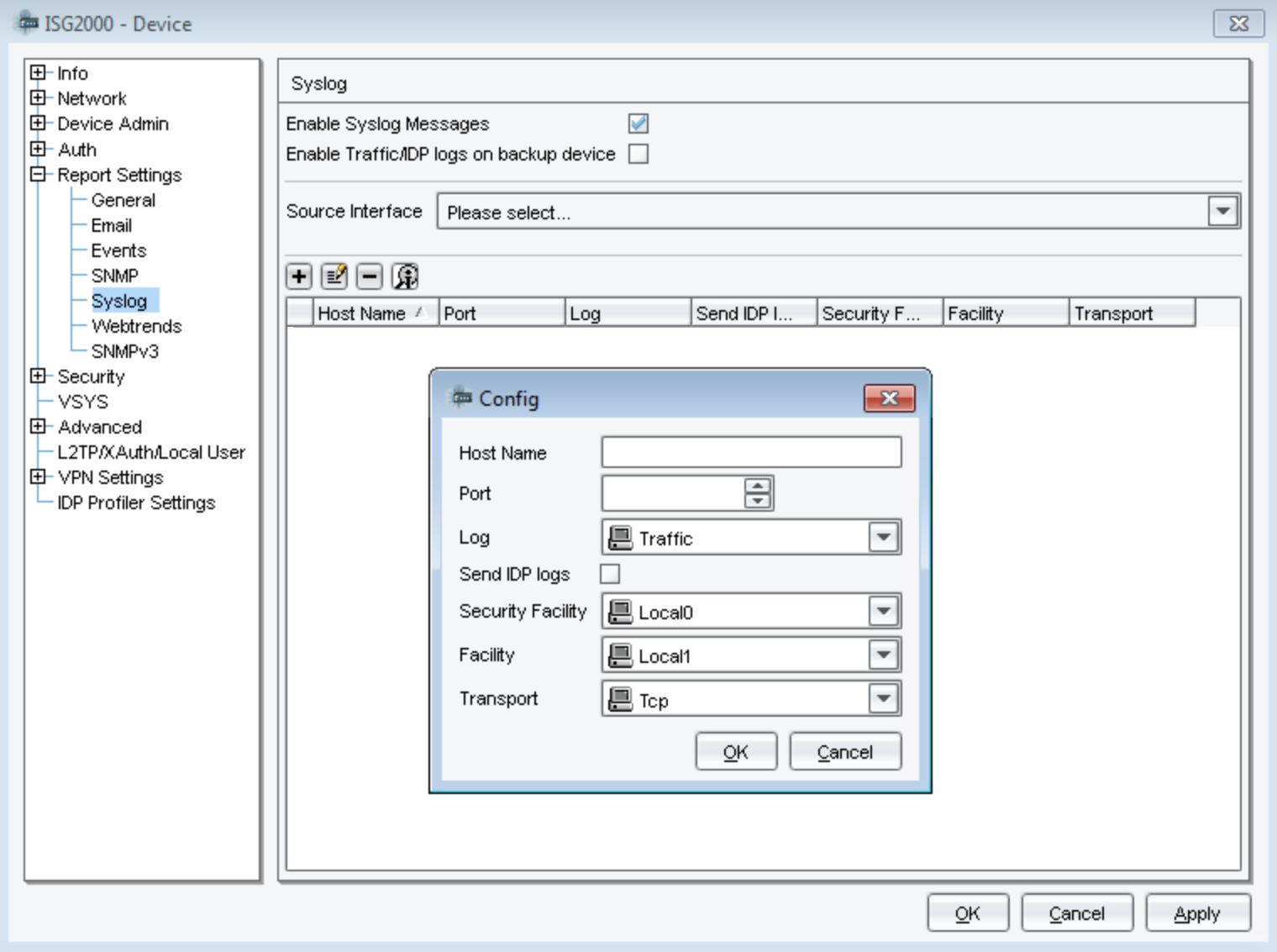
- In the “Facility” dropdown, select the Local1 option, which will capture events from all of the following levels:
- Local1 = Info
- Local2 = Notify
- Local3 = Warning
- Local4 = Error
- Local5 = Critical
- Local6 = Alert
- Local7 = Emergency
- In the “Transport” dropdown, select TCP as your option.
- Click the OK button. The syslog host will appear in the table.
- Click the Apply button to finish the configuration.
Configure SIEM (InsightIDR) to collect data from the event source
After you complete the prerequisite steps and configure the event source to send data, you must add the event source in SIEM (InsightIDR).
To configure the new event source in SIEM (InsightIDR):
- From the left menu, go to Data Collection and click Setup Event Source > Add Event Source.
- Do one of the following:
- Search for Juniper NetScreen in the event sources search bar.
- In the Product Type filter, select Firewall.
- Select the Juniper NetScreen event source tile.
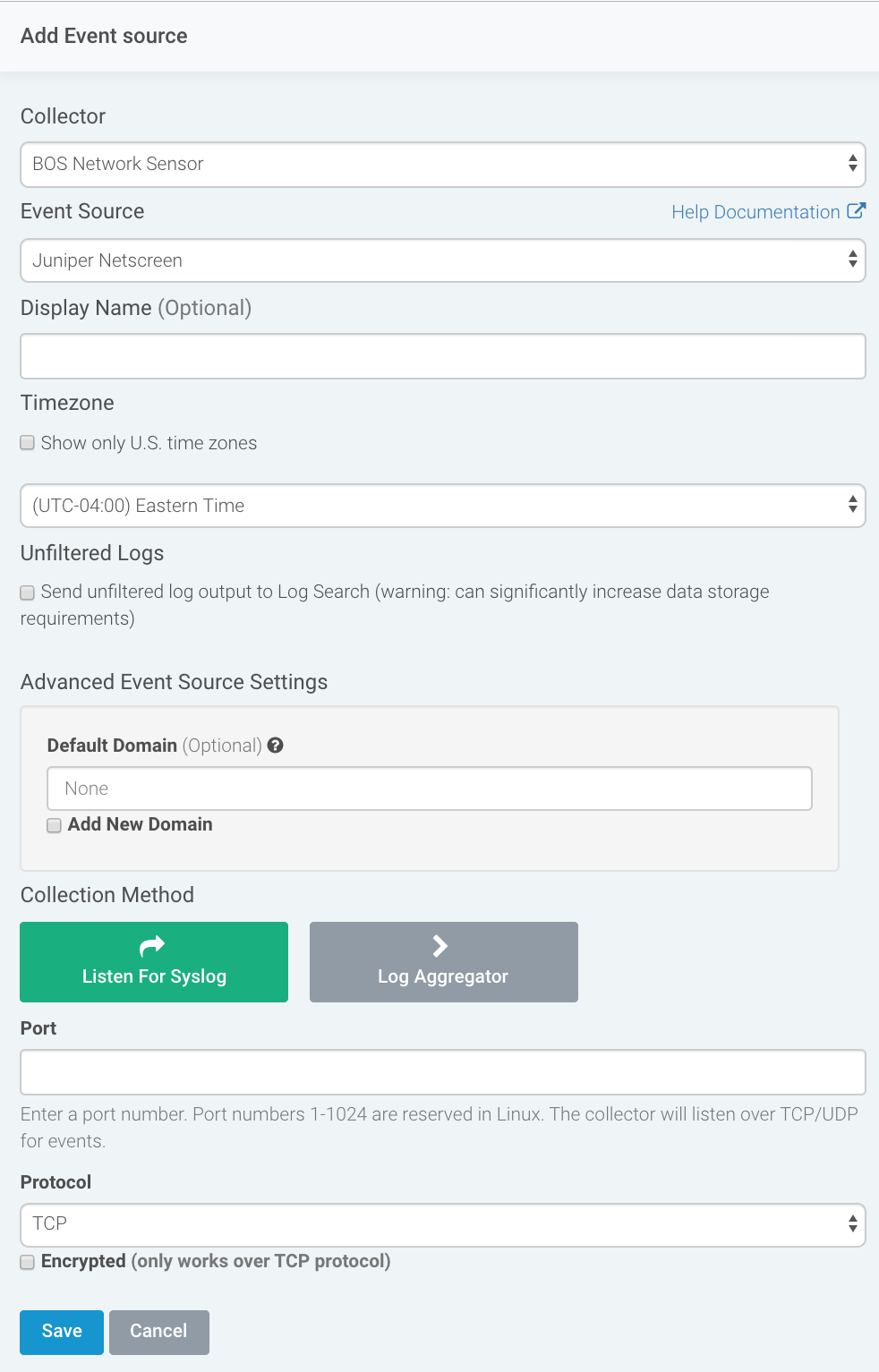
- Choose your collector and select Juniper Netscreen as your event event source. You can also name your event source if you want.
- Choose the timezone that matches the location of your event source logs.
- Optionally choose to send unparsed logs.
- Configure your default domain and any advanced settings.
- Select Syslog as your data collection method, enter the port you specified in the Juniper configuration, and select TCP as your protocol.
- Download the Rapid7 Certificate and install it following the Juniper configuration here: https://kb.juniper.net/InfoCenter/index?page=content&id=KB4777 .
- Click the Save button.
Verify the Configuration
After you finish creating the event source in SIEM (InsightIDR), you should see logs appear in Log Search.
SIEM (InsightIDR) expects logs with the following format:
<133>netscr_pri_01: NetScreen device_id=nsisg2000a [Root]system-notification-00257(traffic): start_time="2014-04-11 14:11:08" duration=0 policy_id=1245 service=syslog proto=17 src zone=Global dst zone=Global action=Deny sent=0 rcvd=390 src=1.2.3.4 dst=5.6.7.8 src_port=50000 dst_port=500 session_id=0 reason=Traffic Denied
<133>netscr_pri_01: NetScreen device_id=nsisg2000a [Root]system-notification-00257(traffic): start_time="2014-04-11 14:10:58" duration=9 policy_id=2051 service=http proto=6 src zone=Partners dst zone=DMZ action=Permit sent=817 rcvd=2293 src=1.2.3.4 dst=5.6.7.8 src_port=4000 dst_port=8080 src-xlated ip=1.2.3.4 port=4000 dst-xlated ip=5.6.7.8 port=8080 session_id=123456 reason=Close - TCP FIN
The sample logs are from the Integrated Security Gateway (ISG) 2000a series of ScreenOS 6.0 devices.