Cisco ISE
Cisco Identity Services Engine (ISE) allows for identity management across diverse devices and applications. You can configure Cisco ISE to send VPN data to SIEM (InsightIDR) for visibility into users’ remote network ingress activity.
To set up Cisco ISE you’ll need to:
- Configure Cisco ISE to send data to your Collector.
- Set up the Cisco ISE in SIEM (InsightIDR).
- Verify the configuration works.
Configure Cisco ISE to send logs to SIEM (InsightIDR)
To enable SIEM (InsightIDR) to receive data from your Cisco ISE remote system logging, complete these steps:
Task 1: Configure a remote logging target in Cisco ISE
- Log in to your Cisco ISE Administration Interface.
- From the navigation menu, select Administration > System > Logging > Remote Logging Targets.
- Click Add, and then configure the following parameters:
| Option | Description |
|---|---|
| Name | Type a unique name for the remote target system. |
| Description | You can uniquely identify the target system for users. |
| IP Address | Enter the IP address of your SIEM (InsightIDR) collector. |
| Port | Enter the port value that you specified in your Cisco ISE log source for SIEM (InsightIDR). |
| Facility Code | From the Facility Code list, select the syslog facility to use for logging events. |
| Maximum Length | Type 1024 as the maximum packet length allowed for the UDP syslog message. |
- Click Submit.
Task 2: Add the new target to your desired logging categories
- Select Administration > System > Logging > Logging Categories.
- Click the radio button next to the category that you want to edit, and click Edit.
- Add the target that you created in the previous section to the following categories. These are default log collection settings and can be modified as needed:
- AAA Audit
- Failed Attempts
- Passed Authentications
- AAA Diagnostics
- Administrator Authentication and Authorization
- Authentication Flow Diagnostics
- Identity Stores Diagnostics
- Policy Diagnostics
- RADIUS Diagnostics
- Accounting
- External MDM
- Passive ID
- Posture and Client Provisioning Audit
- Posture and Client Provisioning Diagnostics
- Profiler
- Administrative and Operational Audit
- System Diagnostics
- System Statistics
- AAA Audit
- Click Save.
- Go to the Logging Categories page and verify the configuration changes that were made to the specific categories.
For more information, see “Logging Mechanism” section of the Cisco Identity Services Engine Administrator Guide .
Configure SIEM (InsightIDR) to collect data from the event source
After you complete the prerequisite steps and configure the event source to send data, you must add the event source in SIEM (InsightIDR).
To configure the new event source in SIEM (InsightIDR):
- From the left menu, go to Data Collection and click Setup Event Source > Add Event Source.
- Do one of the following:
- Search for Cisco ISE VPN in the event sources search bar.
- In the Product Type filter, select VPN.
- Select the Cisco ISE VPN event source tile.
- Choose the timezone that matches the location of your event source logs.
- Optionally choose to send unparsed logs.
- Select an attribution source.
- Optionally configure inactivity timeout threshold in minutes.
- Configure your default domain and any advanced settings.
- Select syslog as your collection method and specify the port and protocol you identified during Cisco ISE configuration.
- Optionally choose to Encrypt the event source if choosing TCP by downloading the Rapid7 Certificate.
- Click the Save button.
Verify the Configuration
Complete the following steps to view your logs and ensure events are making it to the Collector.
- On the new event source that was just created, click the View Raw Log button. If you see log messages in the box, then this shows that logs are flowing to the Collector.
- Next, click Log Search in the left menu. Select the applicable Log Sets and the Log Names within them. The Log Name will be the event source name or “Cisco ISE” if you did not name the event source. Cisco ISE logs flow into the following log sets:
- Ingress Authentication
- Firewall Activity
Parsing Cisco ISE event codes
The following table contains the event logs from Cisco ISE that are parsed by SIEM (InsightIDR).
| Event Code | Description |
|---|---|
| 3000 | RADIUS Accounting start request |
| 3001 | RADIUS Accounting stop request |
| 5200 | Passed-Authentication |
| 5400 | Failed-Attempt |
| 5401 | Failed-Attempt |
| 3304 | TACACS+ Accounting STOP |
Sample Logs
The following are log samples that Cisco ISE sends to SIEM (InsightIDR).
Ingress Authentication (VPN)
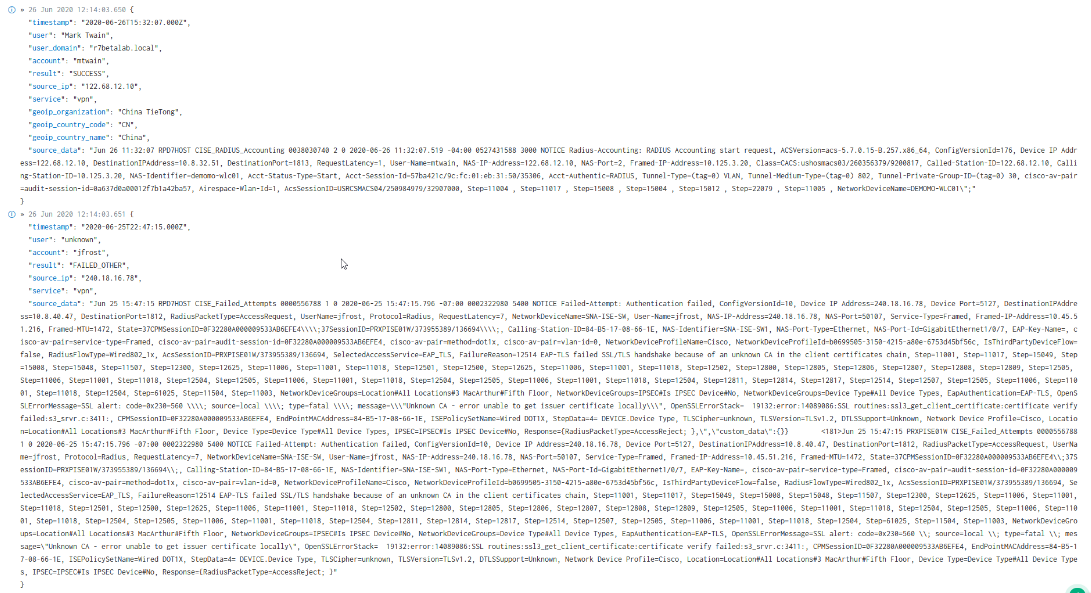
Jun 26 11:32:07 RPD7HOST CISE_RADIUS_Accounting 0038030740 2 0 2020-06-26 11:32:07.519 -04:00 0527431588 3000 NOTICE Radius-Accounting: RADIUS Accounting start request, ACSVersion=acs-5.7.0.15-B.257.x86_64, ConfigVersionId=176, Device IP Address=122.68.12.10, DestinationIPAddress=10.8.32.51, DestinationPort=1813, RequestLatency=1, User-Name=mtwain, NAS-IP-Address=122.68.12.10, NAS-Port=2, Framed-IP-Address=10.125.3.20, Class=CACS:ushosmacs03/260356379/9200817, Called-Station-ID=122.68.12.10, Calling-Station-ID=10.125.3.20, NAS-Identifier=demomo-wlc01, Acct-Status-Type=Start, Acct-Session-Id=57ba421c/9c:fc:01:eb:31:50/35306, Acct-Authentic=RADIUS, Tunnel-Type=(tag=0) VLAN, Tunnel-Medium-Type=(tag=0) 802, Tunnel-Private-Group-ID=(tag=0) 30, cisco-av-pair=audit-session-id=0a637d0a00012f7b1a42ba57, Airespace-Wlan-Id=1, AcsSessionID=USRCSAACS04/250984979/32907000, Step=11004 , Step=11017 , Step=15008 , Step=15004 , Step=15012 , Step=22079 , Step=11005 , NetworkDeviceName=DEMOMO-WLC01";
Ingress Authentication (VPN)
Jun 26 11:32:07 RPD7HOST CISE_RADIUS_Accounting 0173168007 2 0 2020-06-26 11:32:07.519 -04:00 1716674385 3001 NOTICE Radius-Accounting: RADIUS Accounting stop request, ACSVersion=acs-5.7.0.15-B.257.x86_64, ConfigVersionId=47, Device IP Address=162.48.4.12, DestinationIPAddress=10.115.6.51, DestinationPort=1813, RequestLatency=0, User-Name=mtwain, NAS-IP-Address=162.48.4.12, NAS-Port=1, Framed-IP-Address=10.148.15.45, Class=CACS:KRDCSAACS05/254262891/120113033, Called-Station-ID=74-a2-e6-c7-4b-20, Calling-Station-ID=84-a1-34-d0-36-05, NAS-Identifier=Cisco_c7:4b:24, Acct-Status-Type=Stop, Acct-Delay-Time=0, Acct-Input-Octets=70779, Acct-Output-Octets=161620, Acct-Session-Id=57ba5e51/84:a1:34:d0:36:05/28561, Acct-Authentic=RADIUS, Acct-Session-Time=3274, Acct-Input-Packets=471, Acct-Output-Packets=367, Acct-Terminate-Cause=Idle Timeout, attribute-52=00:00:00:00, attribute-53=00:00:00:00, Event-Timestamp=1471834908, NAS-Port-Type=Wireless - IEEE 802.11, Tunnel-Type=(tag=0) VLAN";
Jun 26 11:32:07 RPD7HOST CISE_RADIUS_Accounting 0173168014 2 0 2020-06-26 11:32:07.519 -04:00 1716674482 3002 NOTICE Radius-Accounting: RADIUS Accounting watchdog update, ACSVersion=acs-5.7.0.15-B.257.x86_64, ConfigVersionId=47, Device IP Address=10.3.0.20, DestinationIPAddress=10.115.6.51, DestinationPort=1813, RequestLatency=0, User-Name=mtwain, NAS-IP-Address=10.3.0.20, NAS-Port=1, Framed-IP-Address=10.3.17.20, Called-Station-ID=10.3.0.20, Calling-Station-ID=10.3.17.20, NAS-Identifier=Knox_Plant, Acct-Status-Type=Interim-Update, Acct-Delay-Time=0, Acct-Input-Octets=5803226, Acct-Output-Octets=2622839, Acct-Session-Id=57b8a71a/00:17:23:0c:80:10/1415, Acct-Authentic=Remote, Acct-Session-Time=141421, Acct-Input-Packets=46062, Acct-Output-Packets=17322, Tunnel-Type=(tag=0) VLAN, Tunnel-Medium-Type=(tag=0) 802, Tunnel-Private-Group-ID=(tag=0) 2, cisco-av-pair=nas-update=true, Airespace-Wlan-Id=2, AcsSessionID=KRDCSAACS05/254262891/120118472, Step=11004 , Step=11017 , Step=15008 , Step=15004";Firewall Activity (Passed Authentication)
Jun 25 15:46:23 RPD7HOST CISE_Passed_Authentications 0000556184 1 0 2020-06-25 15:46:23.961 -07:00 0002321066 5200 NOTICE Passed-Authentication: Authentication succeeded, ConfigVersionId=10, Device IP Address=10.64.120.4, DestinationIPAddress=10.8.40.47, DestinationPort=1812, UserName=hfinn, Protocol=Radius, RequestLatency=14, NetworkDeviceName=BR120-SW, User-Name=hfinn NAS-IP-Address=10.64.120.4, NAS-Port=50126, Service-Type=Call Check, Framed-MTU=1472, Calling-Station-ID=FC-3F-DB-4D-69-A2, NAS-Identifier=BR120-SW1, NAS-Port-Type=Ethernet, NAS-Port-Id=GigabitEthernet1/0/26, EAP-Key-Name=, cisco-av-pair=service-type=Call Check, cisco-av-pair=audit-session-id=0478400A0001E0FEF3C90EFB, cisco-av-pair=method=mab, OriginalUserName=hfinn, NetworkDeviceProfileName=Cisco, NetworkDeviceProfileId=b0699505-3150-4215-a80e-6753d45bf56c, IsThirdPartyDeviceFlow=false, RadiusFlowType=WiredMAB, AcsSessionID=PRXPISE01W/373955389/136606, AuthenticationIdentityStore=Internal Endpoints, AuthenticationMethod=Lookup, SelectedAccessService=Default Network Access, SelectedAuthorizationProfiles=WIRED-PERMIT, UseCase=Host Lookup, IdentityGroup=Endpoint Identity Groups:Profiled:HP-Device, Step=11001, Step=11017, Step=11027, Step=15049, Step=15008, Step=15048, Step=15048, Step=15048, Step=15041, Step=15013, Step=24209, Step=24211, Step=22037, Step=24715, Step=15036, Step=15048, Step=15048, Step=15048, Step=15016, Step=11022, Step=11002, SelectedAuthenticationIdentityStores=Internal Endpoints, AuthenticationStatus=AuthenticationPassed, NetworkDeviceGroups=Location#All Locations#RTL - Woodland Hills, NetworkDeviceGroups=Device Type#All Device Types#Switches, NetworkDeviceGroups=IPSEC#Is IPSEC Device#No, IdentityPolicyMatchedRule=Default, AuthorizationPolicyMatchedRule=Printers, UserType=Host, CPMSessionID=0478400A0001E0FEF3C90EFB, EndPointMACAddress=FC-3F-DB-4D-69-A2, PostureAssessmentStatus=NotApplicable, EndPointMatchedProfile=HP-LaserJet-Printer, DeviceRegistrationStatus=notRegistered, ISEPolicySetName=Wired MAB, IdentitySelectionMatchedRule=Default, StepData=5= Normalised Radius.RadiusFlowType, StepData=6= Radius.NAS-Port-Type, StepData=7= DEVICE.Device Type, StepData=9=Internal Endpoints, StepData=15= EndPoints.AnomalousBehaviour, StepData=16= EndPoints.EndPointPolicy, StepData=17= EndPoints.LogicalProfile, allowEasyWiredSession=false, DTLSSupport=Unknown, HostIdentityGroup=Endpoint Identity Groups:Profiled:HP-Device, Network Device Profile=Cisco, Location=Location#All Locations#RTL - Woodland Hills, Device Type=Device Type#All Device Types#Switches, IPSEC=IPSEC#Is IPSEC Device#No, LogicalProfile=3b8d49f0-8c01-11e6-996c-525400b48521, LogicalProfile=b9e45830-1c19-11e8-b9c2-6cb2ae989650, EndPointPolicy=74bff490-51ce-11e8-b9c2-6cb2ae989650, EndPointPolicy=29473540-8c00-11e6-996c-525400b48521, EndPointPolicy=23d26b20-8c00-11e6-996c-525400b48521, Name=Endpoint Identity Groups:Profiled:HP-Device, Response={UserName=hfinn; User-Name=hfinn; State=ReauthSession:0478400A0001E0FEF3C90EFB; Class=CACS:0478400A0001E0FEF3C90EFB:PRXPISE01W/373955389/136606; cisco-av-pair=ACS:CiscoSecure-Defined-ACL=#ACSACL#-IP-WIRED-DOMAIN-USER-5a6269ae; cisco-av-pair=profile-name=HP-LaserJet-Printer; LicenseTypes=2051; }Firewall Activity (Failed Attempts)
Jun 25 15:47:15 RPD7HOST CISE_Failed_Attempts 0000556788 1 0 2020-06-25 15:47:15.796 -07:00 0002322980 5400 NOTICE Failed-Attempt: Authentication failed, ConfigVersionId=10, Device IP Address=240.18.16.78, Device Port=5127, DestinationIPAddress=10.8.40.47, DestinationPort=1812, RadiusPacketType=AccessRequest, UserName=jfrost, Protocol=Radius, RequestLatency=7, NetworkDeviceName=SNA-ISE-SW, User-Name=jfrost, NAS-IP-Address=240.18.16.78, NAS-Port=50107, Service-Type=Framed, Framed-IP-Address=10.45.51.216, Framed-MTU=1472, State=37CPMSessionID=0F32280A000009533AB6EFE4\\;37SessionID=PRXPISE01W/373955389/136694\\;, Calling-Station-ID=84-B5-17-08-66-1E, NAS-Identifier=SNA-ISE-SW1, NAS-Port-Type=Ethernet, NAS-Port-Id=GigabitEthernet1/0/7, EAP-Key-Name=, cisco-av-pair=service-type=Framed, cisco-av-pair=audit-session-id=0F32280A000009533AB6EFE4, cisco-av-pair=method=dot1x, cisco-av-pair=vlan-id=0, NetworkDeviceProfileName=Cisco, NetworkDeviceProfileId=b0699505-3150-4215-a80e-6753d45bf56c, IsThirdPartyDeviceFlow=false, RadiusFlowType=Wired802_1x, AcsSessionID=PRXPISE01W/373955389/136694, SelectedAccessService=EAP_TLS, FailureReason=12514 EAP-TLS failed SSL/TLS handshake because of an unknown CA in the client certificates chain, Step=11001, Step=11017, Step=15049, Step=15008, Step=15048, Step=11507, Step=12300, Step=12625, Step=11006, Step=11001, Step=11018, Step=12501, Step=12500, Step=12625, Step=11006, Step=11001, Step=11018, Step=12502, Step=12800, Step=12805, Step=12806, Step=12807, Step=12808, Step=12809, Step=12505, Step=11006, Step=11001, Step=11018, Step=12504, Step=12505, Step=11006, Step=11001, Step=11018, Step=12504, Step=12505, Step=11006, Step=11001, Step=11018, Step=12504, Step=12811, Step=12814, Step=12817, Step=12514, Step=12507, Step=12505, Step=11006, Step=11001, Step=11018, Step=12504, Step=61025, Step=11504, Step=11003, NetworkDeviceGroups=Location#All Locations#3 MacArthur#Fifth Floor, NetworkDeviceGroups=IPSEC#Is IPSEC Device#No, NetworkDeviceGroups=Device Type#All Device Types, EapAuthentication=EAP-TLS, OpenSSLErrorMessage=SSL alert: code=0x230=560 \\; source=local \\; type=fatal \\; message=\"Unknown CA - error unable to get issuer certificate locally\", OpenSSLErrorStack= 19132:error:14089086:SSL routines:ssl3_get_client_certificate:certificate verify failed:s3_srvr.c:3411:, CPMSessionID=0F32280A000009533AB6EFE4, EndPointMACAddress=84-B5-17-08-66-1E, ISEPolicySetName=Wired DOT1X, StepData=4= DEVICE.Device Type, TLSCipher=unknown, TLSVersion=TLSv1.2, DTLSSupport=Unknown, Network Device Profile=Cisco, Location=Location#All Locations#3 MacArthur#Fifth Floor, Device Type=Device Type#All Device Types, IPSEC=IPSEC#Is IPSEC Device#No, Response={RadiusPacketType=AccessReject; },","custom_data":{}} <181>Jun 25 15:47:15 PRXPISE01W CISE_Failed_Attempts 0000556788 1 0 2020-06-25 15:47:15.796 -07:00 0002322980 5400 NOTICE Failed-Attempt: Authentication failed, ConfigVersionId=10, Device IP Address=240.18.16.78, Device Port=5127, DestinationIPAddress=10.8.40.47, DestinationPort=1812, RadiusPacketType=AccessRequest, UserName=jfrost, Protocol=Radius, RequestLatency=7, NetworkDeviceName=SNA-ISE-SW, User-Name=jfrost, NAS-IP-Address=240.18.16.78, NAS-Port=50107, Service-Type=Framed, Framed-IP-Address=10.45.51.216, Framed-MTU=1472, State=37CPMSessionID=0F32280A000009533AB6EFE4\;37SessionID=PRXPISE01W/373955389/136694\;, Calling-Station-ID=84-B5-17-08-66-1E, NAS-Identifier=SNA-ISE-SW1, NAS-Port-Type=Ethernet, NAS-Port-Id=GigabitEthernet1/0/7, EAP-Key-Name=, cisco-av-pair=service-type=Framed, cisco-av-pair=audit-session-id=0F32280A000009533AB6EFE4, cisco-av-pair=method=dot1x, cisco-av-pair=vlan-id=0, NetworkDeviceProfileName=Cisco, NetworkDeviceProfileId=b0699505-3150-4215-a80e-6753d45bf56c, IsThirdPartyDeviceFlow=false, RadiusFlowType=Wired802_1x, AcsSessionID=PRXPISE01W/373955389/136694, SelectedAccessService=EAP_TLS, FailureReason=12514 EAP-TLS failed SSL/TLS handshake because of an unknown CA in the client certificates chain, Step=11001, Step=11017, Step=15049, Step=15008, Step=15048, Step=11507, Step=12300, Step=12625, Step=11006, Step=11001, Step=11018, Step=12501, Step=12500, Step=12625, Step=11006, Step=11001, Step=11018, Step=12502, Step=12800, Step=12805, Step=12806, Step=12807, Step=12808, Step=12809, Step=12505, Step=11006, Step=11001, Step=11018, Step=12504, Step=12505, Step=11006, Step=11001, Step=11018, Step=12504, Step=12505, Step=11006, Step=11001, Step=11018, Step=12504, Step=12811, Step=12814, Step=12817, Step=12514, Step=12507, Step=12505, Step=11006, Step=11001, Step=11018, Step=12504, Step=61025, Step=11504, Step=11003, NetworkDeviceGroups=Location#All Locations#3 MacArthur#Fifth Floor, NetworkDeviceGroups=IPSEC#Is IPSEC Device#No, NetworkDeviceGroups=Device Type#All Device Types, EapAuthentication=EAP-TLS, OpenSSLErrorMessage=SSL alert: code=0x230=560 \; source=local \; type=fatal \; message="Unknown CA - error unable to get issuer certificate locally", OpenSSLErrorStack= 19132:error:14089086:SSL routines:ssl3_get_client_certificate:certificate verify failed:s3_srvr.c:3411:, CPMSessionID=0F32280A000009533AB6EFE4, EndPointMACAddress=84-B5-17-08-66-1E, ISEPolicySetName=Wired DOT1X, StepData=4= DEVICE.Device Type, TLSCipher=unknown, TLSVersion=TLSv1.2, DTLSSupport=Unknown, Network Device Profile=Cisco, Location=Location#All Locations#3 MacArthur#Fifth Floor, Device Type=Device Type#All Device Types, IPSEC=IPSEC#Is IPSEC Device#No, Response={RadiusPacketType=AccessReject; }Sample Firewall Logs in Log Search
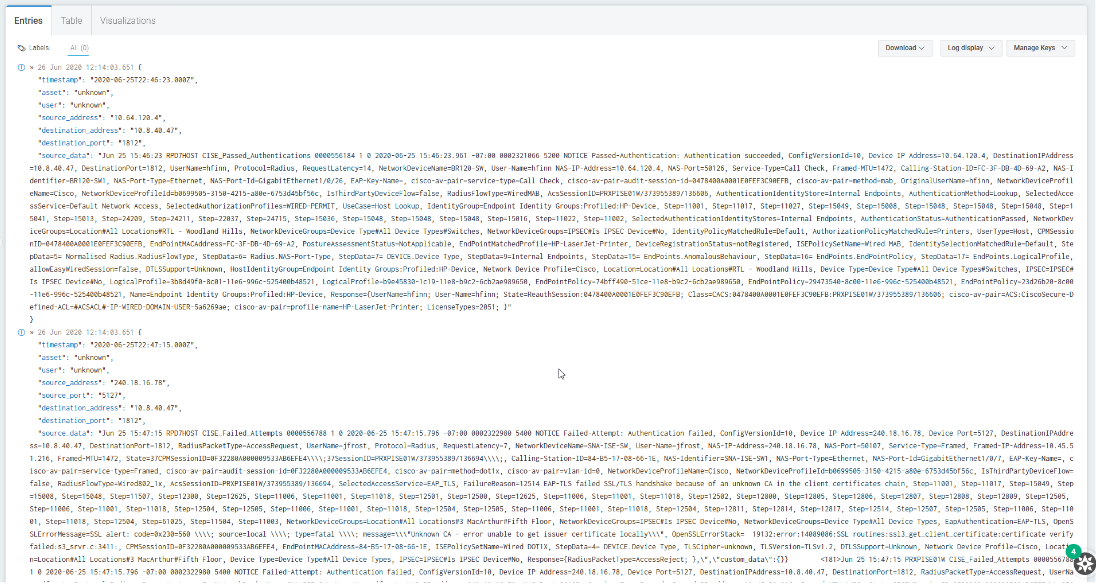
Sample Ingress Authentication (VPN) Logs in Log Search