Configure Azure AD SSO
You can enable users to access the Digital Risk Protection (Threat Command) with IdP-initiated Azure AD SSO. In addition, you can enable SP-initiated SSO and user provisioning with the SAML Just In Time (JIT) method.
User provisioning with JIT enables Azure AD users to register new Digital Risk Protection (Threat Command) users directly from Azure AD, thus bypassing the need to set up each user individually in Digital Risk Protection (Threat Command). For more information, see Provisioning Users with JIT.
Enable access to Digital Risk Protection (Threat Command) with Azure AD
Add the Rapid7 application to the customer Azure AD account.
This section describes the basic Azure AD configuration process. The process is described fully at https://docs.microsoft.com/en-us/azure/active-directory/saas-apps/intsights-tutorial .
Before you begin, ensure that:
- You can access the Azure AD account as an administrator.
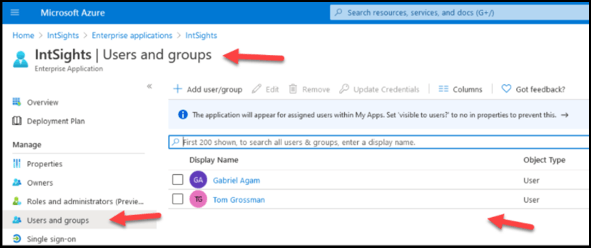
- In the Azure Users and groups section, ensure that your user exists:
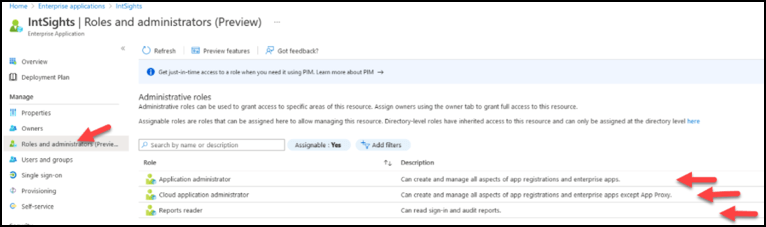
- In Azure Roles and administrators (Preview) section, ensure that administrative roles have permissions for: Application administrator, Cloud application administrator, and Reports reader:
- You can access Digital Risk Protection (Threat Command) as an administrator.
- (Optional) To enable SP-initiatedlogin, you can provide the IDP URL (Login URL) and Issuer ID (Entity ID) for the SSO provider. You can get these values from the Azure Portal .
To enable Azure AD access to Digital Risk Protection (Threat Command):
-
Log in to Azure AD as an administrator.
-
Add the Rapid7 application to Azure AD:
- From the Azure Active Director y, navigate to Enterprise Applications > All Applications.
- Click New application.
- In the Add from the gallery section, type intsights in the search box.
- Select insights and then add the app.
A confirmation message is displayed when the app is added. This may take a few moments.
The Overview page is displayed.
-
Configure the Azure AD SSO:
- From the IntSights application integration page, find the Manage section and click Single sign-on.
- Click SAML.
- In the Basic SAML Configuration section, click Edit.
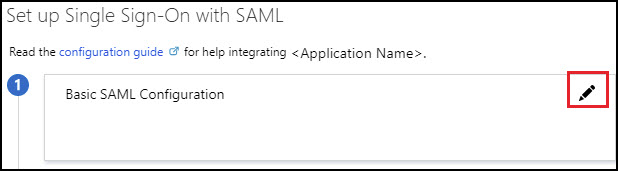
- For the Identifier,**** Reply URL, and Sign on URL fields, type the following:
https://dashboard.ti.insight.rapid7.com/auth/saml-callback/azure -
- Click Save.
- Close the Basic section.
- In the SAML Signing Certificate section, click Download for the Base64 certificate.
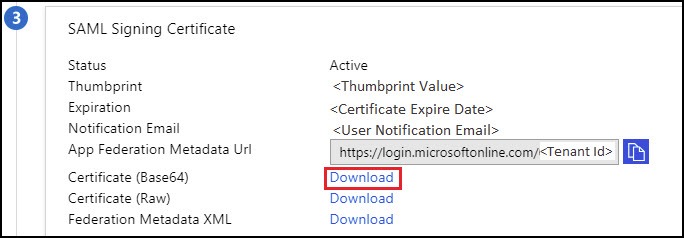
The certificate is downloaded to the default download folder.
-
Log in to Digital Risk Protection (Threat Command) as an administrator.
-
From the Digital Risk Protection (Threat Command) main menu, select Settings > Authentication.
-
Enable SAML single sign-on :
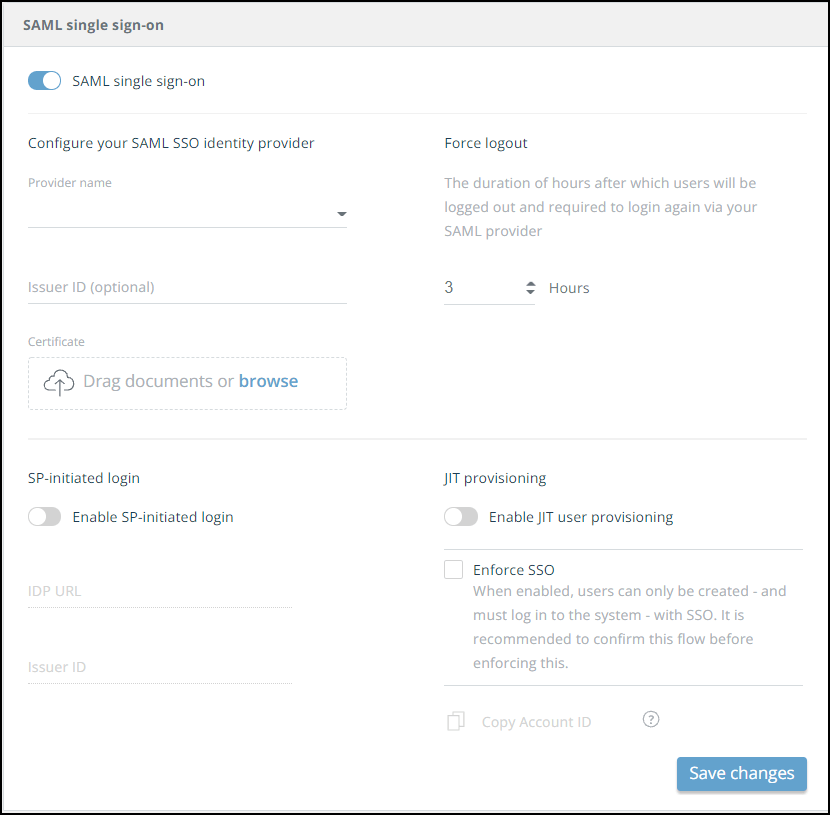
-
Upload the certificate that was downloaded from Azure AD.
-
(Optional) To enable SP-initiated login to Digital Risk Protection (Threat Command), perform the following:
- Select Enable SP-initiated login.
- Enter the IDP URL and Issuer ID.
For the IDP URL value, type the Azure Login URL.
Example: https://login.microsoftonline.com/1a7axxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx/saml2 - For the Issuer ID value, type the Azure Entity ID (same for all Azure users):
https://dashboard.ti.insight.rapid7.com/auth/saml-callback/azure For more information, see Enable SP-Initiated User Login.
-
(Optional) In the Force logout section, set the maximum hours for a user session to remain valid.
After this time period, the user must sign in through their SSO to regain access to Digital Risk Protection (Threat Command). -
(Optional) To enable JIT user provisioning, perform the following:
- Select Enable JIT user provisioning.
- (Optional) When JIT provisioning is enabled, you can force users to log in with SSO.
To enforce this, clickEnforce SSO. Users will not be able to use the Digital Risk Protection (Threat Command) username and password, only SSO. Ensure that your setup supports this before enabling this option. - To get the account ID needed to configure JIT in Azure, click Copy account ID. For more information about provisioning users, see Provisioning Users with JIT.
-
Click Save Changes.
Enable JIT user provisioning in Azure AD SSO
To complete the JIT provisioning setup, you need to perform additional steps in the IntSights application in Azure AD.
In the Azure AD User Attributes & Claims section, the following Required claims must be set:
| Required claim | Value |
|---|---|
| intsightsAccountId | Paste the account ID from the Digital Risk Protection (Threat Command)SAML single sign-ondialog. |
| intsightsRole | SelectAdminorAnalyst |
Before using, you must assign the users, as described in the “Assign the Azure AD test user” section of the Azure AD documentation.
For complete instructions, see https://docs.microsoft.com/en-us/azure/active-directory/saas-apps/intsights-tutorial .