Evidence Best Practice Guidelines
When reporting malicious activity to third-party vendors, they will request particular information related to the activity so that the suspicious site, domain, or similar can be removed. The following sections describe the documentation and information vendors will request to remediate malicious activity.
Evidence required by vendors for remediation
These tables describe the data required by vendors when reporting malicious activity as part of the remediation process. You can find more information about uploading trademarks and letters of authorization (LOA) in Preparing for Remediation . In general, remediations are more successful if you have provided both the company’s Registered Trademark and a signed Letter of Authorization (LOA) in Configurations .
Requirements for Exploitable Data, Data Leakage, Brand Security, or VIP takedown remediation
| Vendor Name | What needs to be taken down? | Trademark Needed? | LOA Needed? | Details |
|---|---|---|---|---|
| Apple App Store | Trademark - Client’s logo or Client’s name | ✓ | The vendor requires a trademark registration document. | |
| Application Stores | Trademark - Client’s logo or Client’s name | ✓ | ✓ | The vendor may require a trademark registration document and a signed LOA in some cases (depending on the application store). |
| Email Outlook | A phishing email that was sent by the reported email address | The vendor requires a copy of the abusive message that was sent by the reported email address (including the full message header). | ||
| Etsy | Trademark - Client’s logo or Client’s name | The team doesn’t have enough data on this type of case to determine which documents are needed. | ||
| Facebook - Trademark and copyright | Trademark - Client’s logo or Client’s name | ✓ | The trademark registration document is mandatory and the vendor requires a signed LOA in some cases. | |
| Facebook - VIP | VIP’s name and photo | ✓ | The VIP’s ID is required by the vendor. There are two options: 1. Government ID: Driver’s license, national identity card, passport, or birth certificate. The ID must include the VIP’s name and date of birth or name and photo. 2. Non-Government IDs: Student card, library card, refugee card, employment verification, diploma, or loyalty card. All IDs must include the VIP’s name, and at least one of the two IDs must include the VIP’s date of birth and/or photo. The vendor requires a signed LOA required in some cases. | |
| Flickr | Trademark - Client’s logo or client’s name | The team doesn’t have enough data on this type of case to determine which documents are needed. | ||
| GitHub | Sensitive information about the client: - Access credentials (passwords, emails, BIN number, etc.) - Leaked secrets - Source code - Documents | ✓ | Files/repositories that expose: 1. Access credentials, such as user names combined with passwords, access tokens, or other sensitive secrets that can grant access to your organization’s server, network, or domain. 2. AWS tokens and other similar access credentials that grant access to a third party on your behalf. You must be able to show that the token does belong to you. 3. Documentation (such as network diagrams or architecture) that poses a specific security risk for an organization. 4. Information related to, and posing a security risk to, you as an individual (such as social security numbers or other government identification numbers). | |
| Google Ads | Trademark - Client’s logo or client’s name | ✓ | ✓ | The vendor requires a trademark registration document and a signed LOA. |
| Google Play | Trademark - Client’s logo or client’s name | ✓ | ✓ | The vendor requires a trademark registration document and a signed LOA. |
| Google Plus | Trademark - Client’s logo or client’s name | ✓ | ✓ | The vendor requires a trademark registration document and a signed LOA. |
| Instagram - Trademark or Copyright | Trademark - Client’s logo or client’s name | ✓ | ✓ | A trademark registration document is mandatory. A signed LOA may be required by the vendor in some cases. |
| Instagram - VIP | VIP’s name and photo | ✓ | The VIP’s ID is required. There are two options: 1. Government ID: Driver’s license, national identity card, passport, or birth certificate. The ID must include the VIP’s name and date of birth or name and photo. 2. Non-Government IDs: Student card, library card, refugee card, employment verification, diploma, or loyalty card. All IDs must include the VIP’s name, and at least one of the two IDs must include the VIP’s date of birth and/or photo. A signed LOA is required in some cases. | |
| LinkedIn - Trademark or copyright | Trademark - Client’s logo or client’s name | The vendor may require a trademark registration document and a signed LOA in some cases. | ||
| LinkedIn - VIP | VIP’s name and photo | The vendor may require a trademark registration document and a signed LOA in some cases. | ||
| Paste Sites | Sensitive information about the client: - Access credentials (passwords, emails, BIN number, etc.) - Leaked secrets - Source code - Documents | The vendor may require a trademark registration document and a signed LOA in some cases. | ||
| Pastebin | Sensitive information about the client: - Access credentials (passwords, emails, BIN number, etc.) - Leaked secrets, source code, documents | The vendor may require a trademark registration document and a signed LOA in some cases. | ||
| Trademark - Client’s logo or client’s name | ✓ | The vendor may require a trademark registration document and a signed LOA in some cases. | ||
| Trademark - Client’s logo or client’s name | ✓ | The vendor may require a trademark registration document and a signed LOA in some cases. | ||
| Scribd - Account | Trademark - Client’s logo or client’s name | The vendor may require a trademark registration document and a signed LOA in some cases. | ||
| Scribd - Post | Trademark - Client’s logo or client’s name Sensitive information about the client: - Access credentials (passwords, emails, BIN number, etc.) - Leaked secrets - Source code - Documents | The vendor may require a trademark registration document and a signed LOA in some cases. | ||
| Studylib | Trademark - Client’s logo or client’s name Sensitive information about the client: - Access credentials (passwords, emails, BIN number, etc.) - Leaked secrets - Source code - Documents | The vendor may require a trademark registration document and a signed LOA in some cases. | ||
| Telegram | Trademark Client’s logo AND Client’s name Telegram policy protects the content of messages inside a group or channel, so those are not sufficient proof of abuse. | Global trademarks and a signed LOA are required in some cases | ||
| TikTok | Trademark - Client’s logo or client’s name | ✓ | ✓ | The vendor requires a trademark registration document and a signed LOA. |
| Tumblr | Trademark - Client’s logo or client’s name | The team doesn’t have enough data on this type of case to determine which documents are needed. | ||
| Twitter - Trademark or copyright | Trademark - Client’s logo AND client’s name Specific Tweets are not supported according to Twitter policy. | ✓ | ✓ | The vendor requires a trademark registration document and a signed LOA. |
| Twitter - VIP | VIP’s name and photo | ✓ | The vendor requires the VIP’s valid government-issued photo ID (driver’s license/passport) and a signed LOA. | |
| VK | Trademark - Client’s logo or client’s name | ✓ | A trademark registration document is mandatory. A signed LOA may be required by the vendor in some cases. | |
| Veoh | Trademark - Client’s logo or client’s name | ✓ | A trademark registration document is mandatory. A signed LOA may be required by the vendor in some cases. | |
| Vimeo | Trademark - Client’s logo or client’s name | ✓ | Trademark registration document is mandatory. A signed LOA may be required by the vendor in some cases. | |
| VirusTotal | Trademark - Client’s logo or client’s name Sensitive information about the client: - Access credentials (passwords, emails, BIN number, etc.) - Leaked secrets - Source code - Documents | Trademark registration document is mandatory. A signed LOA may be required by the vendor in some cases. | ||
| Trademark - Client’s logo or client’s name | Trademark registration document is mandatory. A signed LOA may be required by the vendor in some cases. | |||
| YouTube | Trademark - Client’s logo or client’s name | ✓ | ✓ | The vendor requires a trademark registration document and a signed LOA. |
Requirements for Phishing (website and domain) takedown remediation
| Takedown Type | Vendor Name | Evidence Needed? | Trademark Needed? | LOA Needed? | Details |
|---|---|---|---|---|---|
| Phishing Website | AWS | Optional | The vendor may require a trademark registration document and a signed LOA in some cases. | ||
| Phishing Website | Cloudflare | Optional | The vendor may require a trademark registration document and a signed LOA in some cases. | ||
| Phishing Website | Digital Ocean | Optional | The vendor may require a trademark registration document and a signed LOA in some cases. | ||
| Phishing Website | GoDaddy | ✓ | The vendor may require a signed LOA in some cases | ||
| Phishing Domain | GoDaddy | A phishing email that was sent by the reported email address. | The full email headers and email content that sent by the reported domain. The vendor may require a signed LOA in some cases. | ||
| Phishing Website | ✓ | ✓ | The vendor requires a trademark registration document and a signed LOA. | ||
| Phishing Domain | A phishing email was sent by the reported email address. | ✓ | The full email headers and email content sent from the reported domain. The vendor requires a signed LOA. | ||
| Phishing Website | Hostinger | Optional | The vendor may require a trademark registration document and a signed LOA in some cases. | ||
| Phishing Website | Microsoft | ✓ | ✓ | The vendor requires a trademark registration document and a signed LOA. | |
| Phishing Website | Namecheap | Optional | The vendor may require a trademark registration document and a signed LOA in some cases. | ||
| Phishing Domain | Namecheap | A phishing email that was sent by the reported email address. | The full email headers and email content sent from the reported domain. The vendor may require a signed LOA in some cases. | ||
| Phishing Website | Name.com | Optional | The vendor may require a trademark registration document and a signed LOA in some cases. | ||
| Phishing Website | Namesilo | The vendor may require a trademark registration document and a signed LOA in some cases. |
Request removal of a suspicious domain
To take down a domain, the registrars demand very specific evidence of malicious activity. This section shows you how!
Evidence can be uploaded in TXT, MSG, EML, or MBOX formats. Virus scans can be uploaded in PDF or TXT formats.
To request a takedown of a suspicious domain, the user must supply the original phishing email, sent from the suspicious domain, complete with the email headers (not simply a screenshot).
The header information provides the digital trail of the email and describes how the email passed from its origin to the user’s mailbox. This serves the following purposes:
- Validate the legitimacy of the email (headers are very difficult to falsify).
- Provide some insight into if the email came from the domain listed or if it was spoofed.
Follow the instructions in the following sections to prepare evidence for uploading to the remediation request.
- To extract email headers from Gmail:
- To extract email headers from Outlook:
- To extract email headers from Apple Mail:
- To create a malware scan with VirusTotal:
- To create a malware scan with URLscan.io:
If proper evidence cannot be produced, see what other options are available at Additional Monitoring and Protection Steps.
To extract email headers from Gmail
- In Gmail, open the email message for which you want to extract the header.
- In the top-right of the message, click More, then select Show original.
A page with the email headers is displayed in a new tab or window:
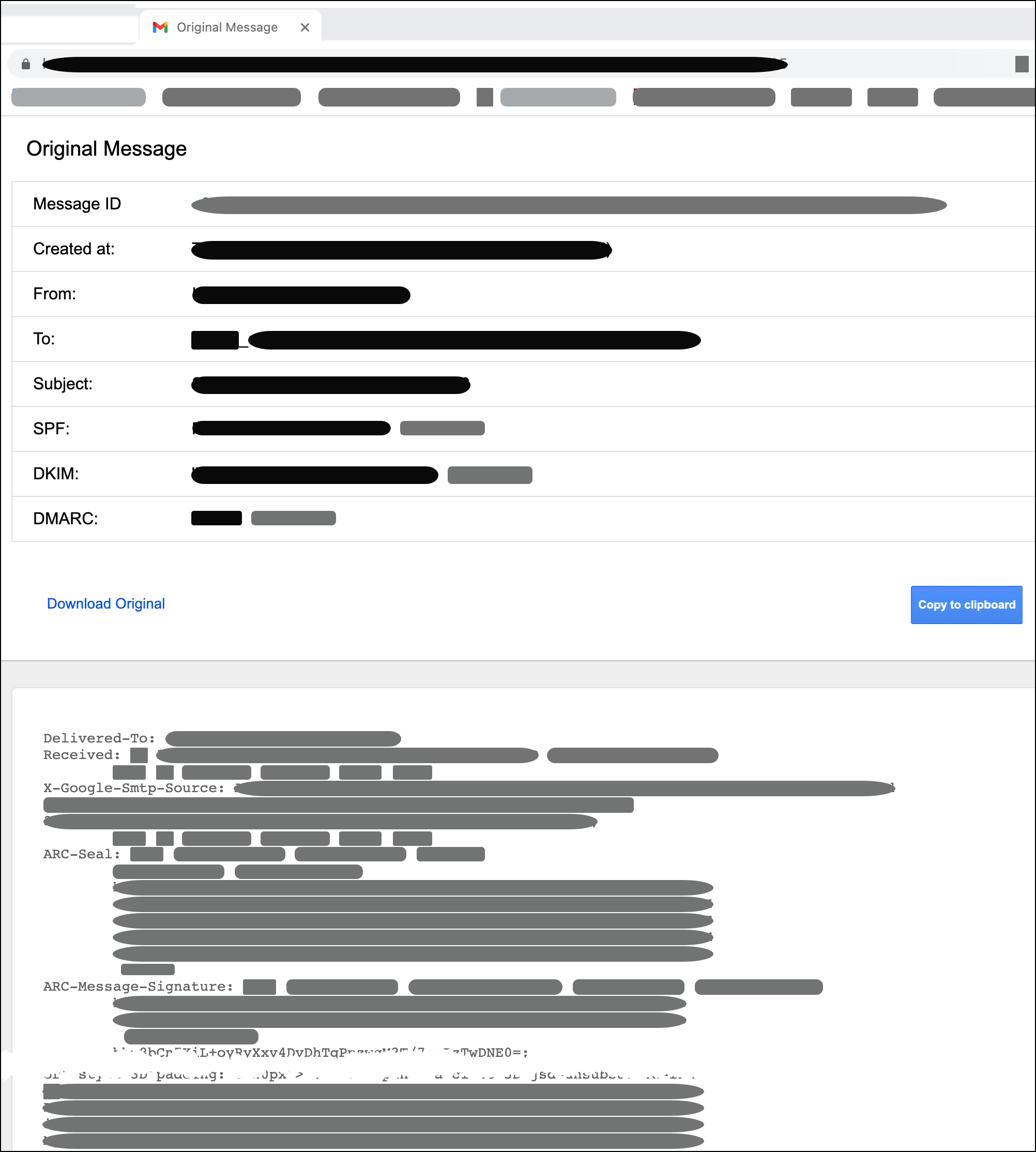
- Click Copy to clipboard (or highlight and copy everything), then paste into a searchable text editor.
- Search (Ctrl+F) to ensure that the phishing domain is located in the pasted content.
- Attach the pasted content to the takedown request as TXT, MSG, EML, or MBOX.
Alternatively, click Download Original, and upload the downloaded EML file.
To extract email headers from Outlook
-
Double-click the email message so it displays in a full window.
-
Display the Properties dialog in either of these ways:
- From the email window, choose File > Properties.
- From the email window, from the Tags section, click the small down-arrow:
The Properties dialog is displayed:
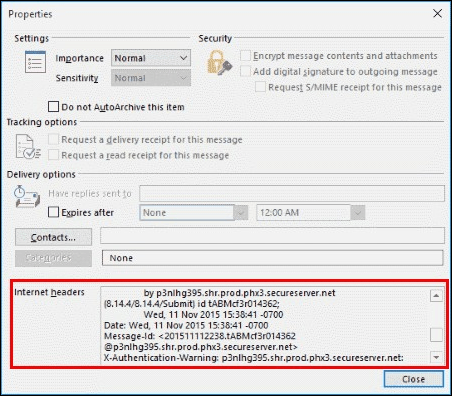
- Highlight, copy and, paste everything from the Internet headers section into a searchable text editor.
- Search (Ctrl+F) to ensure that the phishing domain is located in the pasted content.
- Attach the pasted content to the takedown request as TXT, MSG, EML, or MBOX.
To extract email headers from Apple Mail
- Open the email message in the macOS or OS X Mail reading pane or its window.
- Choose View > Message > All Headers.
The email header is displayed:
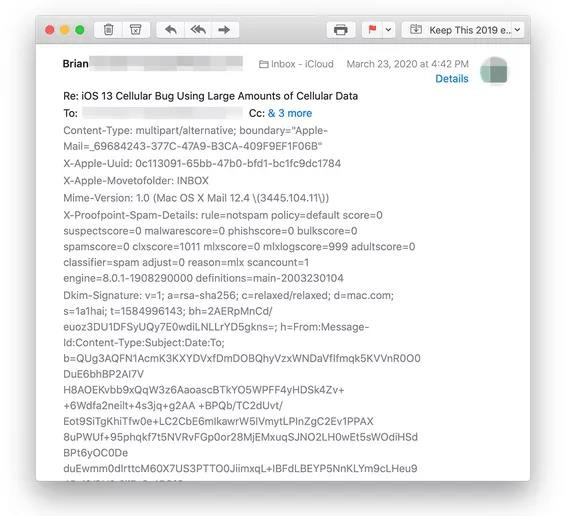
- Highlight, copy and, paste everything from the Internet headers section into a searchable text editor.
- Search to ensure that the phishing domain is located in the pasted content.
- Attach the pasted content to the takedown request as TXT, MSG, EML, or MBOX.
To create a malware scan with VirusTotal
- Copy the domain name that you want to scan.
- Visit https://www.virustotal.com/
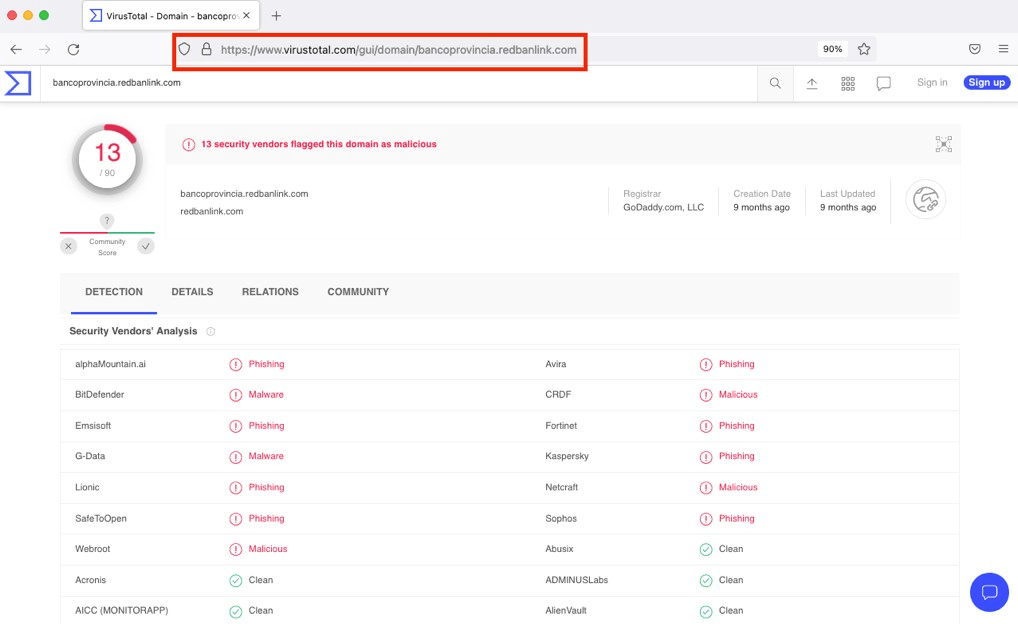
- Select the Search tab and paste the domain name:
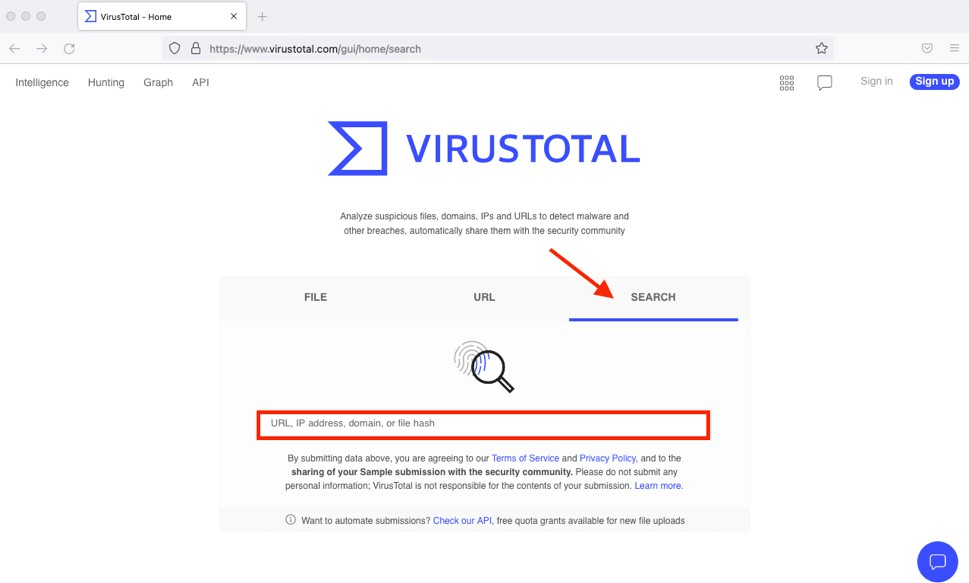
The domain scan is displayed, in which you can verify if there is malicious activity:
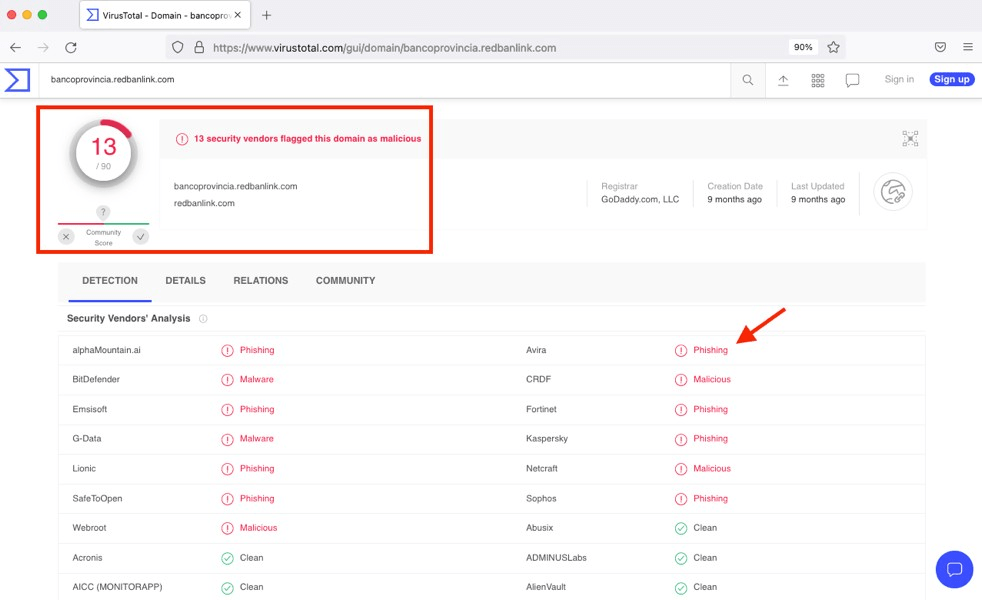
-
Copy and paste the URL of the page, then upload that URL as evidence as a PDF or TXT file.
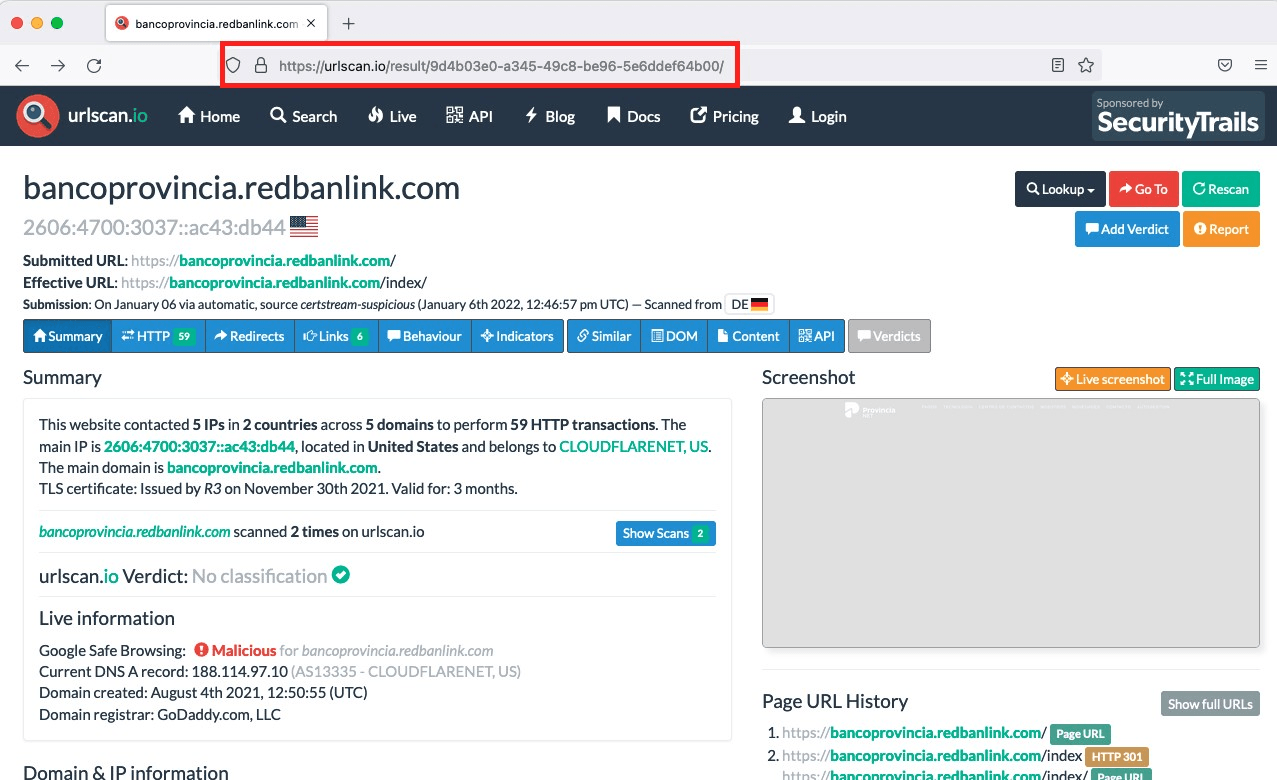
To create a malware scan with URLscan.io
-
Copy the domain name you want to scan.
-
Visit https://urlscan.io/
-
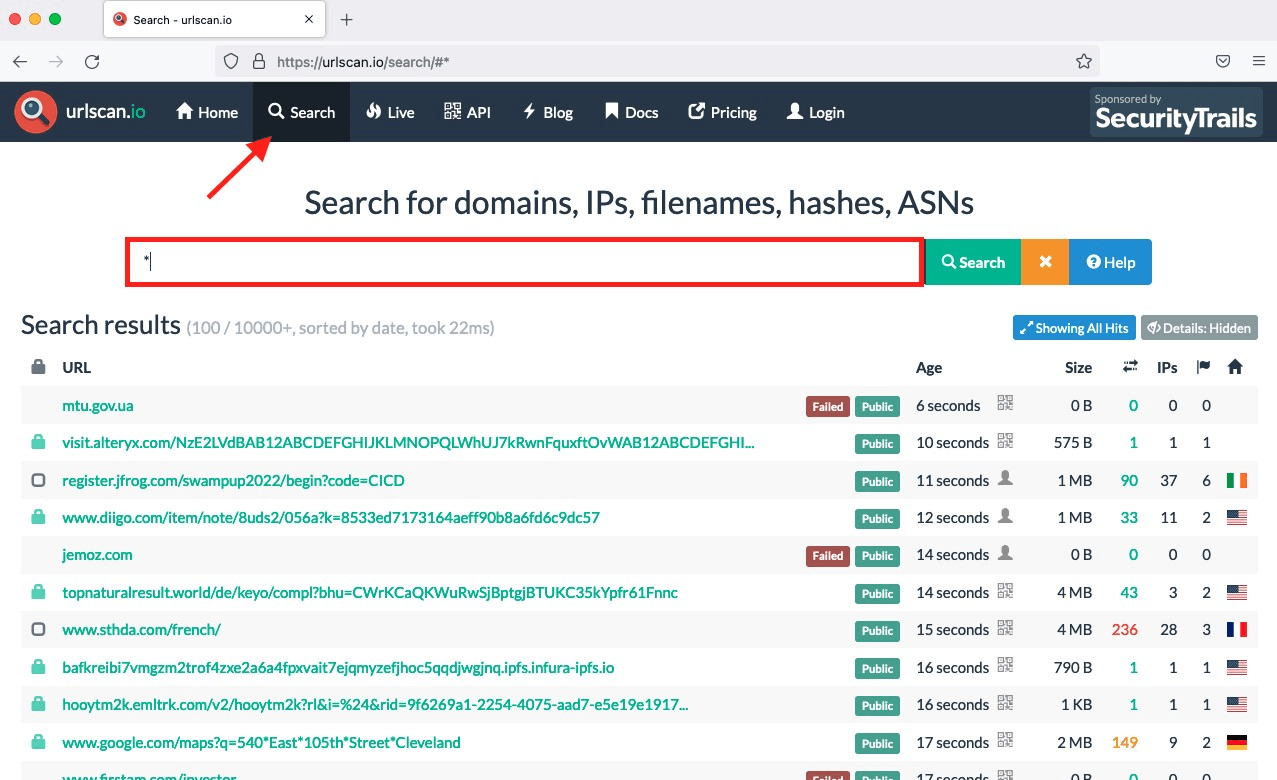
Click Search and paste the domain name:
The domain scan is displayed, in which you can verify if there is malicious activity:
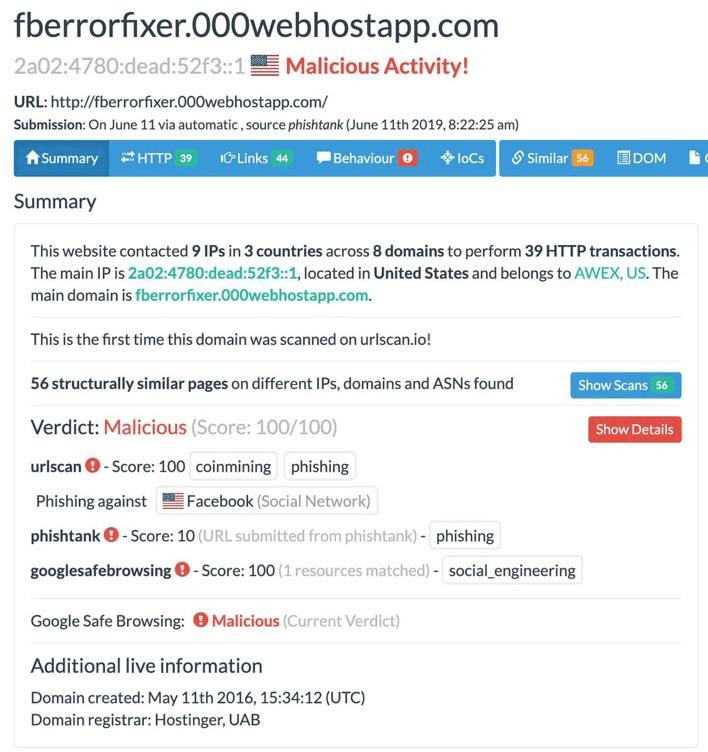
- Copy and paste the URL of the page, then upload that URL as evidence as a PDF or TXT file.