Vulnerability Management (InsightVM) Technology Add-On for Splunk
The Vulnerability Management (InsightVM) Technology Add-On for Splunk allows you to import Vulnerability Management (InsightVM) asset and vulnerability data into your Splunk environment and view that data with the companion Vulnerability Management (InsightVM) Dashboard . For Vulnerability Management (InsightVM) customers, these new Splunk import and visualization tools functionally replace the older Nexpose Technology Add-On and Nexpose Dashboard .
Not available in InsightGovCloud
This feature is not available for InsightGovCloud customers.
The new Vulnerability Management (InsightVM) edition of this add-on differs from its predecessor in the following ways:
| Vulnerability Management (InsightVM) Technology Add-On for Splunk | Nexpose Technology Add-On for Splunk | |
|---|---|---|
| Leverages the Rapid7 Insight Cloud to pull asset and vulnerability data | Yes, the Vulnerability Management (InsightVM) add-on pulls data from the Insight Cloud and does not impact the on-premises Security Console. | No, the Nexpose add-on pulls all data from the Security Console using SQL reports. |
| Includes Site, Tag, and Asset Group details for imported Assets | Yes, the asset import will include Sites and Tags; however, Asset Groups are not currently included. Any sites included with an asset will show up under the tags key. | No, the Nexpose add-on only includes a list of tag names for imported assets. |
| Only imports new data as inputs are run | Yes, the Vulnerability Management (InsightVM) add-on only imports the assets and vulnerabilities of recently scanned devices each time the input is run. This reduces the amount of data stored in Splunk and makes that data more actionable. | The Nexpose add-on imports data based on any new scans identified for the sites in scope. Since all vulnerabilities are imported for the assets identified in new sites, there is no way to distinguish between a new, existing, or remediated vulnerability. |
| Provides the ability to filter assets and vulnerabilities within scope | Yes, the Vulnerability Management (InsightVM) add-on features the same asset and vulnerability filters available with the Query Builder and can define them with input configurations to reduce the scope of the data being imported. | It is possible to filter by site IDs with the Nexpose add-on, but no other filtering is supported. |
| Imports historical data when run for the first time | Yes. All subsequent imports only include data from assets and vulnerabilities that have been scanned since. | Yes. |
| Vulnerability finding imports include remediation status on a device | Yes, the Vulnerability Management (InsightVM) add-on imports vulnerabilitiy findings with a finding_status = remediated value as remediation takes place. All new vulnerability findings are defined with finding_status = new. | No. |
Installation
You can install the add-on as an app using the Splunk UI:
- From the Apps menu in Splunk, select Manage Apps.
- Select Browse More Apps.
- Search for the “Rapid7 Vulnerability Management (InsightVM) Technology Add-On”.
- Select Install from the app listing.
- When prompted, restart Splunk to finish.
Configuration
You must configure two components in the add-on before you can use it:
- The connection
- One or more inputs
Connection
The connection requires an API key for connecting to and retrieving data from InsightVM. The add-on allows you to create multiple connections if you want to use different connections across different inputs.
If you need to generate a new API key for a connection, follow these steps:
- Sign in to the Command Platform (Insight Platform).
- Select the gear icon in the top menu and click API Keys.
- Select Organization Key.
- Select + New Key.
- Enter a name for the key and click Generate.
- Copy and store the generated key in a secure location.
After you have an API key, follow these steps to configure the Vulnerability Management (InsightVM) connection in Splunk.
- Navigate to the Rapid7 Vulnerability Management (InsightVM) Technology Add-On available under the Apps menu in Splunk.
- Select Configuration.
- Select Add.
- Enter a name for the connection.
- Enter your region, which is a two-character string based on your location (such as
us).- Additional region information is available in the Supported Regions section of the Product APIs page.
- Enter your generated API key.
- Click Add.
Inputs
The add-on uses inputs to configure the import of asset and vulnerability data from InsightVM. These inputs allow you to further filter the data that Splunk retrieves and ingests.
There are two inputs available for configuration:
- Vulnerability Management (InsightVM) Asset Import - Imports asset and optional vulnerability finding data.
- Vulnerability Management (InsightVM) Vulnerability Definition Import - Imports vulnerability definitions.
To create a new input, navigate to the add-on menu and click Inputs > Create New Input and select the one you want to configure.
Vulnerability Management (InsightVM) Asset Import
Customizable fields for the Vulnerability Management (InsightVM) Asset Import input are as follows:
| Field | Description |
|---|---|
| Name | The name of the input as it will appear in Splunk. |
| Interval | The frequency in seconds that the add-on imports Vulnerability Management (InsightVM) data. The default (and recommended maximum) is once per hour. |
| Index | Your preferred Splunk index for data. The default is rapid7. Note that you must create a new rapid7 index in Splunk if you choose to use this one. |
| Vulnerability Management (InsightVM) Connection | The Vulnerability Management (InsightVM) connection, created per the previous instructions in the Connection section. |
| Asset Filter | A query for filtering assets that the add-on imports. |
| Import Vulnerabilities | If desired, this option allows the add-on to import vulnerability findings into Splunk in addition to assets. |
| Vulnerability Filter | A query for filtering vulnerability findings that the add-on imports. |
| Include same vulnerabilities | When both this option and Import Vulnerabilities are checked, the add-on will import, as new events, the vulnerabilities that have not changed status since the last time the import was executed. The additional vulnerabilities will have a more recent last_found date, but the total amount of data imported into Splunk will increase. |
Example asset filters
The following queries are examples of what you can set for the Asset Filter field:
- sites IN [`site-name]
- tags IN [
tag-name] - os_family =
Windows
Example vulnerability filters
In similar fashion, these queries are examples for the Vulnerability Filter field:
- cvss_v2_score > 6
- severity =
Critical
Vulnerability Management (InsightVM) Vulnerability Definition Import
The add-on uses this input to import vulnerability definitions from InsightVM. You can use this data to correlate with vulnerability findings (if you elect to import those) as well. Importing vulnerability definitions is not required for visualizing asset findings in your environment, but it does provide additional details about the vulnerabilities.
Only import vulnerability definitions if you need them
If vulnerability definition details are not necessary, we do not recommend that you enable this input as it will ingest a large amount of data each time the input is run. Some vulnerability definitions are so large it’s necessary to truncate the data. When truncation occurs on a String, an ellipsis (…) is inserted at the point of truncation. For a List, a limit of 75 items will apply.
Customizable fields for the Vulnerability Management (InsightVM) Vulnerability Definition Import input are as follows:
| Field | Description |
|---|---|
| Name | The name of the input as it will appear in Splunk. |
| Interval | The frequency in seconds that the add-on imports Vulnerability Management (InsightVM) data. The default (and recommended maximum) is once per day for this input. |
| Index | Your preferred Splunk index for data. The default is rapid7. Note that you must create a new rapid7 index in Splunk if you choose to use this one. |
| Vulnerability Management (InsightVM) Connection | The Vulnerability Management (InsightVM) connection, created per the previous instructions in the Connection section. |
| Vulnerability Filter | A query for filtering vulnerability definitions that the add-on imports. |
Imported Data
The following tables indicate imported data fields and contain example data for each.
Asset Sourcetype
| Field Name | Example Data |
|---|---|
| assessed_for_policies | false |
| assessed_for_vulnerabilities | true |
| credential_assessments | ”port”: 22 “protocol”: “TCP status”: “NO_CREDS_SUPPLIED” |
| critical_vulnerabilities | 5 |
| exploits | 12 |
| host_name | hostname-1 |
| id | 234574486-34a7-40a3-0923-28bd0b5cc90e-default-asset-100 |
| ip | 127.0.0.1 |
| last_scan_end | 2020-06-23T17:45:59.963Z |
| last_scan_start | 2020-06-23T16:38:00.963Z |
| mac | 00:1B:44:11:3A:B7 |
| malware_kits | 1 |
| moderate_vulnerabilities | 8 |
| os_description | Microsoft Windows Server 2008 R2, Enterprise Edition SP1 |
| os_family | Windows |
| os_name | Windows Server 2008 R2, Enterprise Edition |
| os_system_name | Microsoft Windows |
| os_type | General |
| os_vendor | Microsoft |
| os_version | SP1 |
| risk_score | 5000 |
| severe_vulnerabilities | 4 |
| tags | ”name”: “us-austin”, “type”: “SITE” |
| total_vulnerabilities | 17 |
Asset Vulnerability Finding Sourcetype
| Field Name | Example Data |
|---|---|
| first_found | 2020-04-15T02:38:41Z |
| last_found | 2020-06-23T20:40:51.981Z |
| port | 3389 |
| proof | Negotiated with the following insecure cipher suites:
|
| protocol | TCP |
| solution_fix | [Solution details] |
| solution_id | ssl-disable-rc4-ciphers |
| solution_summary | Disable TLS/SSL support for RC4 ciphers |
| solution_type | WORKAROUND |
| status | VULNERABLE_EXPL |
| vulnerability_id | rc4-cve-2013-2566 |
| finding_status | found |
| asset_id | 234574486-34a7-40a3-0923-28bd0b5cc90e-default-asset-100 |
| asset_hostname | hostname-1 |
| asset_ip | 127.0.0.1 |
Vulnerability Definition Sourcetype
| Field Name | Example Data |
|---|---|
| added | 2018-05-16T00:00:00Z |
| categories | 7-Zip,Remote Execution |
| cves | CVE-2016-2334 |
| cvss_v2_access_complexity | medium |
| cvss_v2_access_vector | network |
| cvss_v2_authentication | none |
| cvss_v2_availability_impact | complete |
| cvss_v2_confidentiality_impact | complete |
| cvss_v2_exploit_score | 8.5888 |
| cvss_v2_impact_score | 10.000845 |
| cvss_v2_integrity_impact | complete |
| cvss_v2_score | 9.3 |
| cvss_v2_vector | AV:N/AC:M/Au:N/C:C/I:C/A:C |
| cvss_v3_attack_complexity | low |
| cvss_v3_attack_vector | local |
| cvss_v3_availability_impact | high |
| cvss_v3_confidentiality_impact | high |
| cvss_v3_exploit_score | 1.8345766 |
| cvss_v3_impact_score | 5.873119 |
| cvss_v3_integrity_impact | high |
| cvss_v3_privileges_required | none |
| cvss_v3_scope | unchanged |
| cvss_v3_score | 7.8 |
| cvss_v3_user_interaction | required |
| cvss_v3_vector | CVSS:3.0/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H |
| denial_of_service | false |
| description | Heap-based buffer overflow in the NArchive::NHfs::CHandler::ExtractZlibFile method in 7zip before 16.00 and p7zip allows remote attackers to execute arbitrary code via a crafted HFS+ image. |
| id | 7-zip-cve-2016-2334 |
| links | [\n {\n "href": "http://www.securityfocus.com/bid/90531",\n "id": "90531",\n "rel": "advisory",\n "source": "bid"\n }\n] |
| modified | 2018-06-08T00:00:00Z |
| pci_cvss_score | 9.3 |
| pci_fail | true |
| pci_severity_score | 5 |
| pci_status | fail |
| published | 2016-12-13T00:00:00Z |
| references | bid:90531,cve:CVE-2016-2334,url:http://www.securitytracker.com/id/1035876 |
| risk_score | 598.07 |
| severity | critical |
| severity_score | 9 |
| title | 7-Zip: CVE-2016-2334: Heap-based buffer overflow vulnerability |
The Vulnerability Definition sourcetype is not currently used by the Vulnerability Management (InsightVM) Dashboard, but the imported data is made available to supplement the asset vulnerability findings imported with the Asset Import input.
Data duplication for vulnerability definitions
Note that Vulnerability Definitions do not change often. The resulting data that the add-on imports over time will likely produce duplicates.
Visualizing Data
The Vulnerability Management (InsightVM) Dashboard for Splunk serves as a starting point for visualizing data imported with the add-on. There are two dashboards included:
- The Vulnerability Management (InsightVM) Assets dashboard used for visualizing asset details
- The Vulnerability Management (InsightVM) Vulnerability Findings dashboard used for visualizing details of vulnerability instances found within assets.
The Rapid7 Vulnerability Management (InsightVM) Dashboard features several customization options and you can install it as an app in the same way as the add-on.
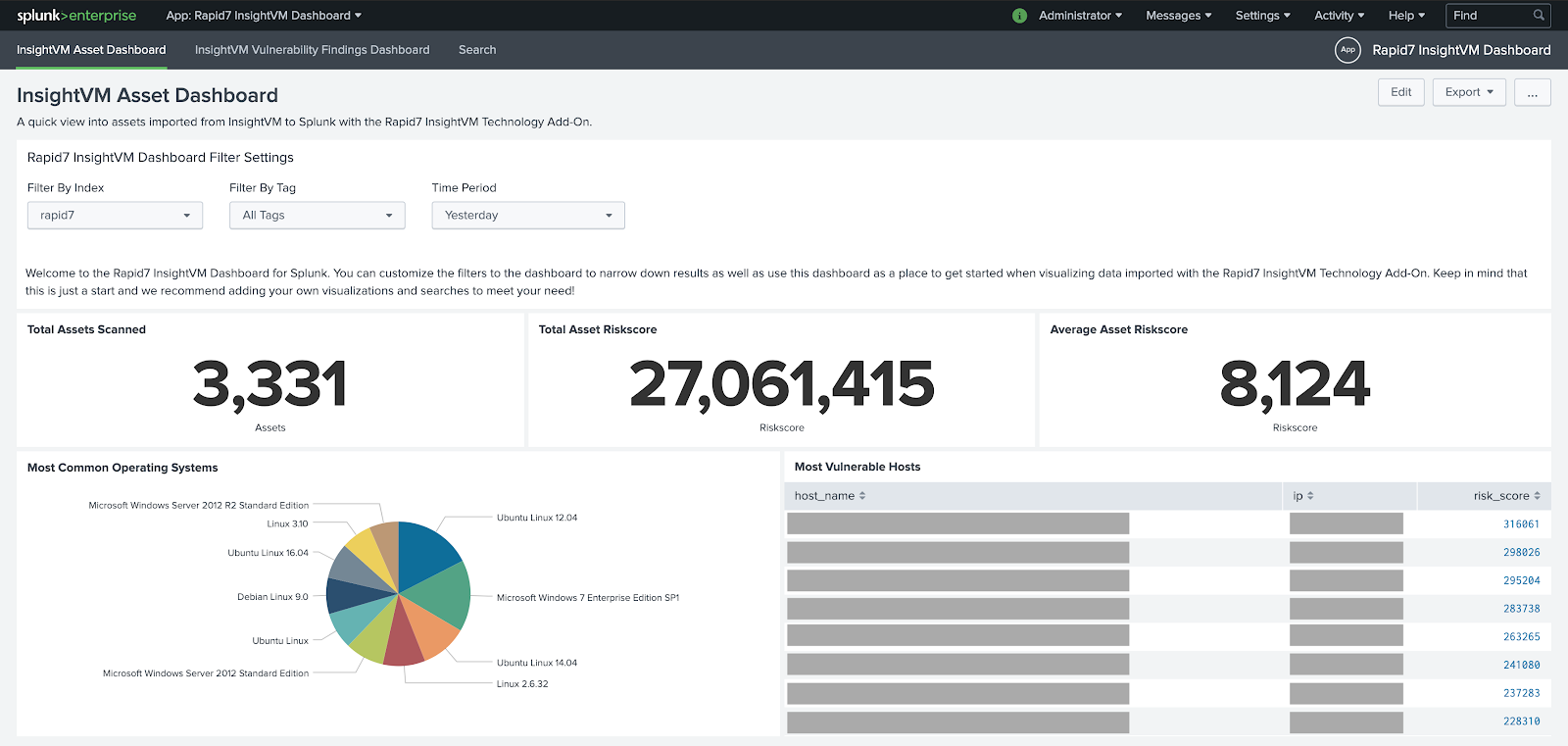
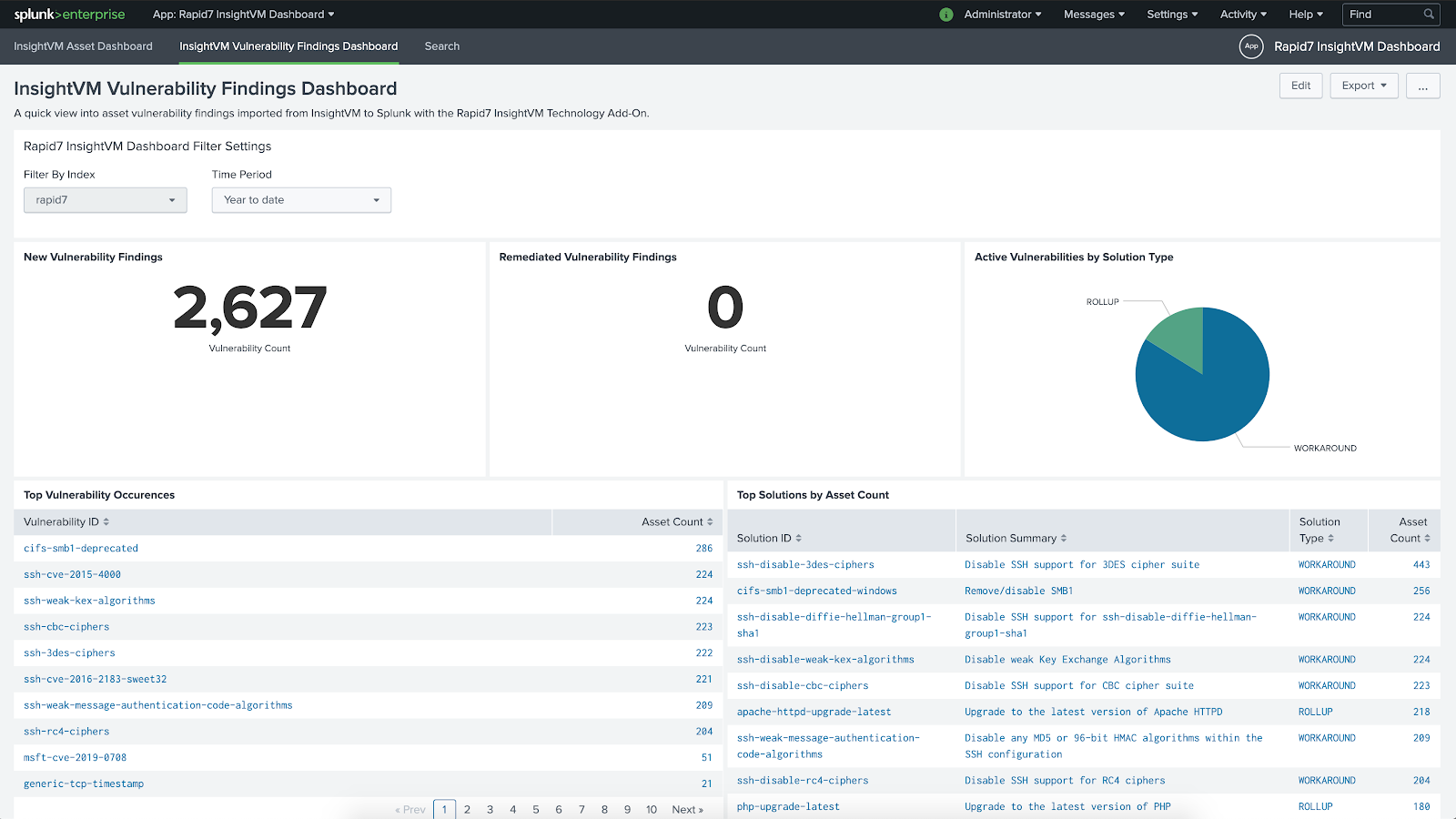
Index and time periods must be set
Note the selected index and time period in these dashboards. Data may not appear if these filter settings are not set correctly.
FAQs
Is there a migration path from the Nexpose Technology Add-On to this new Add-On for Vulnerability Management (InsightVM)?
No. Due to the differences in how each add-on retrieves data and the content that is stored, there is not a migration path from the legacy Nexpose Technology Add-On to the Vulnerability Management (InsightVM) Technology Add-On. However, both add-ons can be used at once so it is possible to continue using the Nexpose Technology Add-On until you are ready to fully disable it.
Why am I not seeing any data in my add-on/dashboard?
Check the selected index and time period for filtering data. These often need to be adjusted to filter correctly for assets and vulnerabilities. In addition, if the default rapid7 index was used for the inputs, make sure this index has already been created.
Does the Asset Import input import all assets each time it runs?
No. When the asset import is run for the very first time it will import all assets. After that, all subsequent imports will only pull in assets that have been newly scanned since the last import occurred.
Does the Vulnerability Definition Import input import all definitions each time it runs?
Yes, all vulnerability definitions will be imported each time it is run. For this reason, we recommend running this import at a maximum of once per day.
How do I know if a vulnerability is new as opposed to remediated?
Check the finding_status field of a vulnerability finding to determine whether it’s new, remediated, or unchanged. The new and remediated statuses indicate new and remediated vulnerabilities respectively, while the found status indicates a previously found, unchanged vulnerability finding.
Can I identify whether a vulnerability has been remediated?
Yes, all vulnerability findings will have a finding_status when the add-on imports them into Splunk. If a vulnerability is remediated, the add-on imports it as a new event with a finding_status of remediated.
Can the add-on import all data every time an input runs?
No, the add-on currently only imports data for assets that have been scanned since the last time the input ran. Internally, Rapid7 tracks the last time a job was successful and it only updates when no errors are received to avoid losing data that should be imported.
In the logs I can see one or more requests failed (such as a status 504), does this mean the import process will miss data?
Not all HTTP requests succeed. For this reason, when a request fails the application will retry making the request up to a maximum of 3 times. A delay is added in between each retry, and will increase in duration for subsequent retries. If the maximum number of retries has been reached and the request has not succeeded, the import will fail and start over next time the Data Input is executed.
If the issue is persistent, confirm that the cause is not due to a proxy or firewall rules. Otherwise, contact Rapid7 Support to ensure there is no service degradation.
Why are some of my vulnerability definition property values truncated?
Only the largest vulnerability definitions (not assets or vulnerability findings) are affected by this. Some vulnerability definitions are so large they may cause performance issues and require that some data is removed. Truncated strings will end with an ellipsis (…) and truncated lists will be capped at a length of 75.
I see truncation warnings in the splunkd.log, what does this mean?
The warnings may look similar to LineBreakingProcessor - Truncating line because limit of XXXXX bytes has been exceeded.
Splunk truncates events that are too large. This can result in data being excluded from the index. If these errors are present in the logs for rapid7:Vulnerability Management (InsightVM):asset or rapid7:Vulnerability Management (InsightVM):asset:vulnerability_finding data sourcetypes, then the TRUNCATE value for the relevant sourcetype should be increased in the Technology Add-On’s app.conf and a new initial import performed.
If I previously chose not to import vulnerability findings but I want to now, will my future runs import the missed vulnerabilities?
No, a new initial import will need to be performed to pick up vulnerability findings that were previously not imported.
If I suspect data has been missed during an import run, what can I do?
Ensure that you’re using the latest version of the add-on. Any data loss issues you are experiencing may be resolved by defect fixes that have been applied in subsequent versions. When upgrading to a newer version of the add-on, it may be necessary to clear the state data stored by the previous version since this could affect future imports. See the Upgrading section for more information.
Upgrading
You can upgrade the add-on by clicking the Update button from the Splunk App Browser page or Update Available from the App Management page. For additional information on the App update process for Splunk Cloud, refer to the Splunk documentation at https://docs.splunk.com/Documentation/AddOns/released/Overview/SplunkCloudinstall .
It’s not always necessary to perform a full import when upgrading, but if the upgrade is because data has been missed during a previous import then a full import should be performed using the latest version of the add-on. The add-on decides whether a full import or partial import ( a “partial import” refers to differences since last import) should be performed using state information it stores in Splunk’s KV store.
It’s important to note that performing a full import may result in a lot of duplicate data being indexed if a new index is not created or the existing index is not refreshed.
There are a number of ways to force a full import. Rapid7 recommends that you read through all the steps before starting the process.
Method 1: Creating a new add-on input
This will not remove any existing data or add-on configuration. Instead, a second add-on input is created. The state data stored in Splunk’s KV store is tied to the add-on input name, so creating an input with a different name means the add-on performs a full import when the new input is executed by Splunk.
- (Optional) Create a new index by going to Settings > Indexes > New. Enter a unique name that differs from the previous index name (such as
rapid7_new). - From the Splunk home page, select Rapid7 Vulnerability Management (InsightVM) from the Apps menu.
- Select Create New Input and enter a unique name that is different from the name chosen during the original input creation.
- Make sure to select the appropriate index.
- An initial import will be performed the next time the import executes. This may result in a lot of duplicate data being indexed if a new index was not created. Consider disabling the original input to mitigate this condition.
Method 2: Manually deleting the state data
This will remove the existing state data which may not be recovered. As previously mentioned, the name of the state data is tied to the name of the input.
- Find the name of the input by clicking on the Rapid7 Vulnerability Management (InsightVM) Splunk App and noting the name of the input, for example “asset_import”. This is the
{{input_name}}used during step 3 below. - (Optional) View the values of all state data by sending a
GETrequest to{{splunkdProtocol}}://{{splunkHost}}:{{splunkdPort}}/servicesNS/nobody/TA-rapid7-insightvm/storage/collections/data/TA_rapid7_insightvm_checkpointer. Don’t forget to replace the placeholders with values appropriate for your environment, for examplehttps://localhost:8090/servicesNS/nobody/TA-rapid7-insightvm/storage/collections/data/TA_rapid7_insightvm_checkpointer. Headers that should be included on the request areContent-Type: application/jsonandAuthorization: {{Basic Auth}}. The basic authorization uses the Splunk username/password. - Send
DELETErequests to remove data for the chosen input. Don’t forget to replace the placeholders with values appropriate for your environment. Headers that should be included on the request areContent-Type: application/jsonandAuthorization: {{Basic Auth}}. The basic authorization uses the Splunk username/password.{{splunkdProtocol}}://{{splunkHost}}:{{splunkdPort}}/servicesNS/nobody/TA-rapid7-insightvm/storage/collections/data/TA_rapid7_insightvm_checkpointer/{{input_name}}-last_import_time{{splunkdProtocol}}://{{splunkHost}}:{{splunkdPort}}/servicesNS/nobody/TA-rapid7-insightvm/storage/collections/data/TA_rapid7_insightvm_checkpointer/{{input_name}}-last_assessed_time
- An initial import will be performed the next time the import executes.
Troubleshooting
Three log files are available to help debug issues, usually located at <splunk_home>/var/log/splunk/:
splunkd.log- Splunk general logta_rapid7_insightvm_insightvm_asset_import.log- Log for the Vulnerability Management (InsightVM) Asset Import inputta_rapid7_insightvm_insightvm_vulnerability_definition_import.log- Log for the Vulnerability Management (InsightVM) Vulnerability Definition Import input