FireEye NX
FireEye NX Network Security helps you detect and block attacks from the web. It protects the entire spectrum of attacks from relatively unsophisticated drive-by malware to highly targeted zero-day exploits. Its capabilities provide an extremely low false positive rate by leveraging the FireEye Multi-Vector Virtual Execution (MVX) engine to confirm when malware calls out to C&C servers.
Before You Begin
FireEye supports syslogs in LEEF or CEF format. Because the InsightIDR parser expects CEF, you must configure FireEye to send data in the correct format.
- Log onto the FireEye NX Web.
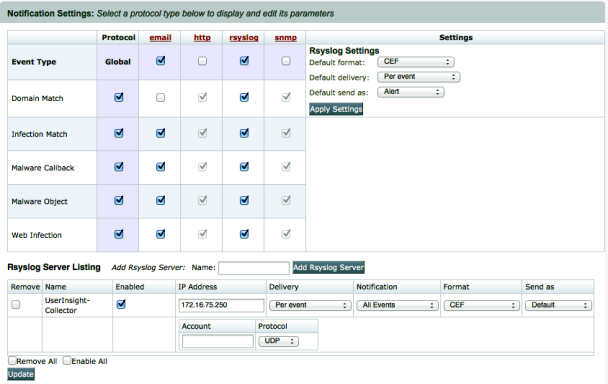
- Go to Settings > Notifications.
- Check off rsyslog to enable a Syslog notification configuration.
- Enter a name to label your FireEye connection to the InsightIDR Collector in the Name field.
- Click the Add Rsyslog Server button.
- Enter the InsightIDR Collector IP address in the “IP Address” field.
- Check off the Enabled check box.
- Select Per Event in the “Delivery” drop-down list.
- Select All Events from the “Notifications” drop-down list.
- Select CEF as the “Format” drop-down list. Other formats are not supported.
- Leave the “Account” field empty.
- Select UDP from the “Protocol” drop-down list.
- Click the Update button.
Ensure that you send syslog to the collector on a unique UDP or TCP port (above 1024). FireEye NX uses port 514 by default. This should be changed from the command line interface.
Do Not Use Port 514
InsightIDR recommends that you do not use port 514 whenever possible. Use this port only for network systems that cannot be configured to use any other port but port 514.
You can read more information about FireEye NX and Splunk here: https://www.fireeye.com/content/dam/fireeye-www/global/en/partners/pdfs/fireeye-splunk-intro-to-integration.pdf .
Configure InsightIDR to collect data from the event source
After you complete the prerequisite steps and configure the event source to send data, you must add the event source in InsightIDR.
To configure the new event source in InsightIDR:
- From the left menu, go to Data Collection and click Setup Event Source > Add Event Source.
- Do one of the following:
- Search for FireEye NX in the event sources search bar.
- In the Product Type filter, select Advanced Malware.
- Select the FireEye NX event source tile.
- Choose your collector and event source. You can also name your event source if you want.
- Choose the timezone that matches the location of your event source logs.
- Optionally choose to send unfiltered logs.
- Select your collection method.
- Optionally choose to Encrypt the event source if choosing TCP by downloading the Rapid7 Certificate.
- Click Save.
Confirm the Integration
Test that the FireEye NX Notifications page does not get sent to the InsightIDR Collector. To accomplish this, trigger a real alert or use the deployment checks.
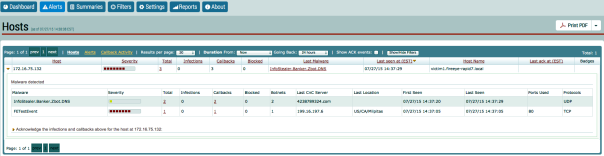
Confirm Alerts within InsightIDR
After you triggered the alert, you should see new incidents in the InsightIDR dashboard.
Once they appear, you can click the Incident to drill down into the event to display the User Context and Asset names.
Click the **Advanced Malware Alert ** link to see more specific details about the alert, such as the occurrences for this alert.
Troubleshooting
Not Seeing FireEye NX Data
Data from this event source should be in the Collector log at C:\Program Files\Rapid7\logs\collector.log in the(Undefined variable: Variables.Project) cloud.
If you do not see this data:
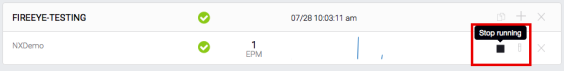
- Click the stop button in the FireEye NX appliance.
- Create a “Custom Logs” listener on the same port. This is found under the Rapid7 category in FireEye NX.
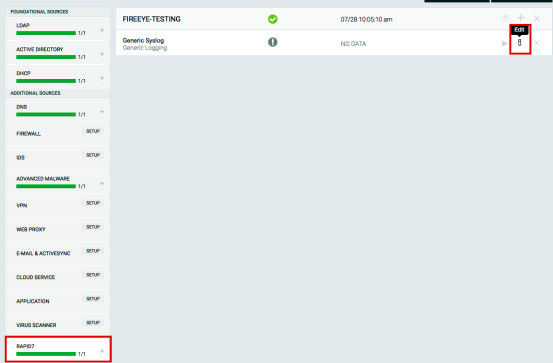
- In InsightIDR, add a new Custom Logs event source from the “Raw Data” category.
- Use the same port and protocol information from the FireEye NX configuration.
- Click Save.