Honeypot
A honeypot is an asset designed to capture information about access and exploitation attempts. Honeypots are the most commonly used intruder trap in the security industry, as they have been traditionally used on the open Internet to capture public-facing attacker behavior.
In today’s world, there is so much activity, scanning, and exploitation attempts on the open Internet that it takes a research team to understand all of the data a public-facing honeypot can capture. For instance, see Rapid7’s Project Lorelei Cloud .
Rapid7 Honeypots
A honeypot is a virtual server that you can deploy on your network from SIEM (InsightIDR). Honeypots can look like any other machine on the network, or they can be deployed to look like something an attacker could target. You can have a single honeypot or multiple honeypots, and you can deploy them straight out of SIEM (InsightIDR).
How Do They Work?
Honeypots lie in wait for “attacker” events to happen, such as a port scan or attempted user authentication, which immediately sets off an alarm. If you deploy the Rapid7 Honeypot and enable the associated detection rules in SIEM (InsightIDR), you will be notified if such activity occurs. Once attackers find an initial foothold in a network, their next step is typically a network scan to identify all the other assets in the network.
OVA Appliance
SIEM (InsightIDR)‘s Honeypot is an OVA appliance designed for deployment in VMware environments. The honeypot can detect network reconnaissance, typically in the form of suspicious network and/or port scanning.
The Honeypot OVA contains an appliance that is able to listen on all ports.
All scanning or connection attempts are allowed. Each time a connection is attempted, the honeypot captures information about the source asset (and potentially user) associated with the connection. This data is immediately pushed up to the Insight platform, generating a Honeypot Access Alert.
Any connection to the honeypot will trigger an incident.
Limit user access to honeypots.
System Requirements
See System Requirements for specific information.
Download Honeypot
Time synchronization
Rapid7 uses Ubuntu’s default NTP configuration (and NTP pool) for your honeypot virtual servers.
- From your SIEM (InsightIDR) homepage, select Data Collection on the left menu. Then, select Setup Honeypot in the top right corner and select Download Honeypot. The Honeypot OVA download will begin automatically.
- In your VMware environment, create a new Virtual Machine (VM) from the OVA. Power on the VM. You will see this prompt:
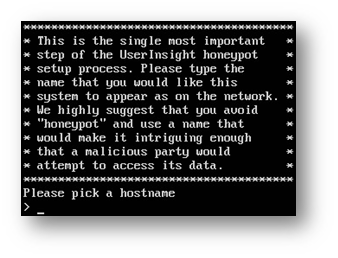
The following message is normal and can be ignored. If it appears, wait for the virtual machine to continue booting.

- Provide a name that fits your network naming convention and makes the machine look important. Be sure to use a fully qualified name, like core-dc.company.com. Otherwise, the honeypot will generate an error that it needs a FQDN.
- Follow the prompts to configure a dynamic or static IP, and/or web proxy for communication purposes.

- Continue until you see the following:
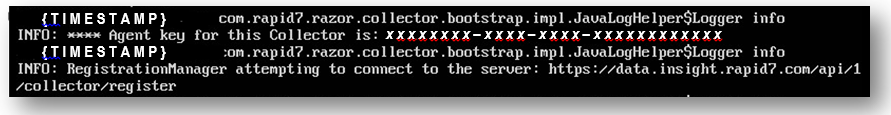
- Take note of the Agent key (xxxxxxxx-xxxx-xxxx-xxxxxxxxxxxx) that is displayed.
- To activate the honeypot in the SIEM (InsightIDR) interface, navigate to Data Collection > Setup Honeypot > Activate Honeypot.
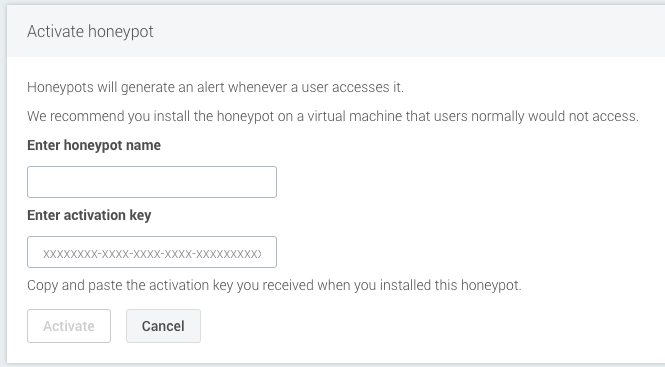
- Fill out the form and click Activate. The collector name is how the collector will be displayed in SIEM (InsightIDR) and does not need to match the actual name used to configure the honeypot. However, the Activation Key must match exactly.
Please note that a new Activation Key will be generated on the honeypot every time it is booted until you actually activate it.
- Once you successfully pair the honeypot with SIEM (InsightIDR), you will receive automated detections for any connection attempts to the honeypot.
- After clicking Activate, you will see a loading page while the honeypot completes the activation process. This may take up to ten minutes to complete.
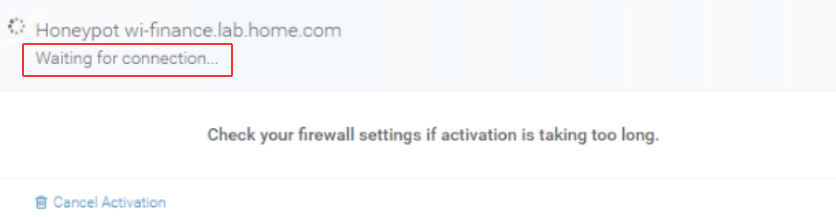
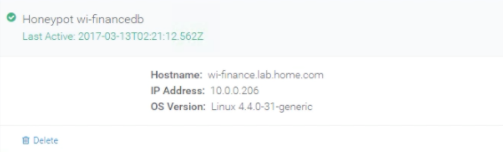
- When you see a “last active” message on the honeypot, the configuration process is complete.
Activation is Taking Too Long
If you have waited over ten minutes and activation still is not complete, something is wrong. Check the log file on the honeypot screen for errors.
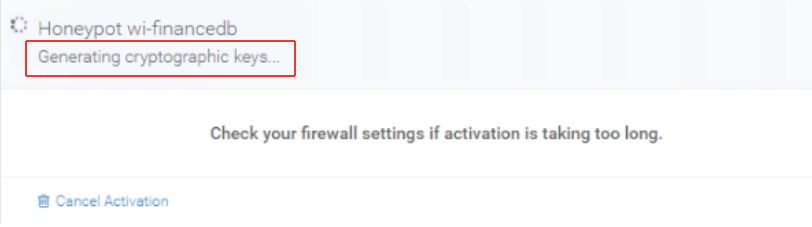
You may have entered in the Activation Key incorrectly, so you may want to select Cancel Activation and try again.
Reinstallation required after configuration change
If you cancel activation or delete the honeypot configuration, you’ll need to reinstall the honeypot to generate a new key, as the original key will no longer be valid.
Ensure Honeypot Detection Rules have a Rule Action
To generate alerts or investigations when an intruder accesses a honeypot, make sure honeypot detection rules have a rule action applied.
- Go to Detection Rules > Detection Rule library.
- In the Search rules field, enter ‘Honeypot’.
- Check the Rule Action field next to
User Behavior - Honeypot Access (Unknown Asset)andUser Behavior - Honeypot Access. If the rule action is Off, click the dropdown and select the appropriate action to apply.
To learn more about the rule action options, read Modify detection rules .
Test the Honeypot
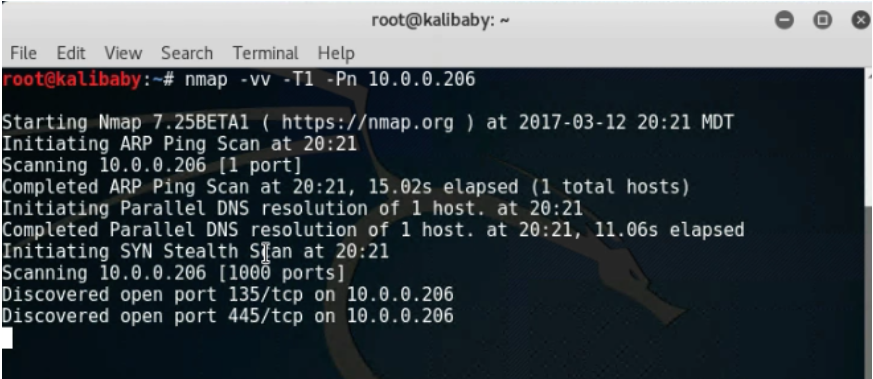
Any access to the honeypot will trigger a detection. A common way to test the honeypot is to run an nmap scan, mimicking intruder behavior.
You could run a standard discovery scan, a vulnerability scan, throw exploits, or attempt to bruteforce the honeypot to trigger an incident. These are all common techniques during the reconnaissance and enumeration phase of the attacker’s kill chain.
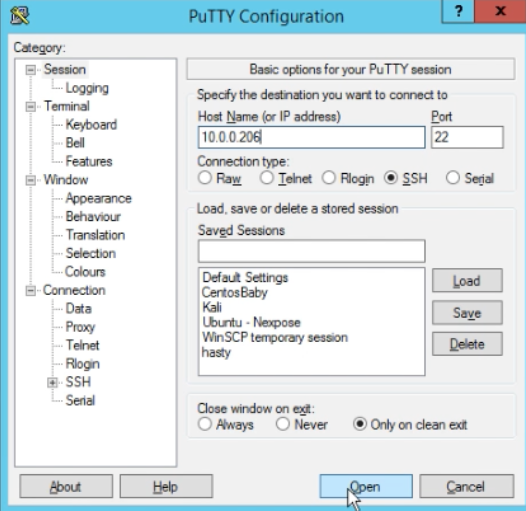
Alternatively, you might use a tool like Putty to attempt to access the honeypot.
After attempting to access the honeypot, wait a few minutes and then verify that the rule action that you previously configured for the honeypot detection rules took place (for example, was an alert triggered, was an investigation created, etc.).