MTC Report Deliverables
With your Managed Threat Complete (MTC) service, you’ll receive various report deliverables uploaded to your Rapid7 Services Portal delivered via the secure file transfer system. Sample deliverables and reports are shown below and listed in the appendix to the right.
Monthly Service Reports
Provided to your team on a monthly basis, this report provides metrics and context about threat detection and incident response activities conducted in the previous month, along with information about the health of detection and response controls in your environment.
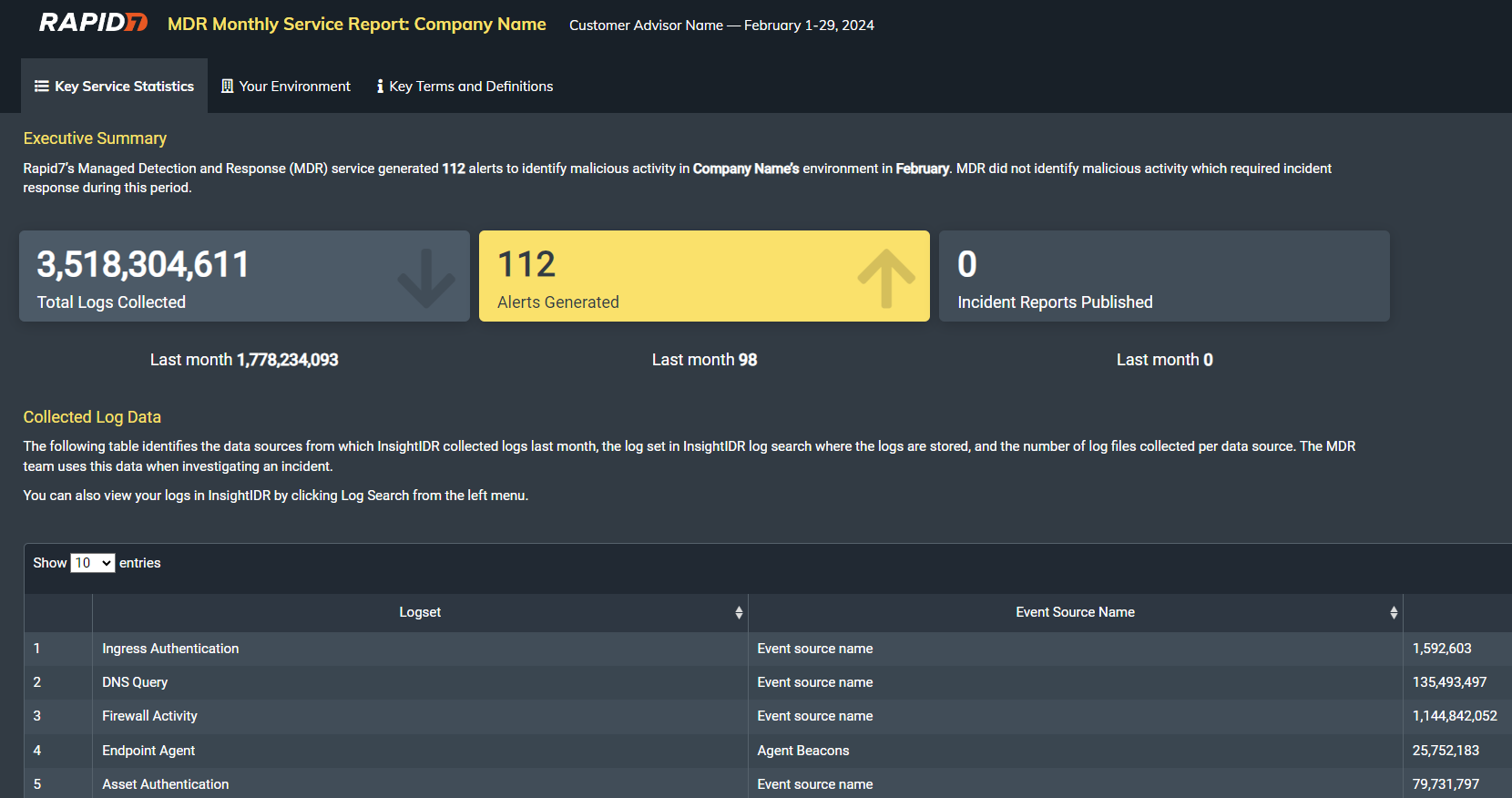
View an example MDR Service Report
Report Walkthrough
Below is a video overview of the Service Report. One of our Managed Detection & Response Cybersecurity Advisors breaks down each section in details to make it easy to understand the details in the report.
Incident Response Reports
This report details all incident management activities, key findings, the timeline of attacker activity, and recommended corrective actions to prevent the likelihood of recurrence and/or improve your ability to detect and respond to similar incidents in the future.

View the Incident Report example - Endpoint Malicious Document .
Service Update & Threat Briefing Presentation
As an MTC Advanced customer, your Cybersecurity Advisor will meet with your team on a monthly basis to:
- Recap the previous month’s MTC related security activities and key metrics
- Perform a security posture review and collaborate with your team to determine a gameplan to strengthen your security posture
- Review your security program against our critical controls framework to strategically improve your security maturity
- Provide advice on your future security projects if requested
Additionally, this review may include metrics to measure and highlight the progress you’ve made to strengthen your security posture by collaborating with your Cybersecurity Advisor and Rapid7. These present a high-level snapshot of MTC related security activities and trending analysis that can be shared with Executive teams to prove the value and ROI of Rapid7 MTC.
View an example Threat Briefing & Trend Reporting Presentation
Security Posture Assessment Report
Once the Rapid7 Agent (Insight Agent) is deployed to 80% or more of the endpoints in your in-scope environment, a Security Posture Assessment will be performed to hunt for potential avenues for a future breach and assess your current security posture. The report deliverable provides remediation and mitigation recommendations to reduce these risks.
If the Security Posture Assessment finds that there is an active compromise, the incident response process will be initiated, and you will be notified by e-mail and/or phone (depending on incident severity).
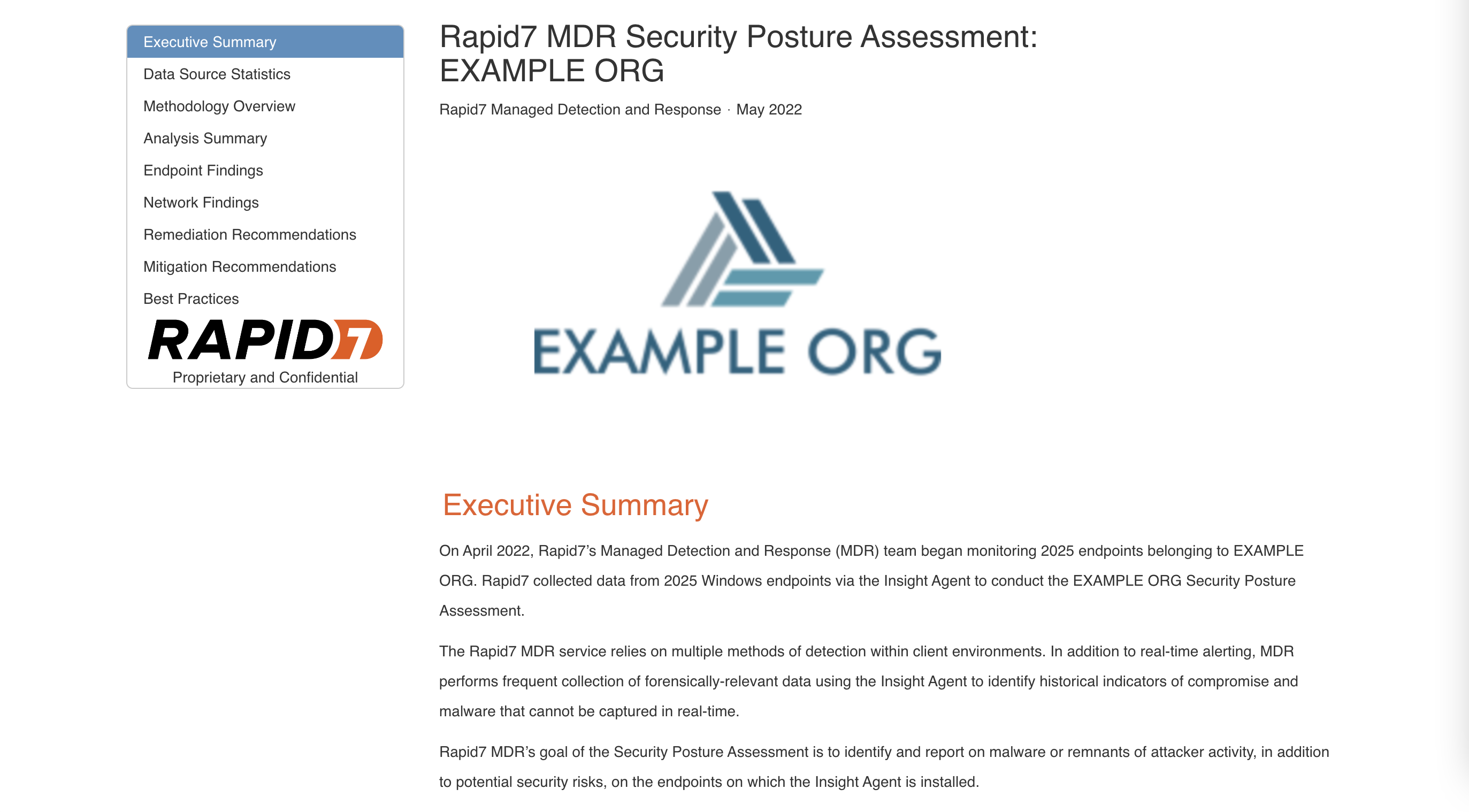
View an example Security Posture Assessment Report
IR Planning Workshop
During onboarding, you will attend an on demand webinar that will help your team to build an Incident Response Plan and Runbook for engaging with the Rapid7 MTC service. This will provide you with the foundational tools and framework to appropriately respond in the event an incident was discovered and addressed by Rapid7’s MTC team.
Top 25 Remediations by Risk Report
The Top Remediations template provides high-level information for assessing the highest impact remediation solutions. The template includes the percentage of total vulnerabilities resolved, the percentage of vulnerabilities with malware kits, the percentage of vulnerabilities with known exploits, and the number of assets affected when the top remediation solutions are applied.
This report presents the best solutions as determined by how recently they were released and how well they address the vulnerability on all the types of machines in your environment. To review all potential solutions for a given vulnerability, see the Remediations section on the details page for that vulnerability.
The Top Remediations template includes information in the following areas:
- The number of vulnerabilities that will be remediated, including vulnerabilities with no exploits or malware that will be remediated.
- Vulnerabilities and total risk score associated with the solution.
- The number of targeted vulnerabilities that have known exploits associated with them.
- The number of targeted vulnerabilities with available malware kits.
- The number of assets to be addressed by remediation.
- The amount of risk that will be reduced by the remediations
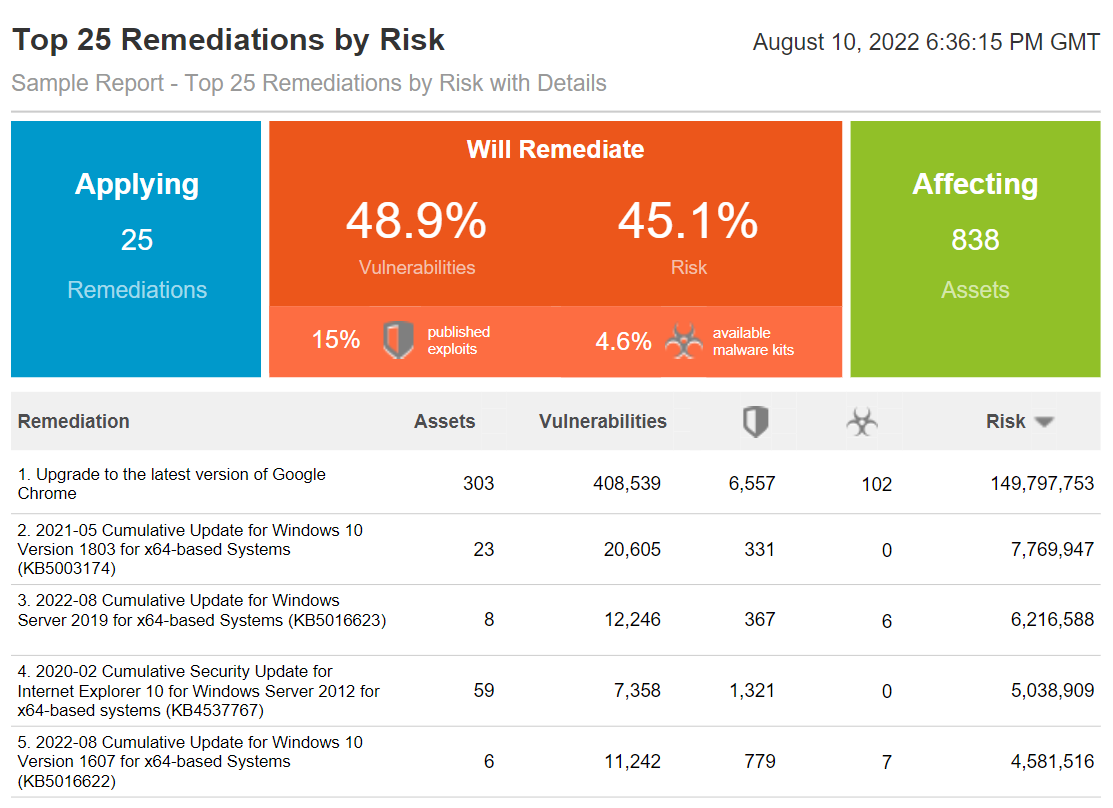
View an example Report to show the Top 25 Remediations by Risk
Vulnerability Risk Scorecard
The Risk Scorecard allows you to be flexible with your reporting. Some of our customers use the risk scorecard to compare risk across each of their offices. Some customers like to see the risk score across each of their critical assets. Some even like to compare the risk score by device or OS type. Whatever the case is for you, the risk scorecard breaks down the risk score of your segments and tells you what vulnerabilities, if remediated, could have the biggest impact and lower your risk score.
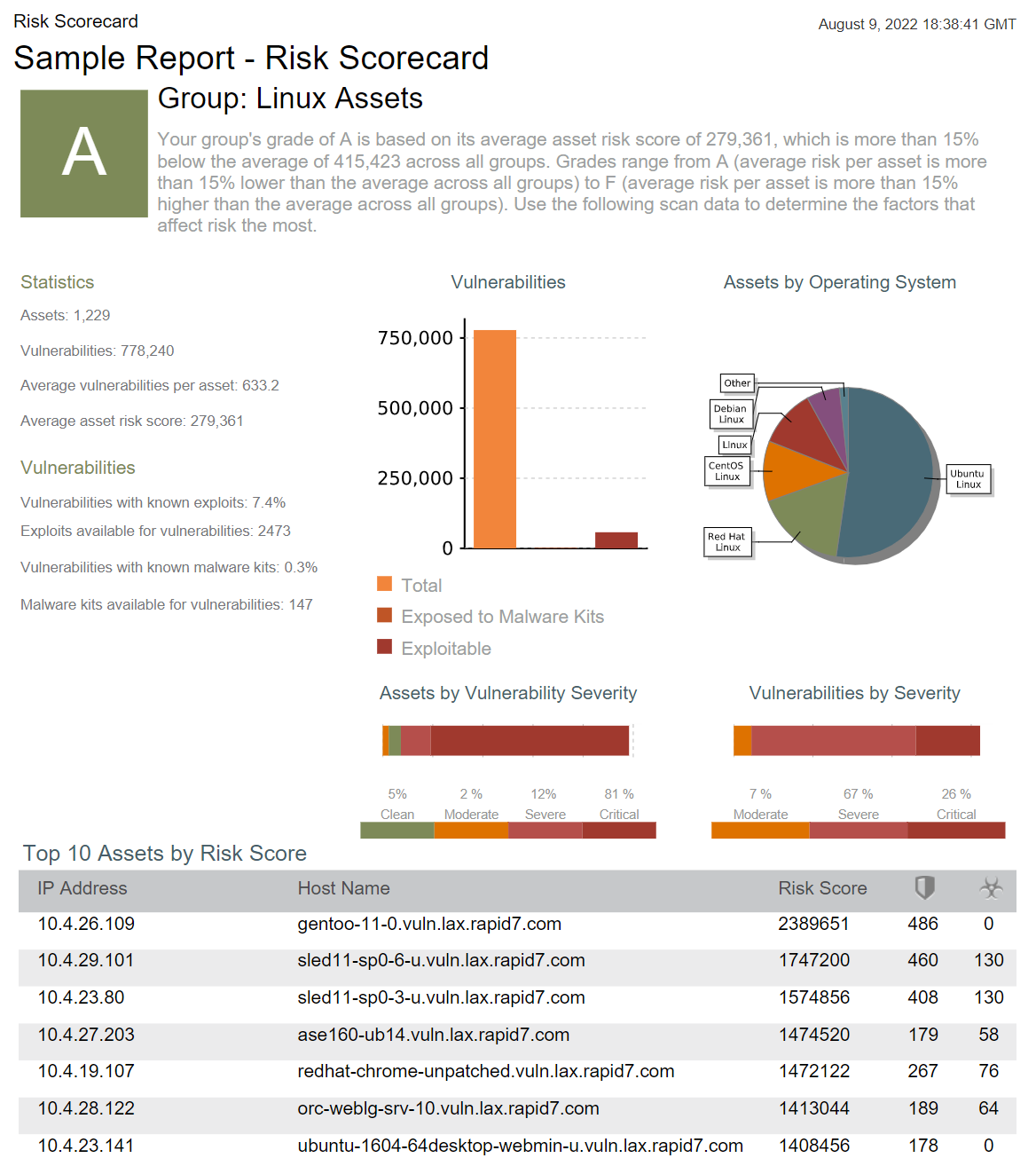
View an example Report to show the Risk Scorecard
Top 10 Assets by Vulnerabilities
The Top 10 Assets by Vulnerabilities report lists the 10 top assets in your organization that have the most vulnerabilities. This report does not account for cumulative risk. You can use this report to view the most vulnerable services to determine if services should be turned off to reduce risk. This report is also useful for prioritizing remediation efforts by listing the assets that have the most vulnerable services.
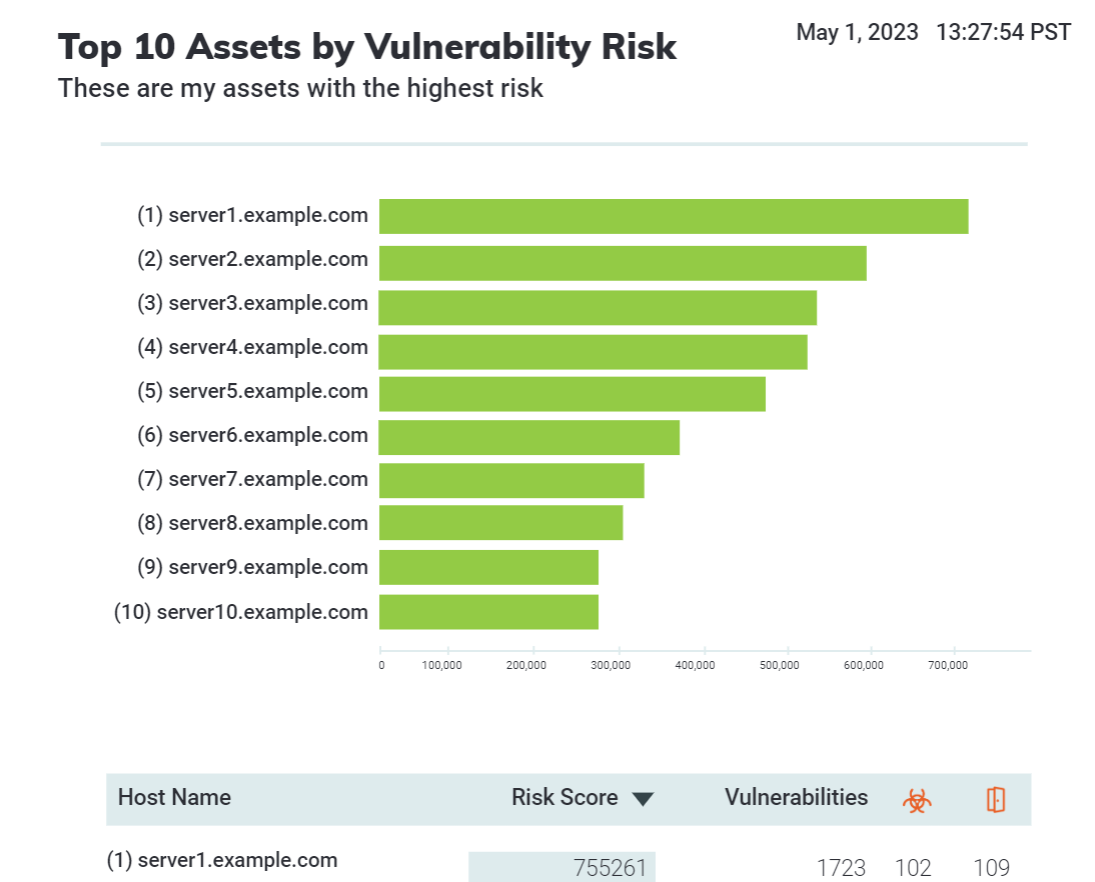
View an example of the Report Top 10 Assets by Vulnerabilities