Oct 15, 2018
Our first release of the Fall introduces three new compliance packs, expanded Microsoft Azure, Google Cloud Platform and Amazon Web Services support and introduces a new Event Driven Harvesting (EDH) model which improves detection and remediation times, as well as provides additional context on lifecycle actions and changes to cloud footprints.
To see comparisons of what has changed in 18.6, please see What’s New. Upgrade Prerequisites Before upgrading your DivvyCloud installation, please take a moment to view our Administrator and Developer Notes at the bottom of this page, or contact support@divvycloud.com for questions. Release Highlights
Additional Cloud Support/Enhancements
Amazon Web Services
- Support for Simple Notification Service (SNS)
- Support for Simple Email Service (SES)
- Support for CloudFront
- Support for visibility into GuardDuty
- Support for visibility into Lambda account limits
- Store the boolean property for automatic minor upgrades for RDS instances
- Store and surface the VPC ID that’s associated with an Elasticache cluster
- Support for harvesting of IAM SAML providers
- Ability to view and modify IAM Role assume role policies
- Visibility into cross account private images
Google Cloud Platform
- Support for Pub/Sub
- Support for Service Account Keys
- Support for tracking VPC flow logging and Google Private Access at the subnet level
- Support for identifying legacy networks
- Support for KMS
- Enhanced GKE visibility and configuration checks
- Enhanced visibility into GCP Storage buckets
Microsoft Azure
- Support for Azure Kubernetes Service (AKS)
- Support for CosmosDB
- Support for Databases
- Support for File Storage
- Support for IAM
- Support for HDInsight
- Support for Network Peers
- Visibility into network limits/usage
- Support for using certificate credentials for subscription authentication
Kubernetes
- Support for proxy servers
New Compliance Packs
CSA CCM
The Cloud Security Alliance maintains an industry standard matrix known as the Cloud Compliance Matrix (CCM). This framework contains controls to harden and secure cloud technology and aligns them against other security regimes such as NIST-800.53, HIPAA and ISO 27001. With 18.6, this compliance standard is now supported within the product.
CIS Benchmarks for GCP
In early September, the Center for Internet Security (CIS) published a new benchmark for security cloud workloads on Google Cloud Platform (GCP). This benchmark contains dozens of security recommendations across Identity & Access Management, Logging/Monitoring, Networking, Storage, Compute and Kubernetes.
CIS Benchmarks for Azure
With release 18.5, we first introduced support for the CIS Benchmarks for Azure, and with 18.6 we’ve added over 25 new Insights and checks against this compliance framework.
Event-Driven Harvesting
Event-driven Harvesting (EDH) is a more intelligent and scalable approach to data collection that is being introduced with this release in Beta and, by default, disabled. Customers can enable EDH if they are are interested in test driving functionality and providing feedback. General Availability is expected in 18.7.
EDH allows customers to get near real-time visibility into changes. As an example, if a user makes a change to the access control list of an S3 bucket, EDH will detect the change within 90 seconds, log the change, and trigger the appropriate automation Bots to remediate the event. More information on EDH can be found under AWS Cloud Support .
Cloud Compliance
The Cloud Compliance view enables users to get quick visibility into how they stand for one or more compliance frameworks. It provides a top level view into the number of failed checks based on the selected compliance pack criteria. Badges can be leverage to tailor the view to specific risk profiles, environments, owners and more.
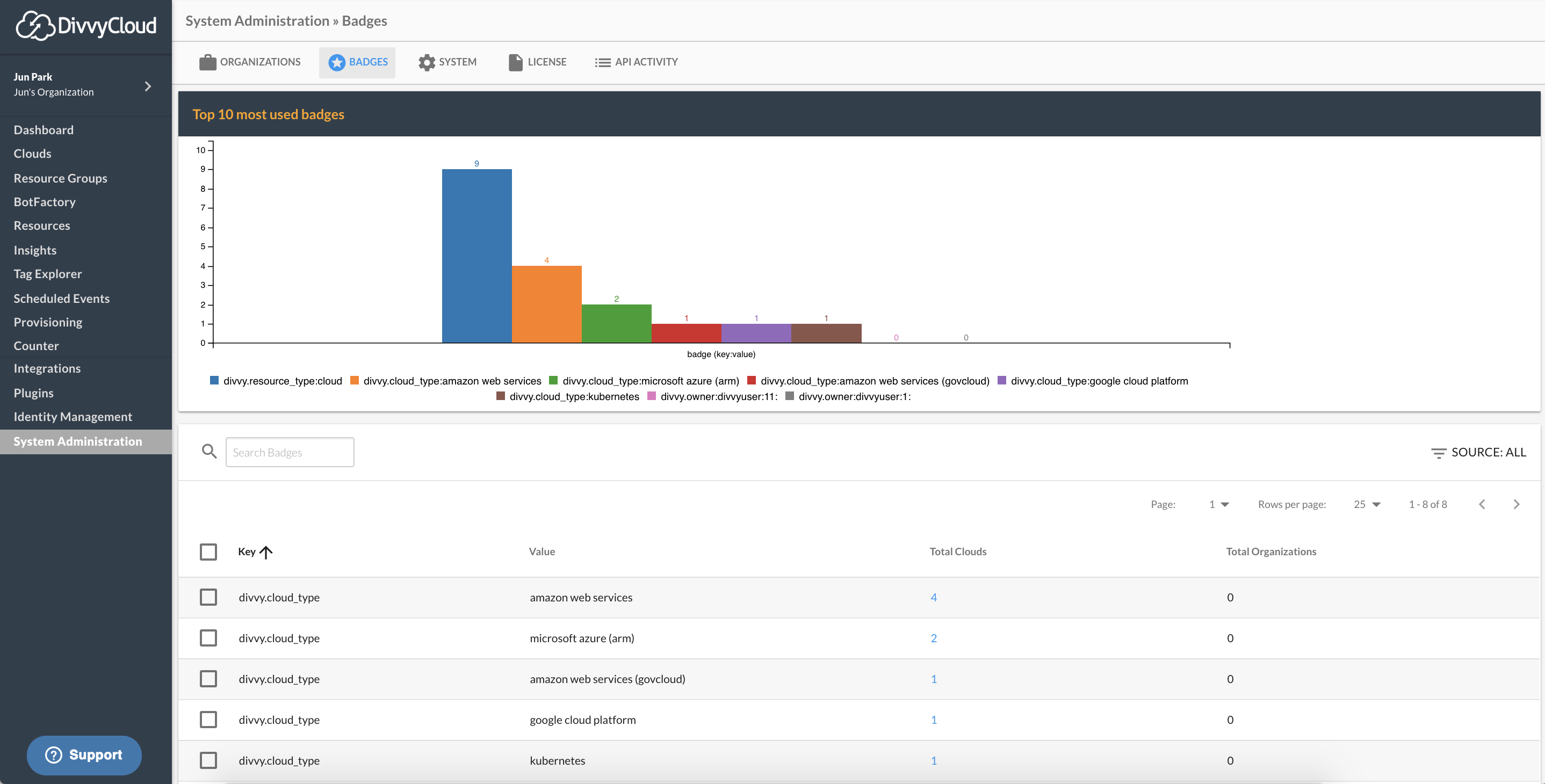
Badge Management View
A dedicated view for listing and searching system-wide badges has been long overdue. With 18.6 release, domain admins are now able to navigate to Badges tab found in** System Administration** page. Within the view include top 10 most used badges by associated clouds counts and an exhaustive table listing all the badges across the system.
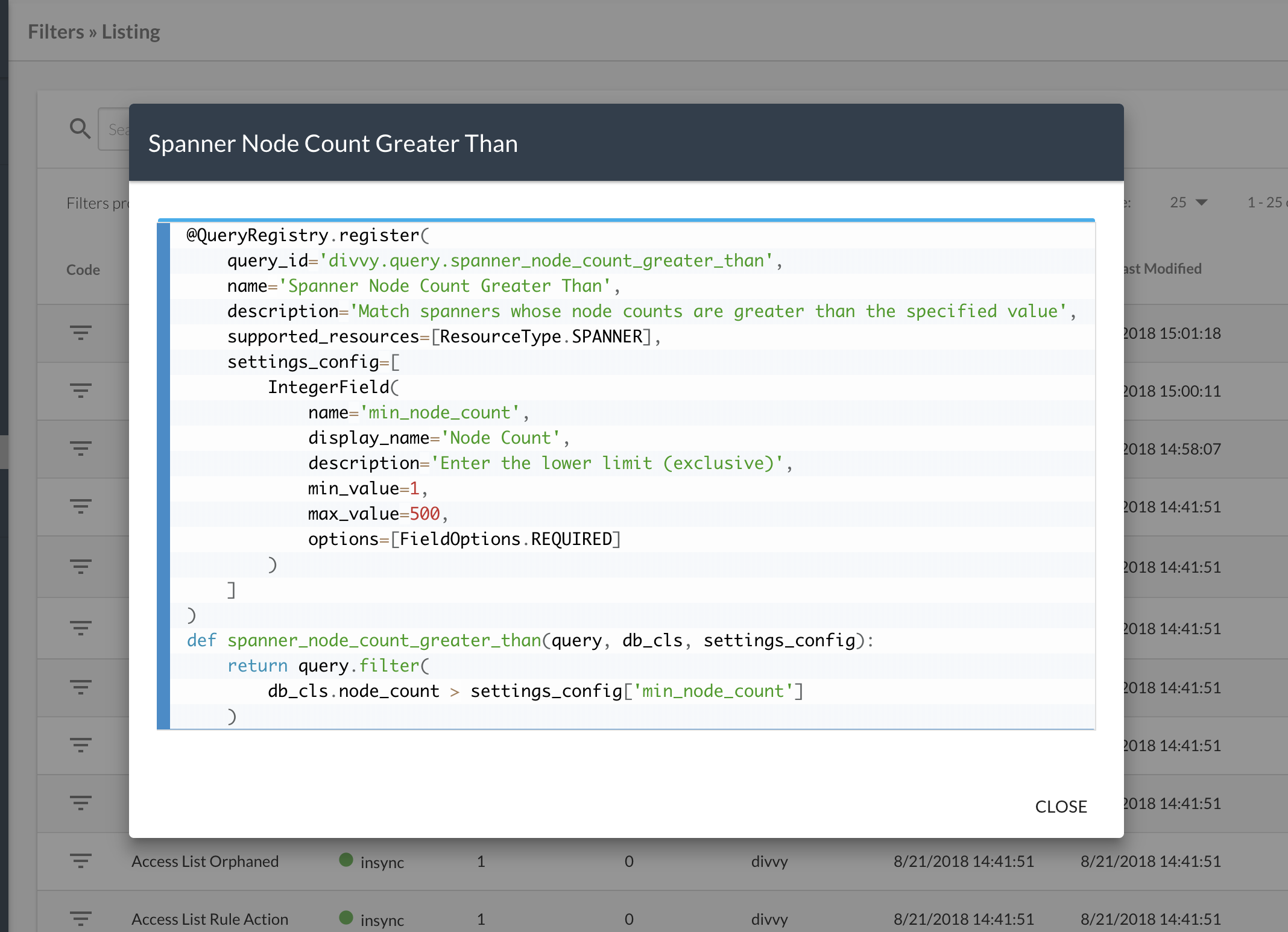
Filters Library
A top-level view reserved for the filters. Filters are one of the key ingredients in how we manage insights and bots. With the 18.6 release, users will now have access to an exhaustive list of all filters employed in our system. This will be the one stop location to check when a filter was created, modified, or deprecated. For those who want to see how the filter functions, this page will also let users open and see the source code of the filter definition.

General Enhancements
- Insight Pack emails now list Insights and Compliance Rules in different columns
- Now in Insight Pack emails, clicking the title of the pack will navigate to the Pack within the tool.
- AWS Organization listing of accounts now display account status within the view
- BotFactory actions like ‘Send Email Summary With CSV’ which allow multiple email entry, now do basic validation on input.
- AWS EMRs now harvest with pagination, allowing for harvesting of vastly larger sets of MapReduce Clusters.
- The account ID of Amazon, Azure and Google cloud accounts are surfaced in the tool.
- Badge keys and values are now case sensitive.
- Added ability to modify the New Account email text via the system settings. Also, it now supports HTML and Jinja2.
- Added Cloud Roles’ trusted accounts to Resource section view
- Failed scheduled events run by bots (in last 24 hours) are counted every 30 minute and exposed to Bot listing.
- Limited resources for Resource Has No Owner filter to Instances only.
- Tags can now be included in the Email Summary CSV action that is used by Bots
- Admins can now manually remove the active job scheduler from the Redis queue and view in active schedulers via the system settings.
- Custom Insights now support badges to persist scope over time New/Improved Actions
Enable S3 Bucket Logging
Enable server access logging to a specific bucket in. Access log records keep detailed accounts about access requests.
Update Assume Role Policy
Update the assume role policy associated with a IAM role.
New Filters
Cloud Account Contains/Missing Identity Resource
Identify cloud accounts which contain or are missing a specific identity resource. This filter takes in user input which defines the identity resource type (user, group, role or policy) and the required name. A common use case for this filter would be to identify cloud accounts which are missing a required Security audit role that must exist across each and every cloud account.
MapReduce Cluster Lifecycle Status
Identify mapreduce clusters in a particular lifecycle status.
MapReduce Cluster Total Node Count Greater Than
Identify clusters with a total node count greater than the specified number of total nodes.
MapReduce Cluster Total Node Count Less Than
Identify clusters with a total node count less than the specified number of total nodes.
MapReduce Cluster Open to the World
Identify MapReduce Clusters which have at least one instance which has an attached security which allows access from the World (0.0.0.0/0).
Access List Rule Contains Public Address (IPv4)
Identify security group, NACL and firewall rules which contain a public IPv4 address. This filter is effective to identify entry points from the Internet.
Storage Containers Without MFA Delete Enabled
Identify AWS S3 buckets which do not have the MFA Delete feature enabled.
Database Instances With/Without Auto Minor Upgrades
Identify database instances based on the value of the automatic minor upgrades boolean value.
Cloud User With Access From Unauthorized Domain
Identify cloud users within Google Cloud Platform which have IAM access from an unapproved domain. This filter can help identify gmail.com and other GSuite users who may have unauthorized/unapproved access into the domain.
Instance With Image Owned Outside Of Organization
Identify instances running on a shared image owned outside of the DivvyCloud organization. This filter will be helpful in detecting potential risk of running on foreign machine images that come from untrusted sources. Another side effect would be detection of cloud accounts that are indeed trusted, but not yet added to the system for DivvyCloud coverage.
Identity Provider Regular Expression
Identify identity providers based on the provider type. This filter leverages customer supplied regular expressions to identify IDP matches based on entity ID.
Cloud Accounts Not Leveraging Identity Providers
Identify cloud accounts who are leveraging Identity Providers for console based authentication.
Storage Container Logging to a Specific Bucket
Identify storage containers that are logging to a specific target bucket.
Instance With Project Wide SSH Keys Enabled/Disabled
Identify instances that have project wide SSH keys enabled or disabled.
Instance Connecting Serial Ports Enabled/Disabled
Identify instances that do and do not enable connecting to serial ports.
Instance With IP Forwarding Enabled/Disabled
Identify instances that have ip forwarding enabled or disabled. IP forwarding allows sending and receiving with destination and source IPs that do not match.
Activity Log Profile Does Not Exist
Identifies clouds which do not have an activity log profile.
Activity Log Retention Below Threshold
Identifies clouds which have an activity log retention period below a set threshold.
Database Instance Auditing Enabled
Identify database instances that have auditing enabled.
Database Instance Auditing Disabled
Identify database instances that have auditing disabled.
Database Instance Auditing Retention Below Threshold
Identify database instances that have an auditing retention less than the supplied threshold.
Database Instance Threat Detection Enabled
Match database instances that have threat detection enabled.
Database Instance Threat Detection Disabled
Match database instances that have threat detection disabled.
Database Instance Threat Detection Retention Below Threshold
Match database instances that have a threat detection retention period that is below the supplied threshold.
Database Instance Threat Detection Types Not Set To All
Match database instances that do not have threat detection configured to detect all types.
Database Instance Threat Detection Alert Recipients Not Set
Identify database instances that do not have any email recipients set for receiving threat detection alerts.
Database Instance Threat Detection Administrator Alerts Disabled
Identify database instances that are not configured to send threat detection alerts to service and co-administrators.
Database Instance Azure Active Directory Administrator Not Configured
Identify database instances that are not configured to use an Azure Active Directory user account for administration.
Database Auditing Enabled
Identify databases that have auditing enabled.
Database Auditing Disabled
Identify databases that have auditing disabled.
Database Auditing Retention Below Threshold
Identify databases that have an auditing retention less than the supplied threshold.
Database Not Encrypted
Identify databases that do not have encryption enabled.
Database Threat Detection Enabled
Match databases that have threat detection enabled.
Database Threat Detection Disabled
Match databases that have threat detection disabled.
Database Threat Detection Retention Below Threshold
Match databases that have a threat detection retention period that is below the supplied threshold.
Database Threat Detection Types Not Set To All
Match databases that do not have threat detection configured to detect all types.
Database Threat Detection Alert Recipients Not Set
Identify databases that do not have any email recipients set for receiving threat detection alerts.
Database Threat Detection Administrator Alerts Disabled
Identify databases that are not configured to send threat detection alerts to service and co-administrators.
Instance Without Monitoring Agent
Identify instances that do not have a monitoring agent extension installed.
Instance Has Unapproved Extensions Installed
Identify instances that have extensions installed which are not in a pre-approved list.
Instance Has Unencrypted Data Volume Associated
Identify instances having a data volume attached which is not encrypted.
Instance Has Unencrypted Root Volume Associated
Identify instances having a root volume attached which is not encrypted.
Instance Does Not Have Endpoint Protection Installed
Identify instances that do not have an endpoint protection extension installed
Network Watcher Not Enabled For All Regions
Identifies clouds which do not have Network Watcher enabled for all supported regions.
Custom Cloud Policy With Owner Access To Subscription
Identify custom cloud policies which have ownership access to the subscription.
Cloud User Is Guest
Match cloud users that are guest accounts.
Bug Fixes
- More harvesting permissions exception surface properly in the Clouds listing.
- Insight Pack emails sometimes render tables past the bottom of the email, and out of frame.
- AWS GovCloud clouds were failing to harvest account number. Now successfully harvests.
- Some DNS records were missing ‘time-to-live’ value and were failing to type cast. Now None value is supported.
- Public access evaluation diagnosed false-negatives for S3 and Elasticsearch resources in a very specific condition.
- Estimated Monthly Savings for Cloud Advisor Check resource now consistently display currency format.
- Fixed a bug where toggling resource groups in the Insights scope would cause cloud badges to not behave properly. Developer/Administrator Notes
Important
For Amazon Web Service customers, the role/user policy associated with each connected account will need to be adjusted to include the permissions below. Without these permissions, visibility into the newly supported AWS services will not be possible.
cloudfront:ListDistributions,
cloudfront:ListStreamingDistributions,
cloudfront:ListTagsForResource,
cloudfront:TagResource,
cloudfront:DeleteDistribution,
cloudfront:DeleteStreamingDistribution,
guardduty:GetDetector,
guardduty:GetMasterAccount,
guardduty:ListDetectors,
guardduty:ListMembers,
iam:GetSAMLProvider,
iam:ListSAMLProviders,
lambda:GetAccountSettings,
ses:GetIdentityVerificationAttributes,
ses:GetIdentityMailFromDomainAttributes,
ses:GetIdentityDkimAttributes,
ses:GetIdentityNotificationAttributes,
ses:ListIdentities,
sns:ListTopics,
sns:GetTopicAttributes,
sns:DeleteTopic,
sns:ListSubscriptions,
sns:GetSubscriptionAttributes,
sns:DeleteSubscriptionFor customers interested in leveraging the new supported actions within the tool, the following AWS permissions are required.
iam:UpdateAssumeRolePolicy,
s3:PutBucketLogging
For Microsoft Azure customers, the App registration for each account will need to be adjusted to include the “Read directory data” application permission for the Windows Azure Active Directory API. These permissions are required to support the new Azure IAM functionality.
Non Matched Bot Action Support
Important
For all cloud accounts, DivvyCloud will no longer support non-matched bot actions in order to facilitate improved bot performance. For release 18.6 we will have reverse compatibility for users that have bots which use non-matched actions. However, moving into release 18.7 all non-matched support will be removed.