Sep 26, 2019
19.4.4 Release Notes
Divvy Software Release Notice - 19.4.4 Maintenance Release (11/06/2019)
Release 19.4.4 is a minor release with just a couple of bug fixes:
- Fixed a bug that caused the insight name to be missing from the custom insight csv file. [Eng-1434]
- Fixed a bug in case sensitivity when adding resource tags to scorecard exports. [Eng-1413]
- Fixed a bug in dark mode that prevented the Bot action text from being visible for integrations that are not yet configured.
Click here to see the release notes for our last major release, 19.4. 19.4.3 Release Notes
Divvy Software Release Notice - 19.4.3 Maintenance Release (10/30/2019)
Release 19.4.3 contains a variety of general, action, and resource enhancements; a new action and several new filters; as well as a number of bug fixes. To review the release notes for 19.4.2 click here , for 19.4.1 click here , and to see the release notes for our last major release, 19.4, click here .
General Enhancements
Improved performance when parsing invalid/unsupported EDH events. [ENG-1340]
Added support for connecting AWS producer accounts which are not part of an AWS Organization to a consumer event bus. [ENG-1339]
Added a new action button to EDH Consumers to trigger a refresh/rescan of the configuration. [ENG-1288]
Added the ability to create a new resource group from the resources page. [ENG-1249]
Added a link that goes directly to the resource in the AWS console from the divvy resource pane. Click here for more information on AWS Smartlink. [ENG-934]
Actions
Enhanced Action
Enhanced the “Publish to Cloud Notification Topic” action to support leveraging the AWS application role. [ENG-1355]
New Action
Added a new BotFactory action to enable default volume encryption in AWS regions. [ENG-1168]
Resource Enhancements
Added a tooltip to provide more insight on what impaired visibility means for S3 buckets. Click here for more information on impaired visibility. [ENG-1291]
Added a clickable link to the AMI ID so that the user can drill in and see the extra metadata for the AMI being used by a resource. If the AMI is from a public image, the user will be notified it is a public (or deregistered) image. If the AMI comes from a private image, the user will be taken to its resource details in DivvyCloud. [ENG-1248]
New Filters
‘Compute Instance Allowing Specific Network Traffic In’ ‘Database Instance With IAM Authentication’ ‘Database Instance Without IAM Authentication’ ‘Load Balancer With DNS Alias Record’ ‘Load Balancer Without DNS Alias Record’
The new filter, ‘Compute Instance Allowing Specific Network Traffic In’, supports inspecting compute instances that allow specific ingress traffic. [ENG-1287]
The two new filters, ‘Load Balancer With DNS Alias Record’ and ‘Load Balancer Without DNS Alias Record’ identify load balancers with and without an associated CNAME record. [ENG-1286]
IAM authentication enabled/disabled information for database instances now appears under resource info and has corresponding filters. The new filters are ‘Database Instance With IAM Authentication’ and ‘Database Instance Without IAM Authentication’. [ENG-1214]
Bug Fixes
- Fixed a bug related to sorting to ensure sorting order for cloud visibility and bot modification timestamp. [ENG-1317]
- AWS Guard Duty findings that are in an archived state are no longer harvested. [ENG-1260]
- Added minor version to the software version displayed on the Compliance Scorecard page. [ENG-1259]
- Fixed bug that caused** issues when trying to authenticate via Azure AD**. [ENG-1156]
- Fixed bug that caused Azure Advisor description to not appear for some records. [ENG-899]
19.4.2 Release Notes
Divvy Software Release Notice - 19.4.2 Maintenance Release (10/23/2019)
Release 19.4.2 includes direct link capability for AWS resources, support for Elastic Beanstalk, and a variety of enhancements, new filters, and bug fixes. To review the release notes for 19.4.1 click here and to see the release notes for our last major release, 19.4, click here .
Direct Link Capability for AWS Resources
Direct links have been added for AWS resources; DivvyCloud now dynamically builds links to resources in the Amazon Web Services console.
Required permissions (already in the AWS policy): iam:ListAccountAliases
You can find this link on the Resource Details page: Select the category (e.g., Compute, Containers, Storage, etc.) of interest, the resource type/s (Instance, Distributed Table, etc.), then select the ‘Open Resource Properties’ dialog (next to the checkbox for individual resources). The last line of the resource properties panel, ‘Direct Link’, will show the link associated with this resource:

You can also use the direct link with Jinja2 to create notifications in Slack that link to the resource. The Jinja2 call is {{resource.get_provider_link()}}. An example of this notification type is:
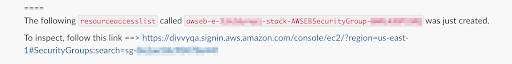
Support for AWS Elastic Beanstalk Resources
We’ve added support and visibility for AWS Elastic Beanstalk. We now offer filter and enhanced insight into both Elastic Beanstalk Applications and Environments. [ENG-205, ENG-202]
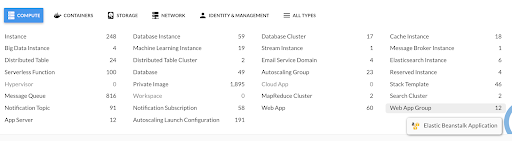
AWS Elastic Beanstalk can have many instances, ASGs, etc., linked to a given environment. The following resource types are supported by DivvyCloud and can be linked to an environment:
- Instances
- Autoscaling Groups
- Launch configurations
- Load balancers
- Queues
The new extensive set of read permissions required is available here .
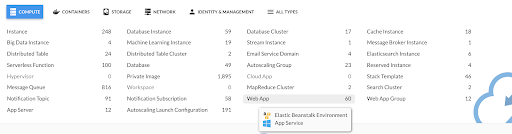
We added a new data point for WebApps: automatic_patching. It is exclusive to AWS Beanstalk and tracks whether or not ‘Managed Actions’ are enabled. To support the new Beanstalk resources we added a few new filters. [ENG-713, ENG715]
- Instance Managed By Web App [ENG-713]
- Web App With Automatic Patching Enabled [ENG-715]
- Web App With Automatic Patching Disabled [ENG-715]
With Beanstalk you can have multiple runtime versions so we added a new column on the resources page to display this information.
When using Beanstalk make sure that you have given DivvyCloud the proper permissions for all the supported resources (see list below) used by your Beanstalk app/environment.
New AWS Elastic Beanstalk permissions:
elasticbeanstalk:DescribeApplications
elasticbeanstalk:DescribeConfigurationSettings
elasticbeanstalk:DescribeEnvironments
elasticbeanstalk:DescribeEnvironmentResources
elasticbeanstalk:DescribePlatformVersion
Additional Features, Enhancements, and Filters
Added the ability to blacklist specific events from a consumer/producer Event Driven Harvesting (EDH) configuration. [ENG-828]
Enhanced the Compliance Scorecard subscription by allowing the user to update the name of the subscription email through editing the scorecard subscription name. [ENG-188]
Increased visibility into EC2 metadata and created a new filter “Instance User Data Search (Regex)” to allow for better interactions with this new metadata. [ENG-143]
Added entitlements support for Resource Groups. The Update Entitlements dialog (Administration/Identity Management/Roles & Entitlements/Entitlements) now allows you to assign users entitlements to Resource Groups [ENG-1032]:

Users can now export the job backlog to GCP Stackdriver. This enables the user to setup intelligent autoscaling of the worker tier. [ENG-1134]
Added new filters to identify suspicious activity based on findings from threat detection services such as AWS GuardDuty [ENG-1034]:
- Cloud User Exhibiting Suspicious Logging Activity
- Cloud User Exhibiting Suspicious Behavior
- Compute Instance Exhibiting Suspicious Behavior
- Compute Instance Mining Cryptocurrency
Added a new filter “Identify Elasticsearch instances that have the enforce SSL encryption” to inspect SSL enforcement for AWS Elasticsearch Instances along with the TLS policy that is used. [ENG-825] Read more here .
Added a new filter “Private Image Is Not In Use” to identify private images which are not associated with any compute instances or autoscaling launch configurations. [ENG-824]
Enhanced the filter “Identity Resource Contains Invalid Actions” to allow user to search for access to a particular ARN, but not supply any actions. This enables visibility into all identity resources with any level of access to a particular cloud resource. [ENG-902]
Enhanced the filter “Service Detector Does Not Have Specified Master Account” to support identifying detectors without any master account defined. [ENG-64]
We have updated the filter names of two powerful tag filters so that their functionality can be more easily understood simply from their names. The filter logic used, All and Any, can be confusing when not properly framed. These filters can be effective in enforcing internal Tagging Standards. [ENG-898]
- “Resource Does Not Contain Any Required Tag Keys” is now called “Resource Missing Tag Keys (Any Missing)”.
- “Resource Does Not Contain All Required Tag Keys” is now called “Resource Missing Tag Keys (All Missing)”.
Improved performance and reduced API calls needed to retrieve tags for Route53 domains. [ENG-874]
Improved performance: reduced standard AWS API harvesting to a minimum of four hours if EDH is enabled. [ENG-826]
We now validate credentials added to the eSlack integration before saving. In addition to this change, when adding actions to a bot you are no longer able to use integration actions that have not been added. ‘(Not Configured)’ will appear next to the integration actions that have not been added. [ENG-1038]
Removed harvesting for Azure database threat detection support for the following database types: MySQL, Postgres, and MariaDB. Threat detection service for these database services was in preview when this was implemented but Azure has decided to remove functionality. [ENG-881]
Added a new resource type search box at the top of the Resources UI which allows customers to search for specific resource types within the tool using the cloud native vernacular. [ENG-880]
New Filters
“Cloud User Exhibiting Suspicious Logging Activity” “Cloud User Exhibiting Suspicious Behavior” “Compute Instance Exhibiting Suspicious Behavior” “Compute Instance Mining Cryptocurrency” “Identify Elasticsearch instances that have the enforce SSL encryption” “Instance Managed By Web App” “Private Image Is Not In Use” “Web App With Automatic Patching Enabled” “Web App With Automatic Patching Disabled”
Renamed Filters
“Resource Missing Tag Keys (Any Missing)” replaces “Resource Does Not Contain Any Required Tag Keys” “Resource Missing Tag Keys (All Missing)” replaces “Resource Does Not Contain All Required Tag Keys”
Bug Fixes
Added a last_modified column to the Bots table to track the last time it was updated. [ENG-908]
Improved performance of the Compliance Scorecard when the account has a large number or clouds and Badges. [ENG-900]
Compliance Scorecard page now shows the correct version. [ENG-897]
The ‘Delete Resource’ action now correctly deletes DB Snapshots when they were snapshots of a DB Cluster. [ENG-820]
Empty DNS zone records are now correctly being harvested. [ENG-816]
The metadata column is now included in CSVs for Insight Pack exports. [ENG-772]
19.4.1 Release Notes
Divvy Software Release Notice - 19.4.1 Maintenance Release (10/16/2019)
This release adds support for two AWS regions: the Bahrain me-south-1 and Hong Kong ap-east-1 regions. These recently unveiled regions are a new classification of region introduced by AWS this year. Both of these regions are “opt-in”, and require active configuration to be enabled. The screenshot below provides an example of how to enable the region in the AWS console.
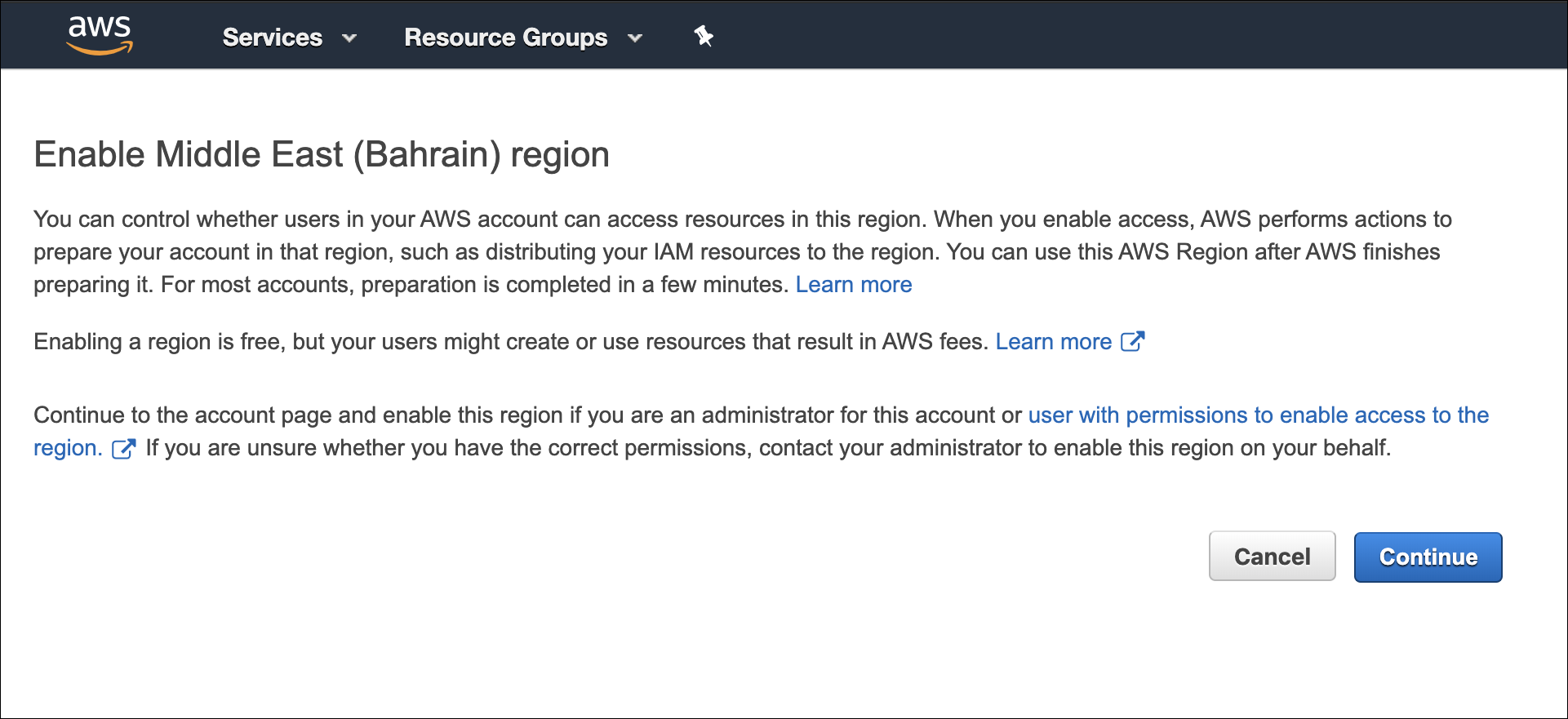
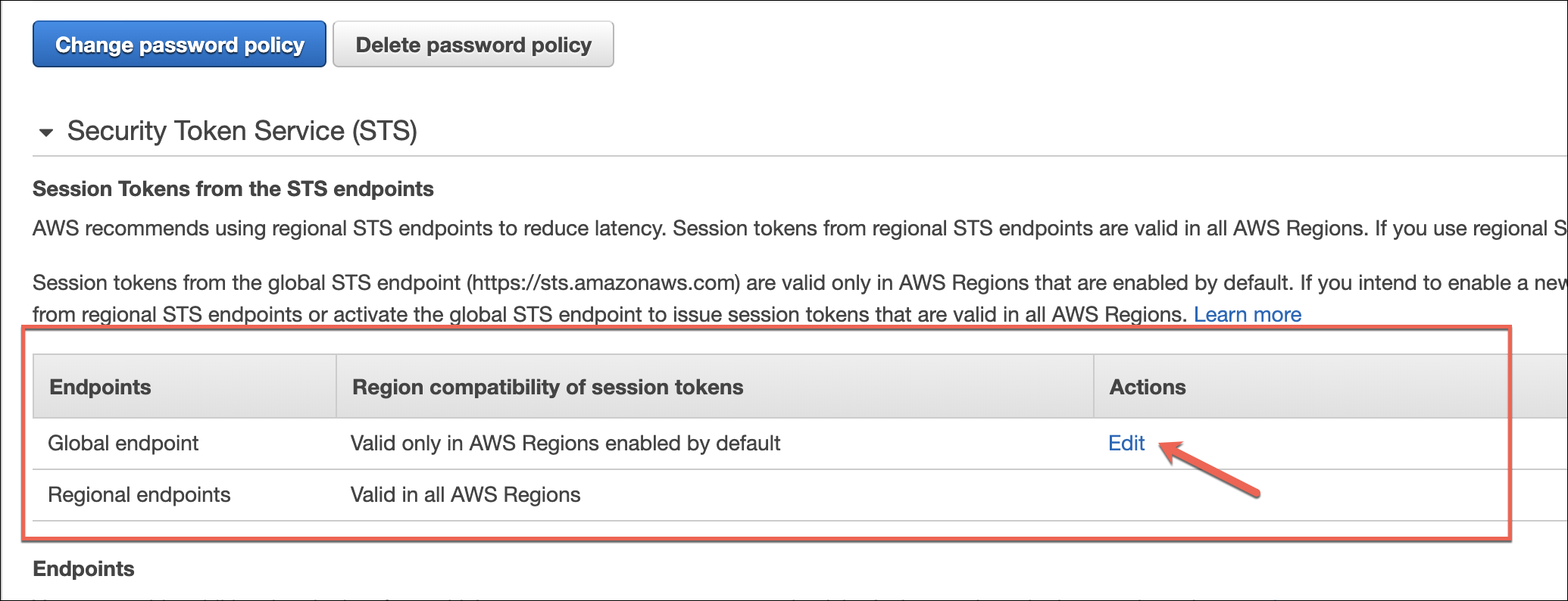
Once enabled, you will need to also update the STS token compatibility to allow DivvyCloud to communicate with these regions.
To do this visit the Amazon console here and modify the Global Endpoint option to allow larger session tokens to the global endpoint (https://stss.amazonaws.com ).
Note
Without this change, DivvyCloud will be unable to retrieve information from these regions even if they are enabled. For customers who prefer to keep these regions disabled, there are no changes required.
19.4.0 Release Notes
Divvy Software Release Notice - 19.4.0 Major Release (10/10/2019)
This release focuses on many improvements and enhancements to existing DivvyCloud features. We’ve added support for more cloud services from AWS and Azure. We’ve updated Azure CIS and HIPPA Compliance Packs while providing more filter support. We’ve also added many enhancements to the Compliance Scorecard and BotFactory.
Added Support for Azure Resources
This release significantly increases our support for Azure. We have added and updated many Azure services, filters, and insights. A complete list of supported Azure services is available here .
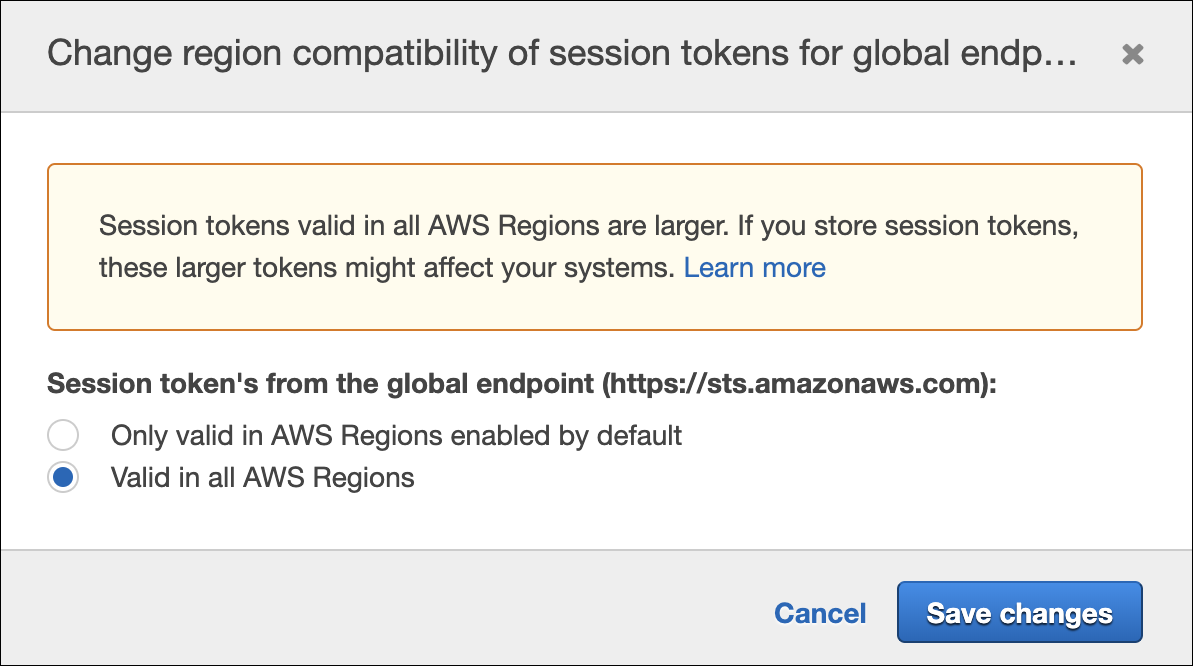
Azure CIS Pack Update With the release of 19.4, DivvyCloud is introducing a major update to the Azure CIS Benchmark. The CIS (Center for Internet Security) [https://www.cisecurity.org/ ] is an industry leader for compliance standards across a number of technologies and Cloud Service Providers. The release of the 1.1.0 spec builds on 1.0.0 (released in 2018) with a number of added checks that customers of the Microsoft Azure platform should perform against their cloud footprint. As you can see from the screenshot below, the version numbers have been included on both compliance standards to identify the version.
Please note that we will be deprecating version 1.0.0 in 2020, and are encouraging customers to begin transitioning to this updated specification.
The updated Azure insight pack to include Azure CIS 1.1.0 compliance insights has these new filters:
- Storage Account Storing Activity Logs
- Activity Log Profile Not Configured to Capture All Categories
- Activity Log Profile Not Configured for All Regions
Added filters for Azure SQL Database We added the following filters to support Azure SQL Database encryption and default key insights:
- Identify database instances that do not have SSL transit encryption enforced
- Identify database instances that have SSL transit encryption enforced
Added visibility and tag support for Azure Service Endpoints Azure Service Endpoints now allow for private, backend communication Azure services without the need to transmit over the Internet.
Added support for Azure Data Lake Storage (ADLS) v1. We now harvest Azure Data Lake Storage.
Added support for Private Azure DNS Zones This feature allows harvesting to capture the distinction between Public vs Private for Azure DNS zones. Current query filters for DNS zones should be updated where appropriate to support Azure cloud types (ARM, GOV, and China). New filters:
- DNS Zone Is Private
- Network Associated With Private DNS Zone
Increased visibility into Azure Data Warehouses Expanded our visibility for Azure Data Warehouses to include the encryption information, audit settings, and public status; added filters to support the increased visibility:
- Database Type
- Resource Is Exposed To Public
Increased visibility into Azure PostgreSQL servers configuration properties We now harvest additional configuration properties for Azure PostgreSQL and have created new filters to support these properties:
- PostgreSQL Servers With connection_throttling Setting
- PostgreSQL Servers With log_checkpoints Setting
- PostgreSQL Servers With log_connections Setting
- PostgreSQL Servers With log_disconnections Setting
- PostgreSQL Servers With log_duration Setting
- PostgreSQL Servers With log_retention_days Below the Selected Threshold
Increased visibility into Azure SQL TDE key information We now captures the TDE key settings for Azure SQL Servers. We also added a new query filter for getting sql server database server instances that are not configured for using BYOK:
- Database Instance With Data Encryption Configuration
Increased visibility for Azure Container Registries Harvesting additional information about Azure container registries and added new filters:
- Container Registry Type
- Container Registry Exposed to the World
Enhanced filter ‘Network Watcher Not Enabled For Region Expanded the Azure filter ‘Network Watcher Not Enabled For Regions’ to support user input for a defined whitelist of regions to filter on.
Harvesting additional properties on key vaults Added filters to enhance harvesting on key vaults:
- Key Vault Is Not Recoverable
- Key Vault Is Recoverable
Visibility around SQL Server audit policy information Added a filter to increase visibility around SQL Server audit policy information:
- Database Instance Missing Required Audit Action Groups
Quick Access to Enqueuing a Re-Harvest
A ‘Trigger Harvest’ option has been added to the actions menu for bots. This ‘Trigger Harvest’ action displays the clouds, resources, and regions a selected bot is looking for, then allows the user to enqueue a re-harvest for selected resources. This feature facilitates testing of bot filters against changes in the accounts.
- From the BotFactory main page, select ‘Trigger Harvest’ from the actions menu.
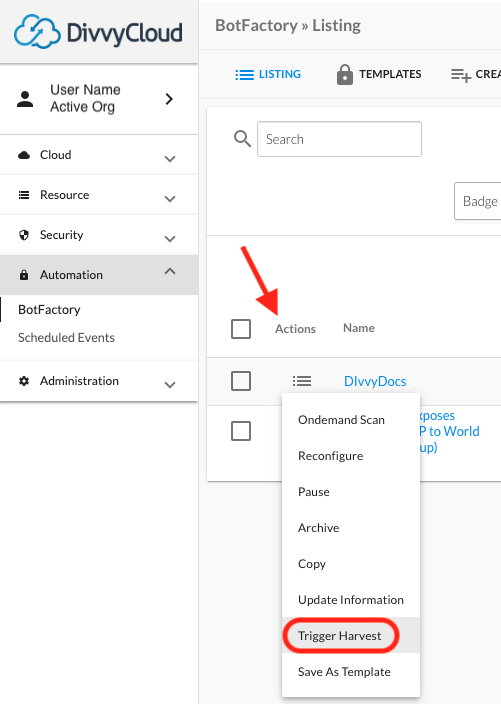
- The Trigger Harvest dialog displays the clouds and resource types to which the bot applies. Select the cloud and resource type of interest.
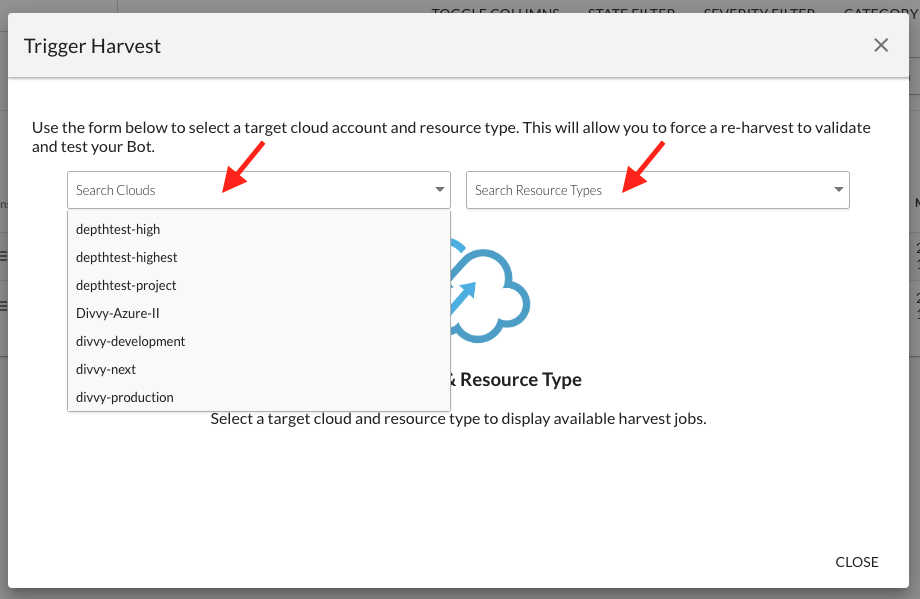
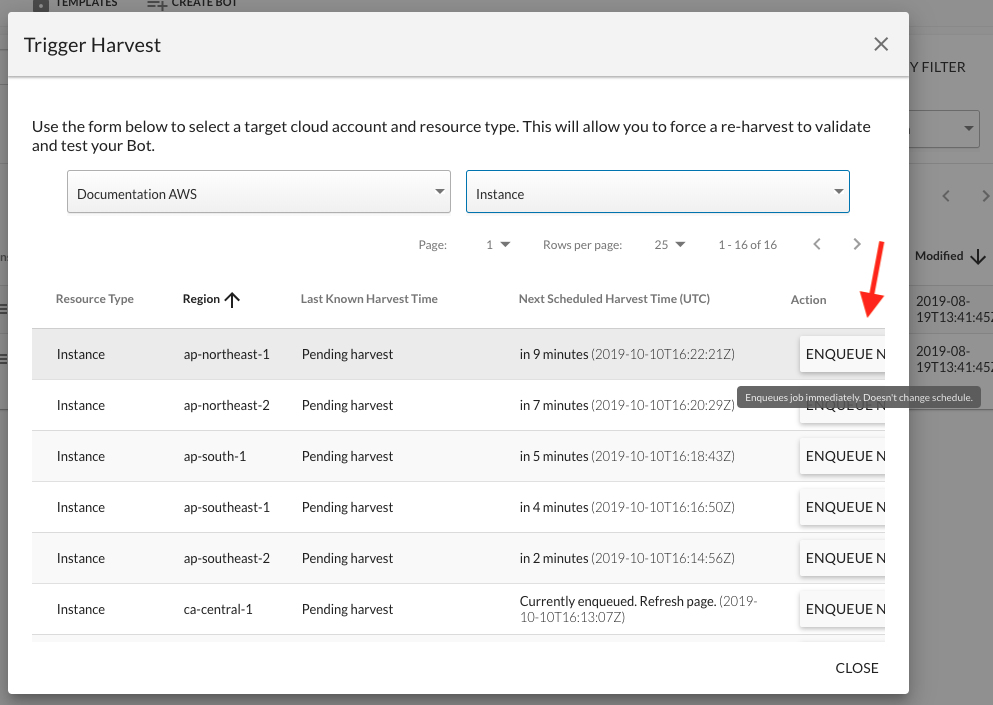
- Once cloud and resource type are selected, choose ENQUEUE for the specific resources and regions of interest.
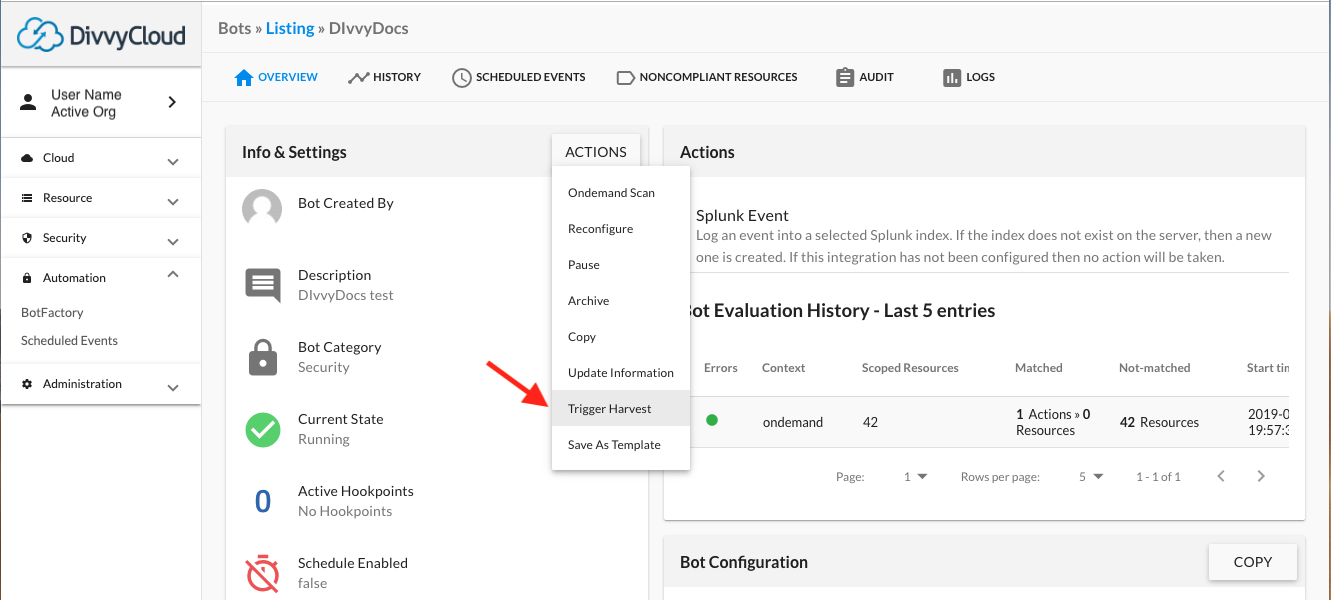
The ‘Trigger Harvest’ action is also available from the details page for a specific bot:
Additional Support for AWS Resources
Following are the additional AWS services which DivvyCloud supports with Release 19.4. A complete list of supported AWS services is available here .
Gave users ability to audit S3, KMS, Role and Elasticsearch policies Users can now filter for specific principals and permissions for policies which are directly associated with S3 buckets, Elasticsearch Nodes, SQS queues, SNS topics, Roles and more.
- Resource Specific Policy Principal Search
Message Broker (MQ) Instances Added visibility, tag, and lifecycle support for Amazon MQ. The new filter:
- Broker Instance Logging
Added SFTP support and created new filters Added support for AWS SFTP with the following associated resources: Logging Role, Invocation Role, VPC Endpoint, User Count, Hostname and Endpoint Type. New SFTP filters:
- Transfer Servers With Specified Endpoint Type
- Transfer Servers With Specified Identity Provider
- Transfer Servers With Specific Role
- Transfer Servers With Specified Hostname
- Transfer Servers With Specified User Count
- Transfer Servers Without Logging
- Transfer Servers With Zero Users
Increased AWS ElasticCache support DivvyCloud now harvests AWS ElasticCache customer managed key support for encryption at rest.
Added visibility into the AWS Redshift logging configuration Added visibility into the AWS Redshift logging configuration along with new filters to validate its compliance:
- Big Data Instance With Logging Enabled
- Big Data Instance Without Logging Enabled
Increased visibility for AWS Container Registries Now harvesting additional information about AWS container registries; added new filters:
- Container Registry Without Images
- Container Registry Open to the World
Store and surface the issuer of AWS ACM SSL certs Now storing and surfacing the issuer of AWS ACM SSL certificates; added a new filter to search for certificates by a particular issuer value:
- SSL Certificate Issuer
Added tagging and delete lifecycle actions against AWS EKS/ECS Added tag visibility and lifecycle support to AWS ECS/EKS clusters.
Increased performance around IAM API calls Reduced the number of IAM API calls required to obtain the permission boundary for each user and improved how IAM Permission Boundaries are harvested for users/groups at scale by using the API call iam:ListEntitiesForPolicy.
Increased visibility for AWS SNS We now pull down SNS encryption keys.
"elasticache:DescribeReplicationGroups",
"iam:ListAccountAliases",
"iam:ListEntitiesForPolicy",
"iam:ListRoleTags",
"iam:ListUserTags",
"mq:DescribeBroker",
"mq:ListBrokers",
"redshift:DescribeLoggingStatus",
"transfer:DescribeServer",
"transfer:ListServers"##New Filters
- Activity Log Profile Not Configured to Capture All Categories
- Activity Log Profile Not Configured for All Regions
- Big Data Instance With Logging Enabled
- Big Data Instance Without Logging Enabled
- Broker Instance Logging
- Container Registry Open to the World
- Container Registry Type
- Container Registry Without Images
- Database Category
- Database Instance Missing Required Audit Action Groups
- Database Instance With Data Encryption Configuration
- Database Running On Public Instance
- Database Type
- Key Vault Is Not Recoverable
- Key Vault Is Recoverable
- Network Associated With Private DNS Zone
- Network With Overlapping CIDR Blocks
- PostgreSQL Servers With connection_throttling Setting
- PostgreSQL Servers With log_checkpoints Setting
- PostgreSQL Servers With log_connections Setting
- PostgreSQL Servers With log_disconnections Setting
- PostgreSQL Servers With log_duration Setting
- PostgreSQL Servers With log_retention_days Below the Selected Threshold
- Resource Specific Policy Principal Search
- Storage Account Storing Activity Logs
- Threat Finding Contains Sample Data
- Threat Finding Without Sample Data
- Transfer Servers With Specified Endpoint Type
- Transfer Servers With Specified Identity Provider
- Transfer Servers With Specific Role
- Transfer Servers With Specified Hostname
- Transfer Servers With Specified User Count
- Transfer Servers Without Logging
- Transfer Servers With Zero Users
Enhancements
Tag support for scorecard excel report When configuring an email or s3 subscription for scorecard exports, you now can include up to 5 tag keys. These tags will be appended as columns to the right most side of the table for the resources and excepted resources worksheets. Create or edit a Scorecard Export schedule to include tags. The number of tags is limited to 5 per export.
Added resource links to impacted resources Added resource links to impacted resources for Guard Duty; this adds the ability to jump to the impacted resource details when viewing threat findings.
Enhanced EKS/K8s clusters handling during deletion/connection error This helps utilize worker capacity in a better way. Increased performance around workers by pausing accounts that are experiencing connection issues are have been deleted.
Enhanced the ‘Resource With Specific Role’ filter Enhanced the ‘Resource With Specific Role’ filter to support the inverse, allowing users to identify resources which are not leveraging one of the supplied roles.
- Resource With Specific Role
Bug Fixes
Long Session Timeouts Fixed an issue that would prevent long session timeouts from being respected when using the web interface and API.
Filter “Supported Resources” now groups by category It also lists by name rather than displaying as rows of icons. This change was necessitated by the rapidly increasing number of supported resources in DivvyCloud.
Resource Group Names When updating Resource Group names in the tool or via the API, the updated name is now properly reflected in Bot configurations which reference the group for exemptions.