Apache Struts (CVE-2017-5638)
To scan for and report on the Apache Struts (CVE-2017-5638) vulnerability, you can use any scan template that includes the Web Spider, such as the Full Audit, HIPPA Compliance, Internet DMZ Audit, or PCI Audit template. These templates include a check that works with the Web Spider functionality and is performed against any discovered URIs with the ".action" suffix.
Step 1: Configure a Scan Template
To scan for the Apache Struts (CVE-2017-5638) vulnerability, you can use one of the default scan templates that include the Web Spider or you can create a custom scan template that only checks for Apache Struts vulnerabilities.
Using a default scan template
- In your security console, go to the Administration tab.
- Under Scans, click the Manage scan engines.
- Choose a template that includes the Web Spider (Full Audit, HIPPA Compliance, Internet DMZ Audit, or PCI Audit), and click the template name to open it.
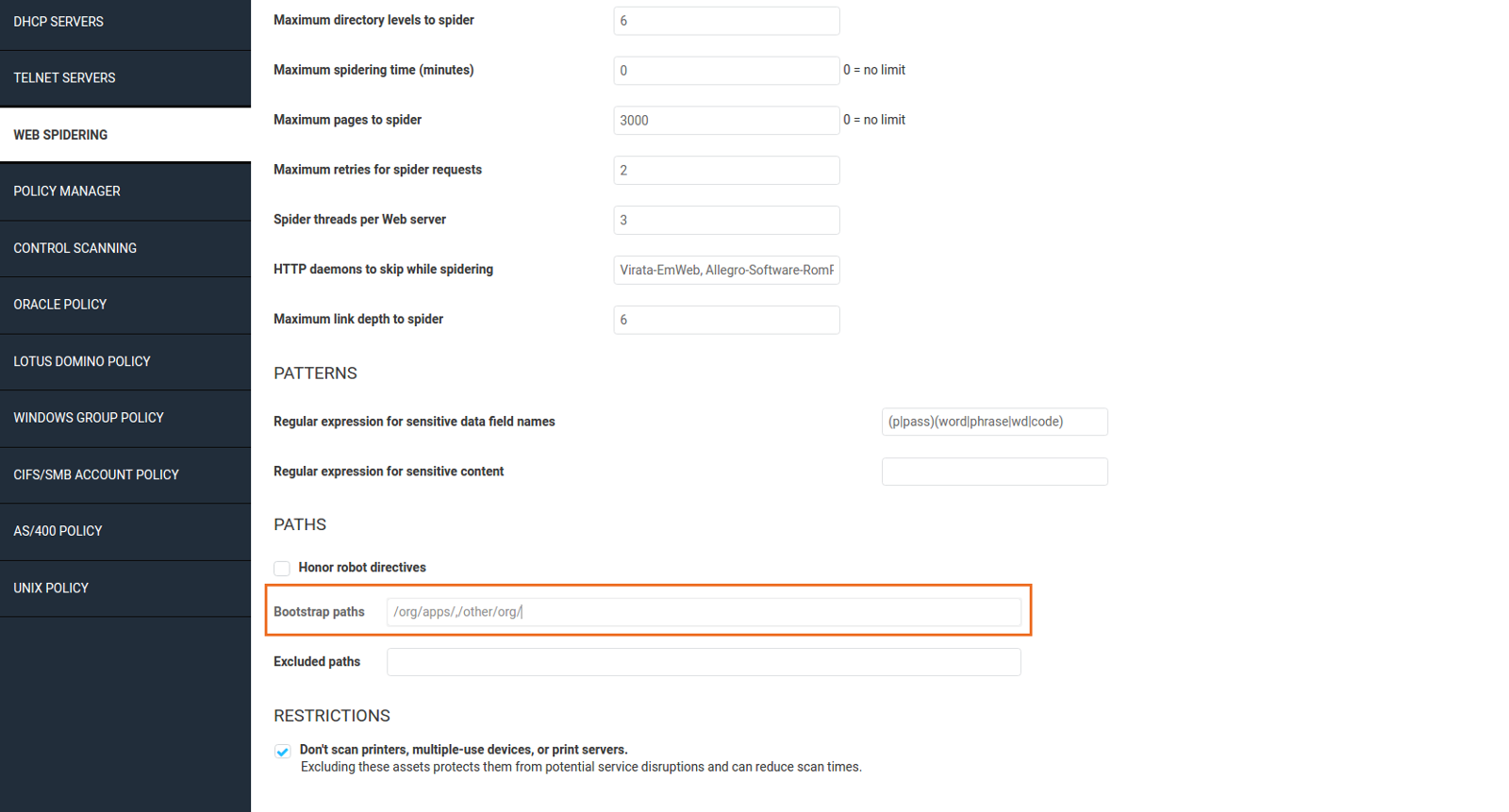
- Browse to the “Web Spidering” tab.
- Under the “Paths” section, add all the necessary paths to the Bootstrap paths field. Each path must be followed by a trailing slash and be comma-separated (e.g.
/org/apps/,/other/org/).
Note
If your application's URIs are not discoverable by the default spidering process, you must add the necessary paths to the scan template.
- Save your changes to the template.
Creating a Custom Scan Template
If you prefer to limit the scope of your scan for efficiency purposes, you can create a scan template that only runs the Apache Struts vulnerability check.
To create a custom scan template that only runs the Apache Struts vulnerability check:
- In your security console, go to the Administration tab.
- Under the Scan Options area, click the Manage scan templates link.
- Find the Full Audit template and click the Copy scan template icon. A copy of the Full Audit template is made so that we configure it specifically for Apache Struts. The copy will have all required fields filled out. No additional changes are required.
Note
Be sure to follow steps 4 through 6 of the previous section if you need to configure Web Spidering.
- From the "General" tab, locate the Name field and enter a new name for the scan template. You should give it an easily identifiable name, such as "Apache Struts."
- Go to the Vulnerability Checks tab and find the “Selected Checks” section. You'll see three dropdown fields: By Category, By Check Type, and By Individual Check.
- Click the “By Individual Check” dropdown to expand it, and click “Add Checks”.
- Search for "CVE-2017-5638."
- When the results appear, click the Select All checkbox to select all of the Apache Struts checks.
- Save your changes.
Now, this scan template only includes checks for Apache Struts. You can further optimize the scan template by removing the "Categories" and "Check Types". To do this, expand those dropdowns, click the “Remove Categories” button, and select all items in the list. Save your changes.
When you are finished, your “Selected Checks” section should look like this:
You now have a custom template designed specifically to scan for Apache Struts vulnerabilities. Save your new scan template.
Step 2: Scan Your Network
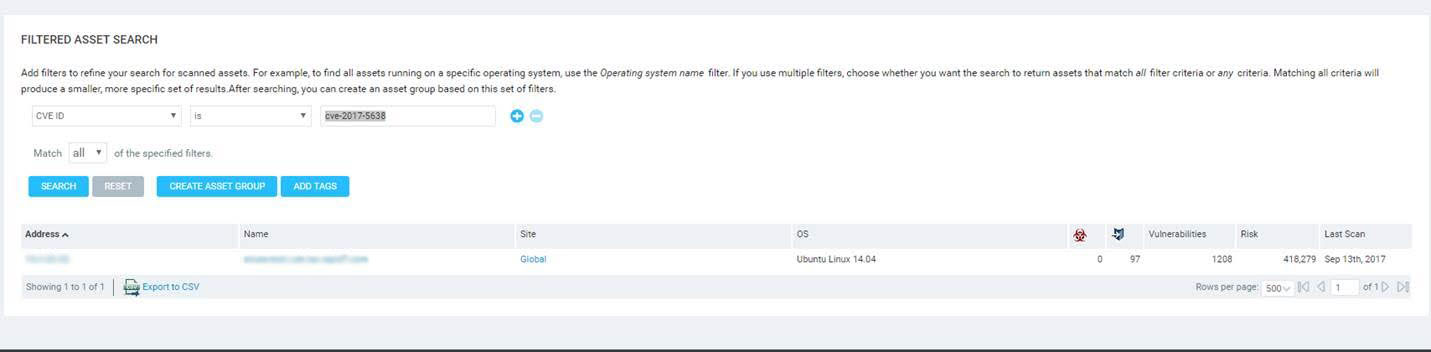
Run a scan with one of the configured templates described above, according to your product. Once the scan has completed, search for “CVE-2017-5638” in the search field on the security console home page.
In order to continually monitor any assets that are vulnerable to Apache Struts, create a Dynamic Asset Group based on the same CVE ID you searched for. Your filtered asset search should look for exact matches to the CVE ID itself (CVE ID = is = CVE-2017-5638).
Step 3: Report on Apache Struts
We can use a SQL query to report on CVE-2017-5638 in your network.
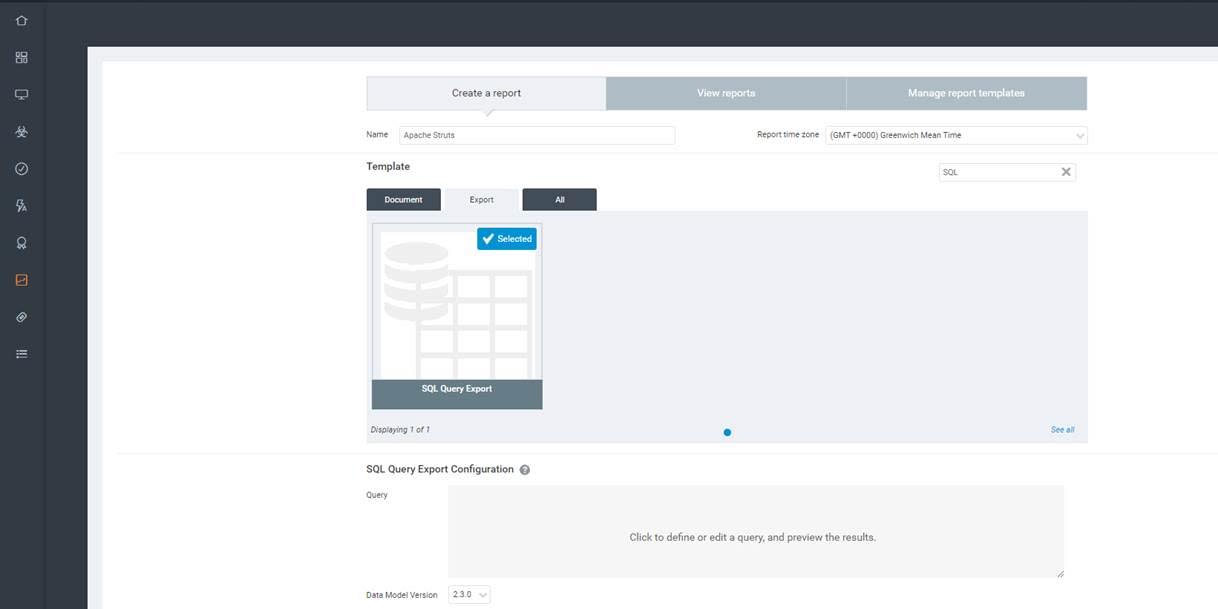
To do this, click the Reports tab on your security console menu. Under “Create a Report”, give it a name and select the “Export” tab under “Template”. Alternatively, you can also type “sql” in the template search field which will narrow the list down to our desired template: SQL Query Export.
With this template selected, you will see a gray “Query” box that appears below the configuration section. Click this area to open it, and then paste the following SQL script inside:
sql
Click “Validate” to make sure the script will be read correctly. If you want to get an idea of what the results will look like, you can use the “Preview” button to retrieve the first ten records that respond to the query. Click “Done” when you’re finished.
If you want to report on a specific scan, site, or asset group, you can define the scope of the report just below the query field. Now we can save this report for future use. If you would like a report created at the same time, click “Save & Run the Report”.
For more information about the Apache Struts vulnerability check, please see the following blog posts:
https://blog.rapid7.com/2017/03/09/apache-jakarta-vulnerability-attacks-in-the-wild/https://blog.rapid7.com/2017/03/15/using-web-spider-to-detect-vulnerable-apache-struts-apps-cve-2017-5638/