Jan 07, 2020
DivvyCloud is pleased to offer the 19.5.4 maintenance release.
Latest 19.5 Release DivvyCloud is pleased to present Maintenance Release 19.5.4 . With this release, we have included the ability to harvest VMs associated with Azure Scale Sets . This behavior mirrors our existing behavior for AWS and is our standard model for harvesting these resources. One thing to note with the inclusion of this change is an increase in VMs for customers using Azure. This release also includes many new and enhanced filters for Microsoft Azure, additional Azure resource enhancements, and new/enhanced EDH events .
Users will also see improved app performance through a reduction in the number of GCP memory store jobs.
Skip ahead to review 19.5.4 permissions as well as 19.5.4 details . As always, contact us at support@divvycloud.com with any questions!
Table of Contents
Major Release 19.5 (11/21/2019) Maintenance Release 19.5.1 (12/04/2019) Maintenance Release 19.5.2 (12/19/2019) Maintenance Release 19.5.3 (01/08/2020) Maintenance Release 19.5.4 (01/16/2020)
19.5 Release Notes
Divvy Software Release Notice - 19.5 Major Release (11/21/2019)
With the release of 19.5 DivvyCloud is happy to introduce a number of improvements. We have completely restructured the product experience for first-time users connecting their clouds. This new workflow is simple, intuitive, and improves usability for both new and existing users when connecting clouds.
We’ve added support for new resources in both AWS and Azure to better surface customer cloud usage and compliance. 19.5 also includes improvements to the Compliance Scorecard with changes to the filtering hierarchy that offers both better performance and better visibility into compliance issues. This release adds many new filters, increases support for functionality around actions and visibility, and highlights permissions required to access the new improvements. Take a look at the details below!
New Features (19.5)
First-Time User Experience
We have included a complete reboot of our onboarding—or “Add a Cloud”—experience. First-time users and users adding new cloud accounts will walk through a newly designed form and workflow. This workflow simplifies the process for adding new cloud accounts, provides additional validation capabilities for certain providers, and streamlines the functionality around connecting your cloud accounts. Additional details can be found here .
Container Vulnerability Scanning
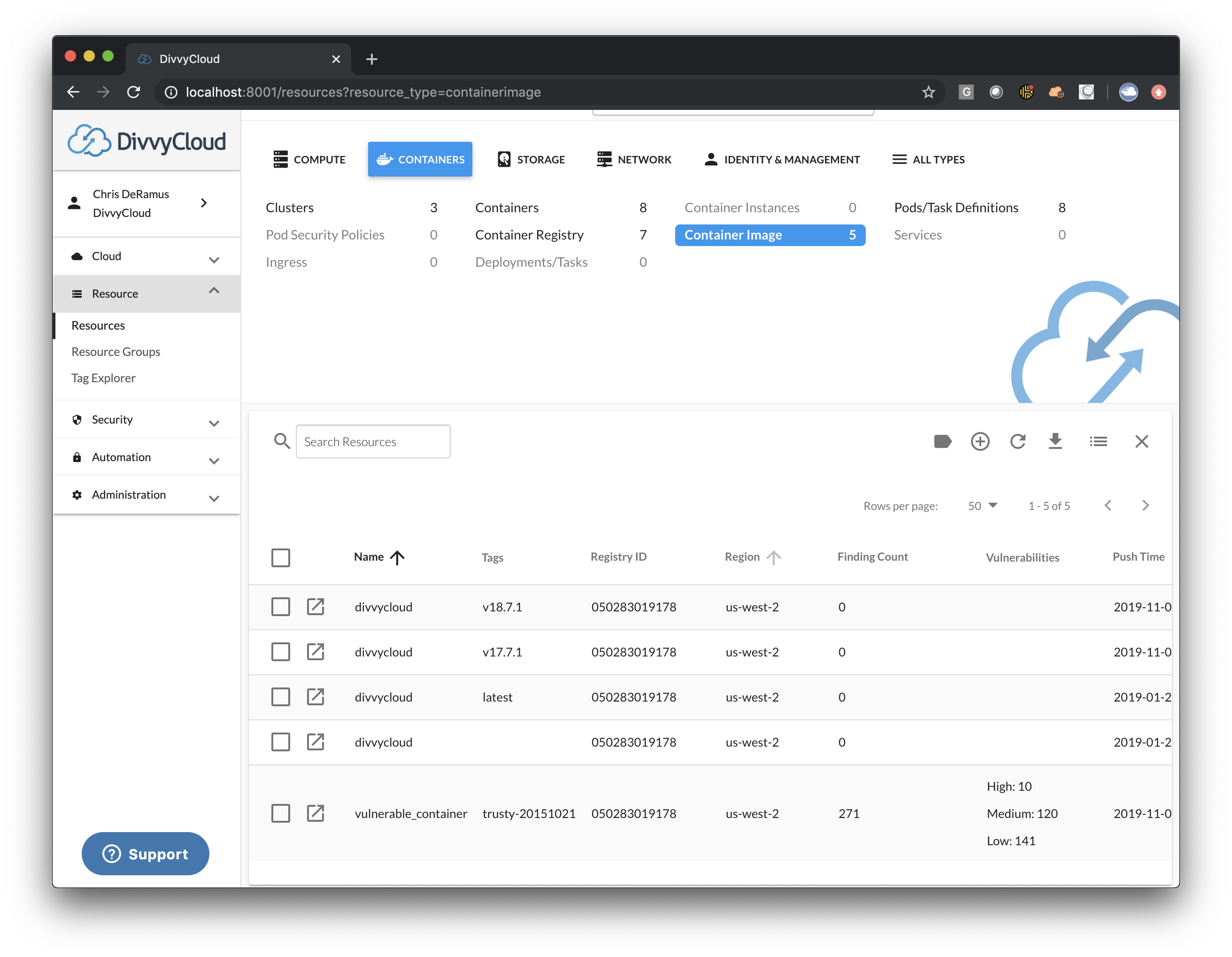
DivvyCloud now supports harvesting the Container Image findings made available via AWS ECR . This is a very exciting enhancement to the Amazon service, and these findings now are included inside of the product. As you can see from the screenshots below you can get quick access to container image findings, and leverage our new filters to key in on specific findings/vulnerabilities.

GCP Updates for Organizations
GCP support now includes two significant features around Organization management within DivvyCloud. The first feature allows users to limit the scope of resource visibility to a folder at the Organization level. Customers will be able to specify a folder when importing an organization’s projects so that projects contained inside of that folder and all child folders will be imported. Projects outside of the folder will not be added as DivvyCloud organization services. In addition, Clouds that are deleted in Google Cloud will be paused in DivvyCloud to prevent attempts at harvesting resources from these clouds.
The second feature ensures that when projects are removed from GCP, the project is also removed from DivvyCloud. Users will have the ability to opt-out of this feature but it will be enabled by default.
Further information can be found in Projects (GCP) and in Organizations (GCP) .
Scorecard Updates
We’ve updated the Compliance Scorecard, improving the filtering hierarchy to more readily and clearly surface the compliance information of interest and improve performance. Check out the Compliance Scorecard documentation for additional details.
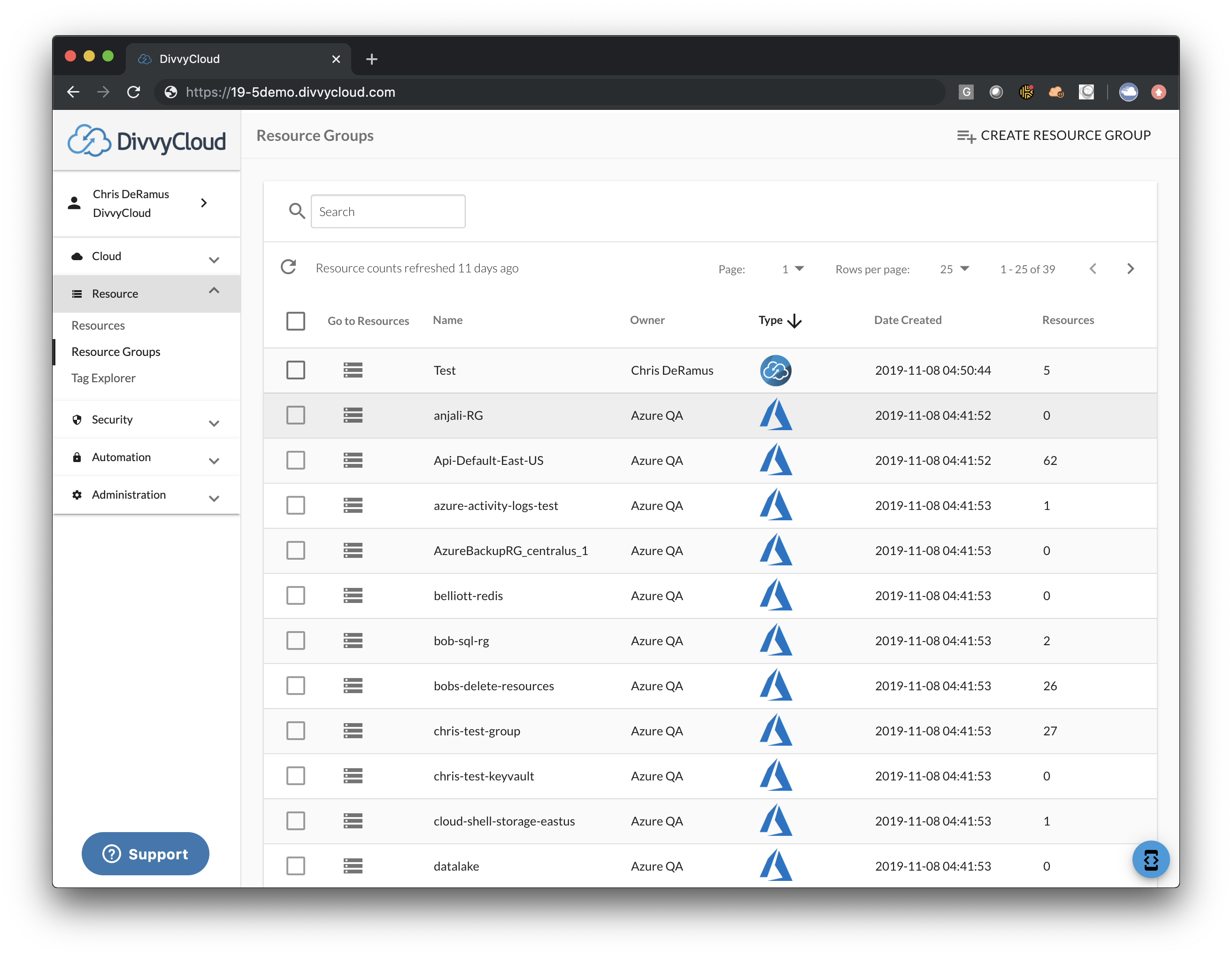
Azure Resource Groups
You can now view and leverage Azure Resource Groups from the Resource Groups section of our product. This is an incredibly useful enhancement as it now allows you to inspect Insights, create Bot automation and even delegate permissions all using your pre-built Resource Groups.
Additional Features (19.5)
Added the ability to harvest Azure ASGs and capture resource properties. [ENG-1389]
Users now have the ability to easily identify the cloud accounts that are in scope of a role. Each Role Name is a clickable link that displays the associated cloud accounts. [ENG-1341]
New Permissions Required (19.5)
New Permissions Required
For AWS: “athena:GetWorkGroup”, “athena:ListWorkGroups”, “cloudsearch:DescribeDomainEndpointOptions”, “codebuild:BatchGetProjects”, “codebuild:ListProjects”, “dms:DescribeReplicationInstances”, “ec2:DescribeTrafficMirrorTargets”, “ecr:DescribeImageScanFindings”, “ec2:DescribeSnapshotAttribute”, “iam:GetUser”, “iam:SimulatePrincipalPolicy”, “rds:DescribeDbSnapshotAttributes”, “rds:DescribeDbClusterSnapshotAttributes”, “waf:GetChangeToken”, “waf:GetRule”, “waf:GetWebACL”, “waf:ListRules”, “waf:ListWebACLs”, “waf-regional:GetRule”, “waf-regional:GetWebACL”, “waf-regional:ListRules”, “waf-regional:ListWebACLs”, “waf-regional:ListResourcesForWebACL”
For Azure: “Microsoft.EventHub//read” “Microsoft.Compute/virtualMachineScaleSets//read”
Actions (19.5)
ENHANCED ACTION
ENG-1432 Enhanced the IAM Identity Summary report to include user group associations and permission boundaries for both IAM users and roles.
NEW ACTIONS
- ENG-1424 Added a new lifecycle/Bot action to enable/disable transit encryption on Azure Storage Accounts.
- ENG-1222 Added visibility and lifecycle support for AWS CodeBuild Projects.
- ENG-1221 Added support for snapshot sharing with unknown accounts
- ENG-1220 Added support for AWS VPC Traffic Mirror Targets and created filters to provide more insight:
Traffic Mirror Target Linked To Unknown Account,'Traffic Mirror Target Linked To Another Account. - ENG-576 Added the **ability to assign GCP Labels **(tags) for Cloud Functions and Managed DNS Zones.
- ENG-511 Made these additional improvements re Bulk Email:
- Send Bulk Email bot action now supports sending email en masse to manually-specified recipients via BCC.
- Send Bulk Email bot action no longer fails ungracefully when attempting to send an email to unverified recipients.
- ENG-176 Added the ability to enable/disable public access for AWS RDS instances.
New Resources (19.5)
DivvyCloud now provides support for the following AWS resources:
Athena - AWS’ interactive query service that allows data analysis in Amazon S3 using standard SQL (on the Resources page: STORAGE/Data Analytics Workspace)
CodeBuild - tool for building and testing code in the cloud (on the Resources page: COMPUTE/Build Project)
DMS - (Database Migration Service) for migrating databases to Amazon (on the Resources page: STORAGE/Database Migration Instance)
WAF - (Web Application Firewall) for protecting Web applications (on the Resources page: NETWORK/Web Application Firewall)
WAF-Regional - AWS WAF with Elastic Load Balancing (ELB) Application Load Balancers
VPC Traffic Mirror Targets - Traffic Mirroring is an Amazon VPC feature that you can use to copy network traffic from an elastic network interface of Amazon EC2 instances (on the Resources page: NETWORK/Traffic Mirror Target)
DivvyCloud also now supports these Azure resources:
EventHub - Azure’s big data streaming platform (On the Resources page: STORAGE/Data Stream)
Virtual Machine Scale Sets - Azure’s resource for creating and managing a group of identical, load balanced VMs (On the Resources page: COMPUTE/Autoscaling Group)
Azure Resource Groups - Azure’s resource for managing resources that are associated with one or more applications/workloads is now visible within the tool.
Resource Enhancements (19.5)
ENG-1579 Now harvesting AWS RDS enabled logging types and added a new filter Database Cluster/Instance Enabled Logging Types that enables customers to effortlessly identify noncompliant logging configurations.
ENG-1567 Added **support for detection of HTTPS enforcement **for AWS Search Clusters.
ENG-1520 Added support for AWS Container Vulnerability scanning and created new filters to enhancement insight into you AWS ECR resources:
Container Registry Without Scan On Push Enabled
Container Image Vulnerability Search
Container Image Vulnerability Severity Search
Container Image Last Scanned
Container Image Push/Upload Date
ENG-1425 Now harvesting the MapReduce Cluster release version and added a new filter, MapReduce Cluster Release Version, to identify map reduce clusters by their version.
ENG-1376 Added the image ID direct link to the resource listing.
ENG-1142 Google Cloud Projects that are managed via Cloud Organizations will now be **auto-badged **with the folder with which they are associated.
New Insights (19.5)
Instance/Map Reduce Cluster With Recent High Severity Threat Finding Identify compute instances and map reduce clusters that have been identified as having a recent high severity external threat via AWS GuardDuty
Cloud User With Recent High Severity Threat Finding Identify IAM users that have been identified as having a recent high severity external threat via AWS GuardDuty
CloudWatch Event Bus Permissions Expose Access To The Public Identify AWS CloudWatch event bus resources whose IAM policy allows for public access
CloudWatch Event Bus Permissions Expose Access To The Public Identify AWS CloudWatch event bus resources whose IAM policy allows access from an unknown/thirty party account
Application Load Balancer Without Web Application Firewall (WAF) Protection Identify load balancers within your AWS footprint that do not have a cloud provided WAF associated to mitigate/prevent layer 7 attacks
Search Cluster Without HTTPS Enforcement Identify Search Cluster resources which do not enforce transit encryption over SSL/TLS
Traffic Mirror Linked To Unknown Account Identify traffic mirror target resources that are configured to enable traffic flows to an unknown/third party account
Compute Instance Mining Cryptocurrency Identify compute instances which have had one or more alerts trigger AWS GuardDuty for potential cryptocurrency mining.
ElasticSearch Cluster Without HTTPS Enforcement Identify ElasticSearch Domains which do not enforce transit encryption over SSL/TLS
Database Instance Without IAM Authentication Identifies MySQL, PostgreSQL and Aurora RDS databases which do not have the IAM authentication feature enabled
Compute Snapshot Trusting Unknown/Third Party Account Identify Compute Snapshots such as AWS EBS with permissions that share the resource with an unknown/third party account
Database Snapshot Trusting Unknown/Third Party Account Identify Database Snapshots such as AWS EBS with permissions that share the resource with an unknown/third party account
Azure Key Vault Is Not Recoverable Identity Key Vault resources which do not have the Soft Delete option enabled to aid in the recovery of an accidental removal
Database Running On Public Instance Identify databases which are running on an instance which allows access from any IP address in the World |
Web Application Without Automatic Patching Enabled Identify Web Applications such as AWS Elastic Beanstalk which do not have the automatic patching feature enabled
Transfer Server Exposed To Public Identifies Secure Transfer Instances that are configured to allow access from the public
Message Broker Instance Publicly Accessible Option Enabled Identify Message Broker resources which are accessible to the public
Message Broker Instance Without Audit Logging Identify Amazon MQ Broker Instances which do not have audit logging enabled
Database Replication Instance Publicly Accessible Option Enabled Identify Database Replication resources which are accessible to the public
Data Analytics Workspace Exports To Public Bucket Identify Data Analytics Workspaces such as AWS Athena Workgroups which are configured to export to an exposed/public S3 bucket
Data Analytics Workspace Exports To Unknown Bucket Identify Data Analytics Workspaces such as AWS Athena Workgroups which are configured to export to an unknown/third party bucket
Data Analytics Workspace Exports To Unencrypted Bucket Identify Data Analytics Workspaces such as AWS Athena which are configured to export results to an S3 bucket that is not configured for encryption at rest
Storage Accounts Without Advanced Threat Protection Identify storage accounts which do not have Advanced Threat Protection (ATP) enabled
Serverless Function Exposed To Public Identifies serverless functions such as AWS Lambda which have a policy that allows access/invocation from the public
Serverless Function Trusting Unknown Account Identifies serverless functions such as AWS Lambda which have a policy that allows access/invocation from an unknown/third party account
DNS Domain Without Transfer Lock Identifies DNS Domains that do not have the Transfer Lock feature enabled to prevent transfer without permission
DNS Domain Without Auto Renew Identifies DNS Domains that do not have the Auto Renew feature enabled
Database Instance Without Audit Logging Identify Amazon RDS Instances which do not have audit logging enabled
Content Delivery Network Not Logging Identify Content Delivery Network resources which do not enable logging
Serverless Function Not Within Private Network Identify Serverless Functions whose code does not execute within a private network such as a VPC
Container Registry Open to the World Identify Container Registries that are configured to allow anonymous/public access
Message Broker Publicly Accessible With Attached Exposed Security Group Identify AWS broker instances which have the publicly accessible boolean enabled and have a security group attached with allows access from the World
Data Analytics Workspace Unencrypted At Rest Identify Data Analytics Workspaces such as AWS Athena which are do not have encryption at rest enabled
New Filters (19.5)
ENG-1579 Now harvesting AWS RDS enabled logging types and added a new filter Database Cluster/Instance Enabled Logging Types that enables customers to effortlessly identify noncompliant logging configurations.
ENG-1547 Expanded “Threat Finding Severity” to apply to cloud user, logging, and instances. Added a new filter, Resource With Recent Threat Finding By Severity, that provides the ability to identify resources with recent threats by severity.
ENG-1528 Added a new filter, Load Balancer Without Any Associated Security Groups, to identify application/classic load balancers without an associated security group.
ENG-1520 Added support for AWS Container Vulnerability scanning and created new filters to enhance insight into AWS ECR resources:
Container Registry Without Scan On Push Enabled
Container Image Vulnerability Search
Container Image Vulnerability Severity Search
Container Image Last Scanned
Container Image Push/Upload Date
ENG-1519 Added new filters to identify AWS Regions with AWS CloudWatch Event Buses which are trusting an unknown account: AWS CloudWatch Event Bus Trusting Unknown Account and AWS CloudWatch Event Bus Exposed To Public.
ENG-1467 Added new filter, Serverless Function Exposed to Public, to identify serverless functions that do/do not prohibit public access. Added Event Driven Harvest support for the following Lambda events:
‘AddPermission’,
‘AddPermission20150331’,
‘AddPermission20150331v2’,
‘CreateFunction’,
‘CreateFunction20150331’,
‘DeleteFunction’,
‘DeleteFunction20150331’,
‘RemovePermission’,
‘RemovePermission20150331’,
‘RemovePermission20150331v2’,
‘UpdateFunctionConfiguration’,
‘UpdateFunctionConfiguration20150331’,
‘UpdateFunctionConfiguration20150331v2’
ENG-1425 Now harvesting the MapReduce Cluster release version and added a new filter, MapReduce Cluster Release Version, to identify map reduce clusters by their version.
ENG-1405 Added a new filter, Resource Associated Role Contains Action, to identify what actions a resource’s associated roles do/do not support.
ENG-1222 Added visibility and lifecycle support for AWS CodeBuild Projects.
ENG-1221 Added support for snapshot sharing with unknown accounts.
ENG-1220 Added support for AWS VPC Traffic Mirror Targets and created filters to provide more insight.
Traffic Mirror Target Linked To Unknown Account
Traffic Mirror Target Linked To Another Account
ENG-745 Added new filters to identify load balancers without an associated Web Application Firewall (WAF) in AWS:
Load Balancer Without Web Application Firewall Protection
Load Balancer With Web Application Firewall Protection
Web Application Firewall Rule Count
Web Application Firewall Orphaned
Bug Fixes (19.5)
ENG-1373 Fixed a bug where some Elastic Beanstalk environment frameworks were not harvesting properly.
ENG-908 Added a last_modified column to the Bots table to track the last time it was updated.
ENG-1453 BotFactory Slack message. Fixed a bug that caused the ‘message preview’ function in the slack action to stop working when scoped to resource groups.
ENG-1370 Fixed a bug that caused the filter “Cloud User With API Credentials Access Key Age Exceeds Threshold” to show old data.
ENG-1356 Performance. Reduced the number of GCP API calls for the Resource Manager API.
ENG-1407 All resource types should now display in the Resource Type search on the Resources page.
Divvy Software Release Notice - 19.5.1 Maintenance Release (12/04/2019) This maintenance release includes several enhancements for resources and actions as well as a number of general enhancements, new filters, and some bug fixes.
General Enhancements (19.5.1)
- Added a human readable label for resource dependencies. [ENG-1748]
- Added direct link capabilities to GCP resources. [ENG-1621]
- Expanded support for direct links to cloud account from a resource. [ENG-1363]
- Now including the author/creator of an Insight Pack in the listing. [ENG-1055]
- Added a create bot button in the compliance scorecard that matches the behavior of our insights page. [ENG-538]
Resource Enhancements (19.5.1)
- Added visibility to AWS Config delivery stream misconfigurations. New filters are:
AWS Config Streaming To Unknown Account Resource(s),AWS Config Streaming To Cross Account Resource(s), andAWS Config Stream Destination. [ENG-1766] - Added tag visibility and lifecycle support for AWS Lambda and Application Gateway Stages. [ENG-1611]
New Filters (19.5.1)
- New filters for the new visibility to AWS Config delivery stream misconfigurations [ENG-1766] are:
AWS Config Streaming To Unknown Account Resource(s)AWS Config Streaming To Cross Account Resource(s)AWS Config Stream Destination
Enhanced Actions (19.5.1)
- We now support the inclusion of cloud and resource scope information within the summary email action. [ENG-967]
Bug Fixes (19.5.1)
ENG-1723 Improved exception handling when harvesting Azure Serverless Functions.
ENG-1608 Fixed an error that caused issues when trying to change the password method from manual to autogenerated.
ENG-1573 Fixed a bug that blocked Insight editors/admins from recording changes to Insights.
ENG-1538 Fixed a bug that caused the insight findings link/url to not work as expected. Divvy Software Release Notice - 19.5.2 Maintenance Release (12/19/2019) In release 19.5.2, we’ve included visibility into AWS Network Interface descriptions for a far easier experience in identifying context around resources. This release also includes support for AWS’ Site-to-Site VPN (VPC) along with a new filter. We’ve added a new sorting capability around disabled resources, direct linking for GCP resources, detection, and filtering for generalized Azure VMs, created additional filters, and resolved numerous bugs. Review the details around this release below, and as always reach out to us at support@divvycloud.com with any questions!
New Permissions Required (19.5.2)
For AWS:
“config:DescribeDeliveryChannels”
“ec2:DescribeVpnConnections”
New Resources (19.5.2)
We now support AWS’ Site-to-Site VPN (VPC), enabling “access to your network from your VPC by attaching a virtual private gateway, creating a custom route table, and updating security group rules.” You’ll find this resource on the Resources main page under the category ‘Network’ and the resource type ‘Site-to-Site VPN’.
To support this resource type, we’ve added the filter Site-to-Site VPN Route Count. [ENG-1025] This allows users to see when the number of routes on a VPN is approaching 100. (AWS only supports up to 100 routes and will kill connections until the number of routes drops below 100.)
General Enhancements (19.5.2)
- Reworked AWS Redshift harvesting to increase performance while reducing unnecessary API calls. [ENG-1844]
- Added the ability to sort clouds (on the Clouds page) by the number of disabled resources. This allows the customer to **more readily surface issues **by allowing them to sort clouds (or projects) by those with the most disabled resources. [ENG-1843]
- Added direct link capabilities to GCP resources. This allows customers, especially those with a large GCP environment, to view their issues more quickly by accessing the GCP console represented in their cloud’s metadata. [ENG-1780]
- Selecting a Harvesting Strategy is now an option while adding a cloud account to DivvyCloud with the redesigned First-Time User Experience . If no harvesting strategy is selected, DivvyCloud will use the default provider strategy. [ENG-1747]
- We now provide a Jinja2 attribute for calling the age of an API Key. [ENG-1702]
- Expanded support for direct links to cloud account from a resource. [ENG-1363]
New Actions (19.5.2)
- Users now have the ability to **use Bots to automatically update the retention policy **(e.g., create a threshold for retaining logs around CloudWatch groups) and/or delete old logs. This provides flexibility in managing logs; as an example, a sandbox account might need less log retention than a production account. [ENG-1653]
Resource Enhancements (19.5.2)
Four resource enhancements in this maintenance release add visibility and filtering to resources we currently support:
- Added detection and filtering for generalized Azure VMs. New filter is ‘Instance is Generalized’. [ENG-1932]
- Added visibility and new filters for AWS Private Images (AMIs) encryption status. The new filters are ‘Private Image Is Encrypted’ and ‘Private Image Is Not Encrypted’. [ENG-1907]
- Added visibility into AWS Network Interface descriptions. The addition of the Network Interface description allows users to more easily determine the purpose and identity of a resource. For example, a resource with the description
VPC Endpoint Interface vpce-0ea98528caa9f35b3clarifies the Network Interface’s connection to other resources. This additional metadata can provide helpful context for customers in a number of scenarios. [ENG-1746] - Added visibility and filtering support for AWS Kinesis Firehose DirectPut encryption configuration. This enhancement was announced by AWS. (You can read details here .) This enhancement provides customers with full visibility into the encryption configuration for every resource that DivvyCloud supports, aligning with our compliance/security Insights and requiring no additional API calls. [ENG-1745]
New Filters (19.5.2)
Encryption Key State- Identifies encryption keys by their lifecycle state. [ENG-1738]Instance is Generalized- Adds detection and filtering for generalized Azure VMs. [ENG-1932]Private Image Is EncryptedandPrivate Image Is Not Encrypted- Add visibility for AWS Private Images (AMIs) encryption status. [ENG-1907]Public IP Attachment Type- Identifies AWS elastic IPs that are associated with NAT gateways. [ENG-1906]Resource Not In Cloud Account By Badge- Excludes resources which are in a cloud with one or more supplied badges. [ENG-1858]Site-to-Site VPN Route Count- Adds visibility and tag lifecycle support for new Network resource AWS Site-to-Site VPN connections. A new permission is required for this support: “ec2:DescribeVpnConnections”. [ENG-1025]Storage Container Without Preventative Public Access Enforcement- Detects S3 buckets without the property preventative public access controls. [ENG-1663]
Bug Fixes (19.5.2)
ENG-1932 Fixed a Bot error due to generalized VM in Azure. Added detection and filtering for generalized Azure VMs. New filter is ‘Instance is Generalized’.
ENG-1747 Added Harvesting Strategy selection when adding a cloud account. If no harvesting strategies exist, the default provider strategy is used. This prevents users from having to remember to return to a harvesting strategy selection after accounts have been added.
ENG-1628 Now correctly capturing the termination protection value for AWS CFTs.This fixes the issue where a reactive Bot with the filter ‘Stack Template with Termination Protection’ was not discovering the CFT.
ENG-764 Expanded the route table harvesting to support local targets.
Divvy Software Release Notice - 19.5.3 Maintenance Release (01/08/2020) In maintenance release 19.5.3, we offer support of a new resource, the AWS IAM Access Analyzer, and include filters, as well as list the permissions required to access this new feature.
Customers should also note the following:
- The filter
Load Balancer Without SSL Listenerno longer assumes that SSL passthrough to the instance port is always running on TCP 443. This bug fix means customers will see an increase in the number of resources flagged by this filter. [ENG-1949] - We added lifecycle support for Alibaba instances, storage containers, databases, and IAM resources. [ENG-1916]
- We added the ability to create badges in bulk. This allows customers to quickly apply multiple badges to cloud accounts for easier tracking and management. [ENG-1539]
New Resource (19.5.3)
This release adds support for the AWS IAM Access Analyzer. This service, announced at re:Invent 2019, helps customers find and triage potential IAM misconfigurations in accounts. Information on the service can be found via https://aws.amazon.com/blogs/aws/identify-unintended-resource-access-with-aws-identity-and-access-management-iam-access-analyzer/ . New filters added are Access Analyzer Finding Count By Type and AWS Access Analyzer Not Enabled In Region. New permissions required are “access-analyzer:ListAnalyzers” and “access-analyzer:ListFindings”. [ENG-1935]
New Permissions Required (19.5.3)
For AWS: “access-analyzer:ListAnalyzers” “access-analyzer:ListFindings”
General Enhancements (19.5.3)
- Insight Violations (Resource>>Resource Details>>Insight Violations) are now in alphabetical order, allowing the user to find the insight that they care about quickly. [ENG-2049]
- Added server-side pagination support for the list_users endpoint. [ENG-2001]
- Updated log messages to include the account information, and improved the status when an account/region runs into rate limiting. [ENG-1998]
- Added the ability to disable AWS regions at scale using harvest strategies. [ENG-1730]
- Included a link to the network resource when viewing route tables. [ENG-1578]
- On the resources page we now allow the selection of multiple resources from different pages at the same time. [ENG-1429]
- Expanded support for direct links to cloud accounts from a resource. [ENG-1363]
- Added the ability to download a CSV report of users/organization admins. [ENG-1319]
- Improved messaging when performing a diagnostics run by adding a brief description below the Run Diagnostics button and a verification message that confirms a run has started. [ENG-1101]
Resource Enhancements (19.5.3)
- Added support for AWS EKS public CIDR blocks. This is a recent update by AWS which adds a new layer of security for EKS clusters that have the public endpoint enabled, and as such changes our definition of what public access is. A new filter,
Kubernetes Cluster Engine Public Access CIDRs, was added to support the increased visibility into AWS EKS. [ENG-1995] - Added the identification date to failed insights. This can be found on the Insight Violations tab, located in the resources property menu. [ENG-1712]
- Added a new property to identify subnets that auto-map public IPs on instance launch. Added a filter,
Subnet Public IP Mapping - AWS/Gov/China, to support new visibility. [ENG-1401] - Added the ability to retrieve threat finding details in an on-demand fashion. These details can be found in the resource properties menu under the Threat Detection tab. [ENG-1086]
New Actions (19.5.3)
- Added the ability to disable specific harvest jobs. [ENG-2003]
- Added lifecycle support for Alibaba instances, storage containers, databases, and IAM resources. [ENG-1916]
- Added the ability to create badges in bulk. This allows customers to quickly apply multiple badges to cloud accounts for easier tracking and management. [ENG-1539]
Enhanced Actions (19.5.3)
- Added the ability to delete Elasticache clusters that are part of a replication group. [ENG-1152]
New EDH Events (19.5.3)
- AWS Event Driven Harvesting (EDH) now supports the following three Elasticache events [ENG-2004]:
- CreateReplicationGroup
- DeleteReplicationGroup
- ModifyReplicationGroup
- Added EDH support for the **Secure File Transfer **resource. [ENG-1470]
New Filters (19.5.3)
Access Analyzer Finding Count By TypeandAWS Access Analyzer Not Enabled In Region- These two filters provide support for the AWS IAM Access Analyzer. This is a service was announced at re:Invent 2019 which helps customers find and triage potential IAM misconfigurations in an account. Information on the service can be found via https://aws.amazon.com/blogs/aws/identify-unintended-resource-access-with-aws-identity-and-access-management-iam-access-analyzer/ . Two new permissions are required to use these filters: “access-analyzer:ListAnalyzers” and “access-analyzer:ListFindings”. [ENG-1935]Cloud Account Contains Multiple Virtual Networks in the Same Region - AliCloud, AWS/Gov/China, Azure/Gov/China- Supports Azure virtual networks. [ENG-1867]Kubernetes Cluster Engine Public Access CIDRs- Increases visibility into the added support for AWS EKS public CIDR blocks. This is a recent update by AWS which adds a new layer of security for EKS clusters that have the public endpoint enabled, and as such changes our definition of what public access is. AWS. [ENG-1995]Message Queue Without Redrive Policy (Dead Letter Queue)andMessage Queue Redrive Policy Configuration (Regular Expression)- These two filters inspect SQS resources based on their redrive/DLQ configuration. AWS/Gov/China. [ENG-2002]Network Peering With External Account - AWS/Gov/China, GCP, Azure/Gov/China- Identifies network peers which peer with any external/outside account. [ENG-1404]Resource Associated With Map Reduce Cluster - AWS/Gov/China- Identifies instances and volumes which are associated with a map reduce cluster. [ENG-1085]Security Group Not Attached to a Network Subnet - Azure/Gov/China- Supports Azure virtual networks. [ENG-1867]Snapshot With Active Share- Identifies compute/database snapshots that are being shared. AWS/Gov/China. [ENG-2005]Subnet Public IP Mapping - AWS/Gov/China- Supports visibility into new property identifying subnets which auto-map public IPs on instance launch. [ENG-1401]
Bug Fixes (19.5.3)
ENG-2006 Removed GovCloud support for the Cloud Account Without Protected Root Account filter; GovCloud does not support AWS root accounts.
ENG-2000 Fixed a bug that prevented the active cloud account and image from being displayed in the Job Backlog settings.
ENG-1972 Fixed the Domain Viewer role permission lookup which prevented a read-only admin from seeing the DivvyCloud “Cloud Listings” Page.
ENG-1949 The filter Load Balancer Without SSL Listener no longer assumes that SSL passthrough to the instance port is always running on TCP 443.
ENG-1948 ‘Add Cloud’ permission now correctly saved when creating a new DivvyCloud Role. Divvy Software Release Notice - 19.5.4 Maintenance Release (01/16/2020) With the release of 19.5.4, we have included the ability to harvest VMs associated with Azure Scale Sets . This behavior mirrors our existing behavior for AWS and is our standard model for harvesting these resources. One thing to note with the inclusion of this change is an increase in VMs for customers using Azure. This release also includes many new and enhanced filters for Microsoft Azure, additional Azure resource enhancements, and new/enhanced EDH events .
Users will also see improved app performance through a reduction in the number of GCP memory store jobs.
New Permission Required (19.5.4)
For Microsoft Azure: “Microsoft.Insights/DiagnosticSettings/read”
This permission is required for the new filter Data Stream Invalid Diagnostic Logging Configuration.
Resource Enhancements (19.5.4)
- We now store the private/public image ID that’s associated with Azure virtual machines. We also enhanced the following Instance Image filters by adding Azure support:
Instance Image ID,Instance Image Age Exceeds Threshold. [ENG-1864] - Added a new Key Vault filter,
Key Vault Access Is Not Restricted to a Federated Role, that allows for filtering access policies that are not restricted to a federated role. [ENG-1863] - Added new filters for Azure Event Hub diagnostics and data capturing as well as filters to identify Azure Event Hub resources by the tier and count:
Data Stream Tier,Data Stream Event Hub Count,Data Stream Publicly Accessible,Data Stream Without Data Capturing Enabled,Data Stream Data Capture Message Retention,Data Stream Data Capture Location Encryption Type,Data Stream Invalid Diagnostic Logging Configuration. [ENG-1862]
General Enhancements (19.5.4)
- Improved performance when loading large numbers of user groups. [ENG-2123]
- Improved and expanded direct links to cloud accounts from a resource. [ENG-2100]
New EDH Events/Enhancements (19.5.4)
- We no longer require cloud properties when building out the consumer event bus. [ENG-2127]
- Added EDH support for the Secure File Transfer resource. [ENG-2087]
New Filters (19.5.4)
Cloud Resource Type Count- Identifies cloud accounts by the number of resources present. [ENG-2121]Database Instance Access Not Restricted to a Service Endpoint Azure/China/Gov Db Instance- Identifies db instances not using service endpoint access. [ENG-1866]Autoscaling Image ID - AWS/Azure/Gov/China Autoscaling/Autoscaling Launch Configuration- For autoscaling image id. [ENG-1865]Key Vault Access Is Not Restricted to a Federated Role- New Key Vault filter allows filtering access policies that are not restricted to a federated role. [ENG-1863]Web App Without Virtual Network Integration- New filter for Azure Web Apps that doesn’t use vnet integration; also enhanced our ‘Resource Allows access from unapproved networks/subnet’ filters by adding support for Azure Web Apps. [ENG-1860]
New filters for Azure Event Hub diagnostics and data capturing, as well as filters to identify Azure Event Hub resources by the tier and count. [ENG-1862]
Data Stream TierData Stream Event Hub CountData Stream Publicly AccessibleData Stream Without Data Capturing EnabledData Stream Data Capture Message RetentionData Stream Data Capture Location Encryption TypeData Stream Invalid Diagnostic Logging Configuration- This filter requires the permission “Microsoft.Insights/DiagnosticSettings/Read”.
New filters for Azure storage account resources.[ENG-1861]
Storage Resource Encryption Type - Azure/China/Gov Storage Container/Shared File SystemResource Allows Access From Unapproved Networks - Azure/China/Gov Db Instance/Data Stream/Service Encryption Key Vault/Storage AccountResource Allows Access From Unapproved Subnets - Azure/China/Gov Db Instance/Data Stream/Service Encryption Key Vault/Storage AccountStorage Resource Allows Access From Unapproved Networks - Azure/China/Gov Storage Container/Shared File System
Enhanced Filters (19.5.4)
Instance Associated With Autoscaling Group - Azure/Gov/China Instances- Enhanced existing filters by adding new cloud support and resources; related to new filter for autoscaling image id. [ENG-1865]Instance Not Associated With Autoscaling Group - Azure/Gov/China Instances- Enhanced existing filters by adding new cloud support and resources; related to new filter for autoscaling image id. [ENG-1865]Instance Running Unknown Image - Azure/Gov/China Instances- Enhanced existing filters by adding new cloud support and resources; related to new filter for autoscaling image id. [ENG-1865]Instance Using Unmanaged Disks - Autoscaling Group- Enhanced existing filters by adding new cloud support and resources; related to new filter for autoscaling image id. [ENG-1865]- ‘Resource Allows access from unapproved networks/subnet’ - added support for Azure Web Apps. Related to new filter
Web App Without Virtual Network Integrationthat doesn’t use vnet integration. [ENG-1860]