F5 Networks BIG-IP Local Traffic Manager
The BIG-IP Local Traffic Manager (LTM) by F5 Networks allows you to control and track user activity on applications and devices in your network. You can configure BIG-IP LTM as an IDS event source in SIEM (InsightIDR) in order to parse IDS events.
You can read more about BIG-IP LTM on this F5 Networks product page:
Before You Begin
Verify that you have administrator privileges on your BIG-IP platform. This event source requires some initial configuration in BIG-IP to ensure that LTM logs are sent to the right place.
Configure F5 BIG IP
In order for SIEM (InsightIDR) to ingest the logs as an IDS event source, you must configure BIG-IP to send its logs to a remote syslog server. You can read about how to complete this process in detail in this F5 support article: https://support.f5.com/csp/article/K13080
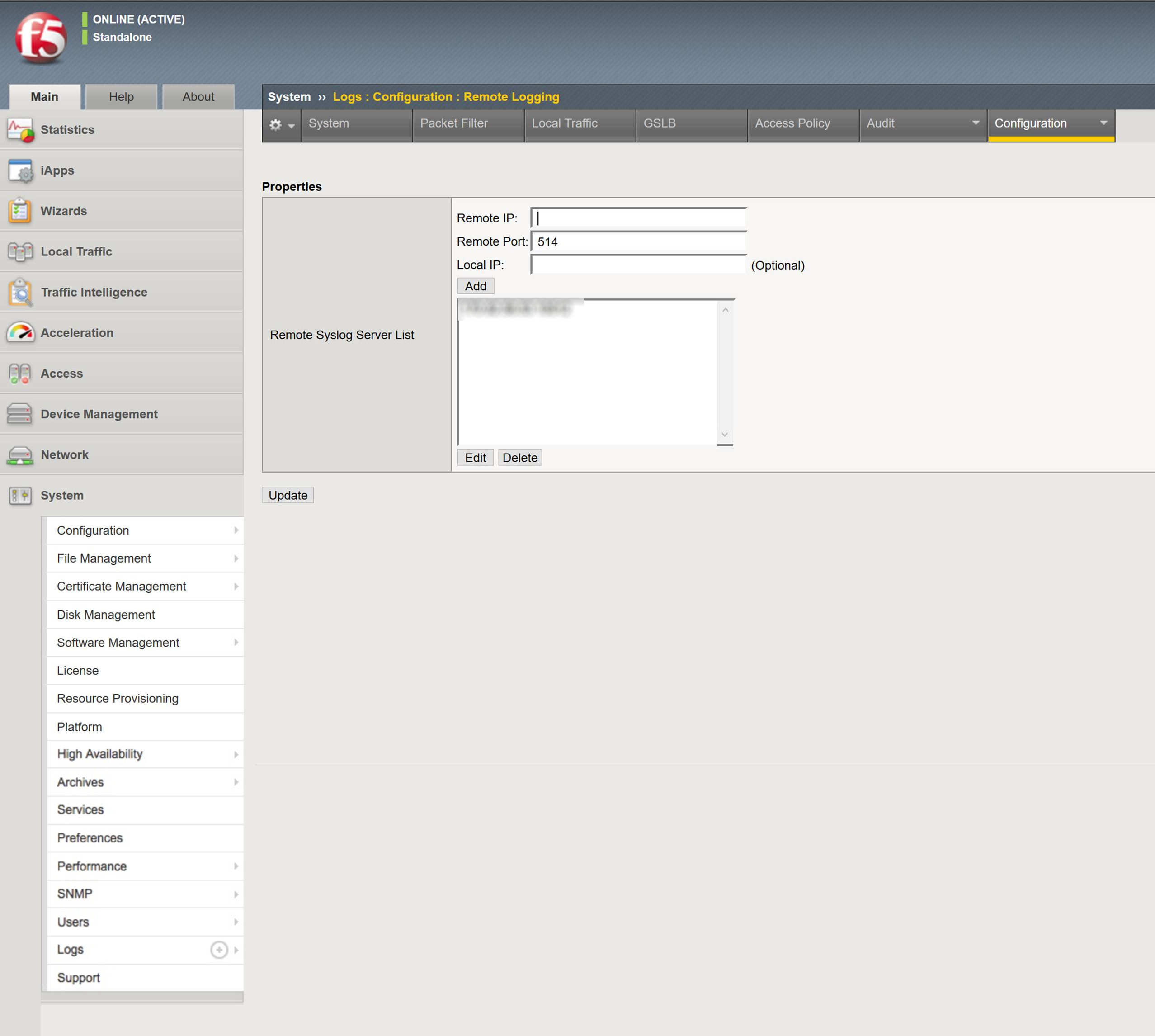
To configure syslog forwarding in BIG-IP:
- Sign in to your F5 BIG-IP interface.
- On the left menu, expand the System page near the bottom of the list and select Logs.
- Expand the Configuration dropdown menu on the right side of the page and click Remote Logging.
- In the “Remote IP” field, enter the IP address for your Collector and the unique port you want to use.
- Enter the unique port you want to use for the syslog server.
- Click Add. The IP address and port will appear in the “Remote Syslog Server List” field below.
- Click Update to confirm the changes.
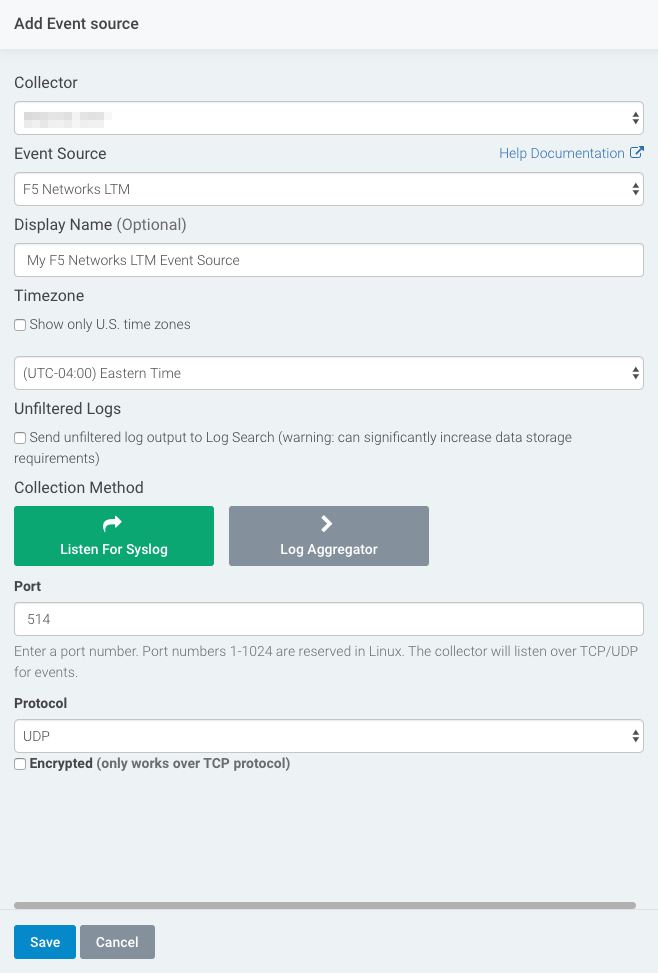
Configure SIEM (InsightIDR) to collect data from the event source
After you complete the prerequisite steps and configure the event source to send data, you must add the event source in SIEM (InsightIDR).
To configure the new event source in SIEM (InsightIDR):
- From the left menu, go to Data Collection and click Setup Event Source > Add Event Source.
- Do one of the following:
- Search for F5 Networks BIG-IP Local Traffic Manager in the event sources search bar.
- In the Product Type filter, select IDS.
- Select the F5 Networks BIG-IP Local Traffic Manager event source tile.
- Choose your collector and event source. You can also name your event source if you want.
- Choose the timezone that matches the location of your event source logs.
- Optionally choose to send unparsed logs.
- Select a data collection method and specify a port and a protocol.
- Optionally choose to Encrypt the event source if choosing TCP by downloading the Rapid7 Certificate.
- Click Save when finished.