Aug 02, 2022
InsightCloudSec is pleased to announce Minor Release 22.4.4
InsightCloudSec Software Release Notice - 22.4.4 Minor Release (08/03/2022)
Our latest Minor Release 22.4.4 is available for hosted customers on Wednesday, August 3, 2022. Availability for self-hosted customers is Thursday, August 4, 2022. If you’re interested in learning more about becoming a hosted customer, reach out through our Customer Support Portal .
Release Highlights (22.4.4)
InsightCloudSec is pleased to announce Minor Release 22.4.4. This Minor Release includes updates to performance for Basic User Roles where large quantities of cloud accounts are configured, improved browsing through the Insight Report view, and added visibility to four resources (three in AWS and one in GCP).
In addition, 22.4.4 includes one updated Insight, one new Insight, seven updated Query Filters, seven new Query Filters, and six bug fixes.
-
For our Cloud IAM Governance module we have relocated the LPA settings view to the main settings menu in navigation and consolidated the details for this feature. We have also added the Principal Activity panel to two resource types and renamed this view from User Activity to Principal Activity. Scroll to the lower half of this page for details around these changes.
-
Contact us through the unified Customer Support Portal with any questions.
New Permissions Required (22.4.4)
New Permissions Required: GCP
The following new permissions are required for GCP:
“securitycenter.sources.list”, “securitycenter.findings.list”
These additions support the added visibility to Google Event Threat Detection (ETD) findings. The new permissions are included in the recommended API “Security Command Center API”. Refer to our documentation on GCP Projects and GCP Organizations for full details. [ENG-8466]
Features & Enhancements (22.4.4)
-
Improved a performance issue for Basic User Roles with scope selection when customers have hundreds or thousands of cloud accounts. [ENG-18215]
-
We have added the ability to sort, paginate, and filter in the Insight Report view. [ENG-18172]
Resources (22.4.4)
AWS
-
Added visibility into the log publishing options for AWS OpenSearch Domains/Clusters. To complement the added visibility, we have added targeted Query Filter
Elasticsearch/OpenSearch With/Without Log Publishing Options. [ENG-18120] -
Expanded support for AWS VPC Flow Logs. Added three new Query Filters–
Network Flow Log Max Aggregation Interval,Network Flow Log Field Exists In Log Format, andNetwork Flow Log File Format—and regular expression support on existing Query FilterNetwork Flow Log Logging To Storage Container. [ENG-18160] -
We have added AWS KMS and S3 information to SSM documents with content. We have added a Query Filter
Systems Manager Document Associated With Storage Containerto help surface that relationship. Finally, we now examine SSM documents when using encryption key Query Filters now that we support encryption key associations. [ENG-18170]
GCP
- Added visibility to Google Event Threat Detection (ETD) findings. New permissions required are: “securitycenter.sources.list” and “securitycenter.findings.list”. In addition, we updated two Query Filters–
Threat Finding Count ExceedsandThreat Finding Source—to support this added visibility. The ETD resource can be found under the resource type Threat Findings, a resource in the Identity & Management category. [ENG-8466]
Insights (22.4.4)
AWS
Cloud User Inactive For 90 Days- The Insight was renamed fromCloud User Inactiveto show the actual use of the Insight. The ‘Cloud User without Activity’ Insights were updated to use Query FilterCloud User Last Activity (Password & API)to search using API keys. [ENG-14531]
AZURE
Storage Container Blob Soft Delete Disabled- New Insight identifies storage containers which have Soft Delete disabled for blobs. [ENG-17626]
Query Filters (22.4.4)
AWS
-
Elasticsearch/OpenSearch With/Without Log Publishing Options- New Query Filter supports added visibility into the log publishing options for AWS OpenSearch Domains/Clusters. [ENG-18120] -
Network Flow Log Field Exists In Log Format- New Query Filter provides expanded support for AWS VPC Flow Logs; matches network flow logs that contain the specified fields within their defined log format. Note:, AWS default fields include: version, account-id, interface-id, srcaddr, dstaddr, srcport, dstport, protocol, packets, bytes, start, end, action, and log-status. [ENG-18160] -
Network Flow Log File Format- New Query Filter provides expanded support for AWS VPC Flow Logs; matches network flow logs configured with specified file format. Note: file format applies only to network flow logs publishing flow log data to a storage container. [ENG-18160] -
Network Flow Log Logging To Storage Container (Regex)- Updated Query Filter adds regular expression support; expands support for AWS VPC Flow Logs. The updated Query Filter matches network flow logs which are not logging to a specific storage container. There is an option to use regular expression to identify the storage container. Flow logs which are not exporting to storage containers will also be matched. [ENG-18160] -
Network Flow Log Max Aggregation Interval- New Query Filter provides expanded support for AWS VPC Flow Logs; matches network flow logs configured with the specified maximum aggregation interval. [ENG-18160] -
Systems Manager Document Associated With Storage Container- New Query Filter identifies systems manager documents with input configurations that are associated with storage containers. This new Query Filter supports the added AWS KMS and S3 information for SSM documents with content. [ENG-18170]
AZURE
Storage Container Blob Soft Delete Retention Threshold- New Query Filter matches storage containers based on the configuration or absence of a soft delete retention policy for blobs. [ENG-17262]
GCP
-
Threat Finding Count Exceeds- Updated Query Filter supports added visibility to Google Event Threat Detection (ETD) findings. [ENG-8466] -
Threat Finding Source- Updated Query Filter supports added visibility to Google Event Threat Detection (ETD) findings. [ENG-8466]
MULTI-CLOUD/GENERAL
-
Container Image With/Without Tag- New Query Filter finds Container Images with or without tags. This Query Filter can be used in conjunction with Bot actions to clean up images or enforce image tags. [ENG-18249] -
We have several Query Filters that return resources with Public IPs (list below). We have updated our definition of Public IP to remove these CIDR blocks
100.64.0.0/10,127.0.0.0/8,192.0.0.0/24, and198.18.0.0/15relative to the following Query Filters [ENG-18212]:Access List Contains Public Addresses Outside Of Known IPsAccess List Contains Public IPsAccess List Rule Contains Public Address (IPv4)Resource Security Group Has Public IP Space
Bug Fixes (22.4.4)
-
[ENG-18317] Updated our GCP Domain Group/User harvesting to properly account for Group membership.
-
[ENG-18224] Fixed a bug with the Query Filter
Resource Exposing Specific Portsrelated to its use of a denormalized table for performance improvements. -
[ENG-18215] Fixed an issue for Basic User Roles where badge scope wasn’t properly applied when the badge key contained a colon
:character. The change also improves a performance issue for Basic User Roles with scope selection when customers have hundreds or thousands of cloud accounts. -
[ENG-18201] Fixes a bug where adding a single AWS account would not properly save the auto generated AssumeRole ExternalId value. This misled users to believe the ExternalId was set. When creating the IAM Role Trust Policy they encountered AssumeRole errors because the policy was checking for the ExternalId but the configuration was sending no ExternalId. The issue could be mitigated by setting the ExternalId from the edit form.
-
[ENG-18166] Fixed a bug in the Query Filter
Subnet Without Traffic Logging Configuredthat improperly evaluated proxy only subnets for flow logging. -
[ENG-17626] Fixed an issue where container delete retention policy wasn’t harvesting correctly for Azure.
Cloud IAM Governance (Access Explorer) Updates - 22.4.4 Minor Release (08/03/2022)
** The following updates are related to enhancements and bug fixes for our Cloud IAM Governance (Access Explorer) capabilities.**
Contact us at Customer Support Portal with any questions.
Cloud IAM Governance Features & Enhancements (22.4.4)
*Note: the following features are only available to licensed users of the IAM/Access Explorer Feature. *
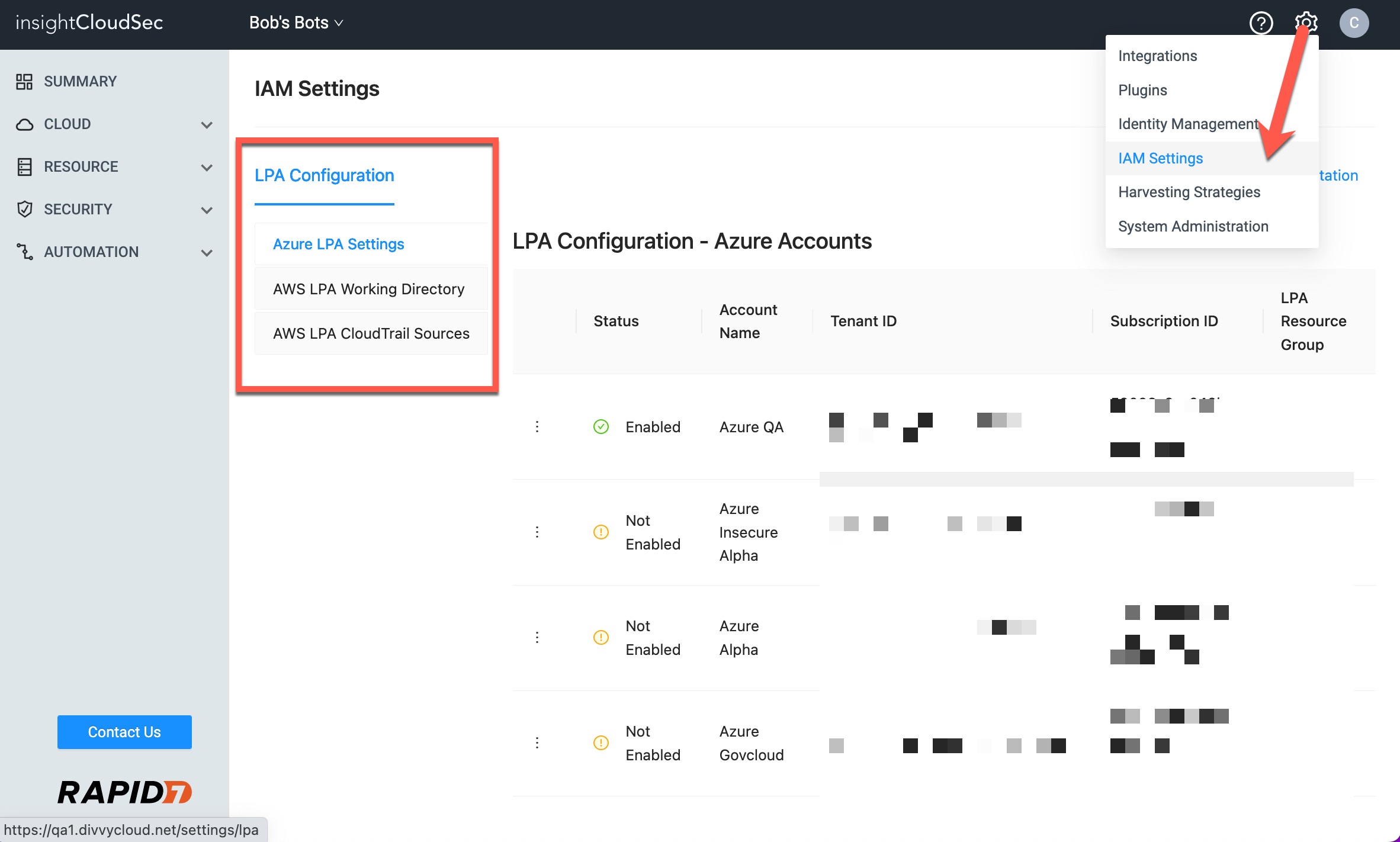
- Beginning with 22.4.4, the IAM settings page will now be available from the top menu bar under a new heading titled “IAM Settings”. This heading will link to a landing page that displays both the LPA Settings for AWS (managed and configured currently as part of Access Explorer) and the recently released Azure LPA settings. [ENG-16230]
- For AWS-based LPA, refer to the documentation on AWS Least Privileged Access for details on this feature including setup and use.
- For Azure-based LPA, refer to the documentation on Azure Least Privileged Access for details on this feature including setup and use.
- Updated InsightCloudSec to display the Principal Activity Blade as part of both Cloud Role and Cloud User resources types. Selecting “Principal Activity” from either of these resource types displays a pane/overlay with a list of activities for the individual resource. [ENG-18304]
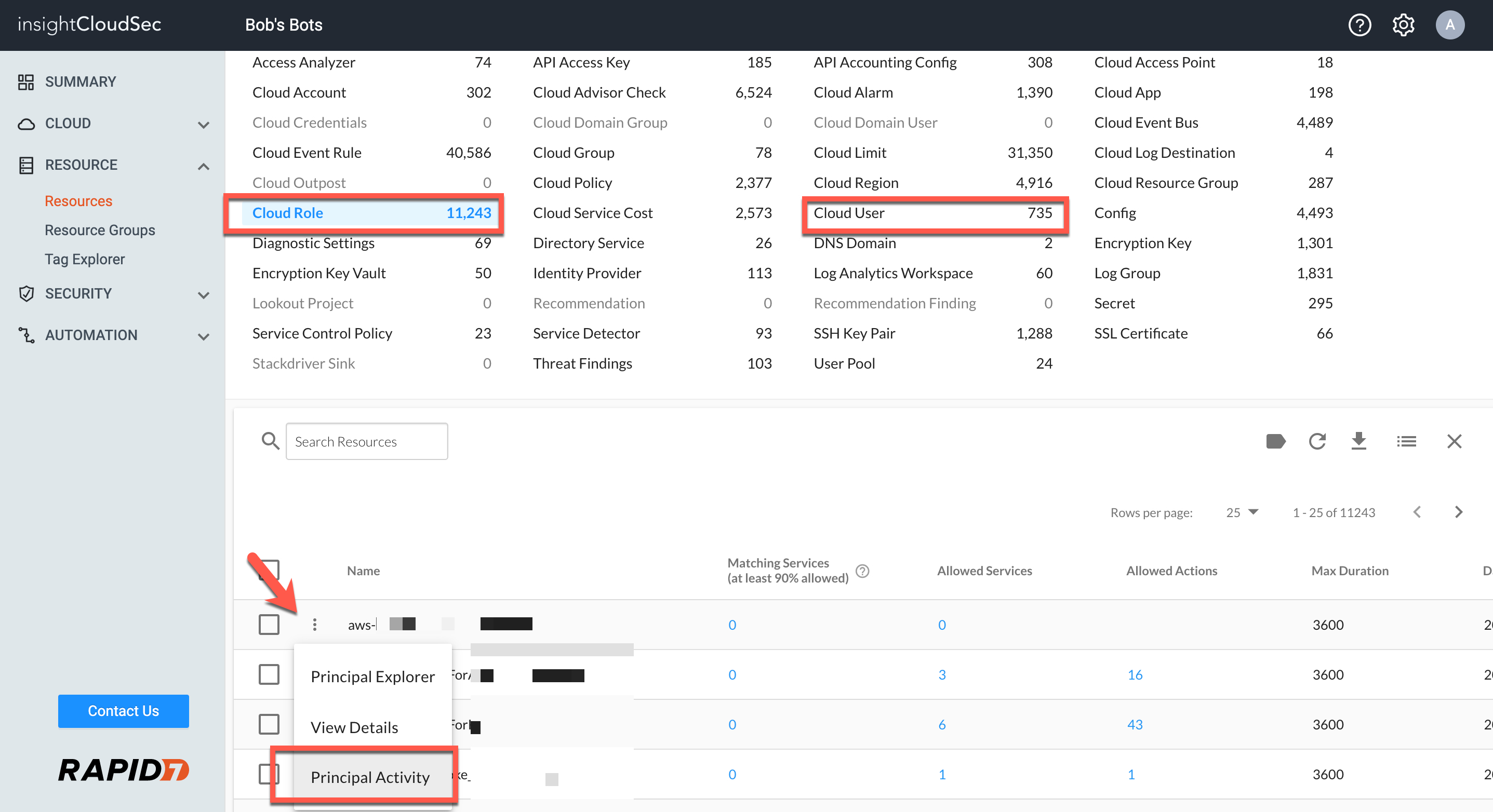
- Renamed menu option “User Activity” to “Principal Activity”. These changes apply to the menu available within Access Explorer and an option in the context menu for both Cloud Roles and Cloud Users. [ENG-18052]
Cloud IAM Governance Bug Fixes (22.4.4)
-
[ENG-18052] Renamed “User Activity” drop down to “Principal Activity” in two places:
- Resources → Cloud User/Role → 3 dots
- Access Explorer → Principals Tab → 3 dots
-
[ENG-17712] Fixed Access Explorer boolean values for principals that had action star or action service star as in
“s3:*” -
[ENG-16951] Fixed a failure in the background jobs LPAAthenaSetupJob and LPAAggregationJob which were failing because the cloud client lacked a target region for EC2, Athena and Glue API endpoints.
-
[ENG-15116] Fixed bug in principal explorer for statements containing NotResource.