Cisco ASA
Cisco ASA is one of the few event sources that can handle multiple types of logs on a single port because it hosts Firewall and VPN logs.
For the SIEM (InsightIDR) parser to work, make sure that your Cisco ASA appliance has “logging timestamp” turned on and the “logging host” has been configured for the SIEM (InsightIDR) collector.
For the complete use of detection capabilities in SIEM (InsightIDR), set the logging level on the device to Severity 6 (Informational Messages). Read the Cisco ASA Configuration Guide for more information: https://www.cisco.com/c/en/us/td/docs/security/asa/asa84/configuration/guide/asa_84_cli_config/monitor_syslog.html#wp1082848 .
Learn how Cisco logging is configured: https://www.cisco.com/c/en/us/td/docs/security/asa/asa-command-reference/I-R/cmdref2/l2.html
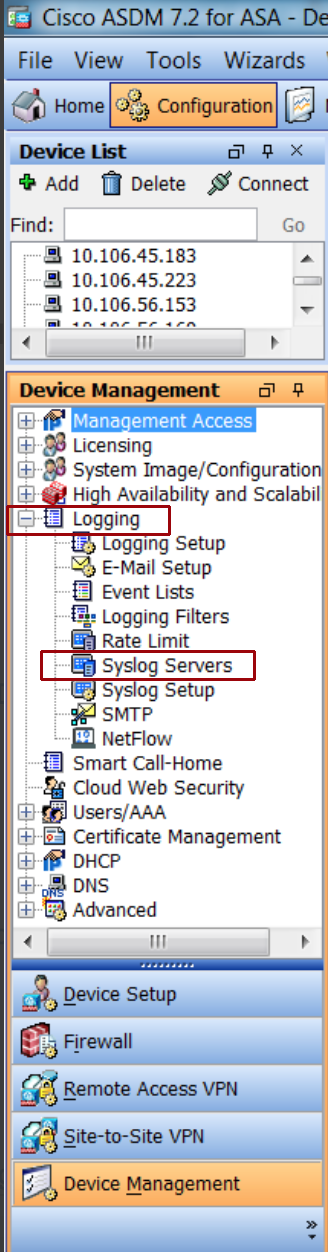
To forward logs from Cisco’s Adaptive Security Device Manager:
- In the ADSM, select Configuration.
- Select Device Management, and choose Logging from the dropdown menu.
- Select Syslog servers.
- Click Add and then in “Syslog Servers,” enter the information for your SIEM (InsightIDR) collector.
- Ensure the Collector is reachable from Cisco ASA.
For more details instructions on syslog configuration, read this information: https://www.cisco.com/c/en/us/support/docs/security/asa-5500-x-series-next-generation-firewalls/113053-asa82-syslog-config-00.html
Configure SIEM (InsightIDR) to collect data from the event source
After you complete the prerequisite steps and configure the event source to send data, you must add the event source in SIEM (InsightIDR).
To configure the new event source in SIEM (InsightIDR):
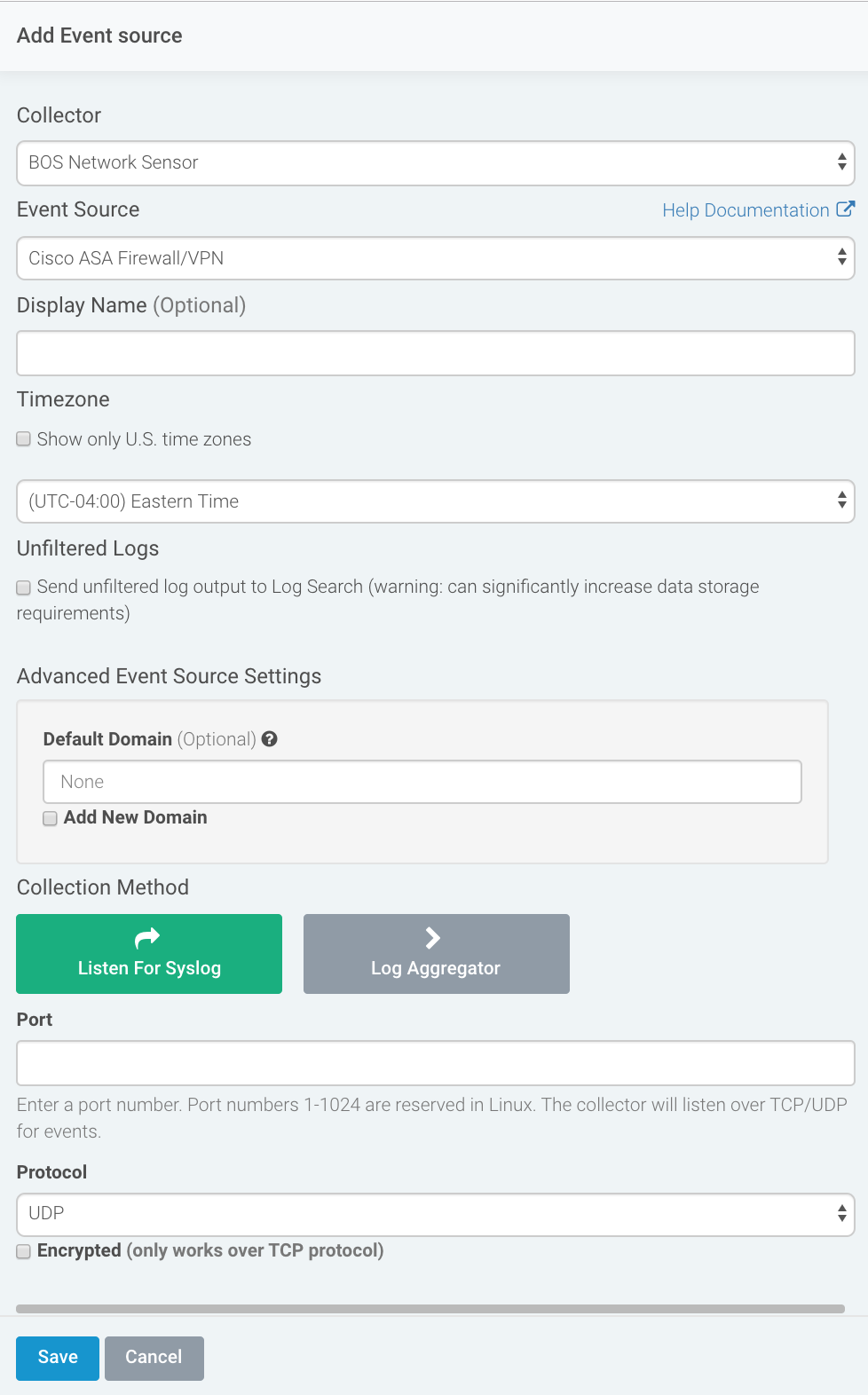
- From the left menu, go to Data Collection and click Setup Event Source > Add Event Source.
- Do one of the following:
- Search for Cisco ASA Firewall VPN in the event sources search bar.
- In the Product Type filter, select Firewall.
- Select the Cisco ASA Firewall VPN event source tile.
- Choose your collector.
- In the Select Event Source Type field, choose the option that corresponds to your Cisco Security Solution as outlined in the following table:
| Cisco Security Solution | SIEM (InsightIDR) Event Source Type |
|---|---|
| ASA | Cisco ASA event-source |
| NGIPS | Cisco ASA event-source |
| NGFW | Cisco ASA event-source |
| Any other firepower service | Cisco ASA event-source |
| Cisco ASA with FirePower services | Cisco ASA event-source |
| Cisco FirePower Threat Defense (FTD) | Cisco FTD event-source |
| Sourcefire 3D | Cisco FirePower (Sourcefire 3D) event-source |
- Choose the timezone that matches the location of your event source logs.
- Optionally choose to send unparsed logs.
- Select an attribution source.
- Configure your default domain and any Advanced Event Source Settings.
- Select a collection method and specify a port and a protocol.
- Optionally choose to Encrypt the event source if choosing TCP by downloading the Rapid7 Certificate.
- Click Save.
Verify the Configuration
To see Cisco ASA logs in SIEM (InsightIDR): From the left menu, click Log Search to view your logs to ensure events are being forwarded to the Collector. Select the applicable Log Sets and the Log Names within them. The Log Name will be the event source name or “Cisco ASA” if you did not name the event source. Cisco ASA logs flow into these Log Sets:
- Unified Asset Authentication
- Ingress Authentication
- Firewall
- VPN Session
- Web Proxy
- Intrusion Detection System (IDS)
Example Input Logs
The following table contains the events from Cisco ASA that are parsed by SIEM (InsightIDR). You may also select to send unfiltered logs to SIEM (InsightIDR) to collect and store additional events.
To learn about what these codes mean, see the Cisco documentation here: http://www.cisco.com/c/en/us/td/docs/security/asa/syslog-guide/syslogs/logsevp.html .
For additional examples of syslog, see this documentation: https://www.cisco.com/c/en/us/support/docs/security/pix-500-series-security-appliances/63884-config-asa-00.html .
| Event ID | Description | Log Example |
|---|---|---|
| ASA-4-106023 | Deny firewall connection | <13>Feb 26 11:59:40 10.62.5.20 Feb 26 11:59:40 usiadasa101 %ASA-4-106023: Deny udp src LSI-TEST-TRANSIT:10.63.1.85/43670 dst DC-TRANSIT:10.62.65.20/111 by access-group \"LSI-TEST-TRANSIT_ACCESS_IN\" [0x257f55e5, 0xe5b85413] |
| ASA-5-106100 | Allow Firewall connection | <189>Feb 27 14:11:58 10.1.2.3: %ASA-5-106100: access-list inside_access_in permitted tcp inside/xxx.xxx.xxx.xxx(60759) -> outside/xxx.xxx.xxx.xxx(80) hit-cnt 1 first hit [0x4e0b70da, 0x386bad81] |
| ASA-6-113005 | VPN Authentication failed with bad password | <166>Aug 07 2014 10:00:03 FW2-COMPANY : %ASA-6-113005: AAA user authentication Rejected : reason = Invalid password : server = 10.10.10.100 : user = username : user IP = xxx.xxx.xxx.xxx |
| ASA-6-302013 | TCP connection created | <189>Mar 25 19:00:02 10.15.128.6: %ASA-4-302013: Built outbound TCP connection 139684278 for Outside:xxx.xxx.xxx.xxx/3598 (xxx.xxx.xxx.xxx/3598) to Inside:xxx.xxx.xxx.xxx/25252 (xxx.xxx.xxx.xxx/25252) |
| ASA-6-302014 | TCP connection completed | <166>Sep 23 2015 16:12:37 xxx.xxx.xxx.xxx : %ASA-6-302014: Teardown TCP connection 115466298 for Outside:xxx.xxx.xxx.xxx/8080 to Inside:xxx.xxx.xxx.xxx/31997 duration 0:00:02 bytes 8040 TCP FINs |
| ASA-6-302015 | UDP connection created | <166>Mar 25 19:00:02 10.15.128.6 %ASA-6-302015: Built outbound UDP connection 145221138078637354 for inside:xxx.xxx.xxx.xxx/0000 (xxx.xxx.xxx.xxx/18406) to outside:xxx.xxx.xxx.xxx/8760 (xxx.xxx.xxx.xxx/8760) |
| ASA-6-302016 | UDP connection completed | <166>Dec 14 2013 16:59:36 10.6.1.1 : %ASA-6-302016: Teardown UDP connection 823803842 for Outside:xxx.xxx.xxx.xxx/00000 to Inside:xxx.xxx.xxx.xxx/00 duration 0:00:00 bytes 121 (reyga) |
| ASA-5-304001 | URL accessed | <13>Mar 5 14:23:11 xx.x.xxx.x %ASA-5-304001: xx.x.xxx.xx Accessed URL xxx.xxx.xx.xx:http://example.com |
| ASA-5-304002 | URL access denied | <189>Feb 27 14:42:23 10.4.5.6: %ASA-5-304002: Access denied URL http://s.tbdress.com/images/favicon.ico SRC 10.69.6.39 DEST xx.xx.xx.xx on interface inside |
| ASA-3-713167 | VPN Access denied | <187>Jul 21 2014 07:21:22: %ASA-3-713167: Group = AGROUP, Username = jsmith, IP = xxx.xxx.xxx.xxx, Remote peer has failed user authentication - check configured username and password |
| ASA-6-713228 | VPN Assigned IP | <134>Aug 19 2013 13:09:20: %ASA-6-713228: Group = vpnusers, Username = jsmith, IP = xx.xx.xx.xxx, Assigned private IP address xxx.xxx.xx.xxx to remote user |
| ASA-6-716039 | WebVPN Authentication failed | <166>Aug 07 2014 10:00:03 FW2-COMPANY : %ASA-6-716039: Group <DfltGrpPolicy> User <username> IP <xx.xxx.xxx.xxx> Authentication: rejected, Session Type: WebVPN. |
| ASA-7-722029 | VPN Session Termination | <164>Feb 11 2013 06:00:52 10.6.1.1 : %ASA-7-722029: Group <Operations> User <jsmith> IP <xxx.xx.x.xx> SVC Session Termination: Conns: 1, DPD Conns: 0, Comp resets: 0, Dcmp resets: 0. |
| ASA-4-722051 | VPN Assign IP | <164>Jan 13 2014 08:47:27: %ASA-4-722051: Group <SGC-VPN> User <username> IP <xx.xxx.xxx.xx> IPv4 Address <xx.xxx.x.xxx> IPv6 address <::> assigned to session |
| ASA-7-751025 | Displays assigned IP address information for AnyConnect IKEv2 connection of specified user | <167>Apr 30 2019 01:20:21: %ASA-7-751025: Local:12.34.177.229:4500 Remote:43.21.143.34:56494 Username:r7user IKEv2 Group:GroupPolicy_SAMB IPv4 Address=192.168.110.141 IPv6 address=invalid-addr-2-0.0.0.0 assigned to session |
| ASA-6-305011 | Address translation slot created | <166>Oct 30 2024 16:04:15 FWVPN01 : %ASA-6-305011: Built {dynamic|static} {TCP|UDP|ICMP} translation from interface_name :real_address/real_port [(idfw_user )] to interface_name :mapped_address/mapped_port |
| ASA-6-305012 | Address translation slot deleted | <166>Oct 30 2024 16:04:15 FWVPN01 : %ASA-6-305012: Teardown {dynamic|static} {TCP|UDP|ICMP} translation from interface_name [(acl-name )]:real_address /{real_port |real_ICMP_ID } [(idfw_user )] to interface_name :mapped_address /{mapped_port |mapped_ICMP_ID } duration time |
| ASA-3-710003 | ASA denied an attempt to connect to interface service | <166>Oct 30 2024 16:04:15 FWVPN01 :%ASA-3-710003: {TCP|UDP} access denied by ACL from xxx.xxx.xxx.xxx/3598 to interface_name :xxx.xxx.xxx.xxx/8760 |
| ASA-6-716038 | User must be authenticated by a local or remote server before WebVPN session can start | <166>Oct 30 2024 16:04:15 FWVPN01 : %ASA-6-716038: Group group User user IP ip Authentication: successful, Session Type: WebVPN. |
| ASA-6-721016 | Remote WebVPN user has logged in successfully and login information has been installed on standby unit | 721016: <166>Oct 30 2024 16:04:15 FWVPN01 :%ASA-6-721016: (device ) WebVPN session for client user user_name , IP xxx.xxx.xxx.xxx has been created. |
| ASA-6-721018 | WebVPN user record was removed from standby unit successfully. | 721018: <166>Oct 30 2024 16:04:15 FWVPN01 : %ASA-6-721018: (device ) WebVPN session for client user user_name , IP xxx.xxx.xxx.xxx has been deleted. |
Cisco ASA logs can also produce logs in the same format as some Sourcefire 3D log entries. These log entries do not contain the ASA Event ID. Here is an example of these logs:
<113>Mar 18 11:38:39 Sourcefire3D sfdc1500avc: [Primary Detection Engine (11727814-7b90-11e2-b768-a8d573eb9cc3)][MHPSA] Connection Type: Start, User: Unknown, Client: SSL client, Application Protocol: HTTPS, Web App: Unknown, Access Control Rule Name: CatchAll-Scan_for_Malware, Access Control Rule Action: Allow, Access Control Rule Reasons: Unknown, URL Category: Parked Domains, URL Reputation: Well known, URL: https://rapid7.com, Interface Ingress: s1p1, Interface Egress: s1p2, Security Zone Ingress: Internal, Security Zone Egress: External, Security Intelligence Matching IP: None, Security Intelligence Category: None, Client Version: (null), Number of File Events: 0, Number of IPS Events: 0, TCP Flags: 0x0, NetBIOS Domain: (null), Initiator Packets: 4, Responder Packets: 4, Initiator Bytes: 608, Responder Bytes: 4368, Context: Unknown, SSL Rule Name: N/A, SSL Flow Status: N/A, SSL Cipher Suite: N/A, SSL Certificate: 0000000000000000000000000000000000000000, SSL Subject CN: N/A, SSL Subject Country: N/A, SSL Subject OU: N/A, SSL Subject Org: N/A, SSL Issuer CN: N/A, SSL Issuer Country: N/A, SSL Issuer OU: N/A, SSL Issuer Org: N/A, SSL Valid Start Date: N/A, SSL Valid End Date: N/A, SSL Version: N/A, SSL Server Certificate Status: N/A, SSL Actual Action: N/A, SSL Expected Action: N/A, SSL Server Name: (null), SSL URL Category: N/A, SSL Session ID: 0000000000000000000000000000000000000000000000000000000000000000, SSL Ticket Id: 0000000000000000000000000000000000000000, {TCP} 10.7.30.21:53431 -> 66.55.15.70:443Troubleshooting
If you are experiencing issues with Cisco ASA, the problem may be with parsing or with Log Configuration.
Problems Parsing
Ensure timestamps are turned on, otherwise the Rapid7 parser will not work.
Problem with Log Configuration
Ensure the following:
- The ‘logging timestamp’ is turned on
- The ‘logging host’ has been configured for the SIEM (InsightIDR) collector.
Make sure to set the logging level on the device to Severity 6 (Informational Messages). Use this guide for instructions: https://www.cisco.com/c/en/us/td/docs/security/asa/asa84/configuration/guide/asa_84_cli_config/monitor_syslog.html#wp1082848 .
Cisco devices running versions < 9.2.1 have a bug (CSCui82751) where ASA-6-113005 events are not logged with the source IP address, preventing them from being used for detection within SIEM (InsightIDR).