Honey users
When an attacker gets into a network, they may try to break into user accounts, especially those that have a description that implies they are important. Attackers frequently attempt to authenticate to as many user accounts as possible during an attack. This helps them expand their footprint and gain access to more assets and privileges without tripping any traditional alarms.
With SIEM (InsightIDR), you can create fake user accounts that look exciting to an attacker within the Active Directory. If any attempt is made to log in using this account, SIEM (InsightIDR) will fire a detection.
These types of user accounts are called honey users. Honey users are a unique way to detect attacker activity. If someone attempts to log in to a honey user account, SIEM (InsightIDR) generates a Honey User Authentication incident, which displays the time at which the attempt was made and the asset that was targeted. Though a honey user should look like a real and vulnerable user, a honey user is a fake user that is not associated with a real person within the organization and should never be accessed.
Honey users must be created following the specific instructions associated with each detection that you want to enable for your organization. This will require you to set up a Generic Windows Event Log to ingest different event codes from the raw logs in Log Search.
Legacy UBA Detection Rules
Before you begin
Before creating a honey user, note the following:
- After you create a honey user, the Collector must make an LDAP pull in order for the honey user to appear. This may take a day or more.
- In order to see honey user attempts or honey user evidence, you must have an Active Directory event source configured to pull security event logs from the Domain Controllers in your environment.
Create a honey user
To create a honey user:
-
Create a new user in Active Directory with a believable name, but do not allow anyone access to the account. This will be your new honey user.
-
Give the honey user every appearance of a normal employee of the company. This includes things like a complex passphrase of 35 characters, organizational mappings, permissions, or whatever else may trick an attacker into believing the user is an actual employee.
Remember that honey users may have multiple accounts. In fact, multiple accounts can increase the likelihood that an attacker will target the user, as it seems more authentic and provides additional chances for reaching an administrative role.
-
Log in to your account in SIEM (InsightIDR). Go to Settings > Deception Technology, and click the Honey Users tab.
-
Enter the newly created honey user’s name in the search bar on the page (not the global search bar).
-
Select the name to mark the user as a honey user.
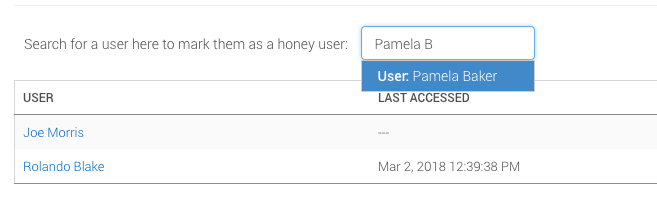
LDAP makes honey users available in SIEM (InsightIDR)
In order for the honey users to appear when you search for them, the Collector needs to make an LDAP pull after you create the honey users.
Therefore, you may need to wait a day or so after creating the honey users in Active Directory before you can configure them in SIEM (InsightIDR).
Test a honey user
Any attempt to authenticate with a honey user will trigger a detection. The easiest way to test the honey user is to use a tool like Microsoft Remote Desktop.
First, attempt to log into the Windows domain with the honey user account.
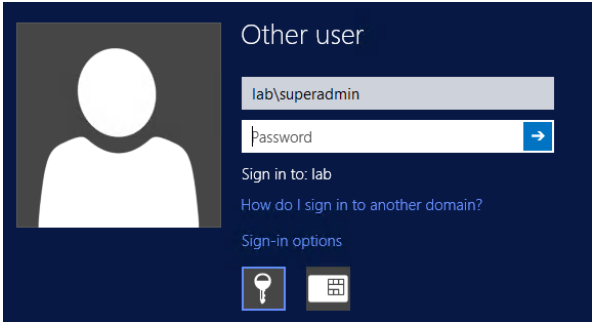
After attempting to authenticate with the honey user, wait a few minutes and then navigate to Investigations in SIEM (InsightIDR) to verify that an investigation was created for a Honey User Authentication detection rule.
Detection Rule Library (MDR Customers Only)
Before you begin
- Ensure that you have set up the Microsoft Active Directory Security Logs event source and that your Active Directory audit policy is set to capture the following Windows event codes:
4662,4768,4769. - Select the Send Unparsed Data check box for each of your Microsoft Active Directory Security Logs event sources to send raw logs to Log Search.
- Make the honey accounts look as realistic as your other Active Directory objects. The naming convention of honey objects should match the normal Active Directory accounts.
Attacker Technique - Honey SPN Kerberos Ticket Requested
This account must have a very strong password
To prevent attempts at cracking the Kerberos ticket by attackers, set up a strong password of at least 35 characters.
To create a honey SPN user:
-
Create a new user in the Domain Controller’s Active Directory Users and Computer Microsoft Management Console with a believable name, but do not allow anyone access to the account. This will be your new honey user.
Give the honey user every appearance of a normal employee of the company. This includes things like a complex passphrase of 35 characters, organizational mappings, permissions, or whatever else may trick an attacker into believing the user is an actual employee.
Remember that honey users may have multiple accounts. In fact, multiple accounts can increase the likelihood that an attacker will target the user, as it seems more authentic and provides additional chances for reaching an administrative role.
-
Go to the Attribute Editor tab in the user’s properties and set the servicePrincipalName to any string e.g.
ldap/dc. -
Add the honey user’s
SamAccountNameorUser Logon Nameto the exception field of the detection rule:
where(
NOT
source_json.insertionStrings.2,
service_name,
destination_account
= NOCASE("<honey user>")
)Make note of the honey user’s SamAccountName or User Logon Name and send it to your Cybersecurity Advisor. They’ll add the exception on your behalf.
Attacker Techniques - AD Honey User Access Triggered and AS-REP Roasting Attack Triggering on Honey User
To create a honey user:
- Select Action > New > User in the Active Directory Users and Computers Microsoft Management Console.
- Enter believable information in the First, Last, and User logon name fields.
- Create a complex password of at least 35-characters and click Finish.
- Go to Account tab in the user’s properties.
- Select Do not require Kerberos preauthentication under Account Options.
- Go to Security tab and click Advanced.
- Add a new Principal Everyone under the Auditing tab.
- Select This object only under the Applies to dropdown.
- Deselect all main permissions.
- Select Read all properties and Read permissions.
- Click OK.
- Go to the Organization tab and add details to the common attributes of the object to mimic other Active Directory users.
- Run the following PowerShell command to acquire the
SamAccountNameandObjectGUID:
Get-ADUser "<HoneyUser>" | Select SamAccountName, ObjectGUIDMake note of the honey user’s SamAccountName and ObjectGUID and send them to your Cybersecurity Advisor. They’ll add the exception on your behalf.
- In the Detection Library, add an exception for Attacker Technique - AD Honey User Access Triggered. Note that this detection rule is designed to ignore all events except the values in the exception field:
where(
NOT
ObjectName,
object_name
ICONTAINS "{ObjectGUID of Honey User Account}"
)- Then, add an exception for Attacker Technique - AS-REP Roasting Attack Triggering on Honey User. Note that this detection rule is designed to ignore all events except the values in the exception field:
where(
NOT
TargetUserName,
target_user_name
= "{honeyuser SamAccountName}"
)Attacker Technique - AD Honey Computer Account Access Triggered
To create a honey computer object:
- Select Action > New > Computer in the Active Directory Users and Computers Microsoft Management Console.
- Enter a Computer Name that follows your organization’s Computer Name patterns and click OK.
- Go to Security tab and click Advanced.
- Add a new Principal Everyone under the Auditing tab.
- Select All in the Type dropdown.
- Select This object only in the Applies to dropdown.
- Deselect all main permissions.
- Select Read all properties and Read permissions.
- Click OK.
- Run the following PowerShell command to acquire the
SamAccountNameandObjectGUID:
Get-ADComputer "{HoneyComputer}" | Select SamAccountName, ObjectGUID- In the Detection Library, add an exception for Attacker Technique - AD Honey Computer Account Access Triggered. Note that this detection rule is designed to ignore all events except the values in the exception field:
where(
NOT
ObjectName,
object_name
ICONTAINS "{ObjectGUID of Honey Computer Account}"
)Make note of the honey computer’s ObjectGUID and send it to your Cybersecurity Advisor. They’ll add the exception on your behalf.