Phishing Threats
The Phishing tab displays the details of suspected phishing threats:
Use the Alert Profiler for phishing alerts
You can use the Alert Profilerto fine-tune which threats trigger alerts. For example, you can modify the default rule so that it will trigger alerts for only certain use cases, i.e. less alerts will be triggered than with the default rule.
For more information, see Phishing Scenario Rule Conditions.
Phishing domains threats
This includes any domain that matches any company assets, including brand or company, or any permutation thereof. These domains may not be used for phishing attacks today, but they can easily be the launchpad for future threats. If, in the future, any credible proof is found that the domain will be used for phishing, for example, the addition of an MX record, it will be automatically converted to an alert.
By default, only domains that have been updated in the last 30 days are displayed.
Phishing domains threats page
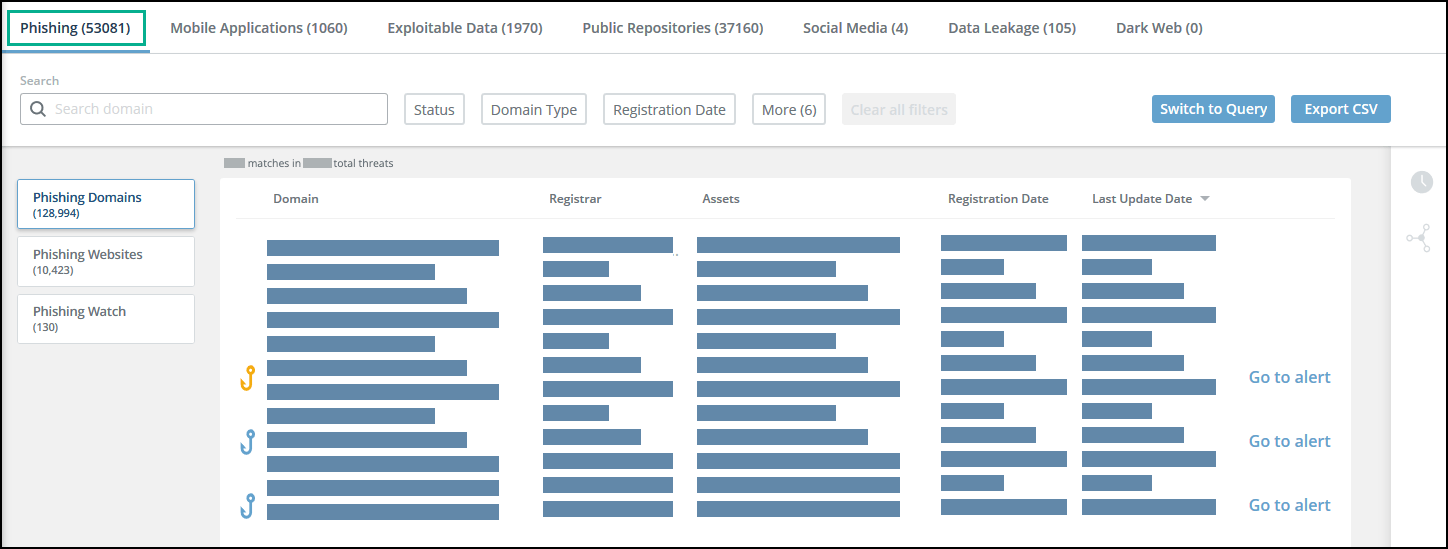
You can search for specific threats. To find exact matches only, wrap the text in “ “. Otherwise, partial matches will be shown.
Use the timeline to understand the full history and story of a domain. The timeline can explain, for example, why a monitored domain was raised to an alert (for example, an MX record was created) as well as why a threat level was lowered (for example, the MX record was deleted). Every change in a monitored parameter is displayed, enabling you to see how the domain evolved over time. For example, when a domain is purchased by a different entity, perhaps that entity has a more malicious background than the previous owner.
From the Phishing Domains tab, you can also launch an investigation on a threat as well as see the decision parameters that describe why a threat was not elevated to an alert. Understanding why a threat was not elevated can help you modify the Alert Profiler rules for a given threat. For more information, see Decision Parameters.
Threats displayed in the Phishing tab are continuously monitored, and all changes are displayed in the threat details.
Phishing domains threat details
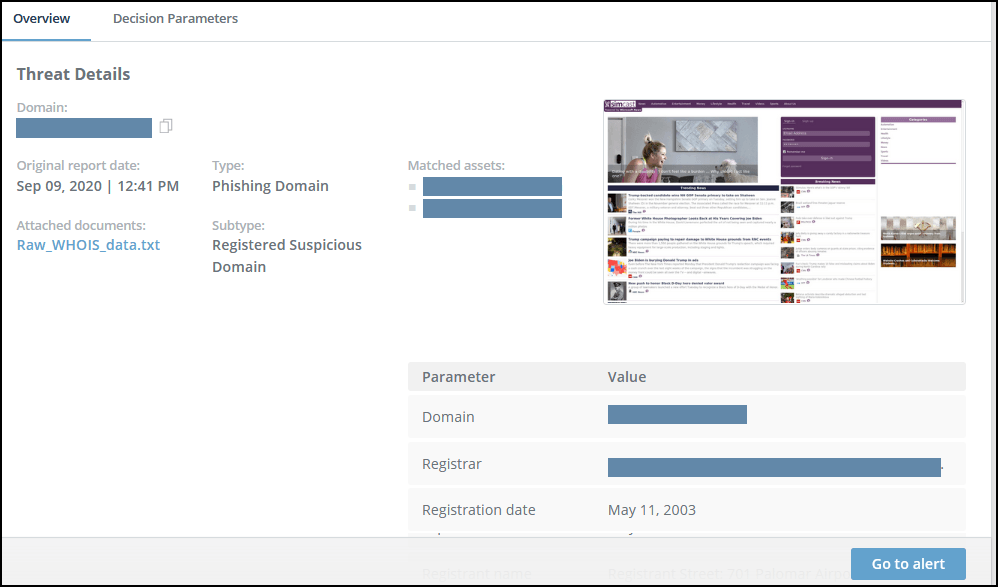
Phishing threats are sorted by date of the last update, by default. You can filter the view by clicking the filter buttons above the table or by using the Query Language. For more information, see Filter and Search Threats.
Phishing websites threats
These threats include the following:
- A website that matches the Brand name, Company name, or Domain asset type.
- A website that appears on a public list of phishing alerts, like PhishTank, etc.
- A phishing domain that also has a website.
These websites may not be used for phishing attacks today, but they can easily be the launchpad for future threats.
If the Investigation module is enabled, you can investigate a select a threat and click  to use the Investigation page to perform in-depth investigation.
to use the Investigation page to perform in-depth investigation.
Phishing websites threats page
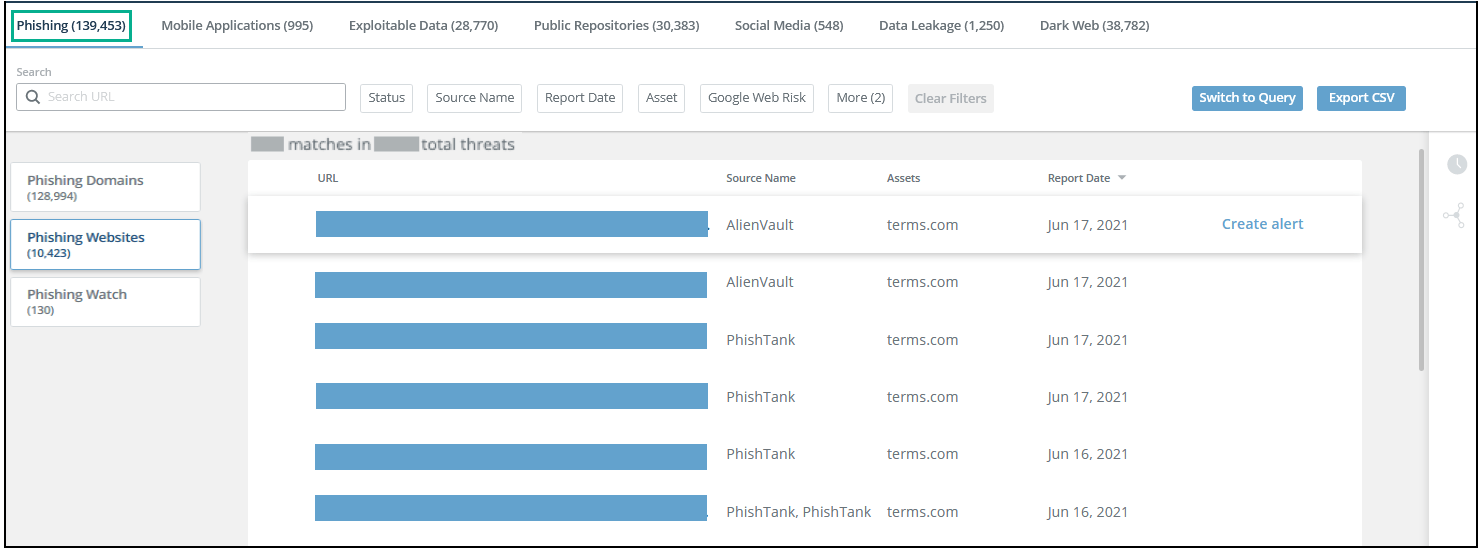
Details for each threat line are shown in the details page.
Phishing websites threat details

Phishing Watch threats
This page lists all instances which were detected by the Phishing Watch solution. (If the Phishing Watch is not enabled, this tab will be empty.)
Phishing threats are sorted by date of the last update, by default. You can filter the view by clicking the filter buttons above the table or by using the Query Language. For more information, see Filter and search threats.
If the Investigation module is enabled, you can investigate a select a threat and click  to use the Investigation page to perform in-depth investigation.
to use the Investigation page to perform in-depth investigation.
Phishing Watch threats page
Details for each threat line are shown in the details page.
Phishing Watch threat details