Data Leakage Threats
The Data Leakage tab shows the following threats:
- Ransomware leak threats: Data found in sources leaked by Ransomware threat actors.
- Confidential document threats: Company confidential documents that are exposed publicly.
Ransomware leak threats
This section contains all the information that is relevant to Ransomware leaks. In some cases, there are links to additional information, for your convenience.
Rapid7 monitors ransomware group leak sites and collects, extracts, and analyzes the data that has been published (in the clear or dark web) from other company’s leaks. Some of these leaks may threaten your company, while others may not.
The Digital Risk Protection (Threat Command) Ransomware Leaks tab shows published data leaks, even if none of your company assets were in the leak. This enables you to know not only if you are at risk, but also if there is no risk.
With this knowledge, you can examine, analyze, and report your potential risks sooner and more completely.
The key to your company is in the Matched objects column. This shows how many of your company’s assets - Company names, Domains, or Brand names - were found in published ransomware data.
With the threat tab, you can easily determine which ransomware leak threats are relevant to your company. The following table describes the possible threats - based primarily on the matched objects - and how we recommend that you respond:
| Threat type | Description | Recommendation |
|---|---|---|
| Clean | No evidence that any of your assets were exposed; no company assets were mentioned. | No further action is required. |
| Mentioned | Your assets were mentioned, but the mention doesn’t seem relevant or threatening. | Review the matched objects (files and folders) to evaluate future action. |
| Alert | Your assets were mentioned. Based on the context and relevance, we assess that the exposure may pose a risk to your company. | Review the matched objects (files and folders) and perhaps the directories listings, as well, to evaluate future action. |
The following figure illustrates what these threat types look like:
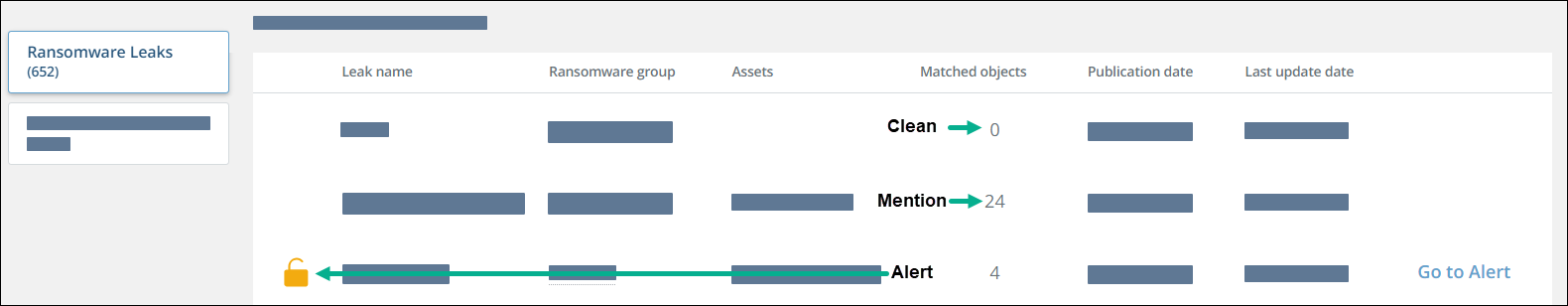
By default, threats are sorted by last update date, with the most recent first. You can reverse the sort order or sort by other columns. You can also filter the view by using the filter buttons above the table.
When you hover over certain ransomware group names, that group’s information from the Threat Library is displayed.
Each threat line includes details such as leak name, ransomware group, assets, and the number of matched objects. To see the full threat details, click the threat line.
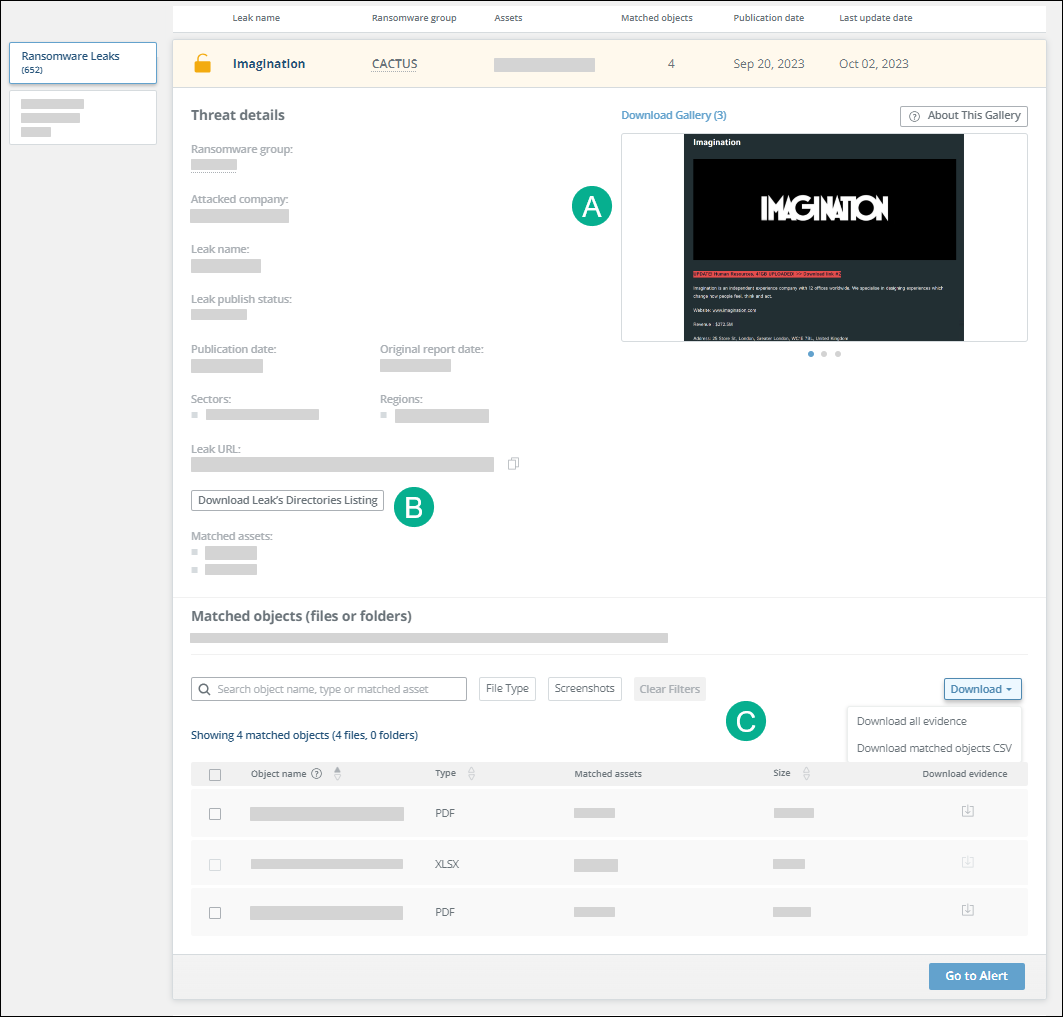
From the threat details section, you can:
- View extended threat details - This section shows additional details about the leak. Exercise extreme caution before clicking the leak URL.
- View and download the gallery (A) - The gallery may include screenshots from the ransomware blog site. If the link includes matched objects, screenshots of those may be included, too. You can download the gallery screenshots with the Download Gallery link.
- Download the leak’s directory listing (B) - Use this CSV listing to determine if your matched objects are in relevant paths. For example, a matched object found in a desktop folder is much more likely to be relevant than if that same object were in a path with the word “junk” in it. To download the file, click Download Leaked Directories Listing. This option is available for all threats, even if there are no matched objects.
- Download leak evidence and matched objects (C) - The Matched objects table shows all folders whose name contains a company asset and also files where a company asset is in the name or content. From the Download dropdown, you can download the following:
- Individual evidence - Select an object then click . To download multiple, select them and click Download Selected.
- All evidence - This contains all of the displayable forms of evidence. Certain file types, such as spreadsheet files, are not displayable. For more information, see Ransomware limitations.
- Matched objects CSV - Use this CSV of all the matched objects for further analysis. You can filter the matched objects.
Ransomware alerts
Whereas the threat page lists all leaks, alerts are only triggered if they meet the conditions in the Alert Profiler default rule, so threats that meet these conditions will trigger an alert:
- A company asset was found AND it is company-relevant (“apple” as a fruit would not be deemed relevant, but if it were a company name it could be).
OR - Multiple company assets of multiple types were found, even if not relevant.
The Alert Profiler rule is enabled, by default.
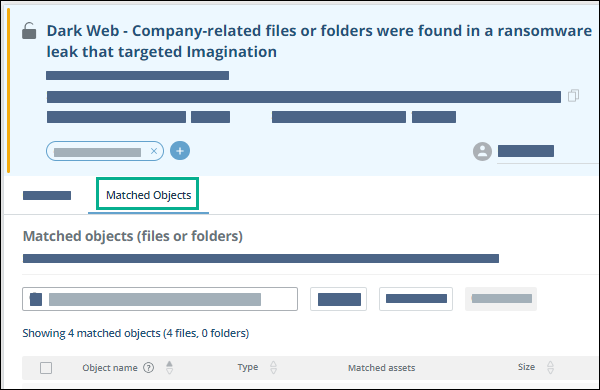
Alerts include a Matched Objects tab, with the same information and download options as in the threat details.
You can use the Alert Profiler to change the way that alerts are triggered. For example, you can make alerts trigger:
- for all mentions of company assets, even if there does not seem to be any relevance
- when your assets are found in a leak in a specific sector or geographic region
You can see the available conditions and use of the Alert Profiler.
Alert Profiler Examples
These examples show how you can use the Alert Profiler to fine-tune ransomware alert reporting.
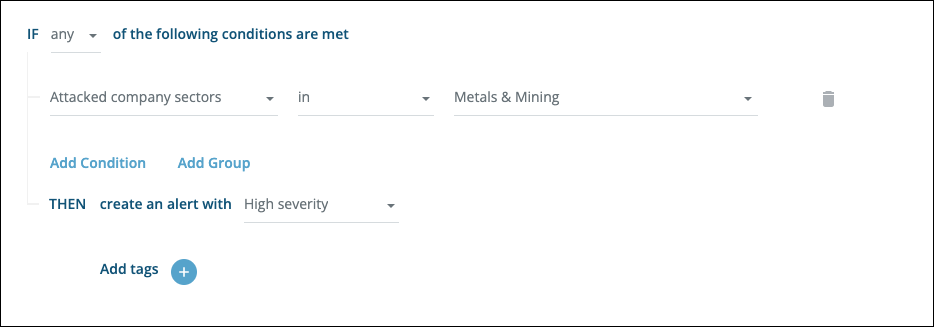
Trigger an alert when a leak is published about a specific sector:
Trigger an alert when a specific ransomware group publishes a leak:
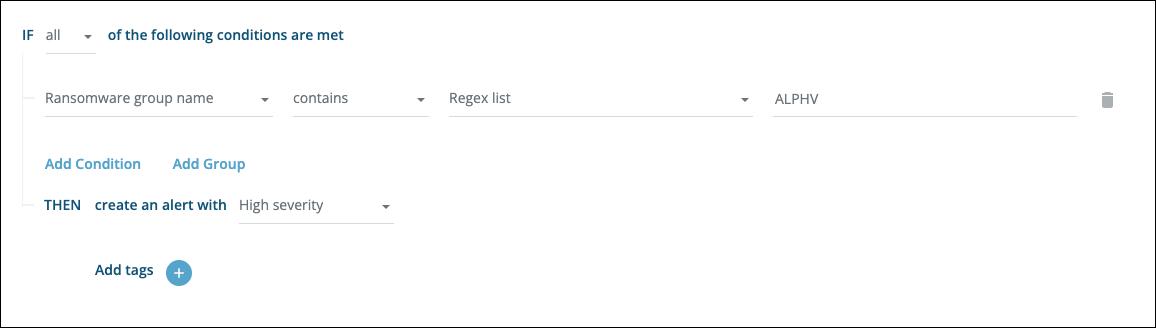
Trigger an alert when your assets are mentioned in any context (even if not deemed to be relevant):
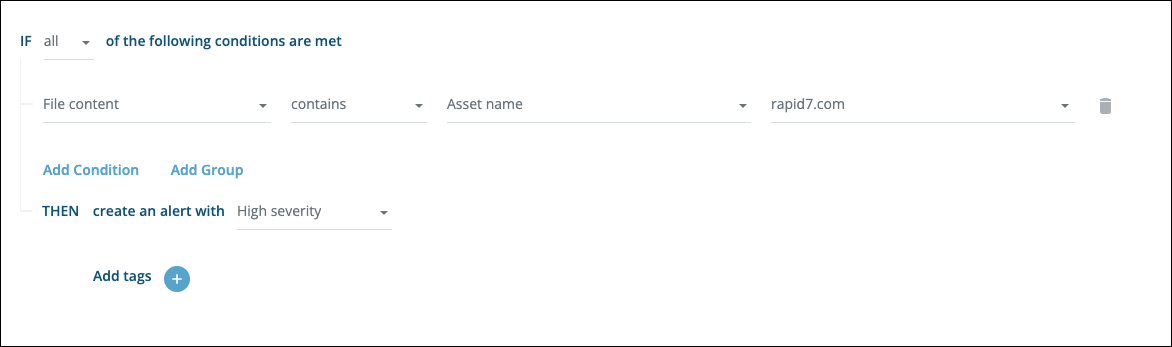
Ransomware Limitations
The following limitations apply to ransomware leak threats:
- Full leak processing may take several days from the time the leaked data is published.
- Only fully published leaks are uploaded, not partially published.
- Ransomware leak threats that originate from the following are not uploaded:
- governmental institutes, federal agencies, and civil databases
- hospitals, health insurance companies, religious institutions (such as temples or churches)
- private social media accounts, credit card companies, and credit bureaus
- human resources platforms (such as Workday) or companies
- membership or affiliation in any organization specific to race, ethnicity, sexual orientation, religion, or health condition
- primary or secondary schools
- pornographic websites
- Only organizational data (such as company strategy documents, commercial methods, and metrics) is uploaded, not data about individuals and personal information.
- Evidence, including gallery screenshots, are redacted to protect privacy. Your matched assets will be highlighted and displayed to you only. (For example, if name@yourdomainasset is found, the name part will be redacted and the domain will be highlighted). Other companies will see only their matched assets. This ensures the privacy of every company seeing this data.
- The following table shows the evidence types that can be displayed and downloaded:
| Format type | Supported | Not supported |
|---|---|---|
| File | Data Interchange Format .dif dBase .dbf HTML Document (Calc) .html SYLK .slk | ODF Spreadsheet .ods ODF Spreadsheet Template .ots Flat XML ODF Spreadsheet .fods Unified Office Format Spreadsheet .uos Microsoft Excel 2007-2013 XML .xlsx Microsoft Excel 2003 XML .xml Microsoft Excel 97-2003. xls Microsoft Excel 97-2003 Template .xlt Text CSV .csv Office Open XML Spreadsheet .xlsx Microsoft Excel 2007-2016 XML (macro enabled).xlsm |
| Presentation | Office Open XML Presentations and Templates (*.pptx, *.ppsx, *.ppmx, *.potx, *.pomx) format (strict OpenXML). Microsoft PowerPoint 2007/2010 Presentations and Templates (*.pptx, *.ppsx, *.ppmx, *.potx, *.pomx) format (transitional OpenXML). Microsoft PowerPoint 97/2000/XP/2003 Document (*.ppt, *.pps, *.ppm, *.pot, *.pom) format | |
| Spreadsheet | No supported formats | Office Open XML Spreadsheets and Templates (*.xlsx, *.xlsm, *.xlst) format (strict OpenXML). Microsoft Excel 2007/2010 Spreadsheets and Templates (*.xlsx, *.xlsm, *.xlst) format (transitional OpenXML). Microsoft Excel 97/2000/XP/2003 Document (*.xls, *.xlw, *.xlc, *.xlt) format. Microsoft Excel 4.x-5/95 Spreadsheets and Templates (*.xls, *.xlw, *.xlc, *.xlt) format. |
| Word processing | Office Open XML Documents and Templates (*.docx, dotx) format (strict OpenXML). Microsoft Word 2007/2010 Documents and Templates (*.docx, *.dotx) format (transitional OpenXML). Microsoft Word 2003/2007 XML (*.xml) format. Microsoft Word 97/2000/XP/2003 Documents and Templates (*.doc, *.dot) format Microsoft Word 6.0-95 Document (*.doc) format. Microsoft WinWord 5 Document (*.doc) format. Microsoft Rich Text Format (*.rtf). |
To add a specific leak, contact Customer Support or use the Ask an analyst portal (preferably with the leak URL).