CylancePROTECT
Because CylancePROTECT is part of the Virus scanning category, information from this event source will provide information to Notable Behaviors and Virus alerts.
Before You Begin
You must configure CylancePROTECT to forward its logs to a syslog server. Additionally, you must change several settings for the events to be collected by a SIEM, or the SIEM (InsightIDR) collector.
To make these changes in CylancePROTECT:
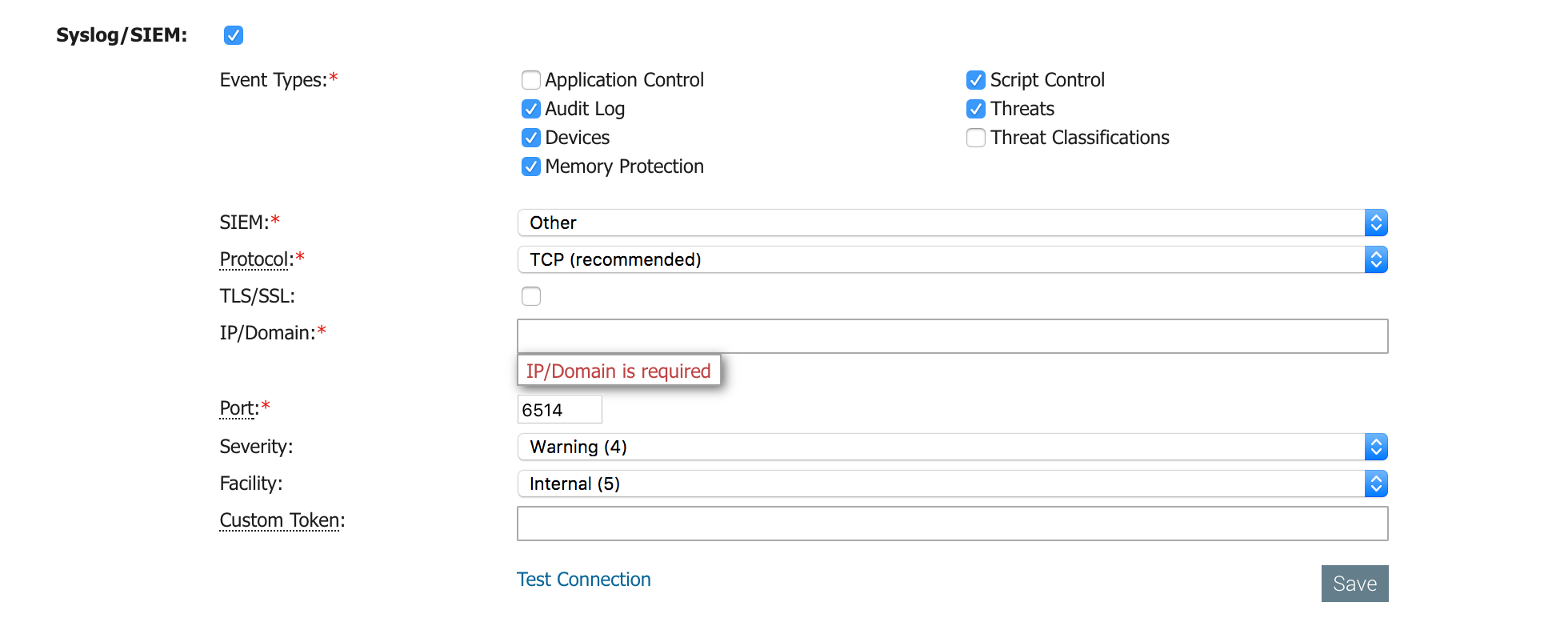
- Go to the CylancePROTECT Admin console and navigate to the “Settings” panel.
- Check the Syslog/SIEM box to enable this configuration.
- Choose which events you want to send to syslog and for SIEM (InsightIDR) to collect.
- Configure the other mandatory options.
- By default, CylancePROTECT uses port 6514 for syslog forwarding. As per the IETF Specification (https://www.ietf.org/about/standards-process.html ), the port supports TLS-enabled syslog on versions 1.1, and 1.2.
Configure SIEM (InsightIDR) to collect data from the event source
After you complete the prerequisite steps and configure the event source to send data, you must add the event source in SIEM (InsightIDR).
To configure the new event source in SIEM (InsightIDR):
- From the left menu, go to Data Collection and click Setup Event Source > Add Event Source.
- Do one of the following:
- Search for Cylance Protect in the event sources search bar.
- In the Product Type filter, select Virus Scan.
- Select the Cylance Protect event source tile.
- Choose your collector and event source. You can also name your event source if you want.
- Choose the timezone that matches the location of your event source logs.
- Optionally choose to send unparsed logs.
- Configure your default domain and any Advanced Event Source Settings.
- Select a collection method and specify a port and a protocol.
- Optionally choose to Encrypt the event source if choosing TCP by downloading the Rapid7 Certificate.
- Click Save.
ℹ️
Not seeing log data?
SIEM (InsightIDR) only parses an event from your Virus Scan event source when a virus is found.