Jul 07, 2021
DivvyCloud is pleased to announce Minor Release 21.4.6
Latest 21.4 Release
Release Availability
Our latest minor release 21.4.6 is available for hosted customers on Wednesday July 7, 2021. Availability for self-hosted customers is Thursday July 8, 2021 - if you’re interested in learning more about becoming a hosted customer reach out to support@divvycloud.com.
Release Highlights (21.4.6)
DivvyCloud is pleased to announce Minor Release 21.4.6. This minor release includes a new “Cost Containment Pack” that comprises 15 Insights for visibility into areas that are commonly associated with increased costs. We have also added visibility into the multi-region configuration of AWS KMS encryption key and expanded IaC support for multiple AWS services. This release also includes several new or enhanced filters and a number of bug fixes.
In addition, for our add-on Cloud IAM Governance module , we have details around multiple enhancements to the Access Analyzer, as well as a number of bug fixes.
Skip ahead to review the new permissions, details for the general release, and details for Cloud IAM Governance. As always, contact us at support@divvycloud.com with any questions.
Important Messages
Upgrading to Redis 5.x For customers on versions of DivvyCloud prior to 21.4.x, upgrading to DivvyCloud 21.4.x (or higher) earlier versions of Redis may create significant issues - we strongly recommend upgrading to Redis 5.x. Contact support@divvycloud.com with any questions or concerns.
Self-Hosted Customers For self-hosted customers, upgrading to 21.4.0 will require updating the RDS parameter values for various MySQL settings using two options: Terraform and the AWS Console. See Required MySQL parameters for details.
Intelligent Harvesting Updates (AWS-Only) As of 21.4.2 Intelligent Harvesting is now enabled by default for all current harvesting strategies. [ENG-8483].
Depending on the size of your cloud footprint (AWS-Only), migration to 21.4.x may take a bit longer to complete to allow for the implementation of our new intelligent harvesting capabilities. These changes are a recommended default update for greatly improved performance around harvesting behaviors for AWS customers, but can also be disabled if desired.
In addition, as part of the updates around intelligent harvesting we have changed the way the system distributes/queues jobs. While we have tested this exhaustively there may be some scenarios where low priority jobs stack up as a result of capacity issues around your quantity of workers.
If your deployment does not have enough capacity to manage the jobs they may slowly accumulate under the Job Backlog (Low Priority) (these details are viewable under Administration —> System Administration —> System in the System Health panel .)
*Important Note: Some customers may be using job queue spikes as a trigger or indicator to dynamically increase worker capacity. This is an issue to be aware of since the job queue will no longer be operating in the same manner. *
Table of Contents
Major Release 21.4 (05/26/2021) Minor Release 21.4.1 (06/02/2021) Minor Release 21.4.2 (06/09/2021) Minor Release 21.4.3 (06/16/2021) Minor Release 21.4.4 (06/23/2021) Minor Release 21.4.5 (06/30/2021) Minor Release 21.4.6 (07/07/2021)
The following are updates related to enhancements and bug fixes for our commercial add-on Cloud IAM Governance (Access Explorer) module:
Cloud IAM Governance (Access Explorer) - 21.4 Major Release (05/25/2021) Cloud IAM Governance (Access Explorer) - 21.4.2 Minor Release (06/09/2021) Cloud IAM Governance (Access Explorer) - 21.4.3 Minor Release (06/16/2021) Cloud IAM Governance (Access Explorer) - 21.4.4 Minor Release (06/23/2021) Cloud IAM Governance (Access Explorer) - 21.4.5 Minor Release (06/30/2021) Cloud IAM Governance (Access Explorer) - 21.4.6 Minor Release (07/07/2021)
Divvy Software Release Notice - 21.4.0 Major Release (05/26/2021)
New Permissions Required (21.4.0)
New Permissions Required: AWS
For AWS Standard (Read-Only) User: “appsync:GetApiCache”, “appsync:ListGraphqlApis”
For AWS Power User: “appsync:*****”
Note: We recommend our AWS Standard (Read-Only) Users employ AWS’ managed read-only policy, supplemented by a small additional DivvyCloud policy. The benefit of using the AWS managed policy lies in AWS’ continuously updating the policy for new services, making it easier for the customer to attach and maintain the policy. Details on this recommendation can be found at AWS Standard User (read-only) Policy - Option 1.
More on AWS Permissions:
- “appsync:GetApiCache” and “appsync:ListGraphqlApis” - Support AWS AppSync. [ENG-8111]
New Permissions Required: Azure
For Azure Standard (Read-Only) User: “Microsoft.Network/frontDoors/read” “Microsoft.Network/privateEndpoints/read”
More on Azure Permissions:
- “Microsoft.Network/frontDoors” - Supports Azure Front Door. [ENG-7540]
- “Microsoft.Network/privateEndpoints/read” - Supports Azure Private Endpoint. [ENG-5997]
User Interface Changes (21.4.0)
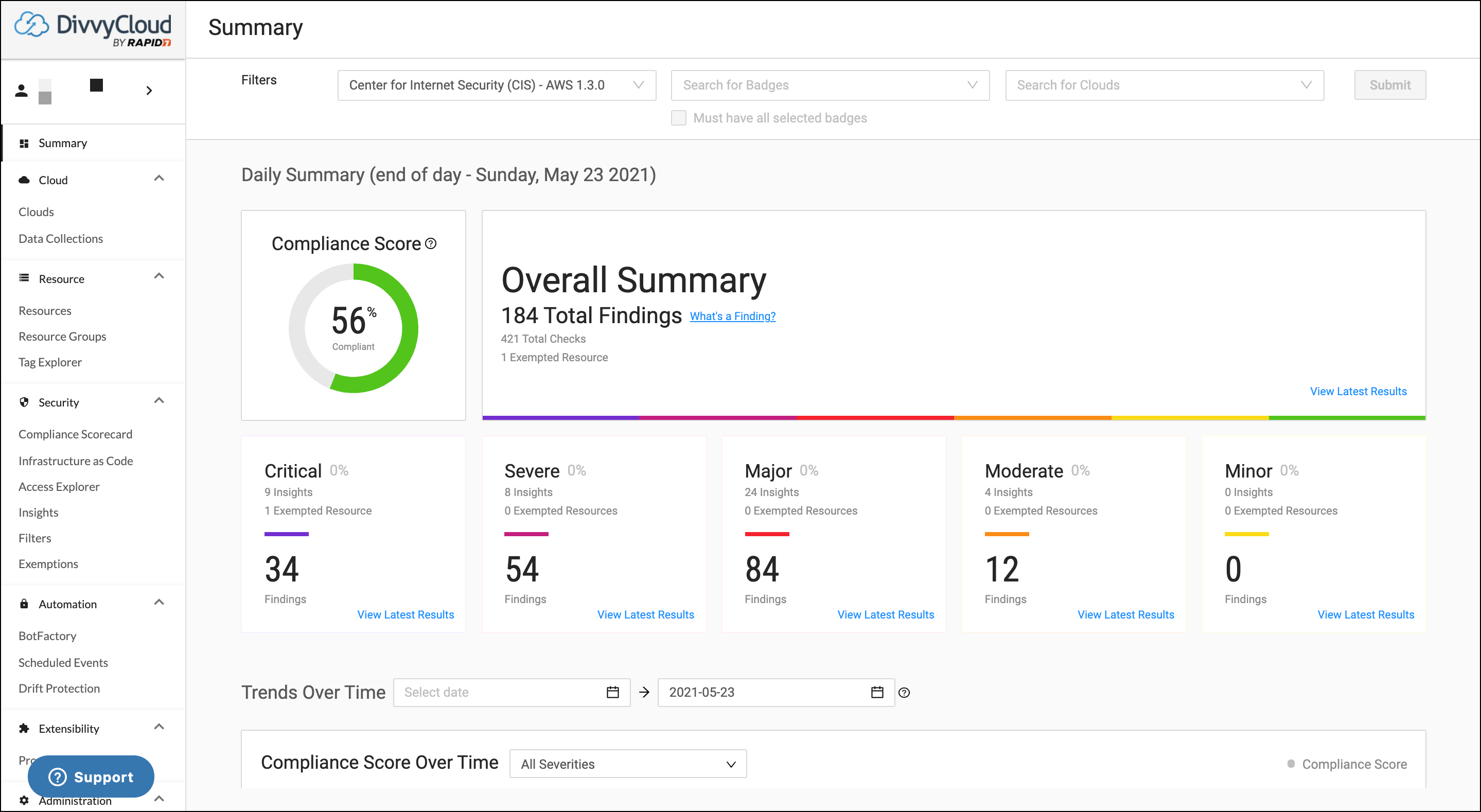
Summary Page As a part of our ongoing effort to improve user experience, we have made several improvements to our homepage (now known as the Summary Page), including:
- Drill-down to the view latest available data through the Compliance Scorecard
- Filter data to a specific date or a date range
- View data beyond 90 days
- Review your overall compliance score and scores divided by individual severity
- Improved performance and loading times
Review the complete documentation here .
Other User Interface Updates
- Added new refresh logs button on JIT sync model. Admins can now refresh logs on modal via this button. [ENG-6632]
- The “Pods/Task Definitions” resource type is now separated to form 2 different resource types—”Pods” and “Task Definitions”— under the Container resource category. [ENG-6125]
- Updated the Bots Listing Page, Bot Action Menu, and Bot Creation process to revise terminology in the product [ENG-4654]:
- In the Bot Creation wizard, the word “Conditions” and “Add Conditions” have been changed to “Filters” and “Add Filters”.
- In the Bot Listing Page and on the Bot detail page under actions, the word/action “Resume” has been replaced by “Enable”.
- Container Image vulnerabilities can now be sorted by their severity when viewing them in the Resources section. [ENG-8065]
Features & Enhancements (21.4.0)
Just-in-time (JIT) User Provisioning 21.4 includes support for Just In-Time (JIT) user provisioning through Active Directory and Azure Active Directory. We have also added support for mapping multiple auth server groups to one DivvyCloud group and added support for preserving client secrets/passwords for Azure AD and AD in the auth server configurations. [ENG-6148]
To review our full documentation on JIT check out the summary page for the feature. Sub pages in this section of the documentation provide detailed instructions on configuration for the options we support.
CloudFormation Template Scanning Support As a part of our ongoing improvements to our IaC security capability, we have added support for CloudFormation templates. This addition will enable customers to scan their CloudFormation infrastructure templates prior to deploying in their AWS environment. Given the widespread use of CloudFormation for building infrastructure, this addition to Terraform is a significant enhancement to our IaC shift-left security capability. Details on our IAC Security capabilities are available here .
**NIST Cybersecurity Framework (CSF) Pack ** DivvyCloud’s new NIST Cybersecurity Framework (CSF) Pack includes DivvyCloud Insights that can map to the NIST CSF requirements. This pack is important for organizations that are required to align with the NIST Cybersecurity Framework (CSF) and includes 455 different Insights. Refer to summary page for complete details.
AWS
- Added visibility and Infrastructure-as-Code support for AWS AppSync, enabling management and updates of mobile app data in real-time between devices and the cloud, and allowing apps to interact with the data on the mobile device when it is offline. New Permissions required: “appsync:GetApiCache” and “appsync:ListGraphqlApis”. This new resource can be found under the Storage category as the new resource type GraphQL API. [ENG-8111]
- Added a new filter
Cache Instance Endpoint Port (AWS)to identify memcache instances/clusters running on nonstandard ports. Supported for memcache_instance in AWS, AWS GovCloud, AWS China. [ENG-8044] - Added a new filter
Cloud User/Role Console Login Within Thresholdthat can be used on installations with AWS Event Driven Harvesting (EDH) in place to identify users/roles which access the provider console within a defined threshold. [ENG-8113] - Added visibility into the option groups that are associated with AWS RDS, Neptune and DocumentDB clusters/instances. [ENG-7937]
- Improved Terraform IaC analysis with additional properties for EKS clusters, ELB/ALBs and EBS Snapshots. [ENG-8152]
- Added Terraform Infrastructure-as-Code (IaC) scanning support for Elastic IPs. [ENG-8031]
AZURE
- Added support for Azure Front Door, Azure’s global, scalable entry-point that uses the Microsoft global edge network to create fast, secure, and widely scalable web applications. New permission required: “Microsoft.Network/frontDoors”. New filters:
Global Load Balancer Without Web Application Firewall Protection,Global Load Balancer Without Session Affinity Enabled,Global Load Balancer With Health Probes Enabled,Global Load Balancer Without Routing Rule Accepted Protocol Set To HTTPS, andGlobal Load Balancer Without Routing Rule Forwarding Protocol Set To HTTPS. Azure Front Door can be found under the Network category as the new resource type Global Load Balancer. [ENG-7540, ENG-7541] - Added support for “Azure Private Endpoint”, Azure’s network interface that connects you privately and securely to a service powered by Azure Private Link. This resource is under the Network category as a Network Endpoint resource type. A new permission is required: “Microsoft.Network/privateEndpoints/read”. [ENG-5997]
- Expanded support for the filter **
Resource Encrypted With Key**to include Azure resources. [ENG-8222]
GCP
- Added visibility, harvesting, and IaC support for GCP Cloud Armor, a DDoS defense service and WAF that helps defend internet facing applications from distributed attacks and exploitation attempts. This resource can be found in the Network category as a Web Application Firewall resource type.
- New filters for this resource are
Load Balancer With/Without Cloud Armor Policy (GCP)andWeb Application Firewall With Allow Default Rule Policy, which applies to AWS and GCP. - Updated Filters to support GCP Cloud Armor are
Web Application Firewall Rule Count,Web Application Firewall Orphaned, andWeb Application Firewall Without Logging Enabled. [ENG-7476, ENG-7477, ENG-7478]
- New filters for this resource are
MULTI-CLOUD/GENERAL
- Added new refresh logs button on JIT sync model. Admins can now refresh logs on modal via this button. [ENG-6632]
- The “Pods/Task Definitions” resource type is now separated to form 2 different resource types—”Pods” and “Task Definitions”—under the Container resource category. [ENG-6125]
- Expanded our Jinja2 support to include
today()andutcnow(). Both can be used viaevent.get_date()andevent.get_timestamp()Jinja2 functions respectively. These functions, in combination with a tagging strategy, can be used to provide context such as indicating when a resource was tagged with time-relevant keys, e.g., “Owner notified of impending delete”, “30 day exemption granted”, etc. [ENG-8070] - Improved performance of the /v2/public/entitlements/set API. [ENG-7888]
- Under this change only domain admins can add cloud orgs. All other non-domain admins will not see the “Add Organization” button in the Clouds section of the app. [ENG-7965]
- Added three new query filters [ENG-7992]:
Container Repository- AWS and Kubernetes - Matches containers on their repository values.Container With Unknown Repository- AWS and Kubernetes - Matches containers where repository values are empty (NULL).Container Repository Hosted By Known/Unknown Cloud Account (AWS)- AWS ONLY - Matches AWS containers whose repository URL is in the form{account_id}.dkr.ecr.{region}.amazonaws.comand we have an organisation_service with the same{account_id}.
- Three filter names were updated to clarify their function (and for clarity). [ENG-8257]
Resources (21.4.0)
AWS
- Added visibility and Infrastructure-as-Code support for AWS AppSync, enabling management and updates of mobile app data in real-time between devices and the cloud, and allowing apps to interact with the data on the mobile device when it is offline. New Permissions required: “appsync:GetApiCache” and “appsync:ListGraphqlApis”. This new resource can be found under the Storage category as the new resource type GraphQL API. [ENG-8111]
AZURE
- Added support for Azure Front Door, Azure’s global, scalable entry-point that uses the Microsoft global edge network to create fast, secure, and widely scalable web applications. New permission required: “Microsoft.Network/frontDoors”. New filters:
Global Load Balancer Without Web Application Firewall Protection,Global Load Balancer Without Session Affinity Enabled,Global Load Balancer With Health Probes Enabled,Global Load Balancer Without Routing Rule Accepted Protocol Set To HTTPS, andGlobal Load Balancer Without Routing Rule Forwarding Protocol Set To HTTPS. Azure Front Door can be found under the Network category as the new resource type Global Load Balancer. [ENG-7540, ENG-7541] - Added support for “Azure Private Endpoint”, Azure’s network interface that connects you privately and securely to a service powered by Azure Private Link. This resource is under the Network category as a Network Endpoint resource type. A new permission is required: “Microsoft.Network/privateEndpoints/read”. [ENG-5997]
GCP
- Added visibility , harvesting, and IaC support for GCP Cloud Armor, a DDoS defense service and WAF that helps defend internet facing applications from distributed attacks and exploitation attempts. This resource can be found in the Network category as a Web Application Firewall resource type. New filters for this resource are
Load Balancer With/Without Cloud Armor Policy (GCP)andWeb Application Firewall With Allow Default Rule Policy, which applies to AWS and GCP. Updated Filters to support GCP Cloud Armor areWeb Application Firewall Rule Count,Web Application Firewall Orphaned, andWeb Application Firewall Without Logging Enabled. [ENG-7476, ENG-7477, ENG-7478]
MULTI-CLOUD
- The “Pods/Task Definitions” resource type is now separated to form 2 different resource types—”Pods” and “Task Definitions”—under the Container resource category. [ENG-6125]
Actions (21.4.0)
GCP
- Added a standard Delete Bot action for GCP Cloud Armor. [ENG-7479]
Insights (21.4.0)
AZURE
Access List Flow Log Retention Less Than 90 Days (Azure)- Identifies NSG Flow Logs with retention periods less than 90 days.Access List Invalid Diagnostic Logging Configuration (Azure)- Matches the resource without the proper diagnostic configuration.Container Registry With Azure Defender Disabled- Identifies cloud accounts that have Defender disabled for the selected resources.Container Registry With Invalid Diagnostic Logging Configuration (Azure)- Matches the resource without the proper diagnostic configuration. _- **
Database Instance With Azure Defender Disabled**- Identifies cloud accounts that have Defender disabled for the selected resources. Database With Azure Defender Disabled- Identifies cloud accounts that have Defender disabled for the selected resources.- **
DNS Zone With Azure Defender Disabled**- Identifies cloud accounts that have Defender disabled for the selected resources. - **
Encryption Key Vault With Azure Defender Disabled**- Identifies cloud accounts that have Defender disabled for the selected resources. _ Instance With Azure Defender Disabled- Identifies cloud accounts that have Defender disabled for the selected resources.Load Balancer With Invalid Diagnostic Logging Configuration (Azure)- Matches the resource without the proper diagnostic configuration.Logic App With Invalid Diagnostic Logging Configuration (Azure)- Matches Logic App resources without the proper diagnostic configuration.Network With Invalid Diagnostic Logging Configuration (Azure)- Matches the resource without the proper diagnostic configuration. _- **
Serverless Function Invalid Diagnostic Logging Configuration (Azure)**- Matches the resource without the proper diagnostic configuration. - **
Storage Container With Azure Defender Disabled**- Identifies cloud accounts that have Defender disabled for the selected resources. - **
Web App With Azure Defender Disabled**- Identifies cloud accounts that have Defender disabled for the selected resources.
Filters (21.4.0)
AWS
- **
Cache Instance Endpoint Port (AWS)**- New filter identifies Memcache instances/clusters running on nonstandard ports. Supported for memcache_instance in AWS, AWS GovCloud, AWS China. [ENG-8044] Cloud User/Role Console Login Within Threshold- New filter can be used on installations with AWS Event Driven Harvesting (EDH) in place to identify users/roles which access the provider console within a defined threshold. [ENG-8113]Container Repository Hosted By Known/Unknown Cloud Account (AWS)- AWS ONLY - Matches AWS containers whose repository URL is in the form{account_id}.dkr.ecr.{region}.amazonaws.comand we have an organisation_service with the same{account_id}. [ENG-7992]
AZURE
- **
Global Load Balancer With Health Probes Enabled**- New filter supports Azure Front Door. [ENG-7540, ENG-7541] - **
Global Load Balancer Without Routing Rule Accepted Protocol Set To HTTPS**- New filter supports Azure Front Door. [ENG-7540, ENG-7541] - **
Global Load Balancer Without Routing Rule Forwarding Protocol Set To HTTPS**- New filter supports Azure Front Door. [ENG-7540, ENG-7541] - **
Global Load Balancer Without Session Affinity Enabled**- New filter supports Azure Front Door. [ENG-7540, ENG-7541] - **
Global Load Balancer Without Web Application Firewall Protection**- New filter supports Azure Front Door. [ENG-7540, ENG-7541] - **
Resource Encrypted With Key**- Enhanced the existing filter to include Azure resources. [ENG-8222]
GCP
Load Balancer With/Without Cloud Armor Policy (GCP)- New filter supports visibility and harvesting for GCP Cloud Armor. [ENG-7476, ENG-7477]Web Application Firewall Orphaned- Filter updated to include support for GCP Cloud Armor. [ENG-7476, ENG-7477]Web Application Firewall Rule Count- Filter updated to include support for GCP Cloud Armor. [ENG-7476, ENG-7477]Web Application Firewall Without Logging Enabled- Filter updated to include support for GCP Cloud Armor. [ENG-7476, ENG-7477]
MULTI-CLOUD/GENERAL
Container Repository- AWS and Kubernetes - Matches containers on their repository values. [ENG-7992]- **
Container With Unknown Repository**- AWS and Kubernetes - Matches containers where repository values are empty (NULL). [ENG-7992] Web Application Firewall With Allow Default Rule Policy- This new filter, created to support GCP Cloud Armor Policy, applies to both AWS and GCP. [ENG-7476, ENG-7477]- The following filter names were updated to clarify their function (and for clarity) [ENG-8257]:
- **
Storage Container With Policy Encryption**renamed fromStorage Container Encrypted Storage Container With Default Server Side Encryptionrenamed fromStorage Container With Default Encryption- **
Storage Container Without Default Server Side Encryption**renamed fromStorage Container Without Server Side Encryption Enabled
- **
Bug Fixes (21.4.0)
AWS
- [ENG-8112] Fixed a bug that would conditionally apply a duplicate suffix to EDH events for the creator record.
- [ENG-8034] Fixed a bug that would skip DocumentDB clusters from being scanned during IaC analysis.
- [ENG-8032] Fixed a bug that would not scan secondary EBS volumes that are attached to AWS EC2 instances during IaC analysis.
AZURE
- [ENG-6691] Fixed a bug that would leave stale Azure Resource Groups in the installation when the parent cloud was removed from the tool.
GCP
- [ENG-8268] Fixed a harvesting issue that resulted in not seeing all GCP Storage Buckets for projects that had over 200 in a single project.
- [ENG-8118] Fixed an attribute error for a missing API. A new google API is required: “https://cloud.google.com/service-usage/docs/reference/rest” . The service endpoint is: “https://serviceusage.googleapis.com” .
- [ENG-6745] Fixed a bug involving stack trace for unauthorized errors with GCP; added optional environment variable ‘DIVVY_LOG_UNAUTHORIZED_ERRORS’ for including a stack trace with such errors.
MULTI-CLOUD/GENERAL
- [ENG-8114] Fixed a bug that prevented Kubernetes Pod, Ingress, Service and Namespace resources from being fully utilized within BotFactory.
- [ENG-8085] Fixed Back Button to work as intended on Resources Screen.
- [ENG-7816] Fixed a bug in /v3/public/resource/query endpoint to return data for resource group resource type.
- [ENG-6692] Fixed: Cloud accounts which are onboarded using Cloud Organizations can no longer be moved to new tenants within the product. Cloud IAM Governance (Access Explorer) Updates - 21.4.0 Major Release (05/26/2021)
** The following updates are related to enhancements and bug fixes for our commercial add-on Cloud IAM Governance (Access Explorer) module.**
Contact us at support@divvycloud.com with any questions.
Cloud IAM Governance Features & Enhancements (21.4.0)
- Implemented better handling of principals and resources with certain kinds of malformed policies attached. We now log the error but continue analyzing that principal or resource based on any correctly formed policies. IAM users who have malformed policies may see new effective access results that were previously obscured by errors. [ENG-7784]
- Some resource/policy names are too long to display in the policy stack navigator. This enhancement provides a mechanism by which the user can view the full long subject name by hovering on the cutoff (with ellipsis) text. [ENG-7251]
- Optimized the organization of the Policy Stack on the Effective Access screen for maximum usability. [ENG-7247]
Cloud IAM Filters (21.4.0)
AWS
Resource Specific Policy With No Conditions (AWS)- New query filter for Cloud IAM governance only. [ENG-7135]
Important Note on Cloud IAM Governance Filter
The filter above requires the implementation of the Parallel Cache Build and whitelisting of accounts .
Cloud IAM Governance Bug Fixes (21.4.0)
- [ENG-7627] Fixed bug in handling resource policies with star :star2: actions.
- [ENG-7626] Fixed and improved handling of malformed resource policies. Divvy Software Release Notice - 21.4.1 Minor Release (06/02/2021) Minor release 21.4.1 includes an enhanced Insight, several new filters, and a handful of bug fixes, including some improvements to our Major Release 21.4.
Features & Enhancements (21.4.1)
AWS
- Added new filters for the Graph API resource (AWS AppSync) [ENG-8376]:
Graph API Without X-Ray Tracing Enabled (AWS)Graph API With/Without Caching Enabled (AWS)Graph API Without At Rest Encryption Enabled (AWS)Graph API Without Transit Encryption Enabled (AWS)Graph API Logging Configuration (AWS)
MULTI-CLOUD/GENERAL
- We have expanded the filter
Instance Lifecycle Stateto support many types of compute resources and their different states. As such, the filter is now calledResource Lifecycle State. Specifically, we have added support for the following resources to the filter: App Server, Broker Instance, Database Cluster, Database Migration Instance, Elasticsearch Instance, Hypervisor, Logic App, Machine Learning Instance, Spanner, and Stream Instance. [ENG-8271] - Updated the Insight Findings tab of the resource property panel to allow direct linking to the Insight in question. [ENG-8416]
- The Insight
Network With No Instances, which identifies networks with zero instances, now supports Azure and GCP.
Insights (21.4.1)
MULTI-CLOUD/GENERAL
Network With No Instances- This Insight, which identifies networks with zero instances, now supports Azure and GCP.
Filters (21.4.1)
AWS
Graph API Logging Configuration (AWS)- Supports the Graph API resource (AWS AppSync). [ENG-8376]Graph API With/Without Caching Enabled (AWS)- Supports the Graph API resource (AWS AppSync). [ENG-8376]Graph API Without At Rest Encryption Enabled (AWS)- Supports the Graph API resource (AWS AppSync). [ENG-8376]Graph API Without Transit Encryption Enabled (AWS)- Supports the Graph API resource (AWS AppSync). [ENG-8376]Graph API Without X-Ray Tracing Enabled (AWS)- Supports the Graph API resource (AWS AppSync). [ENG-8376]
MULTI-CLOUD/GENERAL
Resource Lifecycle State- This filter was expanded from the filterInstance Lifecycle Stateto support many types of compute resources and their different states. Specifically, we have added support for the following resources to the filter: App Server, Broker Instance, Database Cluster, Database Migration Instance, Elasticsearch Instance, Hypervisor, Logic App, Machine Learning Instance, Spanner, and Stream Instance. [ENG-8271]
Bug Fixes (21.4.1)
MULTI-CLOUD/GENERAL
- Fixed an issue where high availability (HA) scheduler was taking over before the main scheduler finished the database upgrade. [ENG-8385]
- Resolved an issue for customers with InsightVM (IVM) integration to fix an IVM data retrieval error that was preventing data from displaying. [ENG-8305] Divvy Software Release Notice - 21.4.2 Minor Release (06/09/2021) Minor Release 21.4.2 includes expanded Terraform AWS Infrastructure-as-Code (IAC) support, added visibility into the availability zones that are configured for AWS Elasticsearch instances, and additional details from harvesting MSK (AWS Managed Streaming Service for Apache Kafka) instances. We’ve added two new filters for Azure Route Tables and enhanced 4 additional filters related to Azure subscriptions. This release also contains two new Insights, several enhancements to the User Interface, and a couple of bug fixes. As always, contact us at support@divvycloud.com with any questions.
User Interface Changes (21.4.2)
- Updated the Microsoft Teams logo. [ENG-7595]
Features & Enhancements (21.4.2)
AWS
- Expanded Terraform AWS IaC support for aws_iam_role_policy and aws_iam_group_policy resources which convert to inline policies. This is important for customers who want to ensure that inline policies are not being implemented for their users. [ENG-8450]
- Added visibility into the availability zones that are configured for Elasticsearch instances as well as a new filter to identify ones based on a certain threshold. New filter
Elasticsearch Instance Availability Zone Countidentifies Elasticsearch Instances based on the number of availability zones. Supported in: AWS, AWS Gov, and AWS China. [ENG-8307] - Added the stream_version and enhanced_monitoring properties for resource comparison when harvesting MSK (AWS Managed Streaming Service for Apache Kafka) instances. [ENG-8269]
- Added resource properties to the UI and added ability to identify specific subnets of Redshift cluster uses. [ENG-6442]
AZURE
- Added two new filters for Azure Route Tables:
Route Table With Propagation Enabled (Azure)andRoute Table Without Propagation Enabled (Azure). [ENG-8298] - Filters
Cloud Policy With Owner Access to Subscription (Azure)andCloud User With Owner Access (Azure)now support not-actions. Two additional filters,Cloud User With Read Access (Azure)andCloud User With Write Access (Azure), were updated to support the new harvesting format, but do not yet support not-actions. (Not-actions support for these two filters will be available at a later date.) [ENG-6367] - Note: Due to a change in harvesting format, the first four filters listed below will not work until the ‘AZURE_ARM:ServiceManagedPolicyHarvester’ job and ‘AzureArmIdentityDetailHarvester’ harvester have run. Users can wait for the next harvest cycle to complete, or they can manually run that harvester through the UI:
- Administration → System Administration → Background Jobs → AZURE_ARM:ServiceManagedPolicyHarvester’ → ENQUEUE NOW
- Clouds → select Azure Cloud → Harvest Info → search for ‘AzureArmIdentityDetailHarvester’ → ENQUEUE NOW
MULTI-CLOUD/GENERAL
- Dynamic harvesting (or Intelligent Harvesting) is now enabled by default for all current Harvesting Strategies. Refer to the “Intelligent Harvesting Updates” note in the Release Highlights callout. [ENG-8483]
- Added the ability to configure compliance exports across DivvyCloud Organizations to a central S3 bucket. This capability is available via a feature flag upon request. Contact us at support@divvycloud.com with any questions and/or for instructions on how to enable this capability. [ENG-8355]
- Added a new filter,
Resource Compute Type, that identifies resources by the cloud- and resource-specific type of compute instance they use, e.g., ml.t2.medium, t3.medium.elasticsearch, etc. The filter can be used to identify compliance issues, e.g., if an App Server is not using a premium server type, operational issues, e.g., resources that are using end-of-life compute types, and cost savings, e.g., help assess whether the purchase of reserved instances would be useful. [ENG-7982] - Added Data Collections to the functionality of
Resource Name Regular Expression Exclusion (Regex). Of note, Regular Expression queries are more expensive than most, so adding multiple values to the filter will delay results. [ENG-6316]
Insights (21.4.2)
Instance Not Exporting To Log Analytics Workspace (Azure)- This new Insight identifies Instances that are not exporting logs to a Log Analytics Workspace.- **
Web Application Firewall Orphaned**- This enhanced Insight now supports GCP. - **
Web Application Firewall Without Logging Enabled**- This enhanced Insight now supports GCP.
Filters (21.4.2)
AWS
Elasticsearch Instance Availability Zone Count- This new filter supports added visibility into the availability zones that are configured for Elasticsearch instances, identifying Elasticsearch Instances based on a threshold number of availability zones. Supported in: AWS, AWS Gov, and AWS China. [ENG-8307]
AZURE
Note on Azure Filtering
Due to a change in harvesting format, the first four filters listed below will not work until the ‘AZURE_ARM:ServiceManagedPolicyHarvester’ job and ‘AzureArmIdentityDetailHarvester’ harvester have run. Users can wait for the next harvest cycle to complete, or they can manually run that harvester through the UI:
- Administration → System Administration → Background Jobs → ‘AZURE_ARM:ServiceManagedPolicyHarvester’ → ENQUEUE NOW
- Clouds → select Azure Cloud → Harvest Info → search for ‘AzureArmIdentityDetailHarvester’ → ENQUEUE NOW
Cloud Policy With Owner Access to Subscription (Azure)- Filter enhanced to support not-actions. See also note in callout. [ENG-6367]Cloud User With Owner Access (Azure)- Filter enhanced to support not-actions. See also note in callout. [ENG-6367]Cloud User With Read Access (Azure)- This filter was updated to support the new harvesting format but does not yet support not-actions. (Not-actions support for this filter will be available at a later date.) See also note in callout. [ENG-6367]Cloud User With Write Access (Azure)- This filter was updated to support the new harvesting format but does not yet support not-actions. (Not-actions support for this filter will be available at a later date.) See also note in callout. [ENG-6367]Route Table With Propagation Enabled (Azure)- New filter supports Azure Route Tables. [ENG-8298]Route Table Without Propagation Enabled (Azure)- New filter supports Azure Route Tables. [ENG-8298]
MULTI-CLOUD/GENERAL
- **
Resource Compute Type**- This new filter identifies resources by the cloud- and resource-specific type of compute instance they use, e.g., ml.t2.medium, t3.medium.elasticsearch, etc. The filter can be used to identify compliance issues, e.g., if an App Server is not using a premium server type, operational issues, e.g., resources that are using end-of-life compute types, and cost savings, e.g., help assess whether the purchase of reserved instances would be useful. [ENG-7982] Resource Name Regular Expression Exclusion (Regex)- This filter was modified by adding Data Collections to its functionality. Of note, Regular Expression queries are more expensive than most, so adding multiple values to the filter will delay results. [ENG-6316]
Bug Fixes (21.4.2)
AWS
- [ENG-8348] Fixed a bug where AWS ELB listeners were not being properly modeled during Terraform IaC analysis.
MULTI-CLOUD/GENERAL
- [ENG-6460] Updated Bot filtering capabilities prevent unsupported resources from surfacing during search/auto-complete during Bot creation. Cloud IAM Governance (Access Explorer) Updates - 21.4.2 Minor Release (06/09/2021)
** The following updates are related to enhancements and bug fixes for our commercial add-on Cloud IAM Governance (Access Explorer) module.**
Contact us at support@divvycloud.com with any questions.
Cloud IAM Governance Features & Enhancements (21.4.2)
- Updated layout on the Effective Access (EA) screen. [ENG-8224]
- UI fine-tuning of the EA page; specifically targeted the computed access section (on the right), which now has updated tabs and table. [ENG-8382]
- Added Organizational Unit harvesting status to the System Health section of the System Settings. [ENG-7874]
Cloud IAM Governance Filters (21.4.2)
21.4.2 includes **five ** Cloud IAM Governance filters. Some of the filters listed below were launched in earlier releases (revised names, release version(s), and original names have been specified below).
Principal has Wildcard Access to Services with Denied Actions Count below Threshold (AWS)- Released in 21.3.0 as
Identity Resource Principal Has Any Actions On Service (AWS)
- Released in 21.3.0 as
Principal has Effective Access to Services with Allowed Actions Count above Threshold (AWS)- Released in 21.3.0 as
Identity Resource Principal With Effective Wildcard Access On Service Or Action (AWS)
- Released in 21.3.0 as
Principal has Effective Wildcard Access to Resources (AWS)- Released in 21.3.4 as
Identity Resource Principal With Effective Wildcard Access On Resource (AWS)
- Released in 21.3.4 as
Resource Specific Policy With No Conditions (AWS)- Released in 21.4.0
Resource Specific Policy With / Without Specific Conditions (AWS)- Released in 21.4.2
Important Note on Cloud IAM Governance Filters
All of the filters listed above require the implementation of the Parallel Cache Build and whitelisting of accounts .
Cloud IAM Governance Bug Fixes (21.4.2)
- [ENG-8084] Fixed a bug where navigating to the EA page, opening the cache status widget, and clicking on either “view cache build logs” or “download debug data” caused unintended navigation.
- [ENG-8081] Fixed a display bug with the policy viewer in Firefox. Divvy Software Release Notice - 21.4.3 Minor Release (06/16/2021) Minor Release 21.4.3 includes enhanced visibility into the resource configuration options for AWS Config, as well as EDH support for AWS Workspaces which allows customers to surface changes more rapidly while reducing their overall API usage. We’ve added two new filters: one supporting AWS Secure Sockets Layer (SSL) Certificate status and one that identifies resources not associated with targeted autoscaling groups. We have also improved an existing filter to better assist in identifying when a particular cloud role was last used. In addition, this release contains a revised Center for Internet Security (CIS) - AWS 1.4.0 Compliance Pack, two revisions to the User Interface, several general enhancements, and a couple of bug fixes. As always, contact us at support@divvycloud.com with any questions.
New Permissions Required (21.4.3)
New Permissions Required: AWS
For AWS Standard (Read-Only) Policy: “redshift:DescribeClusterSubnetGroups”
Note: We recommend our AWS Standard (Read-Only) Users employ AWS’ managed read-only policy, supplemented by a small additional DivvyCloud policy. The benefit of using the AWS managed policy lies in AWS’ continuously updating the policy for new services, making it easier for the customer to attach and maintain the policy. Details on this recommendation can be found at AWS Standard User (read-only) Policy - Option 1.
More on New AWS Permissions
- “redshift:DescribeClusterSubnetGroups” supports the ability to identify specific subnets of Redshift cluster uses, a feature added in 21.4.2. [ENG-6442]
User Interface Changes (21.4.3)
- Hid non “latest release” packs on new Divvy installations and Legacy unused packs. [ENG-8470]
- Added a dedicated column to the Filters page (Core Insights) that tracks the count of core Insights that are using a particular filter. This column includes a linked count that enables users to view the Insights in question. [ENG-8521]
Features & Enhancements (21.4.3)
Center for Internet Security (CIS) - AWS 1.4.0 Pack The new Center for Internet Security (CIS) - AWS 1.4.0 Pack is a group of Insights that align with newly updated AWS CIS 1.4.0 Benchmarks. The CIS Benchmarks provide prescriptive guidance for configuring security options for a subset of Amazon Web Services with an emphasis on foundational, testable, and architecture agnostic settings. Refer to the summary page for additional details.
AWS
- Added visibility into the resource configuration options for AWS Config. These new properties will allow customers to validate that AWS Config is set up the correct way. [ENG-8520]
- Included the status property in AWS ACM certificates. Added ability to filter on status using new filter
SSL Certificate Status (AWS). [ENG-8519] - Added EDH support for Workspaces, allowing customers to surface changes more rapidly while reducing their overall API usage. [ENG-8414]
MULTI-CLOUD/GENERAL
- Added an option to the filter
Cloud Role Last Usedto enable an exact match instead of a threshold. [ENG-8625] - Added a dedicated column to the Filters page (Core Insights) that tracks the count of core Insights that are using a particular filter. This column includes a linked count that enables users to view the Insights in question. [ENG-8521]
- Added a new filter
Instance Not Associated With Target Autoscaling Groupto return instances which are not associated with any autoscaling group, or those that do not match the specified Autoscaling Group name. [ENG-7034]
Filters (21.4.3)
AWS
SSL Certificate Status (AWS)- This new filter allows filtering on the status property in AWS ACM certificates. [ENG-8519]
MULTI-CLOUD/GENERAL
Cloud Role Last Used- This filter was modified by adding an option to enable an exact match instead of a threshold. [ENG-8625]Instance Not Associated With Target Autoscaling Group- New filter returns instances which are not associated with any autoscaling group or those that do not match the specified Autoscaling Group name. [ENG-7034]
Bug Fixes (21.4.3)
AWS
- [ENG-8655] Fixed an AWS SQS EDH issue.
- [ENG-8604] Fixed an edge case where an IAM role can have both inline policies along with its IAM assume role policy. Inline policies were overwriting the IAM policy document and causing confusion amongst our customers. This fix resolves the issue.
- [ENG-8596] Fixed an issue where Containers associated with ECS Task Definitions might incorrectly show an error that the associated Pod has been scheduled for deletion.
MULTI-CLOUD/GENERAL
- [ENG-8628] Fixed a bug with Terraform IaC analysis that resulted in Insight Exemption Rules not processing for RDS database instances.
- [ENG-8622] This change fixes an edge case that prevents Bots from being updated due to the inability to select one or more resource types.
- [ENG-8580] Fixed an issue where an overly long container version caused harvesting to fail.
- [ENG-8337] Resolved an issue where the log line did not show the Container ID in the previous version. Cloud IAM Governance (Access Explorer) Updates - 21.4.3 Minor Release (06/16/2021)
The following updates are related to enhancements and bug fixes for our commercial add-on Cloud IAM Governance (Access Explorer) module.
Contact us at support@divvycloud.com with any questions.
Cloud IAM Governance Features & Enhancements (21.4.3)
- Significantly reduced loading time of large data sets on the Resources tab in Access Explorer; sorting now limited to “Name” column only. [ENG-8124]
- Added the display of a warning banner for the scenario where there are harvesting issues with Organization structure (for IAM licensed customers only). Text: “Unable to properly harvest Org Structure. This may prevent accurate Effective Access Analysis.” [ENG-7875]
Cloud IAM Governance Bug Fixes (21.4.3)
- [ENG-8571] Fixed a checkbox display bug in the Policy Navigator of the Principal Explorer (was called the Effect Access view). Divvy Software Release Notice - 21.4.4 Minor Release (06/23/2021) Minor Release 21.4.4 features added visibility and lifecycle support for AWS’ Systems Manager Documents (SSM Documents). It also includes two User Interface updates, one new filter, two modified filters, and a couple of bug fixes. As always, contact us at support@divvycloud.com with any questions.
New Permissions Required (21.4.4)
New Permissions Required: AWS
For Commercial AWS Standard (Read-Only) User Policy: “ssm:DescribeDocumentPermission”, “ssm:GetServiceSetting”, “ssm:ListDocuments”, “ssm:ListDocumentVersions”
For AWS GovCloud Standard (Read-Only) User Policy: “ssm:List*****”
Note: We recommend our AWS Standard (Read-Only) Users employ AWS’ managed read-only policy, supplemented by a small additional DivvyCloud policy. The benefit of using the AWS managed policy lies in AWS’ continuously updating the policy for new services, making it easier for the customer to attach and maintain the policy. Details on this recommendation can be found at AWS Standard User (read-only) Policy - Option 1 .
More on New AWS Permissions
- “ssm:DescribeDocumentPermission”, “ssm:GetServiceSetting”, “ssm:ListDocuments”, and “ssm:ListDocumentVersions” are needed for the added visibility and lifecycle support for AWS Systems Manager Documents. [ENG-8430]
User Interface Changes (21.4.4)
- Changed tooltip to display as ”Search for badge key or badge value. Limit of 100 results displayed.” Also updated max dropdown display to match. [ENG-6738]
- Revised the URL for the revised Summary Page (formerly the Dashboard). This page was renamed in 21.4.0 but the URL update was not applied until this release. Refer to the following URL for documentation details: https://docs.divvycloud.com/docs/summary-landing-page . (Note this URL has also been updated in the product version 21.4.4.) [ENG-8494]
Features & Enhancements (21.4.4)
AWS
- Added visibility and lifecycle support for AWS Systems Manager Documents. This new Compute resource is named ‘SSM Document’. New permissions required are: “ssm:DescribeDocumentPermission”, “ssm:GetServiceSetting”, “ssm:ListDocuments”, and “ssm:ListDocumentVersions” for the AWS commercial Standard User (Read-Only) policy, and “ssm:List*” for the AWS GovCloud Standard User (Read-Only) policy. Additional information can be found in this article . [ENG-8430]
- Improved the efficiency of the filter
Cloud Role Using Policy With Negation Key (AWS)to increase the speed of the query at enterprise scale. [ENG-8706] - Updated the filter
Resource Trusting Unknown Accountto take into consideration the AWS managed accounts for Redshift logging. [ENG-8671]- Additional Redshift references for these accounts are:
MULTI-CLOUD/GENERAL
- Updated the
**Storage Container HTTP Redirect** filter to catch ‘none’ protocol, and added newStorage Container Has Redirectfilter to find all buckets with a redirect configured. [ENG-8364] - Enhanced the performance for the External Data Source feature. [ENG-8556]
Resources (21.4.4)
AWS
- Added visibility and lifecycle support for AWS Systems Manager Documents. This new Compute resource is named ‘SSM Document’. New permissions required are: “ssm:DescribeDocumentPermission”, “ssm:GetServiceSetting”, “ssm:ListDocuments”, and “ssm:ListDocumentVersions” for the AWS commercial Standard User (Read-Only) policy, and “ssm:List*” for the AWS GovCloud Standard User (Read-Only) policy. Additional information can be found in this article . [ENG-8430]
Filters (21.4.4)
AWS
**Cloud Role Using Policy With Negation Key (AWS) **- Improved the efficiency of this existing filter to increase the speed of the query at enterprise scale. [ENG-8706]
MULTI-CLOUD/GENERAL
Storage Container Has Redirect - New filter finds all buckets with a redirect configured. [ENG-8364]
Storage Container HTTP Redirect - Updated filter to catch ‘none’ protocol. [ENG-8364]
Bug Fixes (21.4.4)
AZURE
- [ENG-8259] Fixed an issue where extensions referenced by custom name rather than name were not found by filters that look at extensions (
Instance Or Autoscaling Group Has Unapproved Extension Installed (Azure),Instance Or Autoscaling Group Missing Required Extensions (Azure)), as the Azure portal often displays extensions with their custom name by default.
MULTI-CLOUD/GENERAL
- [ENG-8507] Fixed an issue where a scheduler restart was needed for some changes in the harvesting strategy.
- [ENG-8377] Fixed issue where “Post Request To URL By Tag Value” for a Bot wasn’t recorded in the history table. The system will now record the “when” and the content of the response.
Cloud IAM Governance (Access Explorer) Updates - 21.4.4 Minor Release (06/23/2021)
The following updates are related to enhancements and bug fixes for our commercial add-on Cloud IAM Governance (Access Explorer) module.
Contact us at support@divvycloud.com with any questions.
Cloud IAM Governance Features & Enhancements (21.4.4)
- Made performance improvements to the Access Explorer load times. [ENG-7834] Divvy Software Release Notice - 21.4.5 Minor Release (06/30/2021) Minor Release 21.4.5 includes added Resource Access Policy support for AWS Elastic File System (EFS), which requires one new permission. We’ve added support for AWS Cost and Usage Report, expanded Infrastructure-as-Code (IaC) support to include Azure Front Door, added pagination support for several Alibaba Cloud resource types, and includes two IAM Security Packs (with and without Access Explorer requirements). This release also includes several improvements to the User Interface, and numerous bug fixes. As always, contact us at support@divvycloud.com with any questions.
New Permissions Required (21.4.5)
New Permission Required: AWS
FOR AWS Standard (Read-Only) Users: “elasticfilesystem:DescribeFileSystemPolicy”
Note: We recommend our AWS Standard (Read-Only) Users employ AWS’ managed read-only policy, supplemented by a small additional DivvyCloud policy. The benefit of using the AWS managed policy lies in AWS’ continuously updating the policy for new services, making it easier for the customer to attach and maintain the policy. Details on this recommendation can be found at AWS Standard User (read-only) Policy - Option 1 .
MORE ON NEW AWS PERMISSION
- “elasticfilesystem:DescribeFileSystemPolicy” - Needed for the added Resource Access Policy support for EFS. [ENG-8514]
User Interface Changes (21.4.5)
- Added a multi-selection dropdown to
Resource Orphanedfilter to choose resources to which the filter applies. [ENG-8633] - Updated the Harvesting Status table to be more explicit about the status of each harvesting job. Customers can now see a status of
SuccessorErrorto indicate the last status of the harvest job and sort by that column. [ENG-8696] - Updated the Edit Scorecard Subscription form for improved performance and visualization. Clarified form field descriptions, added radio buttons to clarify frequency field selections. [ENG-8232]
Features & Enhancements (21.4.5)
ALIBABA
- Added pagination support for several Alibaba Cloud resource types. [ENG-8750]
AWS
- Added Resource Access Policy support for Elastic File System (EFS). New permission required: “elasticfilesystem:DescribeFileSystemPolicy”. [ENG-8514]
- Added support for AWS Cost and Usage Report. Check out the documentation on this report. [ENG-3082]
AZURE
- Added IaC support for Azure Front Door. [ENG-7543]
MULTI-CLOUD/GENERAL
- Added ability for customers to modify a system setting for IaC scans when adding Insights to a pack that contain an existing IaC scan. By default, IaC scan results are set to Fail when a resource does not pass an Insight. That result can be changed to Warn Only or Pass if desired when creating an IaC scan configuration. [ENG-7268]
- When creating IaC scan configurations, customers can use Insight Packs from DivvyCloud or their own custom packs. If they use a custom pack and then add an Insight to that custom pack, that Insight will be verified during subsequent IaC scans. Since, by default, the IaC scan results are set to Fail when a resource does not pass an Insight, new scans using that configuration will fail if the new Insight fails.
- The new system setting allows customers to change that behavior so that by default scan results are set to Warn Only or Pass when a resource does not pass an Insight.
- Added two new Compliance Packs for IAM Security. The first, “IAM Security (with Access Explorer)”, includes a total of 44 Insights, with three Insights that are included with our Cloud IAM Governance - Access Explorer add-on module, and as such, will require licensing for that module. The second pack, “IAM Security (without Access Explorer)”, includes 41 Insights, all of the same Insights included in the original pack, but omits the three Insights that require licensing for the Cloud IAM Governance (Access Explorer) add-on module. Allowing customers that may not have the module access to DivvyCloud’s out-of-the-box compliance pack for IAM Security. Check out the IAM Security Packs feature page for more information.
- Added pagination for several resources, assuring harvesting of all resources. [ENG-8686]
New Resources (21.4.5)
- Added support for AWS Cost and Usage Report. Check out the documentation on this report. [ENG-3082]
Filters (21.4.5)
MULTI-CLOUD/GENERAL
- ‘Resource Orphaned’ - Modified this filter to add a multi-selection menu from which to choose resources to which the filter applies. [ENG-8633]
Bug Fixes (21.4.5)
AWS
- [ENG-8788] Fixed an issue where the structure of new AWS instance types was causing the
AWS:InstanceFlavorHarvesterjob to fail. - [ENG-8778] Fixed an issue where not having an AWS account number can result in some harvests failing unexpectedly.
- [ENG-8762] Fixed an error in EDH lifecycle.
- [ENG-8291] Fixed a bug involving API Accounting Config Bot actions on AWS GovCloud. Added us-gov-east-1 and us-gov-west-1 to list of regions supporting this AWS GovCloud action.
AZURE
- [ENG-8722] Fixed an issue where Azure database instances using the “Deny public network access” configuration might be incorrectly flagged as being publicly accessible.
MULTI-CLOUD/GENERAL
- [ENG-8540] Fixed a small bug around creating Insights with
Identity Resource Contains Invalid Actions. - [ENG-7835] Fixed container version being displayed as ‘latest’ when image used has a digest hash but no tag.
Cloud IAM Governance (Access Explorer) Updates - 21.4.5 Minor Release (06/30/2021)
The following updates are related to enhancements and bug fixes for our commercial add-on Cloud IAM Governance (Access Explorer) module.
Contact us at support@divvycloud.com with any questions.
Cloud IAM Governance Features & Enhancements (21.4.5)
- This update makes the 3-dot ellipsis menu visible for locked packs so that the user can “Toggle Pack Visibility” on locked packs. [ENG-8510]
- Allow sorting by the number of allowed actions or allowed services for IAM Roles and Users on the core Resources page. [ENG-8359] Divvy Software Release Notice - 21.4.6 Minor Release (07/07/2021) Minor Release 21.4.6 includes a new “Cost Containment Pack” that comprises 15 Insights for visibility into areas that are commonly associated with increased costs. We have also added visibility into the multi-region configuration of AWS KMS encryption key and expanded IaC support for multiple AWS services. This release also includes several new or enhanced filters and a number of bug fixes. As always, contact us at support@divvycloud.com with any questions.
New Permissions Required (21.4.6)
New Permissions Required: AWS
For AWS Standard (Read-Only) Users: “ecs:DescribeServices”, “ecs:ListServices”
Note: We recommend our AWS Standard (Read-Only) Users employ AWS’ managed read-only policy, supplemented by a small additional DivvyCloud policy. The benefit of using the AWS managed policy lies in AWS’ continuously updating the policy for new services, making it easier for the customer to attach and maintain the policy. Details on this recommendation can be found at AWS Standard User (read-only) Policy - Option 1.
MORE ON NEW AWS PERMISSIONS
- “ecs:DescribeServices” and “ecs:ListServices” fix a bug with visibility on containers spun by AWS ECS Fargate Services. [ENG-7745]
User Interface Changes (21.4.6)
- Added the cloud provider display name next to the icon when listing harvesting strategies. This avoids confusion where providers use the same icon across commercial, Gov, or China clouds. [ENG-8702]
Features & Enhancements (21.4.6)
- “Cost Containment Pack” - This new Insight pack comprises 15 Insights that can help give you visibility into areas that are commonly associated with driving up costs for your organization. You can read more about this pack here .
AWS
- Added visibility into the multi-region configuration of an AWS KMS encryption key; new filter
Encryption Key Multi Region Configuration (AWS)identifies KMS keys based on the value of the property. [ENG-8732] - Expanded Terraform IaC support to AWS SNS Subscriptions and AWS API Gateway IAM Policies. [ENG-8870]
- Added IAC support for AWS Secret, AWS SFTP Server, and AWS Systems Manager Parameter Store Parameter. [ENG-7750]
- Reworked the filter
Instance Uses Simple Networking (EC2 Classic)to be more performant at enterprise scale. [ENG-8834] - Added new Filter
Instance Image Owner Account (AWS)to identify instances that are using the provided account ID’s images. [ENG-8648] - Added new filter
Shared File System Auditing Configuration (AWS)to check if audit logging is enabled/disabled for windows FSX on AWS. [ENG-8578]
MULTI-CLOUD/GENERAL
- Improved the performance of the Tag Explorer page when multiple tag keys are used. [ENG-8784]
- Added more information about hookpoints to the Bot creation wizard to clarify what each event does. Added a new Resource Threat Finding Discovered event that will trigger on resources when services (such as AWS GuardDuty) identify threats/malicious usage against them. [ENG-1527]
Filters (21.4.6)
AWS
Encryption Key Multi Region Configuration (AWS)- New filter matches encryption keys in AWS based on their multi-region configuration. [ENG-8732]Instance Image Owner Account (AWS)- New filter identifies instances that are using the provided account ID’s images. [ENG-8648]Instance Uses Simple Networking (EC2 Classic)- This filter was modified to be more performant at enterprise scale. [ENG-8834]Shared File System Auditing Configuration (AWS)- New filter checks if audit logging is enabled/disabled for Windows FSX on AWS. [ENG-8578]
Bug Fixes (21.4.6)
AWS
- [ENG-8885] Fixed an issue where an AWS Kendra Search Index failed to harvest if no description had been given.
- [ENG-7745] Fixed a bug with visibility on containers spun by AWS ECS Fargate Services. New permissions are required: “ecs:DescribeServices” and “ecs:ListServices”.
MULTI-CLOUD/GENERAL
- [ENG-8391] IAC Scans page now shows the correct number of IAC Configurations when the page is loaded.
- [ENG-8301] Removed duplicate ‘Date Created’ in the drop down menu in the UI.
- [ENG-8210] Fixed an edge case that resulted in false negatives for the Insight
Database Instance Not Enforcing Transit Encryption. Specifically, the false negatives would manifest for RDS PostgreSQL, Neptune, and DocumentDB resources. - [ENG-7685] Fixed a bug with dependencies with Workspaces.
Cloud IAM Governance (Access Explorer) Updates - 21.4.6 Minor Release (07/07/2021)
The following updates are related to enhancements and bug fixes for our commercial add-on Cloud IAM Governance (Access Explorer) module.
Contact us at support@divvycloud.com with any questions.
Cloud IAM Governance Features & Enhancements (21.4.6)
- Multiple enhancements to the Analyzer [ENG-8544]:
- Updated handling of Service Control Policy (SCP) Hierarchy, including conditional support
- Updated handling of unbounded actions
- Added support for
NotPrincipalin resource policies and trust policies - Various bug fixes
- Added support for
NotPrincipalin resource policies in the analyzer. [ENG-8207] - Improved handling of malformed policies in the analyzer. [ENG-7661]
Cloud IAM Governance Bug Fixes (21.4.6)
- [ENG-8035] Fixed a bug in which a principal named in the resource policy was not found if the principal had no attached identity policies but belonged to a group that did have identity policies.
- [ENG-7636] Fixed a bug in SCP handling in the analyzer.
- [ENG-6848] Fixed a bug in our evaluation of
*in the Action element of identity policies when no*was present in the maximum boundaries established by service control policies and/or permission boundaries. IAM users that use these permission boundaries or SCPs will now see more accurate analysis of*actions allowed in identity policies. - [ENG-5341] Fixed a bug in explicit denial of actions in SCPs.