Detection Rules
Detection rules are the logic SIEM (InsightIDR) uses to detect on suspicious attacker behaviors and user behaviors in your environment. When the conditions of a rule have been satisfied, a detection occurs.
The SIEM (InsightIDR) Detection Rules page allows you to modify detection rules, modify legacy detection rules, create basic detection rules, subscribe or contribute to Community Threats, and gain a deeper understanding of the detection rules SIEM (InsightIDR) uses to create investigations and track notable events.
We've made some detection terminology updates
As of November 2023, we’ve updated the tab names within our Detection Rules experience to better reflect the breadth of rules available:
- The Attacker Behavior Analytics tab is now called Detection Rule Library.
- The User Behavior Analytics tab is now called Legacy UBA Detection Rules.
These changes make way for our teams to migrate all legacy User Behavior Analytics rules to the Detection Library tab to create a singular Detection Rules experience. For more information, read Legacy Detection Rules.
Explore the Detection Rule Library
You can view all of the built-in detection rules and the number of detections over the last 30 days in the Detection Rule Library tab. You can also view details specific to each rule including:
View and manage your detection rules using the filter, sort, and search functionalities.
View rule overview and context
You can click on any detection rule in the Detection Rule Library tab to view an overview of the rule, including:
- Rule Action and Rule Priority: Read more about changing these settings.
- Rule metrics: These metrics show you how often your rule is generating detections, how many exceptions and automations are attached to the rule, and when the rule was added to the library, last detected, and last modified.
- Event Type: The Event Type is the data structure that defines the data contained in an event. When event data comes into the SIEM (InsightIDR) system as logs, (such as from the Collector, event sources, sensors, or Rapid7 Agent (Insight Agent)) the application classes that event data as a particular type.
- Rule sets: Rule sets group rules together by common characteristics such as by threat group, or by third-party provider.
- Recommendation: The recommendation provides steps for remediation in the case that the rule detects malicious activity.
- Threshold and keys that the rule matches on: These conditions refine the rule logic to define when a match will generate a detection and cause the rule action to occur.
- Threshold: The Threshold determines when the rule will generate a detection based on the number of matches that occur within the given time range. A Threshold can also prevent additional detections from being generated once a maximum number of matches has been reached.
- Group matches by these keys: The rule will group data containing the specified keys together and only detect on events that occur within these groups.
- Match only on unique values for this key: The rule will only detect on events that contain unique values for this key.
- Rule Context: The Rule Context provides a description of the associated threat group and shows other detection rules associated with this group.
What is a match?
When the logic of your rule matches content in your environment, a match occurs. A match will generate a detection if it meets the criteria set by the threshold and the matching keys.
View Rule logic
Click into any detection rule on the Detection Rule Library page and navigate to the Rule Logic tab to see the rule logic written in our SQL-style search language, Log Entry Query Language (LEQL). The rule logic query exposes what the detection rule searches for, giving you enhanced visibility into how SIEM (InsightIDR) generates a detection.
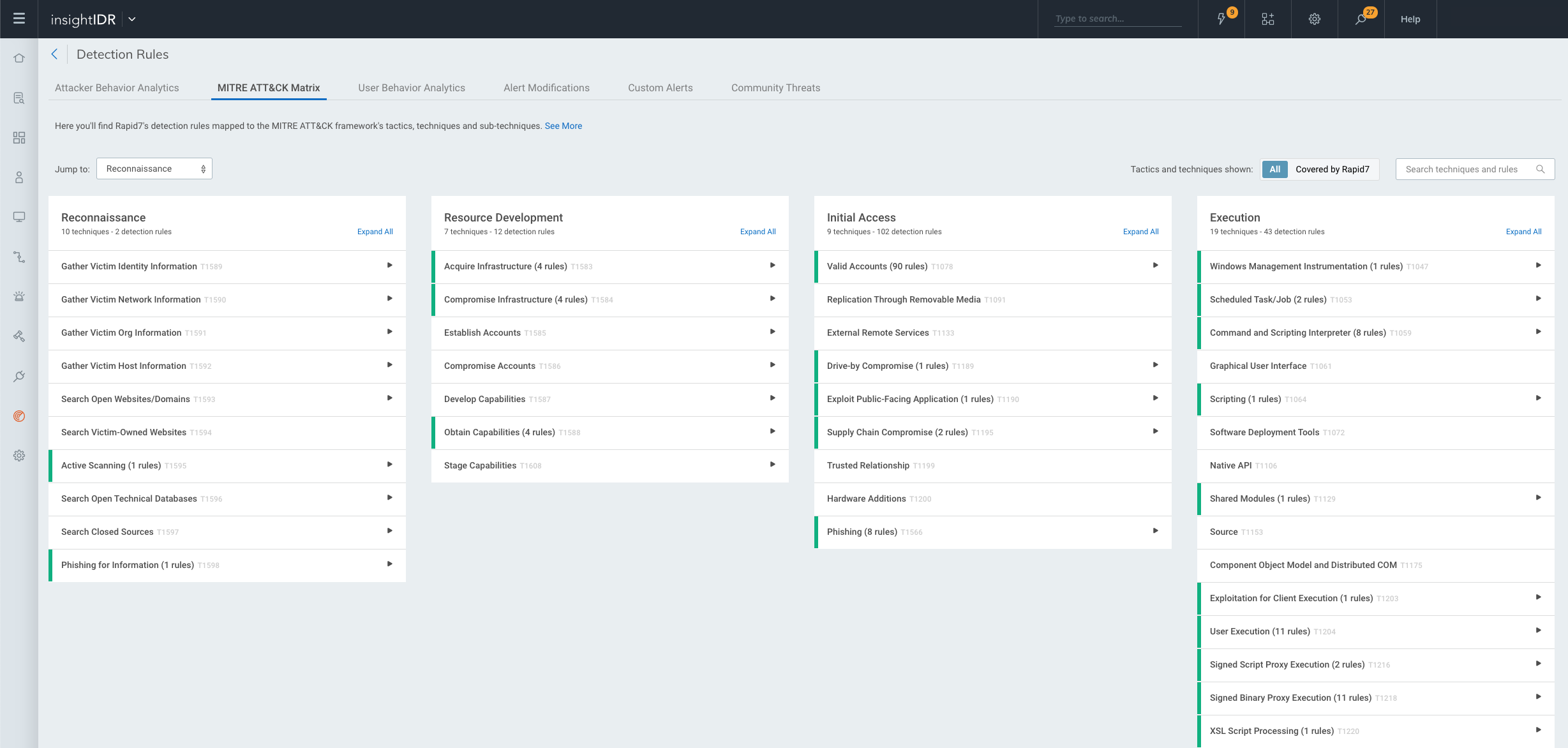
View MITRE ATT&CK mapping
The MITRE ATT&CK framework is a knowledge base created by MITRE to document tactics and techniques based on real-world observations. The framework offers a blueprint for teams on where to focus their detection efforts by identifying where threats fall within the attack chain. For more information about the MITRE ATT&CK framework, visit: https://attack.mitre.org .
Rapid7 detection rules are mapped to MITRE ATT&CK tactics and technique. Click into a detection rule to view the associated MITRE ATT&CK mapping.
You can also find a detailed view of all MITRE ATT&CK tactics and techniques on the MITRE ATT&CK Matrix tab. Click into a technique or subtechnique to see a description and mitigations recommended by MITRE. Techniques and sub-techniques that are covered by Rapid7 detection rules are indicated by a green bar, and expand to show associated rules. Use the Tactics & Techniques shown toggle to view the entire MITRE ATT&CK framework, or only tactics & techniques covered by Rapid7.
Filter detection rules
The filter panel provides many options to narrow down your detection rules.
You can click the radio buttons to show either Log and Process Rules, or Network Sensor Rules.
- Log and Process Rules leverage a wide variety of internal and external threat intelligence, and source data from endpoints and logs. You can view rule logic, related Threat Groups and MITRE ATT&CK mapping, and sort, filter and search these detection rules.
- Network Sensor Rules use network traffic as a source. These rules run locally on the Rapid7 Network Sensor (Insight Network Sensor) and require access to network packets. You can view the rule logic, and sort, filter and search these detection rules.
You can also filter detection rules by date modified, date added, number of exceptions, number of detections, Rule Action, Threat, and MITRE ATT&CK coverage.
Sort detection rules
Sort detection rules by using the up and down arrows in the table header. You can also click the toggle to group rules by Threat, or view rules ungrouped.
Search
You can use the search bar to search through detection rules and threats for specific malicious actions and behaviors.
For example, if you believe that you are vulnerable through SSH, you can use SIEM (InsightIDR) to search for attacker behavior that might be utilized against you.
Legacy detection rules
Migrate to new detection rules for better coverage
Legacy detection rules will be retired on November 30, 2026. To ensure complete coverage and access to the latest detection capabilities, begin migrating to the new rules now in the Detection Rule Library by following the steps in Migrate Legacy Detection Rules . If you have any questions, reach out to your Cybersecurity Advisor or Account Team.
Legacy detection rules run on SIEM (InsightIDR)‘s legacy User Behavior Analytics (UBA) engine. These detections apply insight to the millions of network events your users generate every day to detect compromised credentials, lateral movement, and other malicious behavior. View legacy detection rules in the Legacy UBA Detection Rules tab.