Jun 24, 2020
DivvyCloud is pleased to announce our latest release.
Latest 20.2 Release DivvyCloud announces Minor Release 20.2.6 . This minor release consists of a handful of bug fixes. Skip ahead to review all the 20.2.6 details .
As always, contact us at support@divvycloud.com with any questions.
Table of Contents
Major Release 20.2 (05/06/2020) Minor Release 20.2.1 (05/08/2020) Minor Release 20.2.2 (05/13/2020) Minor Release 20.2.3 (06/03/2020) Minor Release 20.2.4 (06/11/2020) Minor Release 20.2.5 (06/17/2020) Minor Release 20.2.6 (06/24/2020)
Divvy Software Release Notice - 20.2 Major Release (05/06/2020) DivvyCloud is thrilled to present Major Release 20.2. With this major release, we introduce our Infrastructure as Code Security capability. We also include:
- Support for AWS Organizations
- Significant improvements to the display and performance of the Compliance Scorecard
- Additions of dozens of filters and actions to improve our overall cloud parity
- A listing of required new permissions
- An updated NIST 800-53 Compliance Pack
- EDH Enhancements , many general enhancements and improvements , as well as the usual bug fixes
Installation Time
You can expect the upgrade for this release to require significantly longer than usual to install. This is a major release with many new and important features, capabilities, and enhancements. Installation time should be 20 minutes or less.
MS Teams Integration Changes
Customers using the old integration of Microsoft Teams will need to manually update their bots before upgrading to 20.2. Any bots using the old integration will be in an invalid state with the following error: “Bot Instructions Invalid: BotFactory function slack.action.send_microsoft_teams_message does not exist in the registry.”
Updates for the bot actions can be completed using the action dropdown in the BotFactory.
See detailed steps here .
As always, contact us at support@divvycloud.com with any questions!
Highlights (20.2)
Support for AWS Organizations
Our Organizations feature, currently available for GCP, is now extended to AWS. (And you can expect this feature in Azure in the near future.) Organizations allow you to connect to an entire domain, walking that domain through onboarding all of its component projects into the DivvyCloud installation.
This means less maintenance and better synchronization. For example, when a project is removed, it doesn’t remain in our tool as a stale artifact, reporting false positives in compliance infractions; the Organizations feature recognizes the removed project is no longer a cloud.
We’ve provided flexibility as well as multiple management options for onboarding AWS organizations:
- The onboarding of the organization is role-based, ensuring separate credentials for managing your harvesting versus the iteration over your organization. Thus, users can limit the permissions that a role has to only what is needed to iterate over the organization, ensuring permissions to get into an account inappropriately can be denied.
- Users can limit the scope of the projects and organizations being onboarded.
- The Organizations feature will sync your tags as badges; when you modify the tags in your Amazon account, they will come in as badges in DivvyCloud.
Read the full documentation for AWS Organizations here .
Note: Onboarding of GCP organizations will retain the ability to opt-in or opt-out of this feature.
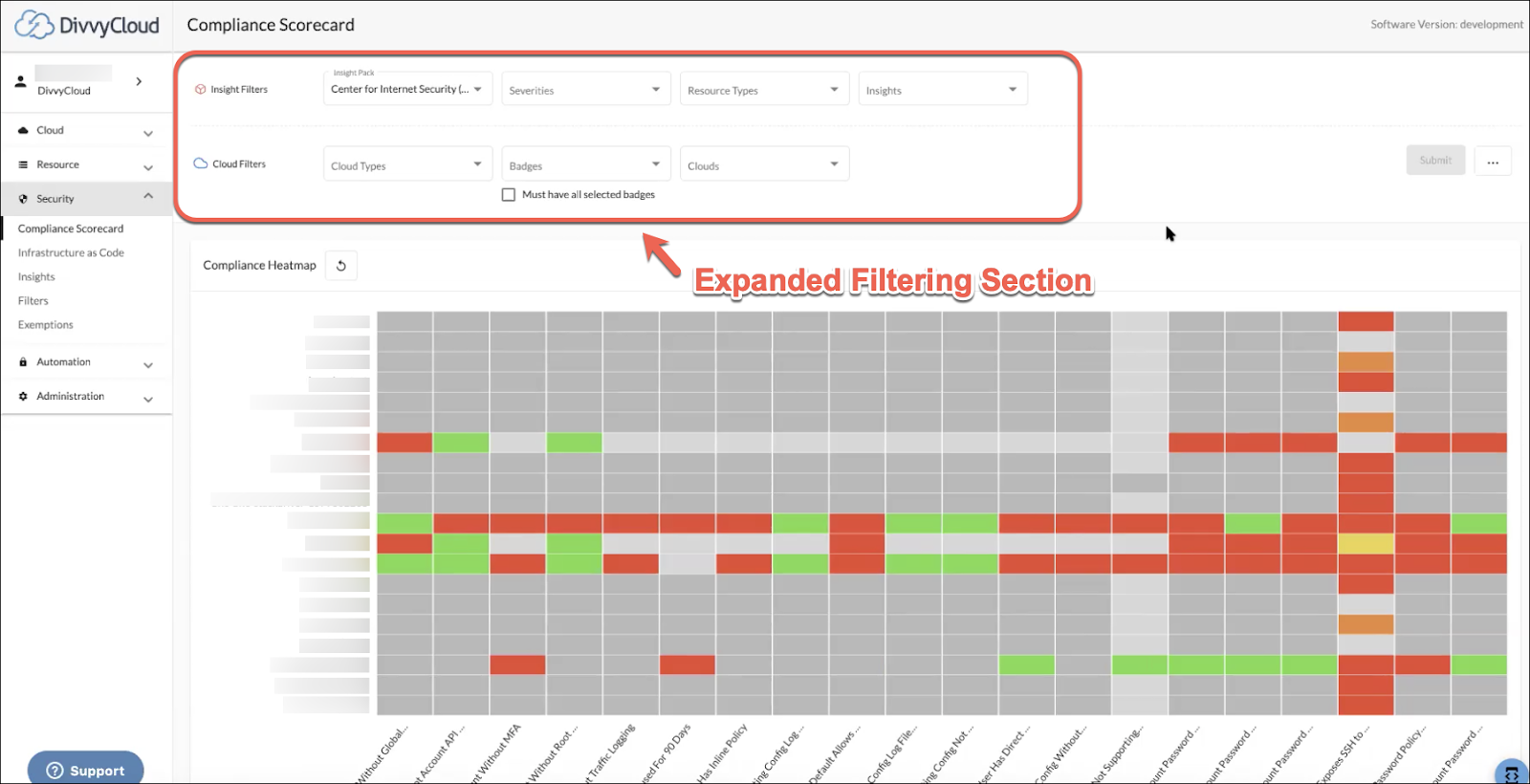
Compliance Scorecard Improvements
The Scorecard has been redesigned to provide improved readability while offering even greater visibility into your overall compliance picture, as well as significantly improving performance. The redesign includes:
- An expanded filtering section at the top of the scorecard
- The Heat Map presentation immediately following the filtering section
- Additional displays (also improved for readability), including Noncompliance by Severity and History of Discovered Noncompliant Resources, visible by scrolling down the page
We have also retained previous navigation functionality, including pagination controls for Insights and clouds, as well as the ability to click into each account/cell for viewing of more detail.
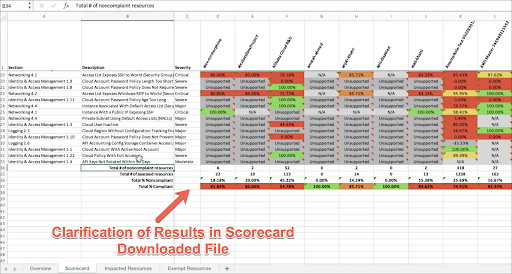
Additional improvements to the Scorecard include improvements to the Excel download. Here again, a more readable format presents additional information about your compliance picture. Users can more readily parse the downloaded data, which now includes:
- For noncompliant resources—the severity of a problem and the time the problem was first discovered
- For exemptions—the creator and approver of the exemption.
- Clarification on values reported—The downloaded report now shows four different rows of values clarifying total resources in violation, number of resources assessed, percentage of noncompliant resources, or percent compliance versus percent noncompliance. These values then are matched with the scorecard’s color legend.
Dynamic links in the Excel download will also take you back into the DivvyCloud tool to the exact location of a particular issue.
Read the updated documentation for the Compliance Scorecard here .
Infrastructure as Code (IaC) Security
DivvyCloud’s IaC Security enables organizations to implement security controls earlier in their CI/CD pipeline (shifting left) and provides an opportunity to address compliance and security concerns before deployment or modifications are made to your cloud infrastructure.
IaC Security allows users to pull in pre-configured infrastructure templates. Templates are analyzed against Insights, with specific feedback about violations, to determine compliance before infrastructure is deployed.
You can find details about this feature in the Infrastructure as Code section of the documentation, beginning with the IAC Overview .
Cloud Parity
Our 20.2 release includes the addition of dozens of filters and actions to improve our overall cloud parity by expanding our support and capabilities for resources within DivvyCloud. These improvements allow our customers additional capabilities around visibility, reporting, and automation. Our enhanced support includes:
For AWS:
- AWS S3 Access Points
- AWS EventBridge
- AWS Glue (esp Settings and Security Configurations)
- AWS Redshift
- AWS Backup Vaults
- AWS SSM (esp Session Manager) Note: Anytime we add Amazon resources, we add EDH support for them as well.
For Azure:
- Service Bus
Read further in these release notes to learn more about the many new filters and actions supporting these resources.
Updated NIST 800-53 Compliance Pack
DivvyCloud’s new NIST 800-53 Compliance Pack now contains over 250 checks that can map to the NIST 800-53 Revision 4 requirements. For complete details on our updated compliance pack, click here .
EDH Enhancements
We’ve restructured how we perform our EDH, reducing overhead on our worker capacity and thereby providing massive performance benefits in our harvesting capability.
We expanded our events by about 20 for this release, providing greater visibility into Lambda, Glue, S3 access points, and EventBridge.
Complete EDH documentation can be found here .
New Permissions Required (20.2)
New Permissions Required
For AWS: “backup:GetBackupVaultAccessPolicy”, “backup:ListBackupVaults”, “ecr:GetLifecyclePolicy”, “events:ListEventBuses”, “glue:GetDataCatalogEncryptionSettings”, “glue:GetResourcePolicy”, “glue:GetSecurityConfigurations”, “rds:DescribeDBClusterParameterGroups”, “rds:DescribeDBClusterParameters”, “rds:DescribeDBParameterGroups”, “rds:DescribeDBParameters”, “s3:GetAccessPointPolicy”, “s3:GetAccessPointPolicyStatus”, “s3:ListAccessPoints”, “ssm:GetDocument”, “wafv2:ListLoggingConfigurations”
For Microsoft Azure: Microsoft.ServiceBus/*/read
More about the new permissions:
- “backup:ListBackupVaults” and “backup:GetBackupVaultAccessPolicy” add visibility, lifecycle, and event-driven harvesting supporting AWS Backup Vaults [ENG-3130].
- “glue:GetDataCatalogEncryptionSettings”, “glue:GetResourcePolicy”, and “glue:GetSecurityConfigurations” support AWS Glue [ENG-2955].
- “rds:DescribeDBClusterParameterGroups” and “rds:DescribeDBClusterParameters” are permissions added in advance of a future release including enhanced support of harvesting of AWS DocumentDB/Neptune Clusters [Eng-3494].
- “rds:DescribeDBParameterGroups” and “rds:DescribeDBParameters” support AWS RDS Instances [ENG-784].
- “s3:GetAccessPointPolicy”, “s3:GetAccessPointPolicyStatus”, and “s3:ListAccessPoints” support the EDH enhancements. [ENG-2017]
- “ssm:GetDocument” supports AWS System Session Manager (SSM) [ENG-990].
- “Microsoft.ServiceBus/*/read” supports visibility into Azure ServiceBus Queues [ENG-3208].
New Resources (20.2)
AWS Backup Vault - We now support AWS Backup Vault, providing visibility and event-driven harvesting (EDH) support for the AWS resource that provides a container in which to organize your backups. You’ll find this resource on the Resources main page under the category ‘Storage’ and the resource type ‘Backup Vault’. [ENG-3130]
AWS EventBridge - We’ve added support for AWS EventBridge, providing visibility, event-driven harvesting (EDH) and lifecycle support for this resource that ‘delivers a stream of real-time data from event sources, such as Zendesk, Datadog, or Pagerduty, and routes that data to targets like AWS Lambda’. You’ll find this resource on the Resources main page under the category ‘Identity & Management’ and the resource type ‘Cloud Event Bus’. [ENG-3007]
AWS Glue - We’ve added support for two AWS Glue–-’a fully managed extract, transform, and load (ETL) service’---resources, specifically AWS Glue Data Catalog and AWS Glue Security Configuration, adding EDH events and filter support for each. Both new resources are found on the Resources main page under the category ‘Storage’; AWS Glue Data Catalog is found under the resource type ‘ETL Data Catalog’, and AWS Glue Security Configuration is found under the resource type ‘ETL Security Configuration’. [ENG-2955]
AWS S3 Access Point - AWS S3 Access Point, a feature of S3 to simplify managing data access at scale for applications using shared data sets on S3, is now supported by filters and actions in the DIvvyCloud tool. This new resource is found on the Resources page under the category ‘Identity & Management’ and the resource type ‘Cloud Access Point’.
Resource Enhancements (20.2)
In Release 20.2, we have added:
-
Visibility into Dynamo DB DAX clusters which do not have encryption at rest enabled. [ENG-2908]
-
Visibility into the KMS key used to encrypt objects in the S3 bucket. [ENG-2652]
-
Enhanced AWS Elastic Beanstalk support. We now store and surface the network, subnet, and security group associations of Elastic Beanstalk applications. [ENG-2507]
-
A new database table, ResourceMatrix, to store the cloud-type-to-divvy-resource-type mapping. [ENG-2454]
-
Support (filters and actions) for S3 Access Points, adding visibility and event driven harvesting support for this resource. This includes two new filters to easily identify misconfigurations with your S3 access points:
Cloud Access Point Allows Public AccessandCloud Access Point Origin. [ENG-2017] -
A filter for Web Application Firewalls that do not have logging enabled. This new filter is
Web Application Firewall Without Logging Enabled. [ENG-2015]
New Actions (20.2)
The new actions added in Release 20.2 are:
-
Tag lifecycle management and visibility for **AWS Elastic Beanstalk **resources from within the tool; web app support to Resource In Network and Resource In Subnet filters. [ENG-3175]
-
The ability to take automated lifecycle actions using Bots against AWS Workspaces. [ENG-3028]
-
Enabling of access logging for AWS classic, application, and network load balancers. [ENG-2982]
-
Lifecycle and automation support for pausing/resuming AWS Redshift clusters. This capability was announced via AWS on March 11th, 2020 via https://aws.amazon.com/about-aws/whats-new/2020/03/amazon-redshift-launches-pause-resume/ . [ENG-2904]
-
Ability to enable the ECR scan on push option for container registries and the ability to trigger a vulnerability scan for container images residing in an AWS container repository. Note that container images can only be scanned once every twenty-four hours. Reference: https://aws.amazon.com/about-aws/whats-new/2019/10/announcing-image-scanning-for-amazon-ecr/ . [ENG-2852]
-
Ability to update the configuration of an Azure web application. New action is “Update Web App Config”. [ENG-2243]
-
Ability to disable specific harvest jobs. For details, read Harvesting Strategies . [ENG-2003]
-
A new lifecycle action to enable AWS VPC Flow Logs from within the tool or using a Bot action. [ENG-988]
New EDH Events/Enhancements (20.2)
The following new EDH events and enhancements have been added in Release 20.2:
-
AWS EDH support for the following Lambda actions [ENG-3159]:
- TagResource20170331
- TagResource20170331v2
- UntagResource20170331
- UntagResource20170331v2
-
Visibility, lifecycle, and event-driven harvesting support AWS Backup Vaults. [ENG-3130]
-
Visibility into AWS Glue ETL Data Catalog and Security Config. EDH events and filter support were added. New permissions are required. [ENG-2955]: EDH Events: ETL Data Catalog: DeleteResourcePolicy PutResourcePolicy PutDataCatalogEncryptionSettings ETL Security Config: CreateSecurityConfiguration DeleteSecurityConfiguration New Filters:
ETA Data Catalog Without EncryptionETA Security Configuration Without EncryptionNew Permissions: “glue:GetDataCatalogEncryptionSettings” “glue:GetResourcePolicy” “glue:GetSecurityConfigurations”
General Enhancements (20.2)
Azure Enhancements (20.2)
- Updated the labels when adding/updating an Azure subscription. [ENG-2816]
- Added support for manipulating Azure Resource Groups as if they were any other cloud resource. This enables customers to perform automation and execute compliance/governance Insights against them from within the tool. [ENG-2522]
- Added the ability to **scan Azure subscriptions **for missing/incomplete permissions. [ENG-2256]
Compliance Scorecard Enhancements (20.2)
- New fields added to scorecard excel export. Customers can now see the following aggregates for each cloud [ENG-3072]:
- Total # of noncompliant resources
- Total # of assessed resources
- % noncompliance
- % compliance
- Added a new column to the compliance scorecard export which includes the Insight severity associated with the control. [ENG-1314]
EDH Enhancements (20.2)
- Enhanced AWS EDH by updating values directly within the database without the need for harvesting. [ENG-3144]
- Added the ability to download a CSV of EDH event history. [ENG-975]
Entitlements (20.2)
- Administrators can now disable entitlements during the user creation process. [ENG-2801]
- Basic users with the admin or editor entitlement for BotFactory can now leverage badges as a scoping mechanism for the Bots. [ENG-2800]
Exemptions (20.2)
- Added the cloud account name and type to the Insight Exemption for additional context. [ENG-3036]
- Added a direct link to the Insight in question when viewing exemptions. [ENG-2848]
GCP Enhancements (20.2)
- Added the ability to enqueue CloudApiHarvest for GCP. [ENG-3062]
Integrations (20.2)
- Removed Old MS Teams Integration: Any bots that were using the old version of the Microsoft Teams integration should be transitioned to use the new webhooks integration before upgrading to 20.2. [ENG-2937]
- Added support for PagerDuty v2 API. [ENG-2560]
- Updated the Splunk integration to support HEC (HTTP Event Collector) as an option for log ingestion. [ENG-958]
Scheduled Events (20.2)
- Added a new archived state for Scheduled Events to hide them from the UI, but retain them for tracking/auditing. [ENG-2896]
- Added the ability to sort scheduled events by the Account that the target resource resides in or the event run time. [ENG-2895]
- Persisted the pagination and sort settings when viewing scheduled events. [ENG-2893]
Other General Enhancements (20.2)
- Reduced calls to the DB while improving the API response time when interacting with the clouds section. [ENG-3058]
- Included the account ID and payer account information when listing cloud accounts from the Resources section of the tool. [ENG-2917]
- Added the last scanned time to the container image view to more easily identify how long it’s been since the first/previous scan. [ENG-2851]
- Improved several names for Storage Container Botfactory actions. [ENG-2814]
- Added the Insight ID (source + auto-incrementing ID) as a column in the CSV download. [ENG-2799]
- Updated email template to include info on password reset link expiration. [ENG-2759]
- Updated ECS naming in resources and created bot pages. [ENG-2734]
- Extended the cloud account nickname field to 255 characters. [ENG-2628]
- Added the ability to view the Created, Modified, and Discovered timestamps in the resources view. [ENG-2503]
- Added support for sorting cloud accounts by the total number of resources. [ENG-2444]
- Renamed insight Storage Container Not Enforcing Encryption At Rest. [ENG-2271]
- Improved and expanded direct links to cloud accounts from a resource - follow up. [ENG-2146]
- Added additional configuration options for SAML. [ENG-2079]
- Added a message (”Everything is great!”) to inform users that all resources are compliant for a specific insight when viewing results by cloud. [ENG-1715]
- Added an info icon next to the “Resource Totals” heading, when hovering display “Data is refreshed daily”. [ENG-72]
New Filters (20.2)
-
API Accounting Target Bucket Without MFA Delete Protection- Identifies AWS CloudTrail resources which are exporting to an S3 bucket without MFA delete in place. [ENG-2910] -
Application Gateway Without Content EncodingandBuild Project Without Logging– new filters for Build Projects without logging and API Gateways without content encoding. [ENG-3206] -
Application Gateway X-Ray Tracing Enabled (AWS Only)andApplication Gateway X-Ray Tracing Disabled (AWS Only)– two new filters for Application Gateway resources that identify the X-Ray tracing configuration value. [ENG-2909] -
Content Delivery Network With Object Storage Origin- Adds visibility into CloudFront/S3 origin linkages. [ENG-2979] -
Distributed Table Cluster Without Encryption- Adds visibility into Dynamo DB DAX clusters which do not have encryption at rest enabled. [ENG-2908] -
DNS Domain Due To Expire Soon- Identifies service domains set to expire which do not have auto-renew enabled. [ENG-3096] -
ETL Data Catalog Without Encryption- Adds visibility into AWS Glue ETL Data Catalog and Security Config. [ENG-2955] -
ETL Security Configuration Without Encryption- Adds visibility into AWS Glue ETL Data Catalog and Security Config. [ENG-2955] -
Instance Associated With Subnet By Name- Identifies compute instances by their associated subnet using regular expressions. Note: this filter looks up the subnet name field and only valid regular expressions will work. [ENG-2790] -
Message Queue Key Reuse Threshold- Identifies AWS SQS resources based on the Key Reuse Period property. [ENG-2768] -
Resource Not Running With Individual Role- Identifies resources that are sharing roles with other resources of the same type. As an example, AWS Lambda functions which are not associated with individual roles. [ENG-2906] -
Resource Using Encryption Key Without Rotation Enabled- Identifies resources that are using CMKs for encryption at rest that do not support key rotation. [ENG-2907] -
Resource With Expiring/Expired SSL Certificate Attached- Identifies Load Balancer and Content Delivery Network resources which are associated with an SSL certificate that’s set to expire. [ENG-2905] -
Resource With Permissive Network Access Rules- Identifies Azure Databases, Cache Instances, Storage Accounts, and Key Vaults with rules which violate the target level of permissiveness. [ENG-3071] -
Serverless Function X-Ray Tracing Disabled (AWS Only)andServerless Function X-Ray Tracing Enabled (AWS Only)- Adds visibility for AWS Lambda X-Ray tracing configurations. [ENG-2755] -
SSL Certificate Is/Is Not In Use- Identifies SSL Certificates that are in use/not in use. [ENG-3095] -
Storage Container Used As CDN Origin- Adds visibility into CloudFront/S3 origin linkages. [ENG-2979] -
Web Application Firewall Without Logging Enabled- Added filter for Web Application Firewalls that do not have logging enabled. [ENG-2015] -
Region Without Valid Session Manager Preferences- Adds visibility into account AWS SSM default preferences, including session encryption, run as user, S3 bucket, and CloudWatch encryption at rest. [ENG-990]
Bug Fixes (20.2)
[ENG-3148] Resolved an issue that was preventing Org admins from creating exemptions.
[ENG-3179] Fixed a bug that prevented the AWS Workspace Computer Name from displaying in the UI.
[ENG-3129] Added text-overflow to the cloud name column to restrict the column width and improve readability.
[ENG-3035] Accounted for cloud scope when summarizing the exemptions within the Insight Library view.
[ENG-2983] Improved S3 bucket policy evaluation for transit encryption enforcement to properly parse IAM policies with a list of resource ARNs which allows for improved accuracy.
[ENG-2891] Routes are now visible within the Resources, Insights, Compliance Scorecard, and BotFactory sections of the product.
[ENG-2885] Fixed a bug where Insights would stop appearing after the 65530th resource in the scorecard export xlsx file. See our notes on scorecard enhancements .
[ENG-2777] Enabled Cloud Advisor Check resource types for automation via BotFactory.
[ENG-2552] Fixed issue where GCP Organization folders were not harvesting correctly and not accurately reflecting as the gcp_folder badge associated with the cloud account. Additionally, the folder value in the gcp_folder badge only represented the immediate parent folder. For example, a project located at folder1/folder2/folder3/my-project would have the badge value of folder3, not the expected folder1/folder2/folder3/my-project. Finally, with the addition of AWS Organization support the badge key has been standardized from gcp_folder to cloud_org_folder.
[ENG-784] Fixed filter “Database Instance With SSL Enforced” not picking up AWS RDS instances.
Divvy Software Release Notice - 20.2.1 Minor Release (05/08/2020) Minor Release 20.2.1 includes the resolution of two issues as follows:
[ENG-3684] Resolved an issue where Jinja2 template validation was failing incorrectly around some Bot configurations.
[ENG-3683] Revised some filtering criteria around the Compliance Scorecard to expand support for up expand support for up to 300 Insights, 60,000 resources, and 500 clouds without an impact to performance. Divvy Software Release Notice - 20.2.2 Minor Release (05/13/2020) DivvyCloud’s Minor Release 20.2.2 consists of several customer-requested enhancements, three new filters, and a handful of bug fixes. As always, contact us at support@divvycloud.com with any questions.
Features (20.2.2)
In release 20.2.2, we have added:
- Visibility into the spot instance configuration for Azure Virtual Machines, Azure Virtual Machine Scale Sets, and AWS Autoscaling Groups. Added Azure support to the filter
Instance Is Spot/Preemptible Instance. The new filter isAutoscaling Group Spot Instance Support. [ENG-3410] - Cloud Access Points to resources in regions filters. [ENG-3629]
- Two new filters,
Application Gateway Without Metrics EnabledandApplication Gateway With Metrics Enabled, to identify Application Gateway resources that have a stage configured without cloud metrics enabled. [ENG-3362] - Sorting of the compliance packs by name in descending view. [ENG-3680]
- Support to AWS EDH that allows users to disable opt-in regions. [ENG-3622]
- Tag visibility and lifecycle support to AWS VPC Flow Logs. [ENG-3458]
- Visibility into IPv4/IPv6 associations of a VPC network. [ENG-3495]
- Visibility into the transit encryption setting for AWS DocumentDB clusters. [ENG-3494]
Resource Enhancements (20.2.2)
- Added visibility into the spot instance configuration for Azure Virtual Machines, Azure Virtual Machine Scale Sets, and AWS Autoscaling Groups. Added Azure support to the filter
Instance Is Spot/Preemptible Instance. The new filter isAutoscaling Group Spot Instance Support. [ENG-3410] - Added visibility into IPv4/IPv6 associations of a VPC network. [ENG-3495]
- Added visibility into the transit encryption setting for AWS DocumentDB clusters. [ENG-3494]
- Added tag visibility and lifecycle support to AWS VPC Flow Logs. [ENG-3458]
Added visibility into AWS Directory Service type with three new filters to query against it:
Directory Service Type,Directory Service Size, andDirectory Service RADIUS Status. [ENG-3564]
General Enhancements (20.2.2)
- Added support to AWS EDH that allows users to disable opt-in regions. [ENG-3622]
- Added region verification to AWS EDH to support disabling opt-in regions. [ENG-3637]
New Filters (20.2.2)
Application Gateway Without Metrics Enabled&Application Gateway With Metrics Enabled- Identify Application Gateway resources that have a stage configured without cloud metrics enabled. [ENG-3362]Autoscaling Group Spot Instance Support- Adds visibility into the spot instance configuration for Azure Virtual Machines, Azure Virtual Machine Scale Sets, and AWS Autoscaling Groups. Added Azure support to the filterInstance Is Spot/Preemptible Instance.[ENG-3410]
In addition, three new filters add visibility into AWS Directory Service type [ENG-3564]:
Directory Service TypeDirectory Service SizeDirectory Service RADIUS Status
Bug Fixes (20.2.2)
[ENG-3703] - Fixed a bug that caused Splunk integration to appear to be configured for new installations/organizations.
[ENG-3654] - Fixed a bug that didn’t properly link EC2 instances which were assigned a dynamic public IP to their corresponding address in the Public IP resources view.
[ENG-3574] - Fixed a bug that prevented users from being able to delete AWS SNS subscription.
[ENG-2653] - Fixed a bug that caused the insight search to break when using the ‘Curate Insight/Bot Exemption’ action. Divvy Software Release Notice - 20.2.3 Minor Release (06/03/2020) DivvyCloud announces Minor Release 20.2.3. This release consists of updated exemptions capabilities, support for Azure Managed SQL Database Instances, improved handling of non-SMTP passwords, as well as new and enhanced filters, and bug fixes.
As always, contact us at support@divvycloud.com with any questions!
20.2.3 New Permissions Required
New Permissions Required
For AWS: “ec2:DescribeVpcEndpointServiceConfigurations”, “ec2:DescribeVpcEndpointServicePermissions”, “ec2:DescribeVpcEndpointConnections”
For Microsoft Azure: “Microsoft.Sql/managedInstances/read”, “Microsoft.Sql/managedInstances/encryptionProtector/read”, “Microsoft.Sql/servers/extendedAuditingSettings/read”
New and Enhanced Features (20.2.3)
-
Updated Exemptions Capabilities, including additional filtering capabilities for Badges, auto-notifications for exemptions that are about to expire, and expanded fields (notes). In addition, the major update is the ability to bulk edit or delete exemptions. Check out our complete documentation here https://docs.divvycloud.com/docs/exemptions . Enhanced features are:
- Added a new Notes field to exemptions. [ENG-3498]
- Added support for bulk editing exemptions. [ENG-3229]
- Implemented Bulk Edit Dialog for Exemptions. [ENG-3228]
- Added support for bulk deleting exemptions. [ENG-3225]
- Added support for filtering exemptions by badges. [ENG-3177]
- Added Email notification for Insight Exemptions which are set to expire within three days. The Email notification will be sent each day until the expiration has expired or the expiration date has been updated. [ENG-2640]
-
Added visibility and filter support for Azure Managed SQL Database Instances. These instances will be included in the Database Instance category of the Resources UI, and a new filter,
Database Instance Is Managed, was added to identify them vs databases which are customer managed. New permissions required are “Microsoft.Sql/managedInstances/read” and “Microsoft.Sql/managedInstances/encryptionProtector/read”. The following existing filters were enhanced to support to Azure:Database Instance Auditing Disabled,Database Instance Threat Detection Enabled, andDatabase Instance Auditing Disabled. [ENG-3407] -
Several items relate to passwords on non-SMTP:
- When resetting a user’s password on an Non-SMTP, configured orgs will get a new temp password dialog instead of the error message. [ENG-3648]
- When creating a new user on an Non-SMTP, configured orgs will get a new temp password dialog instead of the error message. [ENG-3647]
- Added the ability to add and reset a user’s password without SMTP configured. [ENG-3667]
-
Added visibility and and filtering support for AWS ECR Lifecycle Policies. [ENG-3540]
- New Actions: Add Container Registry Lifecycle Policy
- Enhanced Filter: Container Registry Without A Valid Lifecycle Policy
-
Added the ability to put a container registry lifecycle as an action in BotFactory. [ENG-3781]
-
Added additional properties to AWS ACM certificates and allow them to be queried. [ENG-3566]
-
Added support for using SSL to connect to Redis. [ENG-2825]
New EDH Events and Enhancements (20.2.3)
- Expanded the filter
Resource Trusting Unknown Accountto work with Private Images. This now will allow administrators to identify compute images which are shared with accounts outside of the Organization. Event Driven Harvesting support was also added for the ModifyImageAttribute and ResetImageAttribute actions. [ENG-3828] - Added Event Driven Harvesting (EDH) support for AWS ECR, ECS and EKS. [ENG-3545]
New and Enhanced Filters (20.2.3)
The following existing filters were enhanced to provide support to Azure [ENG-3407]:
Database Instance Auditing Disabled
Database Instance Threat Detection Enabled
Database Instance Auditing Disabled
The following filters were added to provide support for the new resource type: Network Endpoint Service. [ENG-3389]
Network Endpoint Service Requiring Acceptance
Network Endpoint Service Not Requiring Acceptance
Network Endpoint Connecting to Unauthorized Service
Database Instance Is Managed - Adds visibility and filter support for Azure Managed SQL Database Instances. [ENG-3407]
MapReduce Cluster Without Logging - Added visibility into the logging URI for Map Reduce Clusters. [ENG-3361]
NAT Gateway Public IP Attachment - Added a new filter to identify NAT Gateway resources based on their public IP association. [ENG-3514]
Region Threat Detection Target Account- This new filter validates Threat Detection configuration at the cloud region level. [ENG-3586]
Resource Is Not Encrypted - This SNS filter was expanded to support Notification Topics. [ENG-3586]
Resource Trusting Unknown Account - This filter was enhanced to work with Private Images. This now will allow administrators to identify compute images which are shared with accounts outside of the Organization. Event Driven Harvesting support was also added for the ModifyImageAttribute and ResetImageAttribute actions. [ENG-3843]
New Action (20.2.3)
“Add Container Registry Lifecycle Policy” - Adds visibility for AWS ECR Lifecycle Policies. [ENG-3540]
New Resource (20.2.3)
- Added support for AWS VPC Endpoint Services as new resource type: Network Endpoint Service. with supported actions: update tags. This new resource type is found on the Resources page under the category Network. [ENG-3389]
Resource Enhancements (20.2.3)
- Now surfacing the Log Group ARN that is associated with API Accounting Configurations in the Resources view. [ENG-3720]
- Added visibility and and filtering support for AWS ECR Lifecycle Policies. [ENG-3540]
- Added visibility and filter support for Azure Managed SQL Database Instances. These instances will be included in the Database Instance category of the Resources UI, and a new filter was added to identify them vs databases which are customer managed. New filter is
Database Instance Is Managed. [ENG-3407] - Added visibility into the logging URI for Map Reduce Clusters. New filter is
MapReduce Cluster Without Logging. [ENG-3361]
General Enhancements (20.2.3)
-
The search string used when browsing the Insight library will now also search the compliance rule(s) associated with the selected Insight Pack. [ENG-3838]
-
We now support role descriptions up to 1024 characters. [ENG-3817]
-
Improved error message handling in data migration logs. [ENG-3758]
-
Updated outputs of IAR CFT/Changeover Workers CFTs now using input Instance Profile. For customers that use get.divvycloud.com/cft/Divvy-CFT-Workers.json to perform upgrades, they should be prepared to provide as an input the name of the Instance Profile their DivvyCloud instances. Prior to this release, the CFT asked for the name of the Role their DivvyCloud instances use for Instance Assume Role permissions and then created an Instance Profile. While Role names and Instance Profile names are often identical, they may not be. You can find the Instance Profile name by examining the Role you use, retrieving its Instance Profile ARN, and using only the name portion of the ARN. The typical format is:
Instance Profile ARN arn:aws:iam::<AWS account number>:instance-profile/<Instance Profile name>[ENG-3746] -
Added an environment variable to update the file extension of the Scorecard zip. [ENG-3721]
-
We have a new redirect when resetting a users password. If the temp password has expired the user will be told to reach out to their administrator. [ENG-3705]
-
You can Auto-Select appropriate Cloud Type for Cloud Specific Packs when filtering against the Compliance Scorecard. [ENG-3672]
-
Changed the styling for the new user and reset password email templates to provide more consistency. [ENG-3650]
-
Added a warning message for users trying to reset their password with an expired reset token. [ENG-3649]
-
Fixed a bug that caused the Provisioning section to appear even when the module was disabled. [ENG-3433]
-
Added a popup on the scorecard page that asks users if they want to repopulate filters with badges if they select a custom pack with badges. [ENG-3249]
-
JSON response for
GET v2/public/insights/packs/selectnow includes the keysbadgesandbadge_filter_operator. When none exists (as is always the case for backoffice packs), the value will be null. [ENG-3233] -
Added new status to IAM cache for fresh install. [ENG-3172]
-
We now send auth server information to DivvyCentral during License harvest. [ENG-1873]
-
Added the ability to include Notes for Bots in the Update Information screen. Notes give you freeform text that can be used to further explain a Bots purpose, why it’s paused, or who to contact in the event of an issue. [ENG-1379]
Bug Fixes (20.2.3)
[ENG-3849] Fixed a bug that prevented customers from overriding the EDH Backoff Interval from the default value.
[ENG-3844] Fixed Non SMTP users reset password workflow not invalidating old password and not focusing the user to reset a new password upon login.
[ENG-3843] Expanded the filter Resource Trusting Unknown Account to work with Private Images. This now will allow administrators to identify compute images which are shared with accounts outside of the Organization. Event Driven Harvesting support was also added for the ModifyImageAttribute and ResetImageAttribute actions.
[ENG-3837] Fixed a bug that prevented the Resource Creator property from being set for IAM Users, Groups, and Roles when EDH is enabled.
[ENG-3827] Hardened Bot creation/modification for basic users to eliminate the possibility of permission escalation.
[ENG-3822] Fixed a bug with resource export that prevented users from searching based on tags, and then exporting.
[ENG-3817] Fixed handling of long role descriptions. We now support descriptions up to 1024 characters.
[ENG-3810] Fixed a bug that caused the Report card “Exempted resources” view to show all resources (compliant or not) when there are no exemptions for selected resource type.
[ENG-3805] The ServiceManagedPolicyHarvester has been converted to run as a processor. This means that Cloud Managed Policy will no longer appear in the Harvest Info list for individual cloud accounts. Harvest information will now be listed under System Administration -> Background Jobs and appear as one background job per cloud type: AWS:ServiceManagedPolicyHarvester, AZURE_ARM:ServiceManagedPolicyHarvester, etc.
[ENG-3800] Fixed a bug that caused harvesting to miss the KMS key association for EMRFS S3 at rest encryption.
[ENG-3761] Fixed a bug in the filter Load Balancer With SSL and HTTP Listener to properly detect load balancers with SSL running on a nonstandard port.
[ENG-3759] Removed duplicate badges from the scorecard dropdown.
[ENG-3748] Updated the API permissions to allow Organization Admins to manage harvesting strategies within their organization. Previously only Domain Admins could perform this functionality.
[ENG-3747] Fixed bug that caused issues with the default harvest strategy when migrating clouds between orgs.
[ENG-3742] Improved our logic for determining incomplete permissions for Azure resource visibility.
[ENG-3739] Added visibility into the RADIUS setting for both small and large AD resources.
[ENG-3736] Fixed a bug that prevented the EDH owner tag from being assigned to S3 buckets which were provisioned via AWS CloudFormation templates.
[ENG-3728] Removed tagging support for Stack Template resource; it is not possible given that CFT tagging must be done at creation of template.
[ENG-3711] Fixed typo in the action “Update log group retention”.
[ENG-3671] Repaired “Database Instance Harvesting Fails” due to unhandled authorization errors; the permission Microsoft.Sql/servers/extendedAuditingSettings/read should be added to the sample Azure standard user policy on the docs site.
[ENG-3575] Restored the ability to delete Route 53 DNS Zones.
[ENG-3572] Restored the ability to schedule deletion for AWS EMR.
[ENG-3569] Removed integration credentials from showing in dev tools.
[ENG-3547] Fixed a bug that caused exempted resources to show on the Scorecard’s Impacted Report Card View.
[ENG-3424] Fixed a bug that prevented Azure Reserved IPs from being harvested.
[ENG-3198] Added a new migration script so that exemptions for BackOffice Insights are scoped to the correct resource type(s).
[ENG-3080] Fixed search input bug for the Trigger Harvest action on the Botfactory page.
[ENG-2564] Restored the ability to sort by tags in the Resource section of the tool.
[ENG-1609] Fixed resource_ids for Azure Data Lake resources so they can associate to Azure resource groups. Divvy Software Release Notice - 20.2.4 Minor Release (06/11/2020) Release 20.2.4 consists of newly added support for AWS Cognito User Pools, enhancements to the Scorecard export and the Scorecard’s Report Card feature, as well as some general enhancements and bug fixes. As always, contact us at support@divvycloud.com with any questions.
New Permissions Required (20.2.4)
New Permissions Required
FOR AWS: “cognito-idp:DescribeUserPool”, “cognito-idp:ListIdentityProviders”, “cognito-idp:ListUserPools”
New Resource (20.2.4)
AWS Cognito User Pool - We now support AWS Cognito User Pool, providing visibility and tagging support for the AWS resource that allows your users to sign in to your web or mobile app through Amazon Cognito. You’ll find this resource on the Resources main page under the ‘Identity & Management’ category and the resource type ‘User Pool’. Note: three new permissions are required: “cognito-idp:DescribeUserPool”, “cognito-idp:ListIdentityProviders”, and “cognito-idp:ListUserPools”. [ENG-3833]
New Action (20.2.4)
Added a new lifecycle action to enable AWS VPC Flow Logs from within the tool or using a Bot action. [ENG-988]
Enhanced Filter (20.2.4)
Encryption Key Origin - This filter was updated to add support for HSM detection for AWS KMS keys. [ENG-3914]
Feature Enhancements (20.2.4)
Report Card Improvements: In the Scorecard Report Card view, if there is an insight scoped to multiple resources, it will have a new dropdown option “all resources” and display noncompliant or exemptions against all instead of defaulting to one. If the report card insight is scoped to 1 resource it will behave the same. Exempt resources are now a slide toggle option. [ENG-3826]
Scorecard Export Improvements:
- Improved performance of Scorecard export; removes heatmap tooltips from Scorecard download. [ENG-3820)
- Increased Insight limits for both insight packs and Scorecard export to 1000; Increased clouds limit in Scorecard export to 1000. [ENG-3861]
General Enhancements (20.2.4)
Allow customers to append an optional suffix to owner/creator tag value. [ENG-3912]
Added support for HSM detection for AWS KMS keys; Updated the Encryption Key Origin filter to support identification of HSM encryption keys. [ENG-3914]
Added a new BotFactory Jinja template resource.get_last_object() which will allow Bot authors to gain access to properties of the last event to further enrich their Bot notification alerts. [ENG-3866]
Clouds Section Changes: Added the ability to download a CSV of the clouds view with optional tags/badges included in the output. [ENG-964]
The search string used when browsing the Insight library now also searches the compliance rule(s) associated with the selected Insight Pack. [ENG-3838]
Bug Fixes (20.2.4)
[ENG-3901]Fixed an edge case that prevented administrators from viewing missing permissions.
[ENG-3851]Fixed an edge case that prevented API Access Keys from being deactivated/activated.
[ENG-3829]Fixed a bug that prevented users from viewing Insight results for Global Insights which span multiple Organizations.
[ENG-3581]Fixed a read replica harvesting bug to allow the Read Replica filter to work after the customer upgrades to 20.2.1.
[ENG-3535]Improved Data Collections CSV import parsing to better handle descriptions.
[ENG-3461]Fixed a bug that did not properly scope Insight packs when viewing summary level information.
[ENG-563] Fixed bug that counts insights and bots that use certain filters across all organizations, allowing clickable columns in Filters Section to scope by Organization. Divvy Software Release Notice - 20.2.5 Minor Release (06/17/2020) This minor release consists of a feature enhancement providing greater visibility into Azure instances, as well as a number of bug fixes.
Feature Enhancement (20.2.5)
We’ve enhanced the visibility of Azure instances by surfacing Azure VM Extensions as a JSON property in the Resource Details view. [ENG-3920]
Bug Fixes (20.2.5)
[ENG-3977] Fixed a bug that prevented S3 versioning from being enabled.
[ENG-3974] Fixed a harvesting bug with Azure Managed SQL Instances.
[ENG-3971] Fixed a bug where ResourceCommon was not being populated when VPC Flow Logs are created from within the tool.
[ENG-3965] Resource_ids for Azure SQL database resources have been changed to include the sql server name to ensure that the resource_ids are unique. This will cause the database resources to be recreated on the next harvest of databases.
[ENG-3964] Exemptions that are in the state “Enabled” will now flip to “Disabled” once the expiration date passes.
[ENG-3951] Fixed a bug that did not take Insight Exemptions into consideration when exploring Insight violations for a specific resource.
[ENG-3899] Fixed a bug related to Network Interface resources for Azure: Network Interface resources for Azure may be recreated on the initial InstanceInterfaceIp harvester run after upgrade due to a change in DivvyCloud resource_ids for those resources to account for case-sensitive storage of case-insensitive values.
[ENG-3787] Fixed a bug that prevented the Row per page from updating.
Fixed several bugs related to dark mode: [ENG-3868] …on the Enable Producers page. [ENG-3782] …on the scorecard page. [ENG-3421] …on the Roles and Entitlements page.
Divvy Software Release Notice - 20.2.6 Minor Release (06/24/2020) Minor release 20.2.6 consists of a handful of bug fixes.
Bug Fixes (20.2.6)
[ENG-4010] Standardized Azure system cloud badges to one type instead of two.
[ENG-3997] Fixed permission issue with Scorecard and Exemptions.
[ENG-3995] Fixed missing permissions for Azure. See updated permissions here .
[ENG-3993]Insight scopes applied at the Insight Library view are now carried forward when drilling down into the Insight to explore the results.
[ENG-3975] Fixed whitespace bug that prevented Azure IPs from being harvested.
[ENG-3538] Increased username character limit to be up to 128 characters.