Host Vulnerability Assessment - Configuration & Workflows
The information on this page has moved
For the most up to date Host Vulnerability Assessment (HVA) guidance, go to Configuring Host Vulnerability Assessment (HVA).
Host Vulnerability Assessment (HVA) enables Security and DevOps teams to efficiently view, prioritize, and orchestrate the response to vulnerabilities (Common Vulnerabilities and Exposures (CVEs)) detected on host instances across their related cloud accounts and production workloads. Hosts are automatically assessed when they are launched and detected by the InsightCloudSec harvesters without the use of traditional network scanning or an embedded agent. Using snapshots of the instances’ root volume, a thorough vulnerability assessment is performed on all packages in the guest operating system and installed software, on Open Source Software (OSS) dependencies, and on select file types. The permissions and configuration required to harvest and assess snapshots across your cloud accounts is detailed below.
The following example shows a normal HVA workflow:
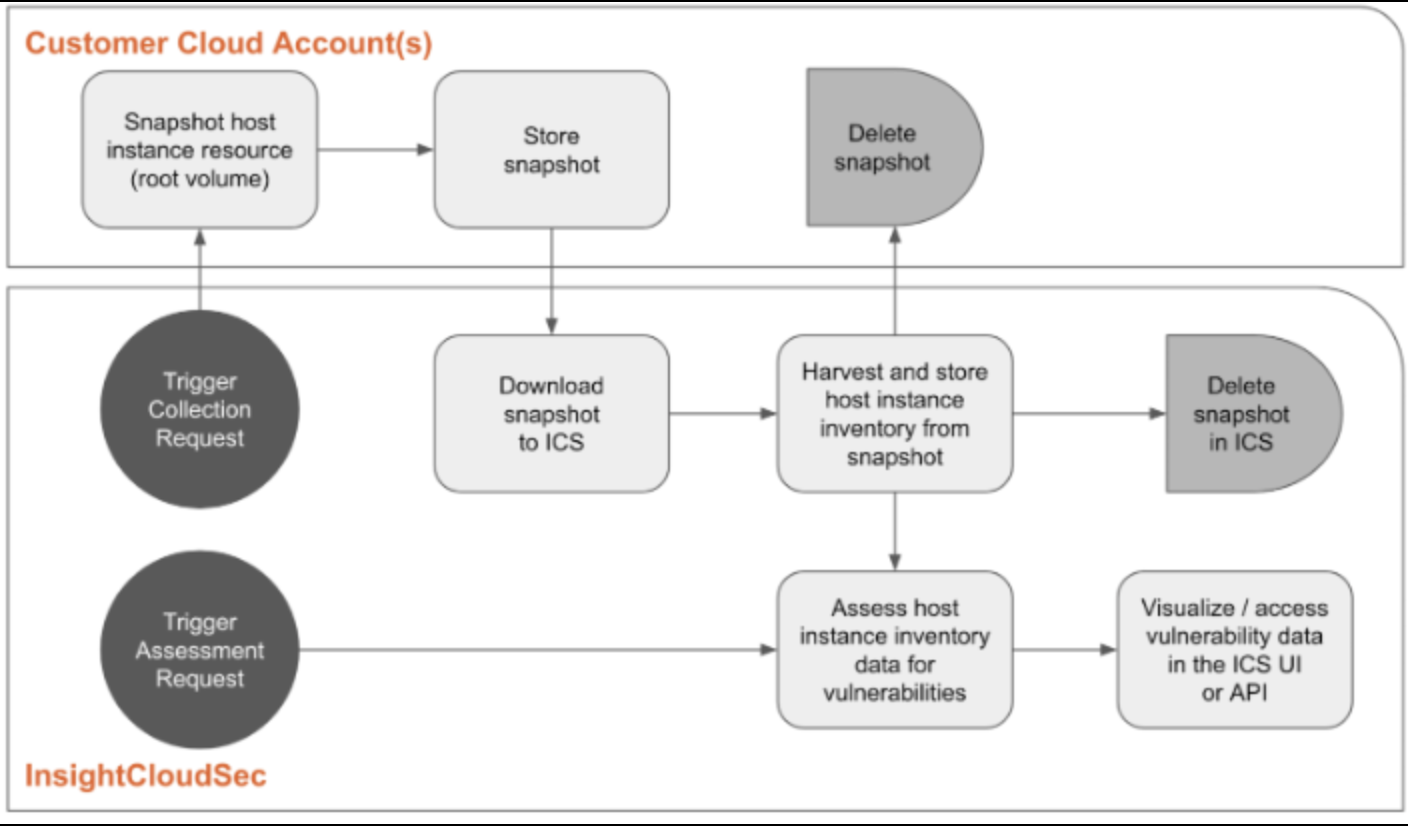
Current Support
HVA supports AWS EC2, Azure Virtual Machine (VM), and GCP VM instances and is only available to InsightCloudSec SaaS customers. In addition, Windows hosts are not supported and will fail assessment.
Prerequisites
Before getting started with HVA you will need to have the following:
- An InsightCloudSec installation (v. 23.2.28) (SaaS-Only)
- The AWS, Azure, and/or GCP permissions outlined below
AWS
These permissions are not part of a default Read-Only AWS deployment and must be explicitly configured to enable operation of the HVA feature. As of InsightCloudSec v. 23.4.11, the new universal onboarding experience for AWS accounts uses CloudFormation Templates (CFTs) to automatically provision relevant accounts with the necessary policies and roles. This means it is easiest to perform HVA configuration while onboarding an account/organization. Review AWS Cloud - Onboarding for more information.
| AWS Permission | Requirement Details |
|---|---|
ec2:CreateSnapshot | Required to take a snapshot of the EBS volume that can be analyzed by InsightCloudSec. |
ec2:CreateTags | Required to create tags in the source account. |
ec2:CopySnapshot | Required to copy snapshots that are encrypted using the default AWS-managed key. |
ec2:DeleteSnapshot | Required to clean up the snapshot in the source account after the analysis has been completed. |
ec2:ModifySnapshotAttribute | Required to grant permission to the InsightCloudSec backend to download the snapshot. |
kms:CreateGrant | Required to create a grant to the KMS key that can be used to decrypt the EBS volume. |
kms:DescribeKey | Required to determine what key is being used to encrypt the volume that is being analyzed. |
kms:Decrypt | Required to decrypt the generated data key so that it can be used to encrypt the copied snapshot. |
kms:Encrypt | Required to encrypt the copied snapshot with a Rapid7-managed Key Management Service (KMS) key. |
kms:GenerateDataKeyWithoutPlaintext | Required to generate a data key that is encrypted under the symmetric encryption Rapid7 KMS key. The data key is used to encrypt the snapshot. |
kms:ReEncryptFrom | Required to modify encrypted snapshots to allow InsightCloudSec to share them to the Host Assessment Service for a Vulnerability Assessment. Review the AWS documentation for more information. |
kms:ReEncryptTo | Required to modify encrypted snapshots to allow InsightCloudSec to share them to the Host Assessment Service for a Vulnerability Assessment. Review the AWS documentation for more information. |
kms:RetireGrant | Required to delete the Rapid7 KMS key grant after the assessment has completed. |
Default Key-Encrypted Snapshots Information
Review this FAQ for more details.
HVA User Policy
The AWS HVA User Policy can be obtained from our public S3 bucket and used to create a custom policy within AWS that contains all the permissions necessary for HVA configuration and assessment. Review the AWS IAM documentation for more information.
Role Attachment
This policy will need to be attached to your existing InsightCloudSec Harvesting role.
Azure
In the table below are the minimum required permissions for your InsightCloudSec Azure role (this should already exist as part of Azure - Onboarding).
| Azure Permission | Requirement Details |
|---|---|
Microsoft.Compute/snapshots/write | Required to create a new snapshot. |
Microsoft.Compute/snapshots/read | Required to read the properties of a snapshot. |
Microsoft.Compute/disks/read | Required to read the properties of a disk. |
Microsoft.Compute/snapshots/beginGetAccess/action | Required to generate an SAS URL for access to the disk snapshot. |
Microsoft.Compute/disks/beginGetAccess/action | Required to generate an SAS URL for access to the disk snapshot. |
Microsoft.Compute/snapshots/endGetAccess/action | Required to disable an SAS URL. |
Microsoft.Compute/snapshots/delete | Required to delete a snapshot. |
HVA User Role
The Azure HVA User Role below can be copied and used to create a custom role within Azure that contains all the permissions necessary for HVA configuration and assessment. Ensure you replace the placeholder Subscription ID value.
{
"properties": {
"roleName": "Disk Access for Host Vulnerability Assessment",
"description": "Read Disk Properties, Revoke and Generate SAS URLs, Create and Delete Snapshots",
"assignableScopes": [
"/subscriptions/<subscription-id>"
],
"permissions": [
{
"actions": [
"Microsoft.Compute/snapshots/read",
"Microsoft.Compute/snapshots/write",
"Microsoft.Compute/snapshots/delete",
"Microsoft.Compute/snapshots/beginGetAccess/action",
"Microsoft.Compute/snapshots/endGetAccess/action",
"Microsoft.Compute/disks/read",
"Microsoft.Compute/disks/beginGetAccess/action"
],
"notActions": [],
"dataActions": [],
"notDataActions": []
}
]
}
}
Azure HVA Limitations
Azure HVA is limited by the following:
- Doesn’t support VMWare vSphere VMs or Azure Classic VMs (EOL in September 2023 )
- Doesn’t support disks with data access authentication mode enabled
- Doesn’t support disks encrypted with customer-provided keys. Review the Azure Blog for more information
GCP
In-Cloud Assessment
For GCP, InsightCloudSec supports In-Cloud Assessment, where all snapshots and scans occur inside GCP. InsightCloudSec snapshots your disks directly into an InsightCloudSec-owned GCP project, and all other GCP operations are done inside this project, minimizing cost to you.
To accomplish In-Cloud Assessment, GCP HVA uses a separate In-Cloud Service Account that is owned by InsightCloudSec and created per customer, instead of using your InsightCloudSec service account. You’ll only need to create the In-Cloud Service Account once through the InsightCloudSec Vulnerability Settings.
- Click “Generate Service Account”
- Copy the service account email or click “Copy and Open GCP console”
- Grant the In-Cloud Service Account the permissions below in the projects you want to assess.
In the table below are the required permissions. These are not automatically granted as part of GCP - Onboarding).
| GCP Permission | Requirement Details |
|---|---|
compute.disks.createSnapshot | Required to create a disk snapshot. |
Additional Permissions for CMEK-encrypted Disks (Optional)
If any disks use Customer Managed Encryption Keys (CMEK), the projects holding those disks will have to grant the InsightCloudSec HVA project’s Compute Engine Service Agent permission to use those CMEKs. You can read more about this requirement in Google Cloud documentation
The InsightCloudSec HVA Compute Engine Service Agent email: service-491641900622@compute-system.iam.gserviceaccount.com
| GCP Permission | Requirement Details |
|---|---|
cloudkms.cryptoKeyVersions.useToDecrypt | Required to access CMEK-encrypted disks. |
cloudkms.cryptoKeyVersions.useToEncrypt | Required to access CMEK-encrypted disks. |
GCP HVA Limitations
GCP HVA support is limited by the following:
- Cannot assess instances with disks encrypted by a Customer Supplied Encryption Key
- Cannot assess Local SSDs
Configuring HVA Assessments
Before hosts can be regularly assessed for vulnerabilities, you must enable the HVA feature and properly scope the hosts that should be assessed. These configuration settings (and others) can be found on the Vulnerability Settings page, which is accessed from the Vulnerabilities page.
Enabling HVA Assessments
Settings are Per InsightCloudSec Organization
The Vulnerability Settings below are unique to the particular InsightCloudSec Organization you are logged in to. For more information on InsightCloudSec Organizations (not to be confused with Cloud Organizations), see Organizations.
- Login to InsightCloudSec and navigate to the Vulnerabilities page.
- In the top right corner, click Settings.
- Click the Enable Host Vulnerability Assessment toggle. The Assessment Scope section appears.
Scoping HVA Assessments
After enabling the feature, you must scope your environment to the hosts that should be assessed. Scoping relies on the Advanced Filtering mechanism seen throughout InsightCloudSec.
Scope Required
Assessments will not be queued until at least one filter exists.
Add Filter
Filtering allows for narrowing the scope of the resources list using properties like cloud accounts, clusters, resource groups, etc. Some things to note about filtering behavior:
- Each selected filter updates dynamically with options appropriate for the property selected.
- After selecting an initial property, click + Add Filter to add an additional filter and further narrow the scope.
- If filtering on a Resource Tag:
- Searching for a tag is case insensitive.
- New tags are harvested every 12 hours by the
ResourceTypeTrigramsProcessbackground job (see System Settings for more information).
To add a filter:
- Click the Add Filters button to open the side panel.
- Select and configure a property to get started.
- After configuring your desired filters, click Apply to update the scope for the feature.
Save Filters (Optional)
After Adding a Filter, you can save it so that it can easily be reused the next time you access the feature. Saved filters are feature-specific (since options vary between features), i.e., a saved filter in Feature “A” will only be available in Feature “A” and will not be available in Feature “B”.
To save a filter:
- Once filter(s) have been applied, ensure the filters list is expanded by clicking the arrow (>)
- Click the ellipsis (…) button, then click Save Filter.
- Provide a name for the filter and an optional description.
- Select the checkbox for Set as Default Filter to set this filter as the default for the feature. This only applies to your user account and will not affect other users’ default filter.
- Select the checkbox for Make this a Public Filter to allow other users to use and see the filter.
- Click OK.
Once a filter has been successfully saved, it can be accessed (along with other saved filters) or edited from the same ellipsis menu.
Coverage
Once the feature has been enabled and a scope has been applied, InsightCloudSec will begin reporting on the assessment coverage for the scoped cloud accounts. Click the Coverage graph to open the Assessment Coverage window, which shows a detailed report, including progress summary and assessment errors for the InsightCloudSec organization grouped by cloud account.
Additional Settings
These additional settings are for GCP only. By default, the GCP snapshot export job will use the default Compute Engine service account and the default VPC network to run the export. If the defaults are not sufficient, you can configure each of these from the Vulnerability Settings page.
To edit GCP Snapshot Export settings:
- Login to InsightCloudSec and navigate to the Vulnerabilities page.
- In the top right corner, click Settings.
- Next to the relevant GCP cloud account, click Edit.
- Update the export_network and export_service_account fields as desired.
- Click Apply.
Downloading Assessment History
Click the Download Assessment History button to download all Host-related assessment history.
Collection & Assessment Workflows
The following workflows gather and store the inventory from the host instances harvested by InsightCloudSec and assess them for vulnerabilities. They also continuously monitor and refresh the inventory and vulnerability data based on changes to the instances and for newly disclosed vulnerabilities.
Collection & Assessment Workflow (New Instance)
As InsightCloudSec harvesting discovers new host instances, HVA triggers the collection step, which creates and downloads a snapshot of the instance from a customer’s cloud account to InsightCloudSec. When HVA is initialized, all host instances already harvested are treated as new, triggering the first collection.
EBS root volume
If the EBS root volume is >= 100 Gb (AWS default is 8 Gb), InsightCloudSec will not download or assess it due to size limitations.
The snapshot is then assessed for vulnerabilities in InsightCloudSec and its inventory (versions of the operating system and software packages, OSS dependencies, and other select file types) is saved. InsightCloudSec discards the snapshot once the assessment is complete.
Recollection & Reassessment Workflow (Existing Instance)
Host instances are reassessed and potentially recollected based on the following triggers.
-
Automated recollection - a proprietary algorithm determines the need to collect a new snapshot using environmental events indicating the instance changed since the last collection
-
Automated reassessment - when new vulnerabilities are reported, InsightCloudSec reviews the host instance inventory and reassesses those with the imaged packages.
-
Manual recollection and reassessment - you can trigger a recollection and reassessment of a specific host instance using an action in the InsightCloudSec console or an API call
Workflow Diagram (Trigger-Based Collection & Assessment)
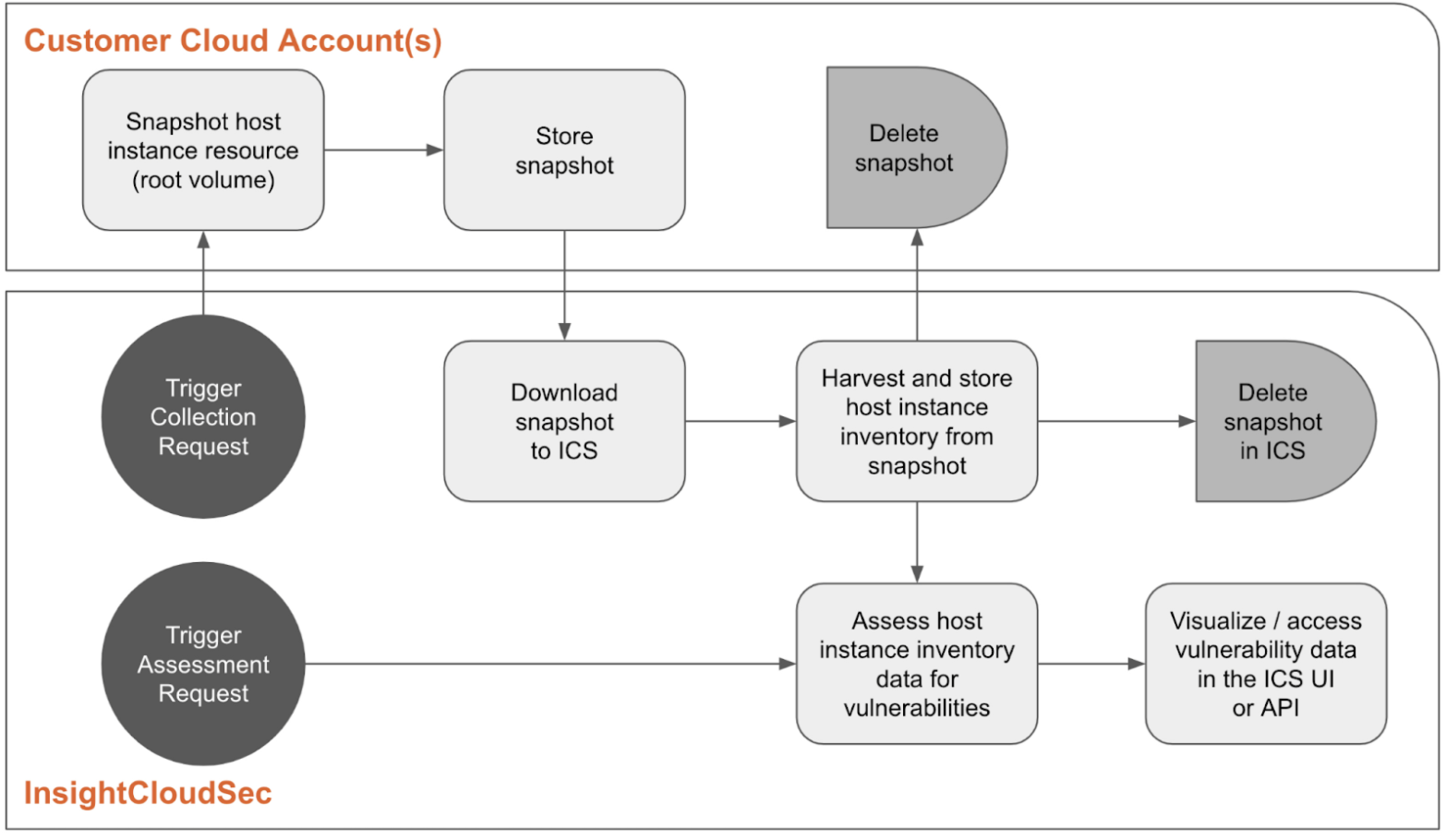
Triggering a collection starts the snapshot and is immediately followed by an assessment. This process can be tracked on the Host Assessment progress page.
- The timing to complete the process depends on the size of the image and can take from 5 minutes to 20 minutes.
- Once the Assessment is complete, results are immediately available.