Apr 26, 2022
InsightCloudSec is pleased to announce Major Release 22.3.0
InsightCloudSec Software Release Notice - 22.3.0 Major Release (04/27/2022)
Our latest Major Release 22.3.0 is available for hosted customers on Wednesday, April 27, 2022. Availability for self-hosted customers is Thursday, April 28, 2022. If you’re interested in learning more about becoming a hosted customer, reach out through our Customer Support Portal .
Release Highlights (22.3.0)
InsightCloudSec is pleased to announce Major Release 22.3.0. This release includes an update to our global navigation, specifically around design and organization to better align with Rapid7 branding. This release provides a new container image vulnerability assessment (CVA) capability, available for all SaaS customers. 22.3.0 also includes expanded support for IaC AWS Serverless Application Model (SAM) Resources. Release 22.3.0 also includes ten updated Query Filters, six new Query Filters, five updated Insights, one updated Bot action, one new Bot action, and 15 bug fixes.
For our Cloud IAM Governance module, we have details around three bug fixes.
Contact us through the new unified Customer Support Portal with any questions.
Permissions (22.3.0)
Permissions:AWS
We have revised our supplemental AWS policy to remove sqs:ReceiveMessage from our deny permissions, as this permission is required to harvest events for EDH.` [ENG-15969]
Note: We recommend our AWS commercial (non-GovCloud) Standard (Read-Only) Users employ AWS’ managed read-only policy, supplemented by a small additional InsightCloudSec policy. The benefit of using the AWS managed policy lies in AWS’ continuously updating the policy for new services, making it easier for the customer to attach and maintain the policy. Details on this recommendation can be found at AWS IAM Policies Standard User (Read-Only) AWS-managed supplemental policy.
Features & Enhancements (22.3.0)
New Container Vulnerability Assessment (CVA) now GA for SaaS Customers Beginning with 22.3.0 a new container image vulnerability assessment (CVA) capability is available for GA for all SaaS customers . CVA is designed to continuously audit running deployments to identify new software vulnerabilities. CVA assesses containers across services including Kubernetes environments using IVM and Snyk vulnerability databases. Vulnerability findings are presented in InsightCloudSec or automatically reported/exported allowing users to zoom in on riskiest assets by focusing on business segments such as deployed workloads and applications. Check out our press release on CVA from March here . [ENG-14327]
GENERAL ENHANCEMENTS
- Added a setting to automatically enable APIs for projects when adding a Google Cloud organization. [ENG-15859]
- Updated remaining mentions of ‘Azure Security Center’ to ‘Microsoft Defender for Cloud’. [ENG-15813]
- Removed unnecessary labels, such as “Expensive Filter”, in Bot Factory. [ENG—15811]
- Just-in-time (JIT) provisioning of Users now supports special characters (except for
/and\) for user names and user groups. [ENG-15707] - Updated the tag filters
Parent Resource Contains Tag KeyandParent Resource Contains Tag Key/Value Pairto leverage aliases which will prevent join issues. [ENG-15655] - We have changed how we handle deleted users in our system. We retain Deleted Users so that it is possible to reconstruct which users took which actions when examining the API activity. This update makes it possible to restore Deleted Users as active users and preserves the ability to examine users in API activity whether active or deleted. [ENG-15419, ENG-15910]
- Organization Admins can now view, create, modify, and delete cloud configurations that are defined at the domain level. [ENG-12157]
- Added button to apply 24 hour (1440 minutes) harvesting times on strategies. Note: if applied to an existing strategy with cloud accounts using it. times will take affect upon 2nd harvest. 1st harvest will use prior scheduled time. [ENG-4078]
- Improved the confirmation dialog when removing Insights from Custom Insight Packs. [ENG-15587]
- Customers can now configure more than one Slack Webhook URL in the Integrations part of the product. [ENG-15381]
User Interface Changes (22.3.0)
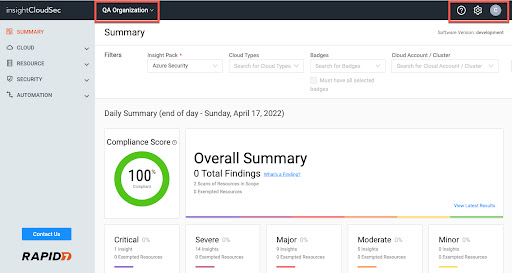
With 22.3.0 InsightCloudSec is pleased to include an update to our global navigation. Note that no items have been renamed and the changes are specific to design and organization.
These changes* include the following:
- The system displays the current Organization (top nav bar, right of the logo) and allows you to select a new Organization from the drop-down.
- New Icons on the top right provide access to:
- Documentation & Release Notes (question mark)
- All Administration options (previously the last category on the left nav, now under the gear)
- Access to your profile, organizations, and log out options (your username initial)
*Changes related to Organizations will only be available to users with the appropriate permissions. [ENG-14739]
Resources (22.3.0)
AWS
- Added harvesting for additional properties for AWS MapReduce clusters, specifically
TerminationProtected,VisibleToAllUsers,MasterPublicDnsName, andLogEncryptionKmsKeyId. Also added a new action to enable/disable termination protection, “Toggle Map Reduce Cluster Termination Protection”. [ENG-15652]
AZURE
- Added tag filter support for Azure Data Factory. [ENG-14979]
Insights (22.3.0)
AZURE
Cluster With Microsoft Defender for Cloud Disabled- Enhanced Insight to work with Azure China. Updated remediation steps. [ENG-15774]Container Registry With Microsoft Defender for Cloud Disabled- Enhanced Insight to work with Azure China. Updated remediation steps. [ENG-15774]Instance With Microsoft Defender for Cloud Disabled- Enhanced Insight to work with Azure China. Updated remediation steps. [ENG-15778]Microsoft Defender your Cloud Standard Pricing Tier Not Selected- Enhanced Insight to work with Azure China. Updated remediation steps. [ENG-15778]
MULTI-CLOUD/GENERAL
Serverless Function Not Within Private Network- Insight renamed toServerless Function not Limited to Private Network Resourcesand description updated for clarity. [ENG-15835]
Query Filters (22.3.0)
AWS
Container Cluster Without Associated Load Balancers- New Query Filter identifies AWS ECS/Fargate clusters which are not behind a load balancer. [ENG-15624]Instance Uses Simple Networking- Updated Query Filter to work the same across all supported resource types. [ENG-15957]Resource Encrypted With Provider Default Keys- Expanded Query Filter to work with AWS Elasticache instances. [ENG-15857]
GCP
Resource Associated With Google Kubernetes Engine- New Query Filter identifies instance/volume resources that are/are not associated with GKE. [ENG-9605]
MULTI-CLOUD/GENERAL
-
Cache Instance Doesn’t Enforce Encryption at Rest- Updated core Insight to filter out Memcached instances, as they do not support encryption at rest. [ENG-15950] -
Cloud Provider Resource ID In List- Expanded Query Filter to work with two resource types that are ICS-specific, Cloud Accounts and ICS Resource Groups, by using their account ID and name, respectively. [ENG-15891] -
Content Delivery Network With/Without Region Specific Geo Restriction Allow- New Query Filter finds Content Delivery Networks with/without specified region allow list. [ENG-15646] -
Content Delivery Network With/Without Region Specific Geo Restriction Block- New Query Filter finds Content Delivery Networks with/without specified region block list. [ENG-15646] -
Encryption Key Customer Managed- New Query Filter finds Encryption Keys that are or are not customer managed. [ENG-15852] -
Identity Resource Contains Invalid Actions- Modified Query Filter now includes thenot inoption. [ENG-15849] -
Instance With InsightVM Agent Last Assessment ThresholdandInstance With Tenable.io Agent Last Checkin Threshold- Updated Query Filters support “after” comparisons in addition to “before” comparisons. An “after” comparison would show instances that are active within a recent time period. [ENG-15897] -
Network Size At Most- Enhanced Query Filter by adding a newExact Matchoption. [ENG-15723] -
Resource Contains Multiple Tag Keys And Value Regular Expressions (Regex)- New Query Filter finds resources based on their tag key and tag value using regular expressions. Tags can be inclusions or exclusions and can be used with OR statements. [ENG-9562] -
Resource Search- Updated this Query Filter to include an optional ‘Exact Match’ boolean. When enabled, this option will convert from a LIKE (~) statement to an EQUAL (=) statement for exact matching. [ENG-15666] -
Serverless Function Does Not Leverage Private Networking- Query Filter renamed toServerless Function Not Limited To Private Network Resourcesand description updated for clarity. [ENG-15835]
Infrastructure as Code (IaC) New Support (22.3.0)
Initial Support for IaC Scanning of AWS Serverless Application Model (SAM) Resources Added initial support for IaC scanning of AWS SAM resources for CFT covering:
- AWS::Serverless::Api
- AWS::Serverless::Function
- AWS::Serverless::HttpApi
- AWS::Serverless::SimpleTable
- AWS::Serverless::StateMachine
Added CFT support for AWS::StepFunctions::StateMachine resources and updated CFT schema models to the latest version (from 28.0.0 to 62.0.0). Note: Not supported are AWS::Serverless::LayerVersion and AWS::Serverless::Application. [ENG-15089]
Bot Actions (22.3.0)
-
“Toggle Map Reduce Cluster Termination Protection” - New action to enable/disable termination protection for AWS Map Reduce Clusters. [ENG-15652]
-
“Disable Storage Container Logging” - Expanded this action from specific S3 buckets under Resource Properties to include Bot actions. This expansion allows a more systematic approach to disabling S3 bucket logging. [ENG-16000]
Bug Fixes (22.3.0)
-
[ENG-15985] Fixed a bug in AWS StorageGateway harvesting.
-
[ENG-15983] Fixed an issue to allow User state to persist on the Resources page after applying Query Filters from the Query Filters blade.
-
[ENG-15882] Fixed a bug that prevented tags from being changed for AWS Transcription Jobs.
-
[ENG-15858] Ensures that all Azure SDK clients are instantiated with the correct Azure cloud-specific resource manager base_urls and requests the correct credential_scopes when calling the endpoints for the client.
-
[ENG-15837] Fixed a bug that would result in select AWS RDS engines being flagged as not supporting transit encryption.
-
[ENG-15836] Fixed a bug where the wrong version number was being sent to AWS when retrieving SSM Documents.
-
[ENG-15755] Fixed an error around users attempting to download when there are no results in the compliance report card.
-
[ENG-15687] GCP jobs which result in API rate limiting will now surface the correct error in the
Harvest InfoUI. -
[ENG-15676] Fixed an issue that prevented InsightCloudSec from properly refreshing Azure credentials.
-
[ENG-15670] Fixed a bug where the table alias was improperly referenced, resulting in incorrect numbers being returned.
-
[ENG-15657] Fixed a bug where the ARNs of AWS StorageGateways were incorrectly harvested.
-
[ENG-15647] Fixed a bug with parsing the
direct_internet_accessboolean during IaC CFT scanning. -
[ENG-15106] Fixed an issue breaking the parser; modified logic to the CFT parser to add the missing Value attribute to incomplete resource tags.
-
[ENG-13499] Fixed a bug that prevented users from downloading resource detail properties.
-
[ENG-13357] Hardened daily scheduled events against skipped days.
Cloud IAM Governance (Access Explorer) Updates - 22.3.0 Major Release (04/27/2022)
** The following updates are related to enhancements and bug fixes for our Cloud IAM Governance (Access Explorer) capabilities.**
Contact us at Customer Support Portal with any questions.
Cloud IAM Governance Bug Fixes (22.3.0)
- [ENG-15565] Fixed an issue with incorrect formatting of XLSX exports from the Access Explorer.
- [ENG-15467] Fixed a bug in Access Explorer that switched the boolean values for “Tag” and “Perm” in the cache (the results of which are displayed in the permissions table).
- [ENG-15020] Resolved an issue in Access Explorer where searching for an application that no longer existed produced an empty applications grid on any subsequent searches.